Pentest+ PT0-002 Exam Objectives
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows Poster 20-12-2013 V3
Microsoft® Discover the Open Specifications technical documents you need for your interoperability solutions. To obtain these technical documents, go to the Open Specifications Interactive Tiles: open specifications poster © 2012-2014 Microsoft Corporation. All rights reserved. http://msdn.microsoft.com/openspecifications/jj128107 Component Object Model (COM+) Technical Documentation Technical Documentation Presentation Layer Services Technical Documentation Component Object Model Plus (COM+) Event System Protocol Active Directory Protocols Overview Open Data Protocol (OData) Transport Layer Security (TLS) Profile Windows System Overview Component Object Model Plus (COM+) Protocol Active Directory Lightweight Directory Services Schema WCF-Based Encrypted Server Administration and Notification Protocol Session Layer Services Windows Protocols Overview Component Object Model Plus (COM+) Queued Components Protocol Active Directory Schema Attributes A-L Distributed Component Object Model (DCOM) Remote Protocol Windows Overview Application Component Object Model Plus (COM+) Remote Administration Protocol Directory Active Directory Schema Attributes M General HomeGroup Protocol Supplemental Shared Abstract Data Model Elements Component Object Model Plus (COM+) Tracker Service Protocol Active Directory Schema Attributes N-Z Peer Name Resolution Protocol (PNRP) Version 4.0 Windows Data Types Services General Application Services Services Active Directory Schema Classes Services Peer-to-Peer Graphing Protocol Documents Windows Error Codes ASP.NET -

IT Security Principles: Windows Exploitation
IT Security Principles: Windows Exploitation IT 444 – Network Security Understanding LLMNR and NBNS • Windows systems go through several different steps to resolve a hostname to an IP address for us. • Windows will search the hosts or LMHosts file on the system to see if there’s an entry in that file. • If there isn’t, then the next step is to query DNS. Windows will send a DNS query to the default nameserver to see if it can find an entry. • In most cases, this will return an answer, and we’ll see the web page or target host we’re trying to connect to. • In situations where DNS fails, modern Windows systems use two protocols to try to resolve. LLMNR and NetBios Understanding LLMNR and NBNS o LLMNR: this protocol uses multicast in order to try to find the host on the network. Other Windows systems will subscribe to this multicast address, and when a request is sent out by a host, if anyone listening owns that name and can turn it into an IP address, a response is generated. Once the response is received, the system will take us to the host o If the host can’t be found using LLMNR, Windows use the NetBIOS protocol to try to discover the IP. It does this by sending out a broadcast request for the host to the local subnet, and then it waits for someone to respond to that request. If a host exists with that name, it can respond directly, and then our system knows that to get to that resource, it needs to go to that location Understanding LLMNR and NBNS o Both LLMNR and NBNS rely on trust o As a malicious actor, though, we can respond to any request sent out to LLMNR or NBNS and say that the host being searched for is owned by us. -

Windows Embedded Compact 7 · User Manual Windows CE7 10.1R442 · I.MX6Q Built on October 20, 2017 Manual Revision 451 Windows CE7 10.1R442 · I.MX6 · User Manual
Windows Embedded Compact 7 · User Manual Windows CE7 10.1r442 · i.MX6Q Built on October 20, 2017 Manual revision 451 Windows CE7 10.1r442 · i.MX6 · User Manual Important hints Thank you very much for purchasing a Garz & Fricke product. Our products are dedicated to professional use and therefore we suppose extended technical knowledge and practice in working with such products. The information in this manual is subject to technical changes, particularly as a result of continuous product upgrades. Thus this manual only reflects the technical status of the products at the time of printing. Before design-in the device into your or your customer’s product, please verify that this document and the therein described specification is the latest revision and matches to the PCB version. We highly recommend contacting our technical sales team priorto any activity of that kind. A good way getting the latest information is to check the release notes of each product and/or service. Please refer to the chapter[ I 10 Related documents and online support]. The attached documentation does not entail any guarantee on the part of Garz & Fricke GmbH with respect to technical processes described in the manual or any product characteristics set out in the manual. We do not accept any liability for any printing errors or other inaccuracies in the manual unless it can be proven that we are aware of such errors or inaccuracies or that we are unaware of these as a result of gross negligence and Garz & Fricke has failed to eliminate these errors or inaccuracies for this reason. -

