Windows Powershell 2 for Dummies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

KDE 2.0 Development, Which Is Directly Supported
23 8911 CH18 10/16/00 1:44 PM Page 401 The KDevelop IDE: The CHAPTER Integrated Development Environment for KDE by Ralf Nolden 18 IN THIS CHAPTER • General Issues 402 • Creating KDE 2.0 Applications 409 • Getting Started with the KDE 2.0 API 413 • The Classbrowser and Your Project 416 • The File Viewers—The Windows to Your Project Files 419 • The KDevelop Debugger 421 • KDevelop 2.0—A Preview 425 23 8911 CH18 10/16/00 1:44 PM Page 402 Developer Tools and Support 402 PART IV Although developing applications under UNIX systems can be a lot of fun, until now the pro- grammer was lacking a comfortable environment that takes away the usual standard activities that have to be done over and over in the process of programming. The KDevelop IDE closes this gap and makes it a joy to work within a complete, integrated development environment, combining the use of the GNU standard development tools such as the g++ compiler and the gdb debugger with the advantages of a GUI-based environment that automates all standard actions and allows the developer to concentrate on the work of writing software instead of managing command-line tools. It also offers direct and quick access to source files and docu- mentation. KDevelop primarily aims to provide the best means to rapidly set up and write KDE software; it also supports extended features such as GUI designing and translation in con- junction with other tools available especially for KDE development. The KDevelop IDE itself is published under the GNU Public License (GPL), like KDE, and is therefore publicly avail- able at no cost—including its source code—and it may be used both for free and for commer- cial development. -

CD Player / Cassette Deck
D01310420B CD-A580 CD Player / Cassette Deck OWNER’S MANUAL IMPORTANT SAFETY INSTRUCTIONS 10) Protect the power cord from being walked on or pinched par- ticularly at plugs, convenience receptacles, and the point where they exit from the apparatus. 11) Only use attachments/accessories specified by the manufacturer. CAUTION: TO REDUCE THE RISK OF ELECTRIC SHOCK, 12) Use only with the cart, stand, tripod, bracket, DO NOT REMOVE COVER (OR BACK). NO USER- or table specified by the manufacturer, or SERVICEABLE PARTS INSIDE. REFER SERVICING TO sold with the apparatus. When a cart is QUALIFIED SERVICE PERSONNEL. used, use caution when moving the cart/ apparatus combination to avoid injury from The lightning flash with arrowhead symbol, within an tip-over. < equilateral triangle, is intended to alert the user to the 13) Unplug this apparatus during lightning storms or when unused presence of uninsulated “dangerous voltage” within the for long periods of time. product’s enclosure that may be of sufficient magnitude 14) Refer all servicing to qualified service personnel. Servicing is to constitute a risk of electric shock to persons. required when the apparatus has been damaged in any way, such as power-supply cord or plug is damaged, liquid has been The exclamation point within an equilateral triangle is spilled or objects have fallen into the apparatus, the apparatus intended to alert the user to the presence of important B has been exposed to rain or moisture, does not operate normally, operating and maintenance (servicing) instructions in or has been dropped. the literature accompanying the appliance. o The apparatus draws nominal non-operating power from the WARNING: TO PREVENT FIRE OR SHOCK HAZARD, AC outlet with its POWER or STANDBY/ON switch not in the ON DO NOT EXPOSE THIS APPLIANCE TO RAIN OR position. -

