BP's Sturgeon, the FISH That Laid No Eggs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ira Sprague Bowen Papers, 1940-1973
http://oac.cdlib.org/findaid/ark:/13030/tf2p300278 No online items Inventory of the Ira Sprague Bowen Papers, 1940-1973 Processed by Ronald S. Brashear; machine-readable finding aid created by Gabriela A. Montoya Manuscripts Department The Huntington Library 1151 Oxford Road San Marino, California 91108 Phone: (626) 405-2203 Fax: (626) 449-5720 Email: [email protected] URL: http://www.huntington.org/huntingtonlibrary.aspx?id=554 © 1998 The Huntington Library. All rights reserved. Observatories of the Carnegie Institution of Washington Collection Inventory of the Ira Sprague 1 Bowen Papers, 1940-1973 Observatories of the Carnegie Institution of Washington Collection Inventory of the Ira Sprague Bowen Paper, 1940-1973 The Huntington Library San Marino, California Contact Information Manuscripts Department The Huntington Library 1151 Oxford Road San Marino, California 91108 Phone: (626) 405-2203 Fax: (626) 449-5720 Email: [email protected] URL: http://www.huntington.org/huntingtonlibrary.aspx?id=554 Processed by: Ronald S. Brashear Encoded by: Gabriela A. Montoya © 1998 The Huntington Library. All rights reserved. Descriptive Summary Title: Ira Sprague Bowen Papers, Date (inclusive): 1940-1973 Creator: Bowen, Ira Sprague Extent: Approximately 29,000 pieces in 88 boxes Repository: The Huntington Library San Marino, California 91108 Language: English. Provenance Placed on permanent deposit in the Huntington Library by the Observatories of the Carnegie Institution of Washington Collection. This was done in 1989 as part of a letter of agreement (dated November 5, 1987) between the Huntington and the Carnegie Observatories. The papers have yet to be officially accessioned. Cataloging of the papers was completed in 1989 prior to their transfer to the Huntington. -

The Paris Apartment Is a Work of Fiction
READI NG GROUP GU I DE PhotosOfYou_TPTextFP Epilogue 2019-11-26 15:34:54 335 AUTHOR’S NOTE The Paris Apartment is a work of fiction. While a product of my imagination, the premises and characters I’ve chosen to create are inspired by real people and real events. The characters of Sophie Seymour and Estelle Allard were shaped by the experiences and courage of Virginia Hall, Pearl Witherington Cornioley, Christine Granville, Josephine Baker, Nancy Wake, and Andrée de Jongh. Their memoirs, interviews, and stories only give us an idea of how truly extraordinary each of these women was. Sophie’s work at Bletchley Park was based on the real men and women who worked tirelessly against time and almost im- possible odds to decode Nazi encryption devices. Most of us have heard of the Enigma cipher and the remarkable work by Alan Turing and his team to break that cipher. Told less often seems to be the story of Tommy Flowers and Bill Tutte, who, together with their teams, developed Colossus—the machine that was able to break the Lorenz cipher, known as Tunny at Bletchley. The Lorenz cipher was favoured by Hitler and used by High Command—and for good reason. It was a far more powerful than the Enigma and capable of exceedingly complex en- cryptions. Additionally, unlike the Enigma, it did not depend ParisApartment_TPtext1P Author’s Note 2020-10-01 21:13:57 395 396 AUTHOR’S NOTE on Morse code. Attached to a teleprinter, it automatically encrypted outgoing messages and decrypted incoming mes- sages, allowing longer messages to be transmitted with greater ease. -