Information Protection Personal Computers Local Area Networks
A Short Course on Information Protection in Personal Computers and Local Area Networks by Dr. Frederick B. Cohen ASP Press FAX:412-422-4135 PO Box 81270 TEL:412-422-4134 Pittsburgh, PA 15217 USA ISBN#1-878109-14-6 Copyright c 1991, ASP ALL RIGHTS RESERVED Made in the USA by ASP Contents i 1 Introduction The proliferation of Personal Computers (PCs) and Local Area Networks (LANs) has brought about a resurgence in computer security problems that were largely solved for main- frames, and a wide variety of new problems that are specific to PC and LAN technologies. In most PCs, there are no access controls, backups are poorly managed if they are kept at all, the operating system can be accidentally corrupted, and denial of service is commonplace. In most LANs, the access controls in place can be easily violated, there is no protection against any user examining or modifying most of the network traffic, and existing controls are not adequately used. Subtle interactions between different machines on LANs can extend security problems, sometimes making even seemingly secure environments open to simplistic attacks. The purpose of this book is to explain the nature and scope of PC and LAN protection problems, describe the defenses available today and the tradeoffs in their use, and to discuss available tools for understanding the technology. 1 About the author: Dr. Cohen is widely known in computer security circles, where he has developed basic the- ory, performed ground-breaking experiments, prototyped practical solutions in widespread use, developed commercial security products for over 15 years, and provided security prod- ucts and services to organizations worldwide. -

Re-Documenting CIFS
WorWorkk IInn PrProoggresress:s: Re-DocumeRe-Documentingnting CIFSCIFS Christopher R. Hertel Storage Architect and CIFS Geek Founder and CTO www.ubiqx.com SambaXP ● April, 2009 IIntntrrooduduccttiionsons 1 IInnttrroodducuctitioonsns Who am I? Why am I here? How did I get myself into this mess? 2 IInnttrroodducuctitioonsns Where are we going? ...and what am I doing in this hand basket? 3 IInnttrroodducuctitioonsns Who am I? SamSambaba TeaTeamm mmememberber jjCCIIFFSS TeaTeamm cco-foundero-founder BrainBrain SurgSurgeeon,on, PlPlaywrite,aywrite, andand SpiSpiritrituualal HealerHealer (not really) This geek here. 4 IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new documentation... ...that covers CIFS circa 19961996. 5 IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new documentation... ...that covers CIFS circa 19961996. Yes, really. Hang on... I'll explain why this is a good thing. 6 IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new Microsoft documentation... ...that covers CIFS circa 19961996. Part of the MCPP/WSPP documentation set. On-line and available to the public. 7 IInnttrroodducuctitioonsns Why am I Here? Microsoft asked a member of the Samba Team to document SMB/CIFS! 8 IInnttrroodducuctitioonsns Why am I Here? Microsoft asked a member of the Samba Team to document SMB/CIFS “If you're surprised, you're not paying attention.” 9 IInnttrroodducuctitioonsns How did I get myself into this mess? In a word:History 10 IInnttrroodducuctitioonsns How did I get -
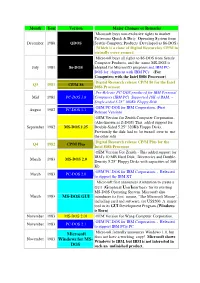
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

Microsoft Windows CE and Windows Mobile Enhanced Cryptographic
Windows Embedded CE, Windows Mobile, and Windows Embedded Compact Operating Systems Microsoft Windows CE and Windows Mobile Enhanded Cryptographic Provider 6.00.1937 and Microsoft Windows Embedded Compact Enhanced Cryptographic Provider 7.00.1687 FIPS 140-2 Documentation: Security Policy 12/4/2012 5:03:12 PM Document Version 1.2 Abstract This document specifies the security policy for the Microsoft Windows CE and Windows Mobile Enhanced Cryptographic Provider 6.00.1937 (RSAENH) and Microsoft Windows Embedded Compact Enhanced Cryptographic Provider 7.00.1687 (RSAENH) as described in FIPS PUB 140- 2. This Security Policy is non-proprietary and may be reproduced only in its original entirety (without revision) Microsoft Windows CE, Windows Mobile, Windows Embedded Compact RSAENH Security Policy 1 CONTENTS INTRODUCTION………………………………………………………………..3 SECURITY POLICY……………………………………………………………4 PLATFORM COMPATIBILITY………………………………………………6 PORTS AND INTERFACES………………………..………………………...7 SPECIFICATION OF ROLES………………………………………………..9 SPECIFICATION OF SERVICES…………………………………………..11 CRYPTOGRAPHIC KEY MANAGEMENT……………………………….21 SELF-TESTS……………………………………………………………………..25 MISCELLANEOUS………………………………………………..…………...27 This Security Policy is non-proprietary and may be reproduced only in its original entirety (without revision) Microsoft Windows Compact RSAENH Security Policy 2 INTRODUCTION Microsoft Windows CE and Windows Mobile Enhanced Cryptographic Provider (RSAENH) 6.00.1937 and Microsoft Windows Embedded Compact Enhanced Cryptographic Provider 7.00.1687 (RSAENH) is a general-purpose, software-based, cryptographic module for Windows CE, Windows Mobile, and Windows Embedded Compact. Like cryptographic providers that ship with Microsoft Windows Embedded Compact, RSAENH encapsulates several different cryptographic algorithms in an easy-to-use cryptographic module accessible via the Microsoft CryptoAPI. It can be dynamically linked into applications by software developers to permit the use of general-purpose cryptography. -

