MULTI-SEGMENT ETHERNET NETWORKS Using Repeaters to Increase Network Diameter by George Thomas, Contemporary Controls
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mikrodenetleyicili Endüstriyel Seri Protokol Çözümleyici Sisteminin Programi
YILDIZ TEKNİK ÜNİVERSİTESİ FEN BİLİMLERİ ENSTİTÜSÜ MİKRODENETLEYİCİLİ ENDÜSTRİYEL SERİ PROTOKOL ÇÖZÜMLEYİCİ SİSTEMİNİN PROGRAMI Elektronik ve Haberleşme Müh. Kemal GÜNSAY FBE Elektronik ve Haberleşme Anabilim Dalı Elektronik Programında Hazırlanan YÜKSEK LİSANS TEZİ Tez Danışmanı : Yrd. Doç. Dr. Tuncay UZUN (YTÜ) İSTANBUL, 2009 YILDIZ TEKNİK ÜNİVERSİTESİ FEN BİLİMLERİ ENSTİTÜSÜ MİKRODENETLEYİCİLİ ENDÜSTRİYEL SERİ PROTOKOL ÇÖZÜMLEYİCİ SİSTEMİNİN PROGRAMI Elektronik ve Haberleşme Müh. Kemal GÜNSAY FBE Elektronik ve Haberleşme Anabilim Dalı Elektronik Programında Hazırlanan YÜKSEK LİSANS TEZİ Tez Danışmanı : Yrd. Doç. Dr. Tuncay UZUN (YTÜ) İSTANBUL, 2009 İÇİNDEKİLER Sayfa KISALTMA LİSTESİ ................................................................................................................ v ŞEKİL LİSTESİ ...................................................................................................................... viii ÇİZELGE LİSTESİ .................................................................................................................... x ÖNSÖZ ...................................................................................................................................... xi ÖZET ........................................................................................................................................ xii ABSTRACT ............................................................................................................................ xiii 1. GİRİŞ ...................................................................................................................... -

Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern
Switched, Fast, and Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern.. Page 1 of 36 [Figures are not included in this sample chapter] Switched, Fast, and Gigabit Ethernet - 3 - Ethernet, Fast Ethernet, and Gigabit Ethernet Standards This chapter discusses the theory and standards of the three versions of Ethernet around today: regular 10Mbps Ethernet, 100Mbps Fast Ethernet, and 1000Mbps Gigabit Ethernet. The goal of this chapter is to educate you as a LAN manager or IT professional about essential differences between shared 10Mbps Ethernet and these newer technologies. This chapter focuses on aspects of Fast Ethernet and Gigabit Ethernet that are relevant to you and doesn’t get into too much technical detail. Read this chapter and the following two (Chapter 4, "Layer 2 Ethernet Switching," and Chapter 5, "VLANs and Layer 3 Switching") together. This chapter focuses on the different Ethernet MAC and PHY standards, as well as repeaters, also known as hubs. Chapter 4 examines Ethernet bridging, also known as Layer 2 switching. Chapter 5 discusses VLANs, some basics of routing, and Layer 3 switching. These three chapters serve as a precursor to the second half of this book, namely the hands-on implementation in Chapters 8 through 12. After you understand the key differences between yesterday’s shared Ethernet and today’s Switched, Fast, and Gigabit Ethernet, evaluating products and building a network with these products should be relatively straightforward. The chapter is split into seven sections: l "Ethernet and the OSI Reference Model" discusses the OSI Reference Model and how Ethernet relates to the physical (PHY) and Media Access Control (MAC) layers of the OSI model. -