Introduction
Title: Daring Missions of World War II Author: William B. Breuer ISBN: 0-471-40419-5 Introduction World war ii, the mightiest endeavor that history has known, was fought in many arenas other than by direct confrontation between opposing forces. One of the most significant of these extra dimensions was a secret war-within-a-war that raged behind enemy lines, a term that refers to actions taken a short dis- tance to the rear of an adversary’s battlefield positions or as far removed as a foe’s capital or major headquarters. Relentlessly, both sides sought to penetrate each other’s domain to dig out intelligence, plant rumors, gain a tactical advantage, spread propaganda, create confusion, or inflict mayhem. Many ingenious techniques were employed to infiltrate an antagonist’s territory, including a platoon of German troops dressed as women refugees and pushing baby carriages filled with weapons to spearhead the invasion of Belgium. Germans also wore Dutch uniforms to invade Holland. The Nazi attack against Poland was preceded by German soldiers dressed as civilians and by others wearing Polish uniforms. In North Africa, British sol- diers masqueraded as Germans to strike at enemy airfields, and both sides dressed as Arabs on occasion. One British officer in Italy disguised himself as an Italian colonel to get inside a major German headquarters and steal vital information. In the Pacific, an American sergeant of Japanese descent put on a Japan- ese officer’s uniform, sneaked behind opposing lines, and brought back thir- teen enemy soldiers who had obeyed his order to lay down their weapons. -

Guides to German Records Microfilmed at Alexandria, Va
GUIDES TO GERMAN RECORDS MICROFILMED AT ALEXANDRIA, VA. No. 32. Records of the Reich Leader of the SS and Chief of the German Police (Part I) The National Archives National Archives and Records Service General Services Administration Washington: 1961 This finding aid has been prepared by the National Archives as part of its program of facilitating the use of records in its custody. The microfilm described in this guide may be consulted at the National Archives, where it is identified as RG 242, Microfilm Publication T175. To order microfilm, write to the Publications Sales Branch (NEPS), National Archives and Records Service (GSA), Washington, DC 20408. Some of the papers reproduced on the microfilm referred to in this and other guides of the same series may have been of private origin. The fact of their seizure is not believed to divest their original owners of any literary property rights in them. Anyone, therefore, who publishes them in whole or in part without permission of their authors may be held liable for infringement of such literary property rights. Library of Congress Catalog Card No. 58-9982 AMERICA! HISTORICAL ASSOCIATION COMMITTEE fOR THE STUDY OP WAR DOCUMENTS GUIDES TO GERMAN RECOBDS MICROFILMED AT ALEXAM)RIA, VA. No* 32» Records of the Reich Leader of the SS aad Chief of the German Police (HeiehsMhrer SS und Chef der Deutschen Polizei) 1) THE AMERICAN HISTORICAL ASSOCIATION (AHA) COMMITTEE FOR THE STUDY OF WAE DOCUMENTS GUIDES TO GERMAN RECORDS MICROFILMED AT ALEXANDRIA, VA* This is part of a series of Guides prepared -

An Archeology of Cryptography: Rewriting Plaintext, Encryption, and Ciphertext
An Archeology of Cryptography: Rewriting Plaintext, Encryption, and Ciphertext By Isaac Quinn DuPont A thesis submitted in conformity with the requirements for the degree of Doctor of Philosophy Faculty of Information University of Toronto © Copyright by Isaac Quinn DuPont 2017 ii An Archeology of Cryptography: Rewriting Plaintext, Encryption, and Ciphertext Isaac Quinn DuPont Doctor of Philosophy Faculty of Information University of Toronto 2017 Abstract Tis dissertation is an archeological study of cryptography. It questions the validity of thinking about cryptography in familiar, instrumentalist terms, and instead reveals the ways that cryptography can been understood as writing, media, and computation. In this dissertation, I ofer a critique of the prevailing views of cryptography by tracing a number of long overlooked themes in its history, including the development of artifcial languages, machine translation, media, code, notation, silence, and order. Using an archeological method, I detail historical conditions of possibility and the technical a priori of cryptography. Te conditions of possibility are explored in three parts, where I rhetorically rewrite the conventional terms of art, namely, plaintext, encryption, and ciphertext. I argue that plaintext has historically been understood as kind of inscription or form of writing, and has been associated with the development of artifcial languages, and used to analyze and investigate the natural world. I argue that the technical a priori of plaintext, encryption, and ciphertext is constitutive of the syntactic iii and semantic properties detailed in Nelson Goodman’s theory of notation, as described in his Languages of Art. I argue that encryption (and its reverse, decryption) are deterministic modes of transcription, which have historically been thought of as the medium between plaintext and ciphertext. -

