Mitigating Pass-The-Hash and Other Credential Theft, Version 2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Word Processing Tool
WORD PROCESSING 3 TOOL Objectives I like the computer because it keeps giving you After completing this Chapter, the options. What if I do this? You try it, and if you student will be able to: don't like it you undo it. The original can always be resurrected. It raises the idea of working on • work with any word processing program, one painting your whole life, saving it and working on it again and again. • create, save and open a Elliott Green document using a word Research Associate and Tutorial Fellow, Oxford University processor, • format a document inserting bullets/numbering, tables, pictures, etc., Introduction • set custom tabs and apply styles, We have to submit a project as part of our course • prepare a document for printing, evaluation. We will perhaps take a chart paper • enhance the features of the and design the project, write a report and submit document inserting graphics, it to our teacher. That’s the way we have done it tables, pictures, charts, etc., and all along? Have we ever thought of typing the entire using different formatting styles, project report using a computer and submitting it • modify document using various in a nicely designed printed form? Ever reflected editing and formatting features on getting information from the Internet and within or across documents, presenting it neatly for the project? Now that’s • produce documents for various the way things are being done! And if we are already purposes and thinking of it, it’s time to discover some document creation software, i.e., word processing tool to get • apply mail merge facility to send a document to different the job done. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Pass-The-Hash Attacks
Pass-the-Hash Attacks Michael Grafnetter www.dsinternals.com Agenda . PtH Attack Anatomy . Mitigation – Proactive – Reactive . Windows 10 + Windows Server 2016 PtH History and Future . 1988 – Microsoft releases Lan Manager . 1997 – Pass-the-Hash demonstrated using a modified Samba . 2007 – Benjamin Delpy releases Mimikatz . 2008 – Pass-the-Ticket attack demonstrated . 2012 – Microsoft releases Pass-the-Hash guidance . 2013 – Windows contains built-in defenses against PtH . 2015 – Michael Grafnetter releases the DSInternals tools ;-) . 2016 – More defense mechanisms coming to Windows PtH Attack Anatomy Theft Use Compromise Lateral and Vertical Movement Metasploit Framework Metasploit Framework Mimikatz DEMO Pass-the-Hash + RDP LSASS NTLM Hashes Passing the Hash PtH Attack Premises Single Symmetric Pass-the-Hash Sign-On Cryptography Attack Surface Stealing the Hash Credentials Lifecycle / Attack Vectors Credentials Lifecycle / Attack Vectors Hashes in SAM/AD Authentication Method Hash Function Salted LM DES NO NTLM, NTLMv2 MD4 NO Kerberos (RC4) MD4 NO Kerberos (AES) PBKDF2 (4096*HMAC_SHA1) YES Digest MD5 YES Active Directory Database - Offline . Files – C:\Windows\NTDS\ntds.dit – C:\Windows\System32\config\SYSTEM . Acquire – Locally: ntdsutil IFM – Remotely: WMI (Win32_Process), psexec – Offline: VHDs, VMDKs, Backups . Extract – Windows: DSInternals PowerShell Module – Linux: NTDSXtract DEMO Extracting hashes from ntds.dit GUI Tools KRBTGT Account Proactive Measures . Encryption . RODC . Backup protection . Regular password changes Active Directory Database - Online . MS-DRSR/RPC Go to www.dsinternals.com for demo ;-) Proactive Measures . Avoid using administrative accounts . Do not run untrusted SW . Do not delegate the right to replicate directory changes . Use an application firewall / IDS ??? SAM Database . Offline – Files • C:\Windows\System32\config\SAM • C:\Windows\System32\config\SYSTEM – Tools • Windows Password Recovery . -

