Security Target for A10 Networks Thunder 3030S and 1030S Application Delivery Controllers, Version 1.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Federal Register/Vol. 83, No. 150/Friday, August 3, 2018/Notices
Federal Register / Vol. 83, No. 150 / Friday, August 3, 2018 / Notices 38161 Community Community map repository address Canadian County, Oklahoma and Incorporated Areas Project: 12–06–1030S Preliminary Date: February 8, 2018 City of El Reno ......................................................................................... Municipal Building, 101 North Choctaw Avenue, El Reno, OK 73036. Aransas County, Texas and Incorporated Areas Project: 15–06–0811S Preliminary Date: March 16, 2018 City of Aransas Pass ................................................................................ City Hall, 600 West Cleveland Boulevard, Aransas Pass, TX 78336. San Patricio County, Texas and Incorporated Areas Project: 15–06–0811S Preliminary Date: March 16, 2018 City of Aransas Pass ................................................................................ City Hall, 600 West Cleveland Boulevard, Aransas Pass, TX 78336. [FR Doc. 2018–16666 Filed 8–2–18; 8:45 am] 97.048, Disaster Housing Assistance to Brown Fund; 97.032, Crisis Counseling; BILLING CODE 9110–12–P Individuals and Households In Presidentially 97.033, Disaster Legal Services; 97.034, Declared Disaster Areas; 97.049, Disaster Unemployment Assistance (DUA); Presidentially Declared Disaster Assistance— 97.046, Fire Management Assistance Grant; DEPARTMENT OF HOMELAND Disaster Housing Operations for Individuals 97.048, Disaster Housing Assistance to and Households; 97.050, Presidentially Individuals and Households In Presidentially SECURITY Declared Disaster Assistance to Individuals -
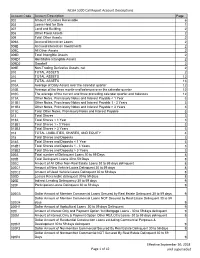
NCUA 5300 Call Report Account Descriptions Page 1 of 42 Effective
NCUA 5300 Call Report Account Descriptions Account Code Account Description Page 002 Amount of Leases Receivable 6 003 Loans Held for Sale 1 007 Land and Building 2 008 Other Fixed Assets 2 009 Total Other Assets 2 009A Accrued Interest on Loans 2 009B Accrued Interest on Investments 2 009C All Other Assets 2 009D Total Intangible Assets 2 009D1 Identifiable Intangible Assets 2 009D2 Goodwill 2 009E Non-Trading Derivative Assets, net 2 010 TOTAL ASSETS 2 010 TOTAL ASSETS 12 010 TOTAL ASSETS 13 010A Average of Daily Assets over the calendar quarter 12 010B Average of the three month-end balances over the calendar quarter 12 010C The average of the current and three preceding calendar quarter-end balances 12 011A Other Notes, Promissory Notes and Interest Payable < 1 Year 3 011B1 Other Notes, Promissory Notes and Interest Payable 1 - 3 Years 3 011B2 Other Notes, Promissory Notes and Interest Payable > 3 Years 3 011C Total Other Notes, Promissory Notes and Interest Payable 3 013 Total Shares 3 013A Total Shares < 1 Year 3 013B1 Total Shares 1 - 3 Years 3 013B2 Total Shares > 3 Years 3 014 TOTAL LIABILITIES, SHARES, AND EQUITY 4 018 Total Shares and Deposits 3 018A Total Shares and Deposits < 1 Year 3 018B1 Total Shares and Deposits 1 - 3 Years 3 018B2 Total Shares and Deposits > 3 Years 3 020A Total number of Delinquent Loans 30 to 59 Days 8 020B Total Delinquent Loans 30 to 59 Days 8 020C Amount of All Other Non-Real Estate Loans 30 to 59 days delinquent 8 020C1 Amount of New Vehicle Loans Delinquent 30 to 59 days 8 020C2 Amount of Used -

T2 R1.5 Femoral Nailing System