A Counterintelligence Reader, Volume 2 Chapter 1, CI in World
CI in World War II 113 CHAPTER 1 Counterintelligence In World War II Introduction President Franklin Roosevelts confidential directive, issued on 26 June 1939, established lines of responsibility for domestic counterintelligence, but failed to clearly define areas of accountability for overseas counterintelligence operations" The pressing need for a decision in this field grew more evident in the early months of 1940" This resulted in consultations between the President, FBI Director J" Edgar Hoover, Director of Army Intelligence Sherman Miles, Director of Naval Intelligence Rear Admiral W"S" Anderson, and Assistant Secretary of State Adolf A" Berle" Following these discussions, Berle issued a report, which expressed the Presidents wish that the FBI assume the responsibility for foreign intelligence matters in the Western Hemisphere, with the existing military and naval intelligence branches covering the rest of the world as the necessity arose" With this decision of authority, the three agencies worked out the details of an agreement, which, roughly, charged the Navy with the responsibility for intelligence coverage in the Pacific" The Army was entrusted with the coverage in Europe, Africa, and the Canal Zone" The FBI was given the responsibility for the Western Hemisphere, including Canada and Central and South America, except Panama" The meetings in this formative period led to a proposal for the organization within the FBI of a Special Intelligence Service (SIS) for overseas operations" Agreement was reached that the SIS would act -
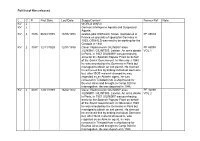
Full List of Files Released L C P First Date Last Date Scope/Content
Full list of files released L C P First Date Last Date Scope/Content Former Ref Note KV 2 WORLD WAR II KV 2 German Intelligence Agents and Suspected Agents KV 2 3386 06/03/1935 18/08/1953 Greta Lydia OSWALD: Swiss. Imprisoned in PF 45034 France on grounds of spying for Germany in 1935, OSWALD was said to be working for the Gestapo in 1941 KV 2 3387 12/11/1929 12/01/1939 Oscar Vladimirovich GILINSKY alias PF 46098 JILINSKY, GILINTSIS: Latvian. An arms dealer VOL 1 in Paris, in 1937 GILINSKY was purchasing arms for the Spanish Popular Front on behalf of the Soviet Government. In November 1940 he was arrested by the Germans in Paris but managed to obtain an exit permit. He claimed he achieved this by bribing individual Germans but, after ISOS material showed he was regarded as an Abwehr agent, he was removed in Trinidad from a ship bound for Buenos Aires and brought to Camp 020 for interrogation. He was deported in 1946 KV 2 3388 13/01/1939 16/02/1942 Oscar Vladimirovich GILINSKY alias PF 46098 JILINSKY, GILINTSIS: Latvian. An arms dealer VOL 2 in Paris, in 1937 GILINSKY was purchasing arms for the Spanish Popular Front on behalf of the Soviet Government. In November 1940 he was arrested by the Germans in Paris but managed to obtain an exit permit. He claimed he achieved this by bribing individual Germans but, after ISOS material showed he was regarded as an Abwehr agent, he was removed in Trinidad from a ship bound for Buenos Aires and brought to Camp 020 for interrogation. -