Ethernet and Wifi
Ethernet and WiFi hp://xkcd.com/466/ CSCI 466: Networks • Keith Vertanen • Fall 2011 Overview • Mul?ple access networks – Ethernet • Long history • Dominant wired technology – 802.11 • Dominant wireless technology 2 Classic Ethernet • Ethernet – luminferous ether through which electromagne?c radiaon once thought to propagate – Carrier Sense, Mul?ple Access with Collision Detec?on (CSMA/CD) – IEEE 802.3 Robert Metcalfe, co- inventor of Ethernet 3 Classic Ethernet • Ethernet – Xerox Ethernet standardized as IEEE 802.3 in 1983 – Xerox not interested in commercializing – Metcalfe leaves and forms 3Com 4 Ethernet connec?vity • Shared medium – All hosts hear all traffic on cable – Hosts tapped the cable – 2500m maximum length – May include repeaters amplifying signal – 10 Mbps bandwidth 5 Classic Ethernet cabling Cable aSer being "vampire" tapped. Thick Ethernet cable (yellow), 10BASE-5 transceivers, cable tapping tool (orange), 500m maximum length. Thin Ethernet cable (10BASE2) with BNC T- connector, 185m maximum length. 6 Ethernet addressing • Media Access Control address (MAC) – 48-bit globally unique address • 281,474,976,710,656 possible addresses • Should last ?ll 2100 • e.g. 01:23:45:67:89:ab – Address of all 1's is broadcast • FF:FF:FF:FF:FF:FF 7 Ethernet frame format • Frame format – Manchester encoded – Preamble products 10-Mhz square wave • Allows clock synch between sender & receiver – Pad to at least 64-bytes (collision detec?on) Ethernet 802.3 AlternaWng 0's 48-bit MAC and 1's (except addresses SoF of 11) 8 Ethernet receivers • Hosts listens to medium – Deliver to host: • Any frame with host's MAC address • All broadcast frames (all 1's) • Mul?cast frames (if subscribed to) • Or all frames if in promiscuous mode 9 MAC sublayer • Media Access Control (MAC) sublayer – Who goes next on a shared medium – Ethernet hosts can sense if medium in use – Algorithm for sending data: 1. -

Gigabit Ethernet
Ethernet Technologies and Gigabit Ethernet Professor John Gorgone Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 1 Topics • Origins of Ethernet • Ethernet 10 MBS • Fast Ethernet 100 MBS • Gigabit Ethernet 1000 MBS • Comparison Tables • ATM VS Gigabit Ethernet •Ethernet8SummaryCopyright 1998, John T. Gorgone, All Rights Reserved 2 Origins • Original Idea sprang from Abramson’s Aloha Network--University of Hawaii • CSMA/CD Thesis Developed by Robert Metcalfe----(1972) • Experimental Ethernet developed at Xerox Palo Alto Research Center---1973 • Xerox’s Alto Computers -- First Ethernet Ethernet8systemsCopyright 1998, John T. Gorgone, All Rights Reserved 3 DIX STANDARD • Digital, Intel, and Xerox combined to developed the DIX Ethernet Standard • 1980 -- DIX Standard presented to the IEEE • 1980 -- IEEE creates the 802 committee to create acceptable Ethernet Standard Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 4 Ethernet Grows • Open Standard allows Hardware and Software Developers to create numerous products based on Ethernet • Large number of Vendors keeps Prices low and Quality High • Compatibility Problems Rare Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 5 What is Ethernet? • A standard for LANs • The standard covers two layers of the ISO model – Physical layer – Data link layer Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 6 What is Ethernet? • Transmission speed of 10 Mbps • Originally, only baseband • In 1986, broadband was introduced • Half duplex and full duplex technology • Bus topology Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 7 Components of Ethernet • Physical Medium • Medium Access Control • Ethernet Frame Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 8 CableCable DesignationsDesignations 10 BASE T SPEED TRANSMISSION MAX TYPE LENGTH Ethernet8 Copyright 1998, John T. -
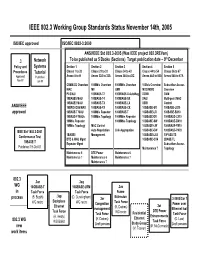
IEEE 802.3 Working Group Standards Status November 14Th, 2005
IEEE 802.3 Working Group Standards Status November 14th, 2005 ISO/IEC approved ISO/IEC 8802-3:2000 ANSI/IEEE Std 802.3-2005 (Was IEEE project 802.3REVam) th .3 Network To be published as 5 Books (Sections) Target publication date – 9 December Policy and Systems Section 1 Section 2 Section 3 Section 4 Section 5 Procedures Tutorial Clause 1 to 20 Clause 21 to 33 Clause 34 to 43 Clause 44 to 54 Clause 56 to 67 Approved Published Annex A to H Annex 22A to 32A Annex 36A to 43C Annex 44A to 50A Annex 58A to 67A Nov-97 Jun-95 CSMA/CD Overview 100Mb/s Overview 1000Mb/s Overview 10Gb/s Overview Subscriber Access MAC MII GMII MDC/MDIO Overview PLS/AUI 100BASE-T2 1000BASE-X AutoNeg XGMII OAM 10BASE5 MAU 100BASE-T4 1000BASE-SX XAUI Multi-point MAC 10BASE2 MAU 100BASE-TX 1000BASE-LX XSBI Control ANSI/IEEE 10BROAD36 MAU 100BASE-FX 1000BASE-CX 10GBASE-SR 100BASE-LX10 approved 10BASE-T MAU 100Mb/s Repeater 1000BASE-T 10GBASE-LR 100BASE-BX10 10BASE-F MAUs 100Mb/s Topology 1000Mb/s Repeater 10GBASE-ER 1000BASE-LX10 10Mb/s Repeater 1000Mb/s Topology 10GBASE-SW 1000BASE-BX10 10Mb/s Topology MAC Control 10GBASE-LW 1000BASE-PX10 IEEE Std 1802.3-2001 Auto Negotiation Link Aggregation 10GBASE-EW 1000BASE-PX20 Conformance Test 1BASE5 Management 10GBASE-LX4 10PASS-TS DTE & MAU Mgmt 10GBASE-CX4 2BASE-TL 10BASE-T Repeater Mgmt Subscriber Access Published 19-Oct-01 Maintenance 7 Topology Maintenance 6 DTE Power Maintenance 6 Maintenance 7 Maintenance 6 Maintenance 7 Maintenance 7 802.3 .3an .3aq WG 10GBASE-T 10GBASE-LRM .3as in Task Force Task Force Frame .3ap process (B. -