T2 R1.5 Femoral Nailing System Operative Technique Femoral Nailing System Contributing Surgeons Prof. Dr. med. Volker Bühren Chief of Surgical Services Medical Director of Murnau Trauma Center Murnau Germany Joseph D. DiCicco III, D. O. Director Orthopaedic Trauma Service Good Samaritan Hospital Dayton, Ohio Associate Clinical Professor of Orthopeadic Surgery Ohio University and Wright State University USA Thomas G. DiPasquale, D. O. Medical Director, Orthopedic Trauma Services Director, Orthopedic Trauma Fellowship and This publication sets forth detailed Orthopedic Residency Programs recommended procedures for using York Hospital Stryker Osteosynthesis devices and York instruments. USA It offers guidance that you should heed, but, as with any such technical guide, each surgeon must consider the particular needs of each patient and make appropriate adjustments when and as required. A workshop training is required prior to first surgery. All non-sterile devices must be cleaned and sterilized before use. Follow the instructions provided in our reprocessing guide (L24002000). Multi-component instruments must be disassembled for cleaning. Please refer to the corresponding assembly/ disassembly instructions. See package insert (L22000007) for a complete list of potential adverse effects, contraindications, warnings and precautions. The surgeon must discuss all relevant risks, including the finite lifetime of the device, with the patient, when necessary. Warning: Fixation Screws: Stryker Ostreosynthesis bone screws are not approved or intended for screw attachment or fixation to the posterior elements (pedicles) of the cervical, thoracic or lumbar spine. 2 Contents Page 1. Introduction 4 Implant Features 4 Instrument Features 6 References 6 2. Indications, Precautions and Contraindications 7 Indications 7 Precautions 7 Relative Contraindications 7 3. -

Reimbursement to American Red Cross for Hurricanes Charley, Frances, Ivan, and Jeanne
United States Government Accountability Office GAO Report to Congressional Committees May 2006 DISASTER RELIEF Reimbursement to American Red Cross for Hurricanes Charley, Frances, Ivan, and Jeanne a GAO-06-518 May 2006 DISASTER RELIEF Accountability Integrity Reliability Highlights Reimbursement to American Red Cross Highlights of GAO-06-518, a report to for Hurricanes Charley, Frances, Ivan, congressional committees and Jeanne Why GAO Did This Study What GAO Found In accordance with Public Law 108- The signed agreement between FEMA and the Red Cross properly 324, GAO is required to audit the established criteria for the Red Cross to be reimbursed for allowable reimbursement of up to $70 million expenses for disaster relief, recovery, and emergency services related to of appropriated funds to the hurricanes Charley, Frances, Ivan, and Jeanne. The Red Cross incurred American Red Cross (Red Cross) $88.6 million of allowable expenses. for disaster relief associated with 2004 hurricanes Charley, Frances, Ivan, and Jeanne. The audit was Consistent with the law, the agreement explicitly provided that the Red performed to determine if (1) the Cross would not seek reimbursement for any expenses reimbursed by other Federal Emergency Management federal funding sources. GAO identified $0.3 million of FEMA paid costs that Agency (FEMA) established the Red Cross properly deducted from its reimbursement requests, so as not criteria and defined allowable to duplicate funding by other federal sources. The Red Cross also reduced its expenditures to ensure that requested reimbursements by $60.2 million to reflect private donations for reimbursement claims paid to the disaster relief for the four hurricanes, for a net reimbursement of Red Cross met the purposes of the 28.1 million. -

Contemplating Money and Wealth in Monastic Writing C. 1060–C. 1160 Giles E
