Network Forensics Report – CMP416 Digital Forensics 2 Zack Anderson ([email protected]) University of Abertay Dundee NETWORK FORENSICS REPORT 2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Interview by Susanne Schuricht with IEPE B.T. Rubingh
Interview by Susanne Schuricht with IEBE B.T.Rubingh, Berlin 2005 (long version / english) SU: How was chessboxing born? Where did the idea come from? IEPE: Chessboxing was born in 2002; I was looking for new ideas after finishing my work called "Miracle of Berlin". In Amsterdam I met Luis, a.k.a. "Luis the Lawyer". We were hanging out in a bar and talking, and we found out that both of us had started boxing a year earlier and both of us have been playing chess for many years. The first idea we had was: Let's have a boxing match. Then I came up with the chessboxing idea from the comic "Froid équateur" by ENKI BILAL, which is set in 2096 and sees inhabitants of a ravaged planet competing in various games, including chessboxing. SU: Had any of your projects been inspired by a comic before? IEPE: Yes, a lot of them. My father owned a nice comic collection. I always had some of the pictures in mind. The project "Jokers performances" (joker.iepe.net) was inspired by the comic strip "Face de lune" by Jodorowsky & Boucq. Another source of inspiration was an essay out of the book "Beyond The Brillo Box" written by the art critic Arthur C. Danto. SU: How does it work? Could you explain to us the rules of chessboxing? IEPE: In the first place we had no idea what it should be like and which rules the match should have. We had long discussions with members of the Dutch chess and boxing federations in order to develop the idea. -

October, 2007
Colorado Chess Informant YOUR COLORADOwww.colorado-chess.com STATE CHESS ASSOCIATION’S Oct 2007 Volume 34 Number 4 ⇒ On the web: http://www.colorado-chess.com Volume 34 Number 4 Oct 2007/$3.00 COLORADO CHESS INFORMANT Inside This Issue Reports: pg(s) Colorado Open 3 Jackson’s Trip to Nationals 11 CSCA Membership Meeting Minutes 22 Front Range League Report 27 Crosstables Colorado Open 3 Membership Meeting Open 10 Pike’s Peak Open 14 Pueblo Open 25 Boulder Invitational/Chess Festival 26 Games The King (of chess) and I 6 Membership Meeting Open Games 12 Pike’s Peak Games 15 The $116.67 Endgame 20 Snow White 24 Departments CSCA Info. 2 Humor 27 Club Directory 28 Colorado Tour Update 29 Tournament announcements 30 Features “How to Play Chess Like an “How to Play Chess Like an Animal” 8 Cutting Off the King 9 “How to Beat Granddad at Checkers” 11 Animal”, written by Shipp’s Log 18 BrianPage Wall 1 and Anthea Carson Colorado Chess Informant www.colorado-chess.com Oct 2007 Volume 34 Number 4 COLORADO STATE Treasurer: The Passed Pawn CHESS ASSOCIATION Richard Buchanan 844B Prospect Place CO Chess Informant Editor The COLORADO STATE Manitou Springs, CO 80829 Randy Reynolds CHESS ASSOCIATION, (719) 685-1984 INC, is a Sec. 501 (C) (3) [email protected] Greetings Chess Friends, tax-exempt, non-profit edu- cational corporation formed Members at Large: Another Colorado Open and to promote chess in Colo- Todd Bardwick CSCA membership meeting rado. Contributions are tax- (303) 770-6696 are in the history books, and deductible. -

Dressed for Success How London Is Becoming the Chess Capital of the World
Chess.May.21/4/11 21/4/11 14:51 Page 1 www.chess.co.uk Volume 76 No.2 May 2011 £3.95 UK $9.95 Canada Dressed for success How London is becoming the chess capital of the world Drunken Knights Vs Wood Green The strongest ever English League match! ChessChess andand FFootballootball Tournament Reports Amber (Blindfold + Rapid), 2011 European Championships, 4NCL Contents May 2011_Chess mag - 21_6_10 27/04/2011 17:38 Page 1 Chess Contents Chess Magazine is published monthly. Founding Editor: B.H. Wood, OBE. M.Sc † Editorial Editor: Jimmy Adams Malcolm Pein on the latest developments in chess 4 Acting Editor: John Saunders Executive Editor: Malcolm Pein European Individual Championship, Aix les Bains Subscription Rates: Vladimir Potkin headed a stellar field of GMs in Aix but the English United Kingdom competitors - professional and amateur - had their moments. 