More Than You Ever Wanted to Know About NT Login Authentication
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mac OS X Server Administrator's Guide
034-9285.S4AdminPDF 6/27/02 2:07 PM Page 1 Mac OS X Server Administrator’s Guide K Apple Computer, Inc. © 2002 Apple Computer, Inc. All rights reserved. Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. RealAudio is a trademark of Progressive Networks, Inc. © 1995–2001 The Apache Group. All rights reserved. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 062-9285/7-26-02 LL9285.Book Page 3 Tuesday, June 25, 2002 3:59 PM Contents Preface How to Use This Guide 39 What’s Included -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -

11.7 the Windows 2000 File System
830 CASE STUDY 2: WINDOWS 2000 CHAP. 11 11.7 THE WINDOWS 2000 FILE SYSTEM Windows 2000 supports several file systems, the most important of which are FAT-16, FAT-32, and NTFS (NT File System). FAT-16 is the old MS-DOS file system. It uses 16-bit disk addresses, which limits it to disk partitions no larger than 2 GB. FAT-32 uses 32-bit disk addresses and supports disk partitions up to 2 TB. NTFS is a new file system developed specifically for Windows NT and car- ried over to Windows 2000. It uses 64-bit disk addresses and can (theoretically) support disk partitions up to 264 bytes, although other considerations limit it to smaller sizes. Windows 2000 also supports read-only file systems for CD-ROMs and DVDs. It is possible (even common) to have the same running system have access to multiple file system types available at the same time. In this chapter we will treat the NTFS file system because it is a modern file system unencumbered by the need to be fully compatible with the MS-DOS file system, which was based on the CP/M file system designed for 8-inch floppy disks more than 20 years ago. Times have changed and 8-inch floppy disks are not quite state of the art any more. Neither are their file systems. Also, NTFS differs both in user interface and implementation in a number of ways from the UNIX file system, which makes it a good second example to study. NTFS is a large and complex system and space limitations prevent us from covering all of its features, but the material presented below should give a reasonable impression of it. -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Windows Poster 20-12-2013 V3
Microsoft® Discover the Open Specifications technical documents you need for your interoperability solutions. To obtain these technical documents, go to the Open Specifications Interactive Tiles: open specifications poster © 2012-2014 Microsoft Corporation. All rights reserved. http://msdn.microsoft.com/openspecifications/jj128107 Component Object Model (COM+) Technical Documentation Technical Documentation Presentation Layer Services Technical Documentation Component Object Model Plus (COM+) Event System Protocol Active Directory Protocols Overview Open Data Protocol (OData) Transport Layer Security (TLS) Profile Windows System Overview Component Object Model Plus (COM+) Protocol Active Directory Lightweight Directory Services Schema WCF-Based Encrypted Server Administration and Notification Protocol Session Layer Services Windows Protocols Overview Component Object Model Plus (COM+) Queued Components Protocol Active Directory Schema Attributes A-L Distributed Component Object Model (DCOM) Remote Protocol Windows Overview Application Component Object Model Plus (COM+) Remote Administration Protocol Directory Active Directory Schema Attributes M General HomeGroup Protocol Supplemental Shared Abstract Data Model Elements Component Object Model Plus (COM+) Tracker Service Protocol Active Directory Schema Attributes N-Z Peer Name Resolution Protocol (PNRP) Version 4.0 Windows Data Types Services General Application Services Services Active Directory Schema Classes Services Peer-to-Peer Graphing Protocol Documents Windows Error Codes ASP.NET -

When Windows 2000 Or Windows Server 2003 Is Introduced
IMPORTANT INFORMATION FOR PRIMERGY CUSTOMERS July 11th, 2007 FUJITSU, LTD. NOTICE: Any server using an Intel Xeon 7100 or higher model CPU and has either Windows 2000, Windows 2000 Server, or Windows 2003 Server installed may encounter a “blue screen.” The problem occurs when the operating system running on a computer with a fast processor and a large L3 cache encounters a timing problem with asynchronous hardware. Although Fujitsu has not received any reports of this problem to date, there is a possibility that PRIMERGY server products may be affected. Problem: Any computer running any edition of Windows 2000, Windows 2000 Server, or Windows 2003 with an Intel Xeon processor (model 7100 or higher) that utilizes a large L3 cache may generate a “blue screen.” An error similar to: STOP 0x0000008E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED or STOP 0x0000001E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED may be displayed with Windows 2003-based and Windows 2000-based computers, respectively. Affected Operating Systems: Microsoft® Windows® 2000 Server Microsoft® Windows® 2000 Advanced Server Microsoft® Windows Server® 2003, Standard Edition (*) Microsoft® Windows Server® 2003, Enterprise Edition (*) (*)This problem has been corrected in Service Pack 1 for Windows Server 2003. Therefore Windows 2003 Server SP1 is not affected by this problem. Affected Fujitsu PRIMERGY models: The following models use Intel Xeon 7100 or higher processors. PRIMERGY Models, Product Codes, and CPU z PRIMERGY RX600 S3 (SAS), Product codes PGR603D* and PGR603B* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) z PRIMERGY RX600 S3, Product codes PGR6038* and PGR6036* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) * Changes by type. -
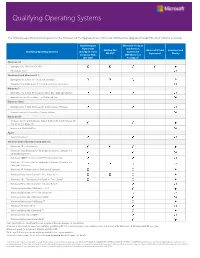
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 2000 Accessibility Options
© 2004 Microsoft Corporation Step By Step Tutorials for Microsoft® Windows 2000 Accessibility Options Step by Step Tutorials for Microsoft Windows 2000 Accessibility Options Table of Contents Overview .................................................................................................................................. 4 Using the Accessibility Wizard ............................................................................................... 6 Opening Accessibility Wizard ............................................................................................... 7 Changing the Font Size of Text on the Screen ...................................................................... 9 Switching to a Lower Screen Resolution to Increase the Size of Items on the Screen ....... 10 Changing the Size of Items on the Screen ........................................................................... 11 Disabling Personalized Menus ............................................................................................ 13 Setting Options for People Who Are Blind or Have Difficulty Seeing Things on the Screen ............................................................................................................................................. 14 Setting Options for People Who Are Deaf or Have Difficulty Hearing Sounds from the Computer ............................................................................................................................. 16 Setting Options for People Who Have Difficulty Using the Keyboard -