Windows Shell Action Command Library
Windows Shell Action Command Library A Guide to the BigFix® Action Shell Commands BigFix, Inc. Emeryville, CA Last Modified: May 27, 2003 Compatible with BigFix Enterprise Suite (BES) version 3.0 and BigFix Consumer Client version 1.7 ii © 1998–2003 BigFix, Inc. All rights reserved. BigFix®, Fixlet® and "Fix it before it fails"® are registered trademarks of BigFix, Inc. i- prevention, Powered by BigFix, Relevance Engine, and related BigFix logos are trademarks of BigFix, Inc. All other product names, trade names, trademarks, and logos used in this documentation are the property of their respective owners. BigFix’s use of any other company’s trademarks, trade names, product names and logos or images of the same does not necessarily constitute: (1) an endorsement by such company of BigFix and its products, and (2) an endorsement of the company or its products by BigFix. No part of this documentation may be reproduced, transmitted, or otherwise distributed in any form or by any means (electronic or otherwise) without the prior written consent of BigFix, Inc. You may not use this documentation for any purpose except in connection with your use or evaluation of BigFix software and any other use, including for reverse engineering such software or creating compatible software, is prohibited. If the license to the software which this documentation accompanies is terminated, you must immediately return this documentation to BigFix, Inc. and destroy all copies you may have. All inquiries regarding the foregoing should be addressed to: BigFix, Inc. 5915 Hollis Street Emeryville, CA 94608-2017 Copyright © 2003 by BigFix, Inc. -
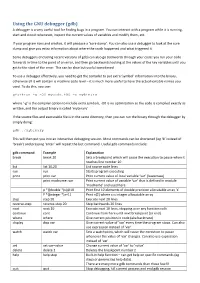
Using the GNU Debugger (Gdb) a Debugger Is a Very Useful Tool for Finding Bugs in a Program
Using the GNU debugger (gdb) A debugger is a very useful tool for finding bugs in a program. You can interact with a program while it is running, start and stop it whenever, inspect the current values of variables and modify them, etc. If your program runs and crashes, it will produce a ‘core dump’. You can also use a debugger to look at the core dump and give you extra information about where the crash happened and what triggered it. Some debuggers (including recent versions of gdb) can also go backwards through your code: you run your code forwards in time to the point of an error, and then go backwards looking at the values of the key variables until you get to the start of the error. This can be slow but useful sometimes! To use a debugger effectively, you need to get the compiler to put extra ‘symbol’ information into the binary, otherwise all it will contain is machine code level – it is much more useful to have the actual variable names you used. To do this, you use: gfortran –g –O0 mycode.f90 –o mybinary where ‘-g’ is the compiler option to include extra symbols, -O0 is no optimization so the code is compiled exactly as written, and the output binary is called ’mybinary’. If the source files and executable file is in the same directory, then you can run the binary through the debugger by simply doing: gdb ./mybinary This will then put you into an interactive debugging session. Most commands can be shortened (eg ‘b’ instead of ‘break’) and pressing ‘enter’ will repeat the last command. -

User's Manual
PSC User’s Manual 703703 Philips Consumer Electronics Company A Division of Philips Electronics North America Corporation Knoxville, TN 37914-1810, U.S.A. Printed in the U.S.A. 703_rhythmic_usermanual.qxd 3/12/01 10:30 AM Page 1 Philips Rhythmic Edge™ 4-Channel PCI Sound Card PSC703 ____________________________ Philips Consumer Electronics Company One Philips Drive Knoxville,TN 37914 Revised 03/9/01 703_rhythmic_usermanual.qxd 3/12/01 10:30 AM Page 2 SOFTWARE END USER LICENSE AGREEMENT PLEASE READ THE FOLLOWING TERMS AND CONDITIONS CAREFULLY. If you (end user, either an entity or an individual) do not agree with these terms and conditions do not install the software.This End User License Agreement is a contract between you and Philips Consumer Electronics B.V, including its suppliers and licensors (“Philips”) for this software program Philips Rhythmic Edge™ (“Licensed Software”). By installing the Licensed Software or using the Licensed Software you agree to and accept the terms and conditions of this End User License Agreement. YOU AGREE THAT YOUR USE OF THE LICENSED SOFTWARE ACKNOWLEDGES THAT YOU HAVE READ THIS END USER LICENSE AGREEMENT, UNDERSTAND IT,AND AGREE TO BE 4-Channel PCI Sound Card BOUND BY ITS TERMS AND CONDITIONS: 1. Copyright © Copyright 2000 The Licensed Software is a proprietary product of Philips, and is protected by copyright laws.Title, ownership rights and intellectual property rights in and to the Licensed Software shall remain with Philips. 2. Right to use Rhythmic Edge™ is a trademark of Philips Consumer Electronics Philips hereby grants you the personal, non-exclusive license to use the Licensed Software only on and in conjunction with one (1) computer at one time.You may not sell, rent, redistribute, sublicense or lease the Licensed Software, or otherwise transfer or assign the right to use it.You may not decompile, disassemble, reverse engineer, or in any way ThunderBird Avenger™ is a trademark of Philips Semiconductors modify program code, except where this restriction is expressly prohibited by applicable law. -

