Apparmor Crash Course
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Storage Administration Guide Storage Administration Guide SUSE Linux Enterprise Server 12 SP4
SUSE Linux Enterprise Server 12 SP4 Storage Administration Guide Storage Administration Guide SUSE Linux Enterprise Server 12 SP4 Provides information about how to manage storage devices on a SUSE Linux Enterprise Server. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xii 1 Available Documentation xii 2 Giving Feedback xiv 3 Documentation Conventions xiv 4 Product Life Cycle and Support xvi Support Statement for SUSE Linux Enterprise Server xvii • Technology Previews xviii I FILE SYSTEMS AND MOUNTING 1 1 Overview -

Security Assurance Requirements for Linux Application Container Deployments
NISTIR 8176 Security Assurance Requirements for Linux Application Container Deployments Ramaswamy Chandramouli This publication is available free of charge from: https://doi.org/10.6028/NIST.IR.8176 NISTIR 8176 Security Assurance Requirements for Linux Application Container Deployments Ramaswamy Chandramouli Computer Security Division Information Technology Laboratory This publication is available free of charge from: https://doi.org/10.6028/NIST.IR.8176 October 2017 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology NISTIR 8176 SECURITY ASSURANCE FOR LINUX CONTAINERS National Institute of Standards and Technology Internal Report 8176 37 pages (October 2017) This publication is available free of charge from: https://doi.org/10.6028/NIST.IR.8176 Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Such identification is not intended to imply recommendation or endorsement by NIST, nor is it intended to imply that the entities, materials, or equipment are necessarily the best available for the purpose. This p There may be references in this publication to other publications currently under development by NIST in accordance with its assigned statutory responsibilities. The information in this publication, including concepts and methodologies, may be used by federal agencies even before the completion of such companion publications. Thus, until each ublication is available free of charge from: http publication is completed, current requirements, guidelines, and procedures, where they exist, remain operative. For planning and transition purposes, federal agencies may wish to closely follow the development of these new publications by NIST. -

Course Outline & Schedule
Course Outline & Schedule Call US 408-759-5074 or UK +44 20 7620 0033 Suse Linux Advanced System Administration Curriculum Linux Course Code SLASA Duration 5 Day Course Price $2,425 Course Description This instructor led SUSE Linux Advanced System Administration training course is designed to teach the advanced administration, security, networking and performance tasks required on a SUSE Linux Enterprise system. Targeted to closely follow the official LPI curriculum (generic Linux), this course together with the SUSE Linux System Administration course will enable the delegate to work towards achieving the LPIC-2 qualification. Exercises and examples are used throughout the course to give practical hands-on experience with the techniques covered. Objectives The delegate will learn and acquire skills as follows: Perform administrative tasks with supplied tools such as YaST Advanced network configuration Network troubleshooting and analysing packets Creating Apache virtual hosts and hosting user web content Sharing Windows and Linux resources with SAMBA Configuring a DNS server and configuring DNS logging Configuring a DHCP server and client Sharing Linux network resources with NFS Creating Unit Files Configuring AutoFS direct and indirect maps Configuring a secure FTP server Configuring a SQUID proxy server Creating Btrfs subvolumes and snapshots Backing-up and restoring XFS filesystems Configuring LVM and managing Logical Volumes Managing software RAID Centralised storage with iSCSI Monitoring disk status and reliability with SMART Perpetual -

How SUSE Helps Pave the Road to S/4HANA
White Paper How SUSE Helps Pave the Road to S/4HANA Sponsored by: SUSE and SAP Peter Rutten Henry D. Morris August 2017 IDC OPINION According to SAP, there are now 6,800 SAP customers that have chosen S/4HANA. In addition, many more of the software company's customers still have to make the decision to move to S/4HANA. These customers have to determine whether they are ready to migrate their database for mission-critical workloads to a new database (SAP HANA) and a new application suite (S/4HANA). Furthermore, SAP HANA runs on Linux only, an operating environment that SAP customers may not have used extensively before. This white paper discusses the choices SAP customers have for migrating to S/4HANA on Linux and looks at how SUSE helps customers along the way. SITUATION OVERVIEW Among SAP customers, migration from traditional databases to the SAP HANA in-memory platform is continuing steadily. IDC's Data Analytics Infrastructure (SAP) Survey, November 2016 (n = 300) found that 49.3% of SAP customers in North America are running SAP HANA today. Among those that are not on SAP HANA, 29.9% will be in two to four years and 27.1% in four to six years. The slower adopters say that they don't feel rushed, stating that there's time until 2025 to make the decision, and that their current databases are performing adequately. While there is no specific order that SAP customers need to follow to get to S/4HANA, historically businesses have often migrated to SAP Business Warehouse (BW) on SAP HANA first as BW is a rewarding starting point for SAP HANA for two reasons: there is an instant performance improvement and migration is relatively easy since BW typically does not contain core enterprise data that is business critical. -