IT Security Principles: Windows Exploitation
IT Security Principles: Windows Exploitation IT 444 – Network Security Understanding LLMNR and NBNS • Windows systems go through several different steps to resolve a hostname to an IP address for us. • Windows will search the hosts or LMHosts file on the system to see if there’s an entry in that file. • If there isn’t, then the next step is to query DNS. Windows will send a DNS query to the default nameserver to see if it can find an entry. • In most cases, this will return an answer, and we’ll see the web page or target host we’re trying to connect to. • In situations where DNS fails, modern Windows systems use two protocols to try to resolve. LLMNR and NetBios Understanding LLMNR and NBNS o LLMNR: this protocol uses multicast in order to try to find the host on the network. Other Windows systems will subscribe to this multicast address, and when a request is sent out by a host, if anyone listening owns that name and can turn it into an IP address, a response is generated. Once the response is received, the system will take us to the host o If the host can’t be found using LLMNR, Windows use the NetBIOS protocol to try to discover the IP. It does this by sending out a broadcast request for the host to the local subnet, and then it waits for someone to respond to that request. If a host exists with that name, it can respond directly, and then our system knows that to get to that resource, it needs to go to that location Understanding LLMNR and NBNS o Both LLMNR and NBNS rely on trust o As a malicious actor, though, we can respond to any request sent out to LLMNR or NBNS and say that the host being searched for is owned by us. -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Windows Embedded Compact 7 · User Manual Windows CE7 10.1R442 · I.MX6Q Built on October 20, 2017 Manual Revision 451 Windows CE7 10.1R442 · I.MX6 · User Manual
Windows Embedded Compact 7 · User Manual Windows CE7 10.1r442 · i.MX6Q Built on October 20, 2017 Manual revision 451 Windows CE7 10.1r442 · i.MX6 · User Manual Important hints Thank you very much for purchasing a Garz & Fricke product. Our products are dedicated to professional use and therefore we suppose extended technical knowledge and practice in working with such products. The information in this manual is subject to technical changes, particularly as a result of continuous product upgrades. Thus this manual only reflects the technical status of the products at the time of printing. Before design-in the device into your or your customer’s product, please verify that this document and the therein described specification is the latest revision and matches to the PCB version. We highly recommend contacting our technical sales team priorto any activity of that kind. A good way getting the latest information is to check the release notes of each product and/or service. Please refer to the chapter[ I 10 Related documents and online support]. The attached documentation does not entail any guarantee on the part of Garz & Fricke GmbH with respect to technical processes described in the manual or any product characteristics set out in the manual. We do not accept any liability for any printing errors or other inaccuracies in the manual unless it can be proven that we are aware of such errors or inaccuracies or that we are unaware of these as a result of gross negligence and Garz & Fricke has failed to eliminate these errors or inaccuracies for this reason. -

Bulletin Board System (BBS) for a VAX/VMS Multi-User Environment
- Bulletin Board System (BBS) for a VAX/VMS Multi-User Environment An Honors Thesis (HONRS 499) by J. Kevin Cooper Advisor: Dr. Earl H. McKinney Ball State University Muncie, Indiana May 1995 Graduation Date: May 6, 1995 - Abstract Overview The BBS (Bulletin Board System) software is a client/server model running on a VAX/VMS com puter system, which allows both interactive, user-friendly access to file bases and online discussion groups, and a versatile database environment with comprehensive security features. This system has been tailored to be platform-independent in its information transfer protocol, while using the specifics of the operating system to benefit both the appearance of the user interface and the efficiency of database m anagem ent. I have attempted to interweave as much functionality as feasibly possible into this project, as to demonstrate what I have learned through the Computer Science program here at Ball State University, as well as through my internship position as a VAX system technician and programmer S.t University Computing Services. Tools Used This project was written using the following software on University-owned VAX machines: DEC Pascal v4.2 for VMS DEC set Module M anagem ent System v2.5 MultiNet -v3.2 shareable TCPIIP network library Open VMS VAX Operating System v6.0, v6.1 This system makes use of system resources such as the VMS Command Language Interpreter (CLI), VMS Message Utility, Run-time Screen Manager Library (SMG), Record Management Services (RM8), and MultiNet's linkable TCP/IP socket library. Acknowledgem ents I would like to thank Dr.