Administrative Guide for Windows 10 and Windows Server Fall Creators Update (1709)
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1903 (May 2019 Update) General Purpose Operating System Protection Profile © 2019 Microsoft. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -
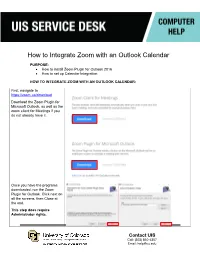
How to Integrate Zoom with an Outlook Calendar
How to Integrate Zoom with an Outlook Calendar PURPOSE: • How to install Zoom Plugin for Outlook 2016 • How to set up Calendar Integration HOW TO INTEGRATE ZOOM WITH AN OUTLOOK CALENDAR: First, navigate to https://zoom.us/download Download the Zoom Plugin for Microsoft Outlook, as well as the zoom client for Meetings if you do not already have it. Once you have the programs downloaded, run the Zoom Plugin for Outlook. Click next on all the screens, then Close at the end. This step does require Administrator rights. Contact UIS Call: (303) 860-4357 Email: [email protected] Restart Outlook, then you will see it in the top menu. Next, navigate to https://cusystem.zoom.us, choose SSO and login with your CU credentials Contact UIS Call: (303) 860-4357 Email: [email protected] On the left side, choose My Meeting Settings Under My Meeting Settings, scroll down until you find Calendar Integration. Click the toggle on the right side. Under Calendar Integration, for the Exchange login username or UPN enter your CU username followed by @ad.cu.edu. Under password, enter your CU password. For Exchange version, select Exchange 2013. In the EWS URL, enter https://exchange.cu.edu/ EWS/Exchange.asmx After that, click Authorize and you should be set! Keep in mind this isn’t a perfect integration, it will only create new meetings for meetings created after this has been done, and changing or deleting meetings will not necessarily reflect in Outlook. The Zoom desktop client will be the best place to check for updated meetings. -

Supporting Operating System Installation | 3
cc01SupportingOperatingSystemInstallation.indd01SupportingOperatingSystemInstallation.indd PagePage 1 08/10/1408/10/14 4:334:33 PMPM martinmartin //208/WB01410/XXXXXXXXXXXXX/ch01/text_s208/WB01410/XXXXXXXXXXXXX/ch01/text_s Supporting Operating LESSON 1 System Installation 70-688 EXAM OBJECTIVE Objective 1.1 – Support operating system installation. This objective may include but is not limited to: Support Windows To Go; manage boot settings, including native virtual hard disk (VHD) and multi-boot; manage desktop images; customize a Windows installation by using Windows Preinstallation Environment (PE). LESSON HEADING EXAM OBJECTIVE Using a Troubleshooting Methodology Viewing System Information Using the Event Viewer Supporting Windows To Go Support Windows To Go Creating and Deploying a Windows To Go Workspace Drive Booting into a Windows To Go Workspace Managing Boot Settings Manage boot settings, including native virtual hard disk (VHD) and multi-boot Using BCDEdit and BCDBoot Configuring a Multi-Boot System Manage boot settings, including native virtual hard disk (VHD) and multi-boot Configuring a Native VHD Boot File Manage boot settings, including native virtual hard disk (VHD) and multi-boot Understanding VHD Formats Installing Windows 8.1 on a VHD with an Operating System Present Installing Windows 8.1 on a VHD Without an Operating SystemCOPYRIGHTED Present MATERIAL Managing Desktop Images Manage desktop images Capturing Images Modifying Images using DISM Customizing a Windows Installation by Using Windows PE Customize a Windows -

Windows 7 Bitlocker™ Drive Encryption Security Policy for FIPS 140-2 Validation
Windows 7 BitLocker™ Security Policy Page 1 of 16 Windows 7 BitLocker™ Drive Encryption Security Policy For FIPS 140-2 Validation For Windows 7 Document version 1.0 08/31/2011 1. Table of Contents 1. TABLE OF CONTENTS ......................................................................................................................... 1 2. INTRODUCTION .................................................................................................................................. 2 2.1 List of Cryptographic Modules ........................................................................................................................... 2 2.2 Brief Module Description ................................................................................................................................... 3 2.3 Validated Platforms ........................................................................................................................................... 4 3. INTEGRITY CHAIN OF TRUST .......................................................................................................... 4 4. CRYPTOGRAPHIC BOUNDARIES ..................................................................................................... 5 4.1 Overall Cryptographic Boundary........................................................................................................................ 5 4.2 BitLocker™ Components Included in the Boundary .......................................................................................... 5 4.3 Other Windows -

System Requirements
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/officescan.aspx Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2017 Trend Micro Incorporated. All rights reserved. Release Date: October 2017 Protected by U.S. Patent No. 5,623,600; 5,889,943; 5,951,698; 6,119,165 Table of Contents Chapter 1: OfficeScan Server Installations Fresh Installations on Windows Server 2008 R2 Platforms .............................................................................................................................................................................. 1-2 Fresh Installations on Windows Server 2012 Platforms ..................................................................................................................................................................................... 1-3 Fresh Installations on Windows Server 2016 Platforms ..................................................................................................................................................................................... 1-4 Fresh Installations -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism. -