User Manual W
ifu_az1816_apac_eng 2006.8.22 5:44 PM Page 1 MP3-CD Soundmachine AZ1816 Meet Philips at the Internet http://www.philips.com User Manual W AZ1816 CLASS 1 LASER PRODUCT Printed in China PDCC-JH-0630 ifu_az1816_apac_eng 2006.8.22 5:44 PM Page 2 Connecting USB 1 1 2 3 4 0 5 ! 6 @ # 7 $ 8 % 9 ^ & ) * USB mass ( storage device 6xR14•UM-2•C-CELLS USB cable ifu_az1816_apac_eng 2006.8.22 5:44 PM Page 3 2 8 Hearing Safety Listen at a moderate volume. • Using headphones at a high volume can impair your hearing. This product can produce sounds in 3 9 decibel ranges that may cause hearing loss for a normal person, even for exposure less than a minute. The higher decibel ranges are offered for those that may have already experienced some USB DIRECT hearing loss. • Sound can be deceiving. Over time your hearing "comfort level" adapts to higher volumes of sound. So after prolonged listening, what sounds "normal" can actually be loud and harmful to your hearing. To guard against this, set your volume to a safe level before your hearing adapts and leave it there. 4 To establish a safe volume level: • Set your volume control at a low setting. • Slowly increase the sound until you can hear it comfortably and clearly, without distortion. Listen for reasonable periods of time: • Prolonged exposure to sound, even at normally "safe" levels, can also cause hearing loss. • Be sure to use your equipment reasonably and take appropriate breaks. Be sure to observe the following guidelines when using your headphones. -

Guidelines for Designing Embedded Systems with Windows 10 Iot Enterprise
Guidelines for Designing Embedded Systems with Windows 10 IoT Enterprise Version 2.0 Published July 15, 2016 Guidelines for designing embedded systems 1 CONFIDENTIAL Contents Overview .................................................................................................................................................................................................... 4 Building a task-specific experience ............................................................................................................................................ 4 General Group Policy settings ....................................................................................................................................................... 4 Application control ................................................................................................................................................................................ 5 Application boot options ................................................................................................................................................................. 5 Auto-boot Universal Windows apps ...................................................................................................................................... 5 Auto-boot Classic Windows apps ........................................................................................................................................... 5 Limit application access with AppLocker ............................................................................................................................... -

3Dp-V264gt/Pro 3Dp-V264gt2/Tv User's Manual
R 3DP-V264GT/PRO R 3DP-V264GT2/TV 3D Graphic Cards USER'S MANUAL Hardware & Video Drivers USER'S NOTICE No part of this product, including the product and software may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any lan- guage in any form by any means without the express written permission of ASUSTeK COMPUTER INC. (hereinafter referred to as ASUS) except documentation kept by the purchaser for backup purposes. Specifications are subject to change without notice. ASUS provides this manual “as is” without warranty of any kind, either express or implied, including but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall ASUS be liable for any loss or profits, loss of business, loss of use or data, interruption of business, or for indirect, special, inci- dental, or consequential damages of any kind, even if ASUS has been advised of the possibility of such damages arising from any defect or error in this manual or product. ASUS may revise this manual from time to time without notice. Products mentioned in this manual are mentioned for identification purposes only. Product names appearing in this manual may or may not be registered trademarks or copyrights of their respective companies. • IBM is a registered trademark of International Business Machines Corp. • Windows and MS-DOS are registered trademarks of Microsoft Corporation. • Sound Blaster AWE32 and SB16 are trademarks of Creative Technology Ltd. • Adobe and Acrobat are registered trademarks of Adobe Systems Incorporated. The product name and revision number are both printed on the board itself. -