© Copyrighted Material Chapter 3 Contemplating Money and Wealth in Monastic Writing c. 1060–c. 1160 Giles E. M. Gasper ashgate.com It is possible to spend money in such a way that it increases; it is an investment which grows, and pouring it out only brings in more. The very sight ofashgate.com sumptuous and exquisite baubles is sufficient to inspire men to make offerings, though not to say their prayers. In this way, riches attract riches, and money produces more money. For some unknown reasons, the richer a place appears, the more freely do offerings pour in. Gold-cased relics catch the gaze and open the purses. If you ashgate.com show someone a beautiful picture of a saint, he comes to the conclusion that the saint is as holy as the picture is brightly coloured. When people rush up to kiss them, they are asked to donate. Beauty they admire, but they do no reverence to holiness. … Oh, vanity of vanities, whose vanity is rivalled only by its insanity! The walls of the church are aglow, but the ashgate.compoor of the church go hungry. The 1 stones of the church are covered with gold, while its children are left naked. The famousApologia of Bernard of Clairvaux to Abbot William of St Thierry on the alleged decadence of the Cluniac monastic observance is well known. While Bernard does not makes an unequivocalashgate.com condemnation of wealth, adornment and money, but rather a series of qualified, if biting, remarks on the subject directed particularly to monastic communities, material prosperity and its 1 Bernard of Clairvaux,ashgate.com An Apologia to Abbot William, M. -

Family Group Sheet for Cnut the Great
Family Group Sheet for Cnut the Great Husband: Cnut the Great Birth: Bet. 985 AD–995 AD in Denmark Death: 12 Nov 1035 in England (Shaftesbury, Dorset) Burial: Old Minster, Winchester. Bones now in Winchester Cathedral Father: King Sweyn I Forkbeard Mother: Wife: Emma of Normandy Birth: 985 AD Death: 06 Mar 1052 in Winchester, Hampshire Father: Richard I Duke of Normandy Mother: Gunnor de Crepon Children: 1 Name: Gunhilda of Denmark F Birth: 1020 Death: 18 Jul 1038 Spouse: Henry III 2 Name: Knud III Hardeknud M Birth: 1020 in England Death: 08 Jun 1042 in England Burial: Winchester Cathedral, Winchester, England Notes Cnut the Great Cnut the Great From Wikipedia, (Redirected from Canute the Great) Cnut the Great King of all the English, and of Denmark, of the Norwegians, and part of the Swedes King of Denmark Reign1018-1035 PredecessorHarald II SuccessorHarthacnut King of all England Reign1016-1035 PredecessorEdmund Ironside SuccessorHarold Harefoot King of Norway Reign1028-1035 PredecessorOlaf Haraldsson SuccessorMagnus Olafsson SpouseÆlfgifu of Northampton Emma of Normandy Issue Sweyn Knutsson Harold Harefoot Harthacnut Gunhilda of Denmark FatherSweyn Forkbeard MotherSigrid the Haughty also known as Gunnhilda Bornc. 985 - c. 995 Denmark Died12 November 1035 England (Shaftesbury, Dorset) BurialOld Minster, Winchester. Bones now in Winchester Cathedral Cnut the Great, also known as Canute or Knut (Old Norse: Knútr inn ríki[1] (c. 985 or 995 - 12 November 1035) was a Viking king of England and Denmark, Norway, and parts of Sweden, whose successes as a statesman, politically and militarily, prove him to be one of the greatest figures of medieval Europe and yet at the end of the historically foggy Dark Ages, with an era of chivalry and romance on the horizon in feudal Europe and the events of 1066 in England, these were largely 'lost to history'. -

1030S.01I Bill