Fact Sheet: Single-Pair Ethernet Trade Article
Fact sheet Single Pair Ethernet Matthias Fritsche – product manager device connectivity & Jonas Diekmann – technical editor HARTING Technology group – October 2016– November 2016 Wireless technology and optical cable have already been often heralded as the future transmission technology. However, simple twisted pair cable based on plain old copper, often pronounced dead, is the most common transmission medium. Simple, robust, and perhaps with 100GBASE T1 soon to be also incredibly fast. From the beginnings of Ethernet in the 1970s, then via diverse multi-pair Ethernet developments with multiple parallel transmission paths, now apparently we are taking a step back. Back to single twisted-pair. With a new protocol and new PHYs transmission rates of up to 10 Gbit/s and PoDL capacities of up to 60 W are no longer a problem. Ultimately one pair is enough. When the team surrounding David Boggs and Robert Metcalf in the 1970s developed Ethernet at the Xerox Palo Alto Research Center (PARC), no one could foresee that this transmission method would develop so dynamically and dominate data transmission worldwide to this day. The original 10BASE5 Ethernet still used coax cable as the common medium. Today, next to wireless and optical cables, twisted-pair cable, often pronounced dead, is the most frequently used transmission medium. Starting in 1990 with 10BASE-T, the data transmission rate of the IEEE standards increased by a factor of 10 approximately every 5 years over 100BASE-TX and 1000BASE-T up to 10GBASE-T. This series could not be continued for the jump to 100GBASE-T, instead however four new IEEE standards were finalized in 2016. -

Ethernet Coax Transceiver Interface 1CY7B8392 Functional Description
CY7B8392 Ethernet Coax Transceiver Interface 1CY7B8392 Functional Description Features The CY7B8392 is a low power coaxial transceiver for Ethernet 10BASE5 and 10BASE2 applications. The device contains all • Compliant with IEEE802.3 10BASE5 and 10BASE2 the circuits required to perform transmit, receive, collision de- • Pin compatible with the popular 8392 tection, heartbeat generation, jabber timer and attachment • Internal squelch circuit to eliminate input noise unit interface (AUI) functions. In addition, the CY7B8392 fea- • Hybrid mode collision detect for extended distance tures an advanced hybrid collision detection. • Automatic AUI port isolation when coaxial connector is The transmitter output is connected directly to a double termi- not present nated 50Ω cable. • Low power BiCMOS design The CY7B8392 is fabricated with an advanced low power • 16-Pin DIP or 28-Pin PLCC BiCMOS process. Typical standby current during idle is 25 mA. Logic Block Diagram RX+ HIGH PASS AUI CCM EQUALIZATION DRIVER RX– RXI LOW PASS FILTER CD+ AUI GND – CARRIER DRIVER LOW PASS SENSE CD– FILTER + TX+ TX– – COLLISION CDS LOW PASS + RCV FILTER TXO WAVEFORM + DC/AC SHAPING SQUELCH – VEE 10 MHz CLK WATCHDOG JABBER RESET OSC TIMER26 ms TIMER0.4 sec RR+ REFERENCE 1K CIRCUIT TRANSMIT RECEIVE RR– STATE STATE MACHINE MACHINE HBE 8392–1 Pin Configurations PLCC DIP Top View Top View – RX+ CD CD+ CDS NC RXI TXO CD+ 1 16 CDS 432 1 28 2726 CD– 2 15 TXO VEE (NC) 5 25 VEE (NC) RX+ 3 14 RXI VEE (NC) 6 24 VEE V VEE 7 23 VEE (NC) EE 4 13 VEE 7B8392 7B8392 VEE 8 22 VEE (NC) VEE 5 12 RR– VEE (NC) 9 21 VEE RX– 6 11 RR+ VEE (NC) 10 20 VEE (NC) TX+ 7 10 GND VEE (NC) 11 121314 15 16 1718 RR– TX– 8 9 HBE – – TX+ TX RX 8392–3 RR+ HBE GND GND 8392–2 Cypress Semiconductor Corporation • 3901 North First Street • San Jose • CA 95134 • 408-943-2600 Document #: 38-02016 Rev. -