Securing Server Applications Using Apparmor TUT-1179
Securing Server Applications Using AppArmor TUT-1179 Brian Six Sales Engineer – SUSE [email protected] 1 Agenda AppArmor Introduction How to interact and configure Demo with simple script Can AppArmor help with containers Final thoughts 2 Intro to AppArmor 3 What is AppArmor? Bad software does what it shouldn’t do Good software does what it should do Secure software does what it should do, and nothing else AppArmor secures the Good and the Bad software 4 What is AppArmor? Mandatory Access Control (MAC) security system Applies policies to Applications Access to files and paths, network functions, system functions 5 What is AppArmor? Dynamic for existing profiled applications Regardless of the “user” the process is running as, the policy can be enforced. Root is no exception. 6 What is AppArmor? 7 Architecture Logging and OS Component Application Alerting AppArmor AppArmor Interface Application Profile AppArmor Linux Kernel 2.6 and later LSM Interface 8 How To Interact And Configure 9 How To Interact With AppArmor Apparmor-Utils First Install package 10 How To Interact With AppArmor Used more often 11 What Do Some Of These Do aa-status: Display aa-genprof : Create aa-logprof: Update aa-complain: Set a aa-enforce: Set a status of profile a profile an existing profile profile in complain profile in enforce enforcement mode mode 12 Common Permissions r – read w – write k – lock ux - unconstrained execute Ux - unconstrained execute – scrub px – discrete profile execute Px - discrete profile execute – scrub ix - inherit execute cx - local security profile l – link a – append m - mmap 13 Profile At-A-Glance https://doc.opensuse.org/documentation/leap/archive/42.3/security/html/book.security/cha.apparmor.profiles.html # a comment about foo's local (children) profile for #include <tunables/global> /usr/bin/foobar. -
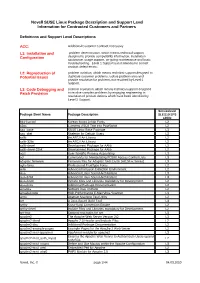
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP3 s390x 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-32bit An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 aalib-devel-32bit Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-32bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. L2 alsa-docs Additional Package Documentation. L2 amanda Network Disk Archiver L2 amavisd-new High-Performance E-Mail Virus Scanner L3 amtu Abstract Machine Test Utility L2 ant A Java-Based Build Tool L3 anthy Kana-Kanji Conversion Engine L2 anthy-devel Include Files and Libraries mandatory for Development. -

High Velocity Kernel File Systems with Bento
High Velocity Kernel File Systems with Bento Samantha Miller, Kaiyuan Zhang, Mengqi Chen, and Ryan Jennings, University of Washington; Ang Chen, Rice University; Danyang Zhuo, Duke University; Thomas Anderson, University of Washington https://www.usenix.org/conference/fast21/presentation/miller This paper is included in the Proceedings of the 19th USENIX Conference on File and Storage Technologies. February 23–25, 2021 978-1-939133-20-5 Open access to the Proceedings of the 19th USENIX Conference on File and Storage Technologies is sponsored by USENIX. High Velocity Kernel File Systems with Bento Samantha Miller Kaiyuan Zhang Mengqi Chen Ryan Jennings Ang Chen‡ Danyang Zhuo† Thomas Anderson University of Washington †Duke University ‡Rice University Abstract kernel-level debuggers and kernel testing frameworks makes this worse. The restricted and different kernel programming High development velocity is critical for modern systems. environment also limits the number of trained developers. This is especially true for Linux file systems which are seeing Finally, upgrading a kernel module requires either rebooting increased pressure from new storage devices and new demands the machine or restarting the relevant module, either way on storage systems. However, high velocity Linux kernel rendering the machine unavailable during the upgrade. In the development is challenging due to the ease of introducing cloud setting, this forces kernel upgrades to be batched to meet bugs, the difficulty of testing and debugging, and the lack of cloud-level availability goals. support for redeployment without service disruption. Existing Slow development cycles are a particular problem for file approaches to high-velocity development of file systems for systems. -