COMMITTEE ON LEGISLATIVE RESEARCH OVERSIGHT DIVISION FISCAL NOTE L.R. No.: 1030S.01I Bill No.: SB 43 Subject: Commerce and Insurance, Department of; Health, Public; Insurance - Health; Medicaid/Mo Healthnet; Social Services, Department of; Type: Original Date: February 2, 2021 Bill Summary: This proposal requires health benefit plans to cover at least those services which are covered for persons receiving benefits under Mo HealthNet. FISCAL SUMMARY ESTIMATED NET EFFECT ON GENERAL REVENUE FUND FUND AFFECTED FY 2022 FY 2023 FY 2024 General Revenue (Unknown, Could (Unknown, Could (Unknown, Could Fund Exceed $4,284,000) Exceed $8,568,000) Exceed $8,568,000) Total Estimated Net Effect on General (Unknown, Could (Unknown, Could (Unknown, Could Revenue Exceed $4,284,000) Exceed $8,568,000) Exceed $8,568,000) ESTIMATED NET EFFECT ON OTHER STATE FUNDS FUND AFFECTED FY 2022 FY 2023 FY 2024 Other Funds (Unknown, Could (Unknown, Could (Unknown, Could Exceed $1,022,000) Exceed $2,044,000) Exceed $2,044,000) Total Estimated Net Effect on Other State (Unknown, Could (Unknown, Could (Unknown, Could Funds Exceed $1,022,000) Exceed $2,044,000) Exceed $2,044,000) Numbers within parentheses: () indicate costs or losses. L.R. No. 1030S.01I Bill No. SB 43 Page 2 of 7 February 2, 2021 ESTIMATED NET EFFECT ON FEDERAL FUNDS FUND AFFECTED FY 2022 FY 2023 FY 2024 Federal Funds (Unknown, Could (Unknown, Could (Unknown, Could Exceed $1,694,000) Exceed $3,388,000) Exceed $3,388,000) Total Estimated Net Effect on All Federal (Unknown, Could (Unknown, Could (Unknown, Could Funds Exceed $1,694,000) Exceed $3,388,000) Exceed $3,388,000) ESTIMATED NET EFFECT ON FULL TIME EQUIVALENT (FTE) FUND AFFECTED FY 2022 FY 2023 FY 2024 Total Estimated Net Effect on FTE 0 0 0 Estimated Net Effect (expenditures or reduced revenues) expected to exceed $250,000 in any of the three fiscal years after implementation of the act. -

DSX Modem Installation Manual
® DSX Modem Installation Manual DSX Access Systems, Inc. 10731 Rockwall Road Dallas, Texas 75238 888-419-8353 Sales, Shipping and Accounting 800-346-5288 Technical Support 214-553-6140 Phone www.dsxinc.com 214-553-6147 FAX Modem 02/05 DSX Access Systems, Inc. 10731 Rockwall Road Dallas, Texas 75238 888-419-8353 Sales, Shipping and Accounting 800-346-5288 Technical Support 214-553-6140 Phone www.dsxinc.com 214-553-6147 FAX Modem 02/05 Table of Contents Modem Operation Overview……………………………………………………………………………1 Modem recommendation…………………………………………………………………………….….2 Phone Call Description………………………………………………………………………………….2 Communication Security Password (Location Password)………………………………………………3 DSX Modem LED Operation.……………………………………………………………………….….4 Modem to PC Connections…………………………………………………………………………….. 4 Modem Power Sources………………………………………………………………………………….5 Modem Mounting in DSX Enclosures………………………………………………………………….5 Modem to DSX-1040, 1032, 1033 and 1034 Connections……………………………………………..7 Modem to DSX-1022, 1021 and 1020 via MCI………………………………………………………...8 Telephone Line Connections……………………………………………………………………………8 Initial Modem Communications Procedure for Dial-up Location………………………………………9 Modem Compatibility………………………………………………………………………………….11 Existing Modems …..………………………………………………………………………………….11 Modem Initialization Strings …..……………………………………………………………………...12 Changing the Modem Initialization String for the PC…………………………………………………13 Modem Speaker Volume…...………………………………………………………………………….13 Resetting the Modem…………………………………………………………………………………..13 Default Baud Rates…………………………………………………………………………………….13 -

AUGUST 12, 2014 a REGULAR MEETING of the Board of Chosen