7 1 year (12 issues) £44.95 2 year (24 issues) £79.95 Problem Album 3 year (36 issues) £109.95 Colin Russ presents Werner Speckmann compositions 11 Europe 1 year (12 issues) £54.95 Melody Amber 2 year (24 issues) £99.95 The Amber light changed to red in Monte Carlo - Levon Aronian 3 year (36 issues) £149.95 had the honour of the ‘last tango in Monte Carlo’. 12 USA & Canada 1 year (12 issues) $90 4NCL British Team League 2 year (24 issues) $170 Andrew Greet reports on the fourth weekend in Daventry, with all 3 year (36 issues) $250 the contenders in their final pools. Some superb chess. 18 Rest of World (Airmail) RAC Centenary Celebration 1 year (12 issues) £64.95 2 year (24 issues) £119.95 The Royal Automobile Club celebrated its 100th birthday in style, 3 year (36 issues) £170 with ten GMs taking on 100 opponents in palatial Pall Mall. -

COOKS up a WIN in NORWAY Learn from the World Champion
GM PAL BENKO UPDATES A CLASSIC CHESS TALE August 2018 | USChess.org CARUANA COOKS UP A WIN IN NORWAY Learn from the World Champion $ Magnus Carlsen has ! ! # ! !% % Tibor Karolyi & $ (' ! ! % " # # % NEW! from the publishers of A Magazine paperback | 272 pages | $24.95 Donate to US Chess Your Tax-Deductible Contribution Will Help US Chess Grow the Game US CHESS counts on donors to support initiatives that further our mission of empowering people through chess, one move at a time. Membership dues cover the basic operating costs for US Chess. Our goals are to grow the game by funding initiatives to improve diversity in chess, sending top players to compete in international events, and growing and retaining women chess players in the game. With your support, we can elevate chess to be a game for life. Every dollar counts. Make your contribution today. uschess.org/donate www.uschess.org 1 Main office: Crossville, TN (931) 787-1234 Press and Communications Inquiries: [email protected] Advertising inquiries: (931) 787-1234, ext. 123 Tournament Life Announcements (TLAs): All TLAs should be e-mailed to [email protected] or sent to P.O. Box 3967, Crossville, TN 38557-3967 Letters to the editor: Please submit to [email protected] Receiving Chess Life: To receive Chess Life as a Premium Member, join US Chess or enter a US Chess tournament, go to uschess.org or call 1-800-903-USCF (8723) Change of address: Please send to [email protected] Other inquiries: [email protected], (931) 787-1234, fax (931) 787-1200 US CHESS US CHESS STAFF EXECUTIVE Executive Director, Carol Meyer ext. -

Fawlty Chess Towers, Weʼve Missed You by Tim Wall
Welcome back to Fawlty Chess Towers, weʼve missed you By Tim Wall “Donʼt mention the mobile phone default war. I mentioned it once, but I think I got away with it. Itʼs all forgotten now, and letʼs hear no more about it. So itʼs one Rausis omelette, a scrambled Sniper, two fried FitBit watches and a DʼCosta frappe coffee.” (John Cleese, Arbiter-at-Large, 2019 British Championships) Itʼs summertime, and that can only mean one thing; itʼs time to head to the seaside, get out your bucket, spade and Chessbase, and enter the British Championships. The 106th British, just concluded in Torquay, was for me – as I guess for a lot of people – a real roller coaster with a random mix of positive and not-so-positive emotions. Unless youʼre Mickey Adams or Jovanka Houska (congratulations on your 7th and 9th British titles, respectively, your Royal Highnesses!) there were snakes as well as ladders on and off the board at the magnificent English Riviera International Centre, or as the Devon locals affectionately call it: ERIC. In my case, there were more snakes than on a Samuel L Jackson plane to LA. Hello, embarrassing blunders. Goodbye, rating points. Oh, and an Airbnb landlady from hell, who would have given Basil Fawlty a decent run for his money as the worst hotelier in Torquay. For other players, the losses and the pain came from unexpected directions. Lorin DʼCosta, the well-liked IM and recent Olympiad coach to the England Womenʼs team, fell foul of the rules (and the prevailing mood in professional chess after the scandalous Igors Rausis cheating affair) when his opponent, ʻSniperʼ FM Charlie Storey, alerted the arbiters that DʼCosta was walking out of the playing hall with a knapsack on his back that might contain a mobile phone. -