Ethernet Basics-1/5 BB-WP3 © 2002 by B&B Electronics
Ethernet Basics-1/5 BB-WP3 © 2002 by B&B Electronics. All rights reserved.1005 ETHERNET BASICS B&B ELECTRONICS Regular, Fast, and Ultrafast Ethernet 10BASE5—Thick Ethernet or Thicknet—is the original Institute of Electronic and Electrical Engineers (IEEE) 802.3 Ethernet. 10BASE2—Thin Ethernet, Thinnet, or Cheapernet—resembles 10BASE5, was introduced to reduce the cost and complexity of installation, and became very popular for replacing Thick Ethernet as an office-cabling solution. 10BASE-T, a completely new physical layer, is IEEE 802.3i and uses two pairs of unshielded twisted-pair (UTP) B&B B&B ELECTRONICS telephone-type cable: one to transmit; the other to receive. 10BASE-F refers to three different fiber-optic specifications: . 10BASE-FL (Fiber Link) replaces the 1987 Fiber Optic Inter-Repeater Link (FOIRL) specification and is backward compatible with existing FOIRL devices. It is the most popular 10-Mbps fiber standard. 10BASE-FP and 10BASE-FB are dead. P means passive; B means backbone. Fast Ethernet 100BASE-T is 10BASE-T with the original Ethernet Media Access Controller (MAC) at 10 times the speed. It allows three physical-layer implementations, all part of IEEE 802.3u: 100BASE-TX, which has two pairs of Category 5 UTP or Type 1 STP cabling and is most popular for horizontal connections; 100BASE-FX, which has two strands of multimode fiber and is most popular for vertical or backbone connections; 100BASE-T4, which as four pairs of Category 3 or better cabling and is not common. Gigabit or 1000-Mb Ethernet is the 1998 IEEE 802.3z standard that includes the Gigabit Ethernet MAC and three physical layers. -

Modern Ethernet
Color profile: Generic CMYK printer profile Composite Default screen All-In-One / Network+ Certification All-in-One Exam Guide / Meyers / 225345-2 / Chapter 6 CHAPTER Modern Ethernet 6 The Network+ Certification exam expects you to know how to • 1.2 Specify the main features of 802.2 (Logical Link Control) [and] 802.3 (Ethernet): speed, access method, topology, media • 1.3 Specify the characteristics (for example: speed, length, topology, and cable type) of the following cable standards: 10BaseT and 10BaseFL; 100BaseTX and 100BaseFX; 1000BaseTX, 1000BaseCX, 1000BaseSX, and 1000BaseLX; 10GBaseSR, 10GBaseLR, and 10GBaseER • 1.4 Recognize the following media connectors and describe their uses: RJ-11, RJ-45, F-type, ST,SC, IEEE 1394, LC, MTRJ • 1.6 Identify the purposes, features, and functions of the following network components: hubs, switches • 2.3 Identify the OSI layers at which the following network components operate: hubs, switches To achieve these goals, you must be able to • Define the characteristics, cabling, and connectors used in 10BaseT and 10BaseFL • Explain how to connect multiple Ethernet segments • Define the characteristics, cabling, and connectors used with 100Base and Gigabit Ethernet Historical/Conceptual The first generation of Ethernet network technologies enjoyed substantial adoption in the networking world, but their bus topology continued to be their Achilles’ heel—a sin- gle break anywhere on the bus completely shut down an entire network. In the mid- 1980s, IBM unveiled a competing network technology called Token Ring. You’ll get the complete discussion of Token Ring in the next chapter, but it’s enough for now to say that Token Ring used a physical star topology. -