ICOHTEC Newsletter July 2010
ICOHTEC NEWSLETTER www.icohtec.org No 64, July 2010 Newsletter of the International Committee for the History of Technology ICOHTEC Editor: Stefan Poser, Helmut-Schmidt-University Hamburg, Modern Social, Economic and Technological History, Holstenhofweg 85, D-22043 Hamburg, Germany, [email protected] Editorial Dear Colleagues and Friends, Our joint meeting of TICCIH, work lab, and ICOHTEC in Tampere will be attended by 330 participants (plus accompanying persons) from 40 countries. In total 270 presentations will be delivered in 70 sessions. Please find the final program and an electronic version of the book of abstracts on the conference main website http://www.tampere.fi/industrialpast2010/ In order to inform the members about the International Committee for the Conservation of the Industrial Heritage (TICCIH) and the International Committee for the History of Technology (ICOHTEC) the Newsletter publishes short articles about both societies. You might be interested to know about the development of the history of technology in Finland. Thus the newsletter offers a bibliography of Finnish books and articles in the history of technology, assembled by the Finnish Society for the History of Technology . In 2007 Timo Myllyntaus, Tiina Männistö, and Riikka Jalonen (University of Turku) published a report about the development of the history of technology in Finland in the ICOHTEC Newsletter; it is available on our website: http://www.icohtec.org/publications-reports.html . A brand new article on this subject will be included in the Tampere conference bags: the journal Tekniikan Waiheita , Finnish Quarterly for the History of Technology , has published a special issue 2/2010 under the title: “Finnish Research on the History of Technology”. -

Von Berlin Über Sermuth Nach Heidelberg
Von Berlin uber¨ Sermuth nach Heidelberg Das Schicksal des Astronomischen Rechen-Instituts in der Zeit von 1924 bis 1954 anhand von Schriftstucken¨ aus dem Archiv des Instituts Roland Wielen und Ute Wielen Astronomisches Rechen-Institut Zentrum fur¨ Astronomie Universit¨at Heidelberg Heidelberg 2012 Diese Arbeit wird elektronisch publiziert auf der Open Access-Plattform HeiDOK der Universit¨at Heidelberg, die von der Universit¨atsbibliothek Heidelberg verwaltet wird: HeiDOK - Der Heidelberger Dokumentenserver Der Internet-Zugang zu HeiDOK erfolgt uber¨ den Link: http://archiv.ub.uni-heidelberg.de Auf den Seiten von HeiDOK kann nach der vorliegenden Arbeit gesucht wer- den. Am schnellsten geht dies uber¨ die Suche nach Wielen“ als Person bzw. ” als Autor. 2 Inhaltsverzeichnis Zusammenfassung 23 Abstract 23 1 Einleitung 24 1.1 Einfuhrung¨ . 24 1.2 Hinweis auf Archivalien . 25 2 Das Astronomische Rechen-Institut in Berlin. Die Zeit von 1924 bis 1938. 26 2.1 August Kopff wird Direktor des Astronomischen Rechen-Instituts 26 2.2 Die Arbeit des Astronomischen Rechen-Instituts . 28 2.2.1 Das Berliner Astronomische Jahrbuch . 28 2.2.2 Die Kleinen Planeten . 35 2.2.3 Der Astronomische Jahresbericht . 37 2.2.4 Der Fundamental-Katalog . 38 2.2.5 Katalog der Anhaltsterne fur¨ das Zonenunternehmen der Astronomischen Gesellschaft . 40 2.2.6 Weitere Arbeitsfelder . 41 2.2.7 Popul¨are Darstellungen der Arbeit des Instituts . 43 2.3 Die astronomischen Grundlagen fur¨ den Kalender . 45 2.4 Hinweise auf die schwierige Lage des Instituts . 46 3 3 Das Astronomische Rechen-Institut in Berlin. Die Zeit von 1939 bis 1944. 49 3.1 Die Umbenennung in Coppernicus-Institut“ . -