Container and Kernel-Based Virtual Machine (KVM) Virtualization for Network Function Virtualization (NFV)
Container and Kernel-Based Virtual Machine (KVM) Virtualization for Network Function Virtualization (NFV) White Paper August 2015 Order Number: 332860-001US YouLegal Lines andmay Disclaimers not use or facilitate the use of this document in connection with any infringement or other legal analysis concerning Intel products described herein. You agree to grant Intel a non-exclusive, royalty-free license to any patent claim thereafter drafted which includes subject matter disclosed herein. No license (express or implied, by estoppel or otherwise) to any intellectual property rights is granted by this document. All information provided here is subject to change without notice. Contact your Intel representative to obtain the latest Intel product specifications and roadmaps. The products described may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are available on request. Copies of documents which have an order number and are referenced in this document may be obtained by calling 1-800-548-4725 or by visiting: http://www.intel.com/ design/literature.htm. Intel technologies’ features and benefits depend on system configuration and may require enabled hardware, software or service activation. Learn more at http:// www.intel.com/ or from the OEM or retailer. Results have been estimated or simulated using internal Intel analysis or architecture simulation or modeling, and provided to you for informational purposes. Any differences in your system hardware, software or configuration may affect your actual performance. For more complete information about performance and benchmark results, visit www.intel.com/benchmarks. Tests document performance of components on a particular test, in specific systems. -

Vnios Deployment on KVM January 2019
Deployment Guide vNIOS deployment on KVM January 2019 TABLE OF CONTENTS Overview .............................................................................................................................................. 3 Introduction ........................................................................................................................................ 3 vNIOS for KVM ................................................................................................................................... 3 vNIOS deployment on KVM ................................................................................................................ 3 Preparing the environment ................................................................................................................. 3 Installing KVM and Bridge utilities ...................................................................................................... 3 Creating various types networks ........................................................................................................ 5 Downloading vNIOS QCOW2 image ................................................................................................. 8 Copying vNIOS qcow2 image .......................................................................................................... 10 Deploying vNIOS with Bridge Networking........................................................................................ 11 Deploying vNIOS through xml file with Bridge Networking ............................................................. -

Ubuntu Server Guide Basic Installation Preparing to Install
Ubuntu Server Guide Welcome to the Ubuntu Server Guide! This site includes information on using Ubuntu Server for the latest LTS release, Ubuntu 20.04 LTS (Focal Fossa). For an offline version as well as versions for previous releases see below. Improving the Documentation If you find any errors or have suggestions for improvements to pages, please use the link at thebottomof each topic titled: “Help improve this document in the forum.” This link will take you to the Server Discourse forum for the specific page you are viewing. There you can share your comments or let us know aboutbugs with any page. PDFs and Previous Releases Below are links to the previous Ubuntu Server release server guides as well as an offline copy of the current version of this site: Ubuntu 20.04 LTS (Focal Fossa): PDF Ubuntu 18.04 LTS (Bionic Beaver): Web and PDF Ubuntu 16.04 LTS (Xenial Xerus): Web and PDF Support There are a couple of different ways that the Ubuntu Server edition is supported: commercial support and community support. The main commercial support (and development funding) is available from Canonical, Ltd. They supply reasonably- priced support contracts on a per desktop or per-server basis. For more information see the Ubuntu Advantage page. Community support is also provided by dedicated individuals and companies that wish to make Ubuntu the best distribution possible. Support is provided through multiple mailing lists, IRC channels, forums, blogs, wikis, etc. The large amount of information available can be overwhelming, but a good search engine query can usually provide an answer to your questions. -

Unbreakable Enterprise Kernel Release Notes for Unbreakable Enterprise Kernel Release 3
Unbreakable Enterprise Kernel Release Notes for Unbreakable Enterprise Kernel Release 3 E48380-10 June 2020 Oracle Legal Notices Copyright © 2013, 2020, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

This Open Source Software Attribution
OSS Disclosure Document DATE CM_PRO Zeppelin 21-August -2020 This Open Source Software Attribution document is valid for following versions AI_PRJ_G3INF4CV_20.0V08.15_Zeppelin VIII AI_PRJ_G3INF4CV_20.0V08.16_Zeppelin IX AI_PRJ_G3INF4CV_20.0V08.18_Zeppelin X This document is provided as part of the fulfillment of OSS license conditions and does not require users to take any action before or while using the product. Page 1 © This is the exclusive property of ROBERT BOSCH ENGINEERING AND BUSINESS SOLUTIONS PRIVATE LIMITED. Without their consent, it may not be reproduced or given to third parties OSS Disclosure Document DATE CM_PRO Zeppelin 21-August -2020 Table of Contents 1 List of used Open Source Components. ........................................................................................... 3 1.1 Academic Free License v2.1 ................................................................................................. 86 1.2 Apache License 2.0 ............................................................................................................ 88 1.3 Apple Public Source License 1.1 ............................................................................................ 91 1.4 BSD 2-clause "Simplified" License.......................................................................................... 99 1.5 BSD 3-clause "New" or "Revised" License .............................................................................. 100 1.6 BSD-4-Clause (University of California-Specific)......................................................................