How to Accelerate Your Internet
How To Accelerate Your Internet A practical guide to Bandwidth Management and Optimisation using Open Source Software How To Accelerate Your Internet For more information about this project, visit us online at http://bwmo.net/ Editor: Flickenger R. Associate Editors: Belcher M., Canessa E., Zennaro M. Publishers: INASP/ICTP © 2006, BMO Book Sprint Team First edition: October 2006 ISBN: 0-9778093-1-5 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibil- ity for errors or omissions. No liability is assumed for incidental or consequen- tial damages in connection with or arising out of the use of the information con- tained herein. This work is released under the Creative Commons Attribution-ShareAlike 2.5 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/2.5/ Contents Preface ix About This Book xi Introduction 1 Bandwidth, throughput, latency, and speed.............................................................................. 2 Not enough to go around........................................................................................................ -

Cheetahub Classic-2041 Quick Installation Guide
CheetaHub Classic-2041 Quick Installation Guide EH2041S E0898-R02 Copyright © 1998 by Accton Technology Corporation. All rights reserved. No part of this document may be copied or reproduced in any form or by any means without the prior written consent of Accton Technology Corporation. Accton makes no warranties with respect to this documentation and disclaims any implied warranties of merchantability, quality, or fitness for any particular purpose. The information in this document is subject to change without notice. Accton reserves the right to make revisions to this publication CheetaHub Classic-2041 without obligation to notify any person or entity of any such changes. Smart Ethernet Hub with 16 10BASE-T (RJ-45) ports, 1 10BASE2 (BNC) port, and 1 AUI port International Headquarters USA Headquarters No. 1 Creation Road III, P.O. Box 51420 Science-based Industrial Park Irvine, CA 92619-1420 Hsinchu 300, Taiwan, R.O.C. Phone Numbers - Phone: 886-3-5770-270 Sales: 888-398-2101 or 949-707-4800 FAX: 886-3-5770-267 Support: 888-398-4101 or 949-707-4847 BBS: 886-3-5770-654 RMA: 888-398-3101 or 949-707-4828 Internet: [email protected] FAX: 949-707-2460 Accton is a trademark of Accton Technology Corporation. Other trademarks or brand names mentioned herein are trademarks or registered trademarks of their respective companies. EH2041S E0898-R02 CheetaHub Classic-2041 Quick Installation Guide Contents Introduction The CheetaHub Classic-2041 includes 16 RJ-45 ports, 1 BNC port for connection to thin Ethernet (10BASE2), and 1 Introduction 1 AUI port for connection to a variety of media types including 10BASE5 or fiber (using a suitable transceiver). -

10Mb/S Ethernet 10BASE2/AUI Adapter
10Mb/s Ethernet 10BASE2/AUI Adapter 32-Bit PCI 28F512 10BASE2 64Kbyte BIOS memory PMC Front AMD 79C970A AUI to 10BASE2 Panel Ethernet +5V MAU Controller +5 to -9V DC-to-DC DSUB-15 (AUI) 10Mb/s "AUI" Rear Rear I/O E-Net Interface I/O PN4 AUI ISOLATION +12V The 10 Mb/s Ethernet Adapter is field-selectable for The AUI interface provides resettable fuse-protected either AUI (10BASE5) or Thinnet (10BASE2) opera- +12V on the DB-15 connector for powering an exter- tion. nal MAU. When operating in AUI mode, the +12V power to the AUI defeats the isolation barrier, and the An AMD 79C970A Ethernet controller provides a 10 PMC system Ground is tied to the external MAU Mb/s Attachment Unit Interface (AUI) for connection to Ground. Media Attachment Units (MAU) either out the rear of the PMC or out the PMC front panel. A 15-pin D- The board features a FLASH memory for storing an Subminiature female is used on the front PMC panel, on-board BIOS. A 28F512 chip is used, providing up complete with the standard MAU retaining slide latch. to 64Kbytes of BIOS storage. The 28F512 chip is installed in a PLCC socket on the PMC card. The AUI interface is available at the PMC “PN4” con- nector for rear connection to the “a” and “c” rows of a Four activity and status LEDs are visible from the PMC VMEbus P2 connector. If the VMEbus host processor front panel. Interrupts are posted on the PCI bus us- adheres to the proposed IEEE 1386 routing from PN4 ing Interrupt Request “A” (INTA).