Golden Fish an Intelligent Stream Cipher Fuse Memory Modules
Golden Fish: An Intelligent Stream Cipher Fuse Memory Modules Lan Luo 1,2,QiongHai Dai 1,ZhiGuang Qin 2 ,ChunXiang Xu 2 1Broadband Networks & Digital Media Lab School of Information Science & Technology Automation Dep. Tsinghua University ,BeiJing, China,100084 2 School of Computer Science and Technology University of Electronic Science Technology of China, ChengDu, China, 610054 E-mail: [email protected] Abstract Furthermore, we can intelligent design the ciphers according to different network environments [4-5]. In In this paper, we use a high-order iterated function order to demonstrate our approach, we construct a generated by block cipher as the nonlinear filter to simple synchronous stream cipher, which provides a improve the security of stream cipher. Moreover, by significant flexibility for hardware implementations, combining the published rounds function in block with many desirable cryptographic advantages. The cipher and OFB as the nonlinear functional mode with security of the encryption and decryption are based on an extra memory module, we enable to control the the computational complexity, which is demonstrated nonlinear complexity of the design. This new approach by AES and NESSIE competition recently, where all fuses the block cipher operation mode with two the finalists fall into the category “no attack or memory modules in one stream cipher. The security of weakness demonstrated”, in which people can go for this design is proven by the both periodic and the simplest, and most elegant design comparing an nonlinear evaluation. The periods of this structure is more complicate and non-transparent one. To guaranteed by the traditional Linear Feedback Shift implement the idea above, we take output feedback Register design and the security of nonlinear mode (OFB) of the block cipher as the nonlinear filter characteristic is demonstrated by block cipher in stream cipher design. -

A Review Analysis of Two Fish Algorithm Cryptography Quantum Computing
IJCSN International Journal of Computer Science and Network, Volume 6, Issue 1, February 2017 ISSN (Online) : 2277-5420 www.IJCSN.org Impact Factor: 1.5 A Review Analysis of Two Fish Algorithm Cryptography Quantum Computing 1 Sukhvandna Abhi, 2 Umesh Sehgal 1, 2 GNA University Phagwara Abstract - In this analysis paper we tend to describe the evolution of cryptography ranging from the start of the twentieth century and continued into this day. Last 10 years quantum computing can begin to trounce everyday computers, resulting in breakthroughs in computer science. Specifically within the cryptography used from 1900 till the tip of war II.Quantum technologies supply immoderate secure communication sensors of unprecedented exactness and computers that square measure exponentially a lot of powerful than any mainframe for a given task. We compare the performance of the 5 AES finalists one kind of common software package platforms current 32-bit CPUs and high finish sixty four bit CPUs. Our intent is to indicate roughly however the algorithm’s speeds compare across a range of CPUs.The future of cryptography primarily based within the field of natural philosophy and by analyzing the hope to supply a allot of complete image of headed the 2 mail algorithms utilized in cryptography world. Keywords - Cryptography ancient secret writing system 1. Introduction regulated wherever the primary letter is substituted by the last letter, the second letter by the second to last letter then ryptography may be a subject that has been studied on. as a result of it's a monoalphabetic cipher and may and applied since ancient Roman times, and have only 1 doable key, this cipher is comparatively weak; Canalysis into higher coding ways continues to the but this wasn't a viable concern throughout its time as current day. -

Pdf På Finska
ITSETEHOSTUKSESTA NÖYRYYTEEN SUOMENSAKSALAISET 1933–46 Lars Westerlund Kansikuva: Korkean tason saksalais-suomalaista kanssakäymistä presidentinlinnassa huhtikuussa 1938. Vasemmalta kenraali Rüdiger von der Goltz, presidentti Kyösti Kallio, marsalkka Gustaf Mannerheim ja Saksan Suomen lähettiläs Wipert von Blücher. Erik von Frenckellin kokoelma. Svenska Litteratursällskapet Kansallisarkisto 2011 Tekninen toimitus: Jyri Taskinen Painopaikka: Oy Nord Print Ab, Helsinki 2011 ISBN 978-951-53-3373-5 2 SISÄLLYS JOHDANTO ................................................................................................. 6 Tarkoitus ja jäsentely ................................................................................. 6 Suomen saksalaisyhteisö ............................................................................ 7 Aikaisempi tutkimus ................................................................................ 21 Käytetty arkisto- ja lehtiaineisto .............................................................. 37 YHDISTYKSET .......................................................................................... 41 Suomen Saksalainen Siirtokunta – Die Deutsche Kolonie ...................... 41 Saksalaisen Siirtokunnan jäsenistö 1935–42 ........................................... 57 NSDAP:n Suomen puoluejärjestö ............................................................ 70 Deutscher Verein Helsingissä .................................................................. 93 Deutscher Frauenverein ........................................................................