See the Teaser Edition
orthwes $3.95 N t C h e September 2021 s s Oregon Closed Championship Oregon Closed Challengers Northwest Chess On the front cover: September 2021, Volume 75-09 Issue 884 Players from the Champions Section: (L-R):Carl Haessler, ISSN Publication 0146-6941 Champion Matt Zavortink, Nick Raptis, Zoey Tang, Cory Published monthly by the Northwest Chess Board. Russel, Konner Feldman, Wilson Gibbins, and Havish Sripada. Players from the Challengers’ Section: (L-R): Ryan To see the games online in this issue click: Richardson, Lennart Bjorksten, Darrel Bourne, David Murray, https://www.nwchess.com/articles/games/published/NWC_2021_ Ryan Lu, Karl Cosner, Austin Tang, and Jason Cigan. Published_Games_cb.htm#202109 Photo credit: Mike Morris. POSTMASTER: Send address changes to the Office of Record: Northwest Chess c/o Orlov Chess Academy 4174 148th Ave NE, Building I, Suite M, Redmond, WA 98052-5164. On the back cover: Periodicals Postage Paid at Seattle, WA “Multiple Susans” Photo credit: Philip Peterson. USPS periodicals postage permit number (0422-390) NWC Staff Editor: Jeffrey Roland, Submissions [email protected] Games Editor: Ralph Dubisch, Submissions of games (PGN format is preferable for games), [email protected] stories, photos, art, and other original chess-related content Publisher: Duane Polich, are encouraged! Multiple submissions are acceptable; please [email protected] indicate if material is non-exclusive. All submissions are Business Manager: Eric Holcomb, subject to editing or revision. Send via U.S. Mail to: [email protected] Jeffrey Roland, NWC Editor Board Representatives 1514 S. Longmont Ave. Aniruddha Barua, Eric Holcomb, Boise, Idaho 83706-3732 Alex Machin, Duane Polich, Ralph Dubisch, or via e-mail to: Jeffrey Roland, Josh Sinanan, Wilson Gibbins. -

Ocm-2018-11-01
NOVEMBER 2018 Chess News and Chess History for Oklahoma Chess Lessons from an Old Kung-Fu Movie The Big Chess Story… … this month is obviously the Carlsen-Caruana Match for the World Championship, beginning on November 9 in London. In This Issue: Games with live Internet coverage will start at • 09:00am local time. It’s the first time an Mystery of American has been in a prominent championship Chess Boxing match since Fischer, and it could have positive • effects for publicity on chess in the USA. “Oklahoma’s Official Chess Heavy Piece Here in Oklahoma, we have a WATCH PARTY Bulletin Covering Oklahoma Chess Endings event on Saturday, November 10, in Tulsa (see on a Regular Schedule Since 1982” • Upcoming Tournaments page), with big-screen IM Donaldson http://ocfchess.org TV live coverage and side events to make it fun. Book Review Oklahoma Chess Check that out! • Foundation Plus Also, this month I annotate Caruana’s impressive Register Online for Free News Bites, victory over World #3 grandmaster Shakhriyar Game of the Mamedyarov, part of an in-depth article on Editor: Tom Braunlich Month, Heavy Piece Endings. The way he outplayed Asst. Ed. Rebecca Rutledge st Puzzles, Mamedyarov in this game is impressive and Published the 1 of each month. Top 25 List, bodes well for the match. Carlsen knows now Send story submissions and Tournament that he will have his hands full, and Caruana is tournament reports, etc., by the Reports, ready and able to take him down. What will 15th of the previous month to and more. -

Chess-Boxing by Danny Maldonado & Dan Healey WGA
