Deploying Webobjects Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Managing Files with Sterling Connect:Direct File Agent 1.4.0.1
Managing Files with Sterling Connect:Direct File Agent 1.4.0.1 IBM Contents Managing Files with Sterling Connect:Direct File Agent.......................................... 1 Sterling Connect:Direct File Agent Overview.............................................................................................. 1 How to Run Sterling Connect:Direct File Agent.......................................................................................... 2 Sterling Connect:Direct File Agent Logging.................................................................................................3 Sterling Connect:Direct File Agent Configuration Planning........................................................................ 3 Sterling Connect:Direct File Agent Worksheet ...........................................................................................4 Considerations for a Large Number of Watch Directories.......................................................................... 6 Modifying MaxFileSize............................................................................................................................ 6 Modifying MaxBackupIndex...................................................................................................................6 Considerations for a Large Number of Files in a Watch Directory..............................................................7 Sterling Connect:Direct File Agent Configuration Scenarios...................................................................... 7 Scenario:Detecting -

An Overview of the Jumplist Configuration File in Windows 7
Journal of Digital Forensics, Security and Law Volume 7 Number 1 Article 2 2012 An Overview of the Jumplist Configuration File in Windows 7 Harjinder S. Lallie University of Warwick, Coventry Parmjit S. Bains University of Derby, School of Computing and Mathematics Follow this and additional works at: https://commons.erau.edu/jdfsl Part of the Computer Engineering Commons, Computer Law Commons, Electrical and Computer Engineering Commons, Forensic Science and Technology Commons, and the Information Security Commons Recommended Citation Lallie, Harjinder S. and Bains, Parmjit S. (2012) "An Overview of the Jumplist Configuration File in Windows 7," Journal of Digital Forensics, Security and Law: Vol. 7 : No. 1 , Article 2. DOI: https://doi.org/10.15394/jdfsl.2012.1110 Available at: https://commons.erau.edu/jdfsl/vol7/iss1/2 This Article is brought to you for free and open access by the Journals at Scholarly Commons. It has been accepted for inclusion in Journal of Digital Forensics, Security and Law by an authorized administrator of (c)ADFSL Scholarly Commons. For more information, please contact [email protected]. Journal of Digital Forensics, Security and Law, Vol. 7(1) An Overview of the Jumplist Configuration File in Windows 7 Harjinder Singh Lalli University of Warwick, International Digital Laboratory (WMG), University of Warwick, Coventry, CV4 7AL, UK; [email protected] Parmjit Singh Bains University of Derby, School of Computing and Mathematics, Kedleston Road, Derby, DE22 1GB, UK; [email protected] ABSTRACT The introduction of Jumplists in Windows 7 was an important feature from a forensic examiners viewpoint. Jumplist configuration files can provide the examiner with a wealth of information relating to file access and in particular: dates/times, Volume GUIDs and unique file object IDs relating to those files. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -
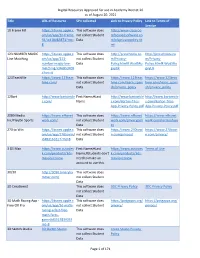
Digital Resources Approved for Use in Academy District 20 As Of
Digital Resources Approved for use in Academy District 20 as of August 20, 2021 Title URL of Resource SPII collected Link to Privacy Policy Link to Terms of Service 10 Frame Fill https://itunes.apple.c This software does http://www.classroo om/us/app/10-frame- not collect Student mfocusedsoftware.co fill/id418083871?mt= Data m/cfsprivacypolicy.ht 8 ml 123 NUMBER MAGIC https://itunes.apple.c This software does http://preschoolu.co http://preschoolu.co Line Matching om/us/app/123- not collect Student m/Privacy- m/Privacy- number-magic-line- Data Policy.html#.Wud5Ro Policy.html#.Wud5Ro matching/id46853409 gvyUk gvyUk 4?mt=8 123TeachMe https://www.123teac This software does https://www.123teac https://www.123teac hme.com/ not collect Student hme.com/learn_spani hme.com/learn_spani Data sh/privacy_policy sh/privacy_policy 12Bart http://www.bartontile First Name;#Last http://www.bartontile http://www.bartontile s.com/ Name s.com/Barton-Tiles- s.com/Barton-Tiles- App-Privacy-Policy.pdf App-Privacy-Policy.pdf 2080 Media https://www.nfhsnet This software does https://www.nfhsnet https://www.nfhsnet Inc/PlayOn Sports work.com/ not collect Student work.com/privacypoli work.com/termsofuse Data cy 270 to Win https://itunes.apple.c This software does https://www.270towi https://www.270towi om/us/app/270towin/ not collect Student n.com/privacy/ n.com/privacy/ id483161617?mt=8 Data 3 DS Max https://www.autodes First Name;#Last https://www.autodes Terms of Use k.com/products/3ds- Name;#Students don't k.com/products/3ds- max/overview need to make an max/overview account to use this. -

Learning the Vi Editor
Learning the vi Editor en.wikibooks.org December 29, 2013 On the 28th of April 2012 the contents of the English as well as German Wikibooks and Wikipedia projects were licensed under Creative Commons Attribution-ShareAlike 3.0 Unported license. A URI to this license is given in the list of figures on page 103. If this document is a derived work from the contents of one of these projects and the content was still licensed by the project under this license at the time of derivation this document has to be licensed under the same, a similar or a compatible license, as stated in section 4b of the license. The list of contributors is included in chapter Contributors on page 101. The licenses GPL, LGPL and GFDL are included in chapter Licenses on page 107, since this book and/or parts of it may or may not be licensed under one or more of these licenses, and thus require inclusion of these licenses. The licenses of the figures are given in the list of figures on page 103. This PDF was generated by the LATEX typesetting software. The LATEX source code is included as an attachment (source.7z.txt) in this PDF file. To extract the source from the PDF file, you can use the pdfdetach tool including in the poppler suite, or the http://www. pdflabs.com/tools/pdftk-the-pdf-toolkit/ utility. Some PDF viewers may also let you save the attachment to a file. After extracting it from the PDF file you have to rename it to source.7z. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard Filesystem Hierarchy Standard Group Edited by Rusty Russell Daniel Quinlan Filesystem Hierarchy Standard by Filesystem Hierarchy Standard Group Edited by Rusty Russell and Daniel Quinlan Published November 4 2003 Copyright © 1994-2003 Daniel Quinlan Copyright © 2001-2003 Paul ’Rusty’ Russell Copyright © 2003 Christopher Yeoh This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Table of Contents 1. Introduction........................................................................................................................................................1 1.1. -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

The OS/2 Warp 4 CID Software Distribution Guide
SG24-2010-00 International Technical Support Organization The OS/2 Warp 4 CID Software Distribution Guide January 1998 Take Note! Before using this information and the product it supports, be sure to read the general information in Appendix D, “Special Notices” on page 513. First Edition (January 1998) This edition applies to OS/2 Warp 4 in a software distribution environment and to NetView Distribution Manager/2 (NVDM/2) with Database 2 (DB2) Version 2.11 for OS/2 and Tivoli TME 10 Software Distribution 3.1.3 for OS/2 (SD4OS2) software distribution managers. This edition also applies to OS/2 Warp 4 subcomponents, such as TCP/IP 4.0, MPTS, NetFinity 4.0, Peer Services, and LAN Distance, and to OS/2- related products, such as eNetwork Personal Communications