Office 365 Exchange Online Using Powershell
Relay Calendar Setup 1 Create a new room mailbox resource. If your room already has a calendar, you can skip this step. a. Log in to the Microsoft 365 admin center. b. Go to Resources › Rooms & equipment. c. Select + Add a resource mailbox. d. Fill out the New Resource form. This guide will assume an email address of [email protected]. No license is needed for the resource. e. Click Save. 2 Connect to Office 365 Exchange Online using PowerShell. This will let you configure room resource calendars in the next step. a. Allow signed scripts by opening Windows PowerShell as an administrator and running Set-ExecutionPolicy RemoteSigned b. Open a non-admin Windows PowerShell and log in by running $UserCredential = Get-Credential $Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https:// outlook.office365.com/powershell-liveid/ -Credential $UserCredential -Authentication Basic -AllowRedirection Import-PSSession $Session For more information, refer to the Exchange Online PowerShell documentation. 3 Create a distribution group for your rooms. This restricts Relay to only read specific calendars in your organization. a. Create the group. New-DistributionGroup -Name bluejeans-relay -Type Security -Notes "Rooms from which Relay can read calendars." b. Grant the Relay app access to the group. New-ApplicationAccessPolicy -AppId 5a75b6b1-f653-40b1-ab48-6ec9cea91b36 -PolicyScopeGroupId bluejeans-relay -AccessRight RestrictAccess -Description "Relay can only read calendars from mailboxes in this group." If you get a CommandNotFoundException, or if only your user appears in Get-Mailbox, then log in to Exchange Online Powershell as an admin. 4 Share the calendar with Relay. Do not skip this. -

Windows Poster 20-12-2013 V3
Microsoft® Discover the Open Specifications technical documents you need for your interoperability solutions. To obtain these technical documents, go to the Open Specifications Interactive Tiles: open specifications poster © 2012-2014 Microsoft Corporation. All rights reserved. http://msdn.microsoft.com/openspecifications/jj128107 Component Object Model (COM+) Technical Documentation Technical Documentation Presentation Layer Services Technical Documentation Component Object Model Plus (COM+) Event System Protocol Active Directory Protocols Overview Open Data Protocol (OData) Transport Layer Security (TLS) Profile Windows System Overview Component Object Model Plus (COM+) Protocol Active Directory Lightweight Directory Services Schema WCF-Based Encrypted Server Administration and Notification Protocol Session Layer Services Windows Protocols Overview Component Object Model Plus (COM+) Queued Components Protocol Active Directory Schema Attributes A-L Distributed Component Object Model (DCOM) Remote Protocol Windows Overview Application Component Object Model Plus (COM+) Remote Administration Protocol Directory Active Directory Schema Attributes M General HomeGroup Protocol Supplemental Shared Abstract Data Model Elements Component Object Model Plus (COM+) Tracker Service Protocol Active Directory Schema Attributes N-Z Peer Name Resolution Protocol (PNRP) Version 4.0 Windows Data Types Services General Application Services Services Active Directory Schema Classes Services Peer-to-Peer Graphing Protocol Documents Windows Error Codes ASP.NET -

Microsoft Windows Server 2012 R2
MICROSOFT WINDOWS SERVER 2012 R2 APPLICATION-FOCUSED SERVICES TOP 3 BENEFITS Windows Server 2012 R2 enables you to build and deploy applications in your data center that utilize higher-level, ❒4 Comprehensive Cloud Platform cloud-based application services and APIs that are ❒4 Cost Savings and Increased Efficiencies compatible with service provider clouds and Windows Azure. This functionality provides improved application ❒4 Support for a Modern Work Style portability between on-premises, public and partner- hosted clouds, increasing the flexibility and elasticity of your IT services. OPTIMIZE YOUR CLOUD BUSINESS Windows Server 2012 R2 also provides frameworks, With the world of IT changing rapidly, traditional services and tools to increase scalability and elasticity approaches to solving infrastructure problems are for multitenant-aware applications and websites. inadequate. The Microsoft vision for this new era of IT is to provide one consistent platform for infrastructure, apps, and data: the Cloud OS. The Cloud OS spans customer data centers, service provider data centers and the Microsoft PEOPLE WHO GET IT public cloud. At the heart of the solution is Windows Server 2012 R2. With Windows Server 2012 R2, you gain Along with your dedicated account manager, an enterprise-grade platform to cost-effectively optimize CDW has Microsoft trained and certified your business with a cloud. experts who can help find the right data center technologies for you, including: SIMPLE AND COST-EFFECTIVE DESIGN Windows Server 2012 R2 enables you to blend your Professional Services: on-premises solutions with the cloud without having • 500 engineers and project managers, to reengineer infrastructure, systems management or including 90+ Microsoft engineers applications.