Windows Passwords: Everything You Need
WindowsWindows Passwords:Passwords: EverythingEverything YouYou NeedNeed ToTo KnowKnow JesperJesper M.M. JohanssonJohansson Enterprise Security Architect Security Business and Technology Unit Microsoft Corporation [email protected]@microsoft.com OverviewOverview HowHow passwordspasswords areare storedstored HowHow passwordspasswords areare usedused HowHow passwordspasswords areare attackedattacked PasswordPassword bestbest practicespractices HowHow WindowsWindows StoresStores PasswordsPasswords InIn thethe beginningbeginning…… PasswordPassword RepresentationsRepresentations LMLM ““hasheshashes”” OldOld technologytechnology usedused onon LANLAN ManagerManager NTNT hasheshashes A.k.a.,A.k.a., UnicodeUnicode passwordpassword oror MD4MD4 hashhash UsedUsed forfor authenticationauthentication onon moremore recentrecent WindowsWindows systemssystems CachedCached credentialscredentials DerivationDerivation ofof NTNT hashhash StoredStored UserUser NamesNames andand PasswordsPasswords CallingCalling applicationapplication decidesdecides onon representationrepresentation LMLM ““HashHash”” GenerationGeneration Padded with NULL to 14 characters Converted to upper case Separated into two 7 character strings Seattle1 = SEATTLE + 1****** Key Key Constant DESDES DESDES Constant Concatenate LM Hash LMLM ““HashHash”” ConsiderationsConsiderations ItIt’’ss notnot aa hashhash LimitedLimited charactercharacter setset CommonCommon alphanumericalphanumeric setset onlyonly CaseCase insensitiveinsensitive 142142 symbolssymbols PaddedPadded toto exactlyexactly -

More Than You Ever Wanted to Know About NT Login Authentication
A Perspective On Practical Security 2000 More Than You Ever Wanted to Know about NT Login Authentication SystemExperts Corporation Philip C. Cox & Paul B. Hill Abstract Inside The login process is the user's entry-point to the computing • Under the covers for a local NT login environment, the best or perhaps only chance for real • NT & LAN Manager compatibility authentication. No authorization decision has any meaning absent authentication. Taking the rapid adoption of NT as a given, any • Password encryption within the Security Accounts Manager organization must understand exactly how NT login authentication (SAM) database works if it is to determine whether or not NT login can meet the organization's needs. Otherwise, the choices are faith and luck. • User Authentication Process This white paper describes an Interactive NT login and lays the • Use of the LsaLogonUser API groundwork for understanding the Network login. This information is current as of NT 4.0 Service Pack 5. • The groundwork for understanding network login. NT Login Authentication SystemExperts Corporation There are no less than 5 types of “logons” in Windows NT, but only three are commonly used: Interactive, Network, and Service. Boston New York Washington D.C Tampa San Francisco Los Angeles Sacramento 1. Interactive logons are for users logging onto the console and for processes that require “interactive” access. Interactive NT Toll free (USA only): +1 888 749 9800 user authentication itself takes several forms: From outside USA: +1 978 440 9388 - Login with a locally defined user account — no network access is required; the account is authenticated by the machine you are logging into and only by that machine www.systemexperts.com [email protected] Copyright 1997-2001 SystemExperts Corporation. -

Redocumenting Historic CIFS
ReDocumenReDocumentingting HisHistorictoric CCIFSIFS Christopher R. Hertel Storage Architect and CIFS Geek Founder and CTO www.ubiqx.com SNIA Storage Developer's Conference ● September, 2009 Copyright © 2009 Christopher R. Hertel IIntntrrooduduccttiionsons Who am I? Why am I here? Where are we going? SNIA Storage Developer's Conference ● September, 2009 1 IIntntrrooduduccttiionsons ...and what am I doing in this handbasket? SNIA Storage Developer's Conference ● September, 2009 2 IInnttrroodducuctitioonsns Who am I? This geek here. SNIA Storage Developer's Conference ● September, 2009 3 IInnttrroodducuctitioonsns Who am I? Samba Team (12± years) jCIFS Co-Founder Started with SMB/CIFS circa 1990 (DEC Pathworks) SNIA Storage Developer's Conference ● September, 2009 4 IInnttrroodducuctitioonsns Who am I? I have founded a new company We do SAN and NAS consulting We are a team of geeks SNIA Storage Developer's Conference ● September, 2009 V IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new documentation... SNIA Storage Developer's Conference ● September, 2009 6 IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new documentation... ...that covers CIFS circa 19961996. SNIA Storage Developer's Conference ● September, 2009 7 IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new documentation... ...that covers CIFS circa 19961996. Yes, really. Hang on... I'll explain why this is a good thing. SNIA Storage Developer's Conference ● September, 2009 8 IInnttrroodducuctitioonsns Why am I Here? To tell you about the exciting new Microsoft documentation... ...that covers CIFS circa 19961996. Part of the MCPP/WSPP documentation set. On-line, downloadable, and available to the public. SNIA Storage Developer's Conference ● September, 2009 9 IInnttrroodducuctitioonsns Why am I Here? Microsoft asked a member of the Samba Team to document SMB/CIFS. -