AUGUST 12, 2014 A REGULAR MEETING of the Board of Chosen Freeholders of the County of Somerset was held on the above date at 6:30 P.M.8/ The Pledge of Allegiance to the Flag was led by Director Scaglione. Deputy Clerk Quick stated that the meeting was in compliance with the Open Public Meetings Act and that adequate notice was provided on January 3, 2014 and May 30, 2014 for the change in time as follows: 1. Mailed to the Star Ledger, the Home News, and the Courier News. 2. Posted on the Official County Bulletin Board. 3. Filed with the County Clerk. 4. Distributed to all persons requesting such information. Roll Call ------------------ PRESENT: Zaborowski, Palmer, Caliguire, Scaglione ABSENT: Walsh ALSO PRESENT: County Administrator/Clerk M. Amorosa, County Counsel W. Cooper, P. McCall, K. Quick, T. Jenkins, S. Tomaro, Y. Childress, M/ Frost, M. Loper, Y. Childress EMPLOYEE RECOGNITION COMMITTEE PRESENTATION • Employee of the month – Raquel Aiello, Human Services This presentation was made at the August 12, 2014 work session meeting at 4:30 p.m. at which time Ms. Aiello accepted her award and thanked the Board. At this time Director Scaglione instructed the Board that, due to the lack of quorum at the July 22, 2014 meeting, a vote still needed to be taken on the two Ordinances for which the Public Hearings were held. MRS. WALSH INTRODUCED THE FOLLOWING RESOLUTION AND MOVED ITS ADOPTION: ORD14-431 BOND ORDINANCE PROVIDING AN APPROPRIATION OF $12,504,740 FOR VARIOUS IMPROVEMENTS AND PURPOSES FOR AND BY THE COUNTY OF SOMERSET, NEW JERSEY, AND AUTHORIZING THE ISSUANCE OF $11,879,503 BONDS OR NOTES OF SOMERSET COUNTY FOR FINANCING PART OF THE COST THEREOF BE IT ORDAINED, BY THE BOARD OF CHOSEN FREEHOLDERS OF THE COUNTY OF SOMERSET, NEW JERSEY (not less than two-thirds of all members thereof affirmatively concurring) AS FOLLOWS: SECTION 1: The improvements described in Section 3 of this bond ordinance (the “Improvements”) are hereby authorized to be undertaken by the County of Somerset, New Jersey (the “County”) as general improvements. -
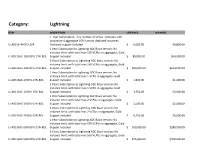
A10 Networks Price List
Category: Lightning ITEM DESCRIPTION LIST PRICE DIR PRICE 1 Year Subscription. Any number of virtual instances with maximum 4 aggregate VCPU across deployed instances. LI-ADC-B-4VCPU-1YR Technical support included $ 6,000.00 $4,800.00 1 Year Subscription to Lightning ADC Basic version; No instance limit, with total max 100 VCPUs in aggregate, Gold LI-ADC-BAS-100VCPU-1YR-BDL Support included $ 80,000.00 $64,000.00 3 Years Subscription to Lightning ADC Basic version; No instance limit, with total max 100 VCPUs in aggregate, Gold LI-ADC-BAS-100VCPU-3YR-BDL Support included $ 200,000.00 $160,000.00 1 Year Subscription to Lightning ADC Basic version; No instance limit, with total max 1 VCPU in aggregate, Gold LI-ADC-BAS-1VCPU-1YR-BDL Support included $ 1,500.00 $1,200.00 3 Years Subscription to Lightning ADC Basic version; No instance limit, with total max 1 VCPU in aggregate, Gold LI-ADC-BAS-1VCPU-3YR-BDL Support included $ 3,750.00 $3,000.00 1 Year Subscription to Lightning ADC Basic version; No instance limit, with total max 2 VCPUs in aggregate, Gold LI-ADC-BAS-2VCPU-1YR-BDL Support included $ 2,500.00 $2,000.00 3 Years Subscription to Lightning ADC Basic version; No instance limit, with total max 2 VCPUs in aggregate, Gold LI-ADC-BAS-2VCPU-3YR-BDL Support included $ 6,250.00 $5,000.00 1 Year Subscription to Lightning ADC Basic version; No instance limit, with total max 500 VCPUs in aggregate, Gold LI-ADC-BAS-500VCPU-1YR-BDL Support included $ 350,000.00 $280,000.00 3 Years Subscription to Lightning ADC Basic version; No instance limit, with total max 500 VCPUs in aggregate, Gold LI-ADC-BAS-500VCPU-3YR-BDL Support included $ 875,000.00 $700,000.00 1 Year Subscription to Lightning ADC Basic version; No instance limit, with total max 5 VCPUs in aggregate, Gold LI-ADC-BAS-5VCPU-1YR-BDL Support included $ 5,000.00 $4,000.00 3 Years Subscription to Lightning ADC Basic version; No instance limit, with total max 5 VCPUs in aggregate, Gold LI-ADC-BAS-5VCPU-3YR-BDL Support included $ 12,500.00 $10,000.00 1 Year Subscription. -