Using Windows Media Player Version 12 (Windows 7) from the Media Player Help System John Lortz ([email protected]) – Discoverskills (
Using Windows Media Player Version 12 (Windows 7) From the Media Player Help System John Lortz ([email protected]) – DiscoverSkills (www.DiscoverSkills.com) You can use Windows Media Player to find and play digital media files on your computer or network, play CDs and DVDs, and stream media from the Internet. You can also rip music from audio CDs, burn CDs of your favorite music, sync media files to portable device, and find and purchase content on the Internet through online stores. Getting started with Windows Media Player Windows Media Player provides an intuitive, easy-to-use interface to play digital media files, organize your digital media collection, burn CDs of your favorite music, rip music from CDs, sync digital media files to a portable device, and shop for digital media content from online stores. Start Windows Media Player To start Windows Media Player, click the Start button , click All Programs, and then click Windows Media Player. Two ways to enjoy your media: the Player Library and Now Playing mode Windows Media Player allows you to toggle between two modes: the Player Library, which gives you comprehensive control over the Player's many features; and Now Playing mode, which gives you a simplified view of your media that's ideal for playback. From the Player Library, you can go to Now Playing mode by clicking the Switch to Now Playing button in the lower- right corner of the Player. To return to the Player Library, click the Switch to Library button in the upper-right corner of the Player. Player Library In the Player Library, you can access and organize your digital media collection. -

Intel® 64 and IA-32 Architectures Software Developer's Manual
Intel® 64 and IA-32 Architectures Software Developer’s Manual Volume 3B: System Programming Guide, Part 2 NOTE: The Intel® 64 and IA-32 Architectures Software Developer's Manual consists of five volumes: Basic Architecture, Order Number 253665; Instruction Set Reference A-M, Order Number 253666; Instruction Set Reference N-Z, Order Number 253667; System Programming Guide, Part 1, Order Number 253668; System Programming Guide, Part 2, Order Number 253669. Refer to all five volumes when evaluating your design needs. Order Number: 253669-029US November 2008 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANT- ED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL'S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. UNLESS OTHERWISE AGREED IN WRITING BY INTEL, THE INTEL PRODUCTS ARE NOT DESIGNED NOR IN- TENDED FOR ANY APPLICATION IN WHICH THE FAILURE OF THE INTEL PRODUCT COULD CREATE A SITUA- TION WHERE PERSONAL INJURY OR DEATH MAY OCCUR. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked "reserved" or "unde- fined." Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. -

Windows Embedded Standard 2009 Prepkit
MCTSi Exam 70-577 Windows Embedded Standard 2009 Preparation Kit Certification Exam Preparation Automation Not for resale. ii Table of Contents Contents at a Glance 1 Creating and Customizing the Configuration 2 Managing the Development Environment 3 Integrating Embedded Enabling Features 4Creating Components 5 Generating and Deploying an Image 6 Adding Windows Functionality Chapter 6 Adding Windows Functionality Microsoft® Windows® Embedded Standard 2009 enables you to add to the run-time image custom functionality that enhances security and the user experience. For example, you can customize a client shell to expose selected functionality of the device. You can also enable remote administration on your device, add multiple languages, and add multiple user accounts. Exam objectives in this chapter: ■ Create a custom shell component ■ Configure multiple user accounts ■ Configure security ■ Add support for multiple languages ■ Add support for remote administration Before You Begin To complete the lessons in this chapter you need the following: ■ Windows Embedded Studio for Windows Embedded Standard 2009 installed. ■ Completed Chapters 1–5. 177 178 Chapter 6 Adding Windows Functionality Lesson 1: Create a Custom Shell Component Windows Embedded Standard 2009 provides several shells, such as Explorer shell, Task Manger shell and Command shell. You can extend the functionality they provide by creating a custom shell that reflects your application and OS design functionality. For example, if your device monitors a car’s engine at a service garage, the display may need to present gauges that show engine condition and buttons to operate the device. Because the use of embedded devices is so specific, it is preferable that the user not be able to start applications, access the file system or interact in the way they usually do with regular Windows XP client based computers. -

Design of the RISC-V Instruction Set Architecture
Design of the RISC-V Instruction Set Architecture Andrew Waterman Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2016-1 http://www.eecs.berkeley.edu/Pubs/TechRpts/2016/EECS-2016-1.html January 3, 2016 Copyright © 2016, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor David Patterson, Chair Professor Krste Asanovi´c Associate Professor Per-Olof Persson Spring 2016 Design of the RISC-V Instruction Set Architecture Copyright 2016 by Andrew Shell Waterman 1 Abstract Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman Doctor of Philosophy in Computer Science University of California, Berkeley Professor David Patterson, Chair The hardware-software interface, embodied in the instruction set architecture (ISA), is arguably the most important interface in a computer system. Yet, in contrast to nearly all other interfaces in a modern computer system, all commercially popular ISAs are proprietary.