Chess-Boxing By Danny Maldonado & Dan Healey WGA Registered Danny A. Maldonado 61 Lexington Ave, Oyster Bay, NY 11771 - 516-864-1205 Daniel P. Healey 8420 Freemantle Dr. Colorado Springs, CO 80920 719-659-2305 FADE IN: INT. DAMIAN’S ROOM - MORNING DAMIAN RODRIGUEZ, Mid 20’s, an attractive, tan skinned man with a buzz cut lies face down on his bed. Naked, with a bed sheet barely covering his leg, he slowly awakens to the sound of knocking at his door. SEAN (knocking) Damian? Damian slowly lifts his head. He frantically feels around for something on the floor. SEAN (Still knocking) D-Rod? You okay, buddy? Damian’s hands pass from object to object on the floor. First, he grazes his college diploma, then an overturned trash can, then finally settles on a small boxed fan. SEAN MURRAY, a fragile looking man with short, light brown hair enters the room as Damian begins to puke into the fan. SEAN How ya feelin? Beige, chunky vomit sprays all over the room. Large quantities hit the ceiling, the window, and finally Sean’s face and chest. SEAN (In a dead stare) ...you fuckin’ asshole. EXT. SHOPPING CENTER - DAY Damian and Sean pull up to a quaint looking shopping center with a rather large variety of stores linked together. The largest; "G.G’s Pet Swag", a super store dedicated to the accessories and wardrobe of household pets The second largest; Jim’s Gym, a super gym complete with a spa, Olympic sized pool, and vitamin shop. (CONTINUED) CONTINUED: 2. And right in between these two mega stores sits "McDuffie’s McMovies." A decent sized video and game rental store. -

Chessboxing Organisation of India Activity Report
CHESSBOXING ORGANISATION OF INDIA ACTIVITY REPORT Sl.No. Date Event Name Venue 1. 27th Nov 2011 First Chessboxing Demo Match Kolkata, W.B. 2. 21st April 2012 Chessboxing Demo Match Coochbehar, W.B. 3. 3rd June 2012 Chessboxing Demo Match Kolkata, W.B. 4. 11-13th July 2012 National Chessboxing Training Camp Kolkata, W.B. & Seminar 5. 10-13 Jan 2013 1st National Chessboxing K.A.K KOLKATA Championship(2012-2013) 6. 5-7 April 2013 National Chessboxing Camp & C.L.W BURDWAN, W.B. referee Seminar 7. 26-28 July 2013 2nd National Chessboxing SALEM, TAMILNADU Championship (2013-2014) 8. 20th October 2013 INDIAN Team Selection for World Kolkata, W.B. Chessboxing Championship 9. 28th Nov 2013 Participate in World Chessboxing MOSCOW, RUSSIA Championship 10. 22-25 May 2014 3rd National Chessboxing JODHPUR, RAJASTHAN Championship(2014-2015) 11. 28-31st Aug 2014 International Chessboxing Camp & Kolkata, W.B. Seminar 12. 29-30 Aug 2014 1st CBOI Federation Cup Kolkata, W.B. 13. 31st Aug 2014 National Chessboxing League Kolkata, W.B. 14. 28-29 Aug 2014 National Chessboxing Camp Kolkata, W.B. 15. 21st Nov 2014 Participate in World Chessboxing Berlin, Germany Championship 16. 08th to 11th January 1st National Inter-School & College Mumbai, Maharastra 2015 Championship 17. 24th January 2015 National Referee Seminar Ernakulam, Kerala 18. 25th to 28th June 4th Senior National Championship Kolkata, W.B. 2015 19. 4th to 8th October 4th Sub-Junior & Junior National Nagpur, Maharastra 2015 Championship 20. 15th to 18th 5th Sub-Jr., Jr. & Sr. National Salem, Tamilnadu December 2016 Championship 21. -
Subject-English 07.06.2020 Class 5 Lesson 2 : Unusual Sports Dear
Subject-English 07.06.2020 Class 5 Lesson 2 : Unusual Sports Dear students, today you will get knowledge about different types of games so firstly I take following:- 1. Bossaball Bossaball was invented by a Belgian, Fllip Eyckmans, in 2004.it is played on an inflatable court with a trampoline on both side of a net. The objective in Bossaball , as in volleyball, is to ground the ball on the opponent's side of the court. The players ( three to five) can use any part of their body to get the ball over the net and into their opponent's section. Only one player is allowed on the trampoline; the others are around it. A maximum of five touches are allowed per touch. points are awarded based on where the ball falls and when it gets grounded. The first team to score 25 points win the game. The referee of the game is a samba referee who is both Master of ceremony and DJ for the sport. The height of the net can be adjusted for different levels such as adults, beginners or children. Bossaball 2. Chess Boxing Chess Boxing is a hybrid board game invented by a Dutch performer lepe Rubingh in 2003.it is now a well- loved sports in Germany, Great Britain, India and Russia. The match starts with a four minute round of chess, followed by a three minute round of boxing before returning to the chess board. It consists of 11 rounds with one minute interval between rounds. The player wear headphones for the chess round so that they don't hear advice from the audience and gloves for the boxing round. -