Skaldic Praise-Poetry at the Court of Cnut
Contextualising the Knútsdrápur: Skaldic Praise-Poetry at the Court of Cnut Matthew Townend Centre for Medieval Studies, University of York, UK It is generally recognised that during the reign of Cnut the Danish king’s court came to represent the focal point for skaldic composition and patronage in the Norse-speaking world. According to the later Icelandic Skáldatal, no fewer than eight poets were remembered as having composed for Cnut,1 and the works of five of them survive (some, admittedly, in fragmentary form): Sigvatr fiór›arson’s Knútsdrápa;2 Óttarr svarti’s Knútsdrápa;3 Hallvar›r háreksblesi’s 1 For the Skáldatal list see Edda Snorra Sturlusonar, ed. Sveinbjörn Egilsson et al, 3 vols in 4 (Copenhagen, 1848- 87), III, 251-86: 282-3. 2 For text see Den Norsk-Islandske Skjaldedigtning, ed. Finnur Jónsson, 4 vols (Copenhagen, 1912-15), IB, 232-4. For (almost complete) translation see English Historical Documents: Volume I c. 500-1042, ed. Dorothy Whitelock (London, 1955), 310-11 (No. 16, where the poem is titled Tøgdrápa). 3 For text see Skjaldedigtning, ed. Finnur Jónsson, IB, 272-5; Margaret Ashdown, English and Norse Documents Relating to the Reign of Ethelred the Unready (Cambridge, 1930), 136-9 (text and translation). For translation see English Historical Documents, ed. Whitelock, 308-9 (No. 15). 511 512 Matthew Townend Knútsdrápa;4 fiórarinn loftunga’s Höfu›lausn5 and Tøgdrápa;6 and (probably) a fragment by Arnórr jarlaskáld.7 Of the other poets cited in Skáldatal, no verse in honour of Cnut is extant by Bersi Torfuson, and none at all by Steinn Skaptason and the obscure Ó›arkeptr. -

Life and Cult of Cnut the Holy the First Royal Saint of Denmark
Life and cult of Cnut the Holy The first royal saint of Denmark Edited by: Steffen Hope, Mikael Manøe Bjerregaard, Anne Hedeager Krag & Mads Runge Life and cult of Cnut the Holy The first royal saint of Denmark Life and cult of Cnut the Holy The first royal saint of Denmark Report from an interdisciplinary research seminar in Odense. November 6th to 7th 2017 Edited by: Steffen Hope, Mikael Manøe Bjerregaard, Anne Hedeager Krag & Mads Runge Kulturhistoriske studier i centralitet – Archaeological and Historical Studies in Centrality, vol. 4, 2019 Forskningscenter Centrum – Odense Bys Museer Syddansk Univeristetsforlag/University Press of Southern Denmark Report from an interdisciplinary research seminar in Odense. November 6th to 7th 2017 Published by Forskningscenter Centrum – Odense City Museums – University Press of Southern Denmark ISBN: 9788790267353 © The editors and the respective authors Editors: Steffen Hope, Mikael Manøe Bjerregaard, Anne Hedeager Krag & Mads Runge Graphic design: Bjørn Koch Klausen Frontcover: Detail from a St Oswald reliquary in the Hildesheim Cathedral Museum, c. 1185-89. © Dommuseum Hildesheim. Photo: Florian Monheim, 2016. Backcover: Reliquary containing the reamains of St Cnut in the crypt of St Cnut’s Church. Photo: Peter Helles Eriksen, 2017. Distribution: Odense City Museums Overgade 48 DK-5000 Odense C [email protected] www.museum.odense.dk University Press of Southern Denmark Campusvej 55 DK-5230 Odense M [email protected] www.universitypress.dk 4 Content Contributors ...........................................................................................................................................6