Porting BSP to Wince 6.0 5Th December, 2008 System Analysis
Porting BSP to WinCE 6.0 5th December, 2008 System Analysis Porting BSP to WinCE 6.0 System Analysis Copyright 2008 CodeConcept All rights reserved Prepared by: CC Team Last update: 5th December, 2008 Revision: 1.03 Revision Description Date By 1.01 First Draft 03 October, 2008 CC Team 1.02 Device driver related details added 10 November, 2008 CC Team 1.03 Porting BSP details added 05 December, 2008 CC Team 2008 is the year that this unpublished work was originally created. CodeConcept sp. z o.o., hereinafter referred to as “CodeConcept”, owns all rights to this work and intends to maintain this work as confidential so as to maintain this work as a trade secret. CodeConcept may also seek to maintain this work as an unpublished copyright. In the event of an inadvertent or deliberate publication, CodeConcept intends to enforce its rights to this work under copyright laws as a published work. Those having access to this work may not copy, use or disclose the information in this work unless expressly authorized by CodeConcept to do so. PORTING BSP TO WINCE 6.0 - SYSTEM ANALYSIS VER 1.03 081205 CC.DOC Page 1 of 31 Porting BSP to WinCE 6.0 5th December, 2008 System Analysis Table of Contents 1. Introduction ................................................................................................................................. 4 1.1. Purpose ................................................................................................................................ 4 1.2. Scope ................................................................................................................................... -

Opensource Software Im Alltag
OpensourceOpensource SoftwareSoftware imim AlltagAlltag -- IstIst dasdas möglich?möglich? Willkommen zum Xing Stammtisch Alexander Demmler – 25.11.2016 © A. Demmler 2016 www.lacunasolutions.com 1 Marktanteile Desktop Systeme 2016 © A. Demmler 2016 www.lacunasolutions.com 2 Webserver Systeme © A. Demmler 2016 www.lacunasolutions.com 3 Einsatz von OSS in US Unternehmen: Northbridge Eine Venture Capital Company. Game changers disrupt existing markets. They also create new multi-billion dollar markets and have the potential to change the way we live and work. http://www.northbridge.com © A. Demmler 2016 www.lacunasolutions.com 4 Was bedeutet OpenSource? • OpenSource Software (OSS) ist professionelle Software unter einer alternativen Entwicklungs- und Vertriebsform • OpenSource ist nicht Linux - aber Linux ist auch OpenSource! • OpenSource bedeutet ein Stück Freiheit: - freie Auswahl - Freiheit ob und wieviel man bezahlt - Freiheit in der Nutzung © A. Demmler 2016 www.lacunasolutions.com 5 Was ist die Community? • Die Community besteht aus - Entwicklern + Beratern + Anwendern + Hobbyisten - grossen Unternehmen (HP, IBM, SUN) - Distributoren wie SUSE, RedHat, Ubuntu u.a. • Die Community entwickelt und pflegt gemeinsam die Software und bietet Unterstützung (Support) • Die Community ist kein Club von Hackern, Freaks und anderen Bösewichten! © A. Demmler 2016 www.lacunasolutions.com 6 Das Geschäftsmodell Freie Software Dienstleistungen (Kosten) Basis Version Erweiterungen Download im WWW Service + Support Online Support Schulungen Zusatzeinkünfte Werbung + Sponsoren © A. Demmler 2016 www.lacunasolutions.com 7 Lizenzrechtliches • Softwarecode (Quellen) sind offen gelegt: - Verbreitung und Nutzung sind ausdrücklich erlaubt - Veränderung (Anpassung, Erweiterung) erlaubt - Quellcode muss offengelegt werden • Es gibt historisch bedingt verschiedene Lizenzmodelle. (GPL, OSL, CPL, EPL u.a) • EU Initiative um Lizenzen vereinen: http://ec.europa.eu ACHTUNG: Auch hier gelten Vorschriften! Computerwoche: http://www.computerwoche.de © A.