Arkadiusz Radwan* Chess-Boxing Around the Rule of Law – Polish Constitutionalism at Trial**
Arkadiusz Radwan* CHESS-BOXING AROUND THE RULE OF LAW – POLISH CONSTITUTIONALISM AT TRIAL** It was a chilly Sunday, in late October of san stance and indulging into political rent- 2015, when I lined up in a lengthy queue in seeking, though with varying revolutionary front of the Museum of the Warsaw Uprising zeal, as this article seeks to evidence. But it in the Polish capital. I was in the company wasn’t until the aftermath of the October 2015 of my old friend and academic master Hans- election with the power shift from the Civic Bernd Schäfer, who was visiting Poland those Platform (Platforma Obywatelska – PO) to the days. We spent roughly one hour moving Law & Justice party (Prawo i Sprawiedliwość slowly towards the Museum’s admission. This – PiS) that the wrestling around the seats in reminded my companion of a story he shared the Tribunal arose to such a level as to make with me while we awaited our turn. The headlines in Polish and international media. story was about a similar experience Hans- The alert has soon turned into a public outcry Bernd Schäfer had years earlier in Washing- and SOS for democracy in the heart of Eu- ton, where he once spent even a longer time rope. amidst American people lining up to pay a last Before getting down to the facts let’s have tribute to the late William Rehnquist, Chief a brief disclaimer: freedom and democracy are Justice of the US Supreme Court, who passed so precious, in this part of Europe, maybe more away a few days earlier. -
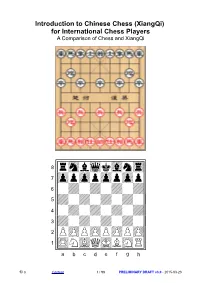
Introduction to Chinese Chess (Xiangqi) for International Chess Players a Comparison of Chess and Xiangqi
Introduction to Chinese Chess (XiangQi) for International Chess Players A Comparison of Chess and XiangQi !""""""""# çtMvWlVmT% æOoOoOoOo% å + + + +% ä+ + + + % ã + + + +% â+ + + + % ápPpPpPpP% àRnBqKbNr% /èéêëìíîï) © G Content 1 / 98 PRELIMINARY DRAFT v3.0 - 2015-03-23 Online Information Title Introduction to Chinese Chess (XiangQi) for International Chess Players Keywords Chess, Xiangqi, Comparison, Tactic, Strategy, Opening, Midgame, Endgame, Self-test, Checkmate, Rules, Piece, Board, Term, History, Software, Database Abstract While Chess is widely known and practiced all over the world Xiangqi (Chinese Chess) is popular only behind the Chinese Wall. Increasing cultural exchange between China and the western hemisphere advocates for an introduction of Xianqi to the western public, especially to people interested in mind sports like Chess. This publication takes the view of a Chess player to teach Xiangqi. Starting from the qualities of Chess, or the knowledge about Chess, the similarities of and the differences between both Chess variants are studied. All aspects of the games were compared and conclusions drawn which allow the Chess player to understand Xiangqi by applying and extending his basic, preexisting knowledge about tactics, strategy, opening, midgame and endgame. Facts about the history of Chinese characters and the history of Xiangqi dig a hole into the Chinese language wall big enough to adopt the Chinese or Asian way to record games and read Chinese game notations. The reader is invited to test his initial understanding of Xiangqi by filling in a self-test for beginners. A rating system gives feedback about areas where to improve skills. For readers who like to go further steps into Xiangqi, resources are listed like internet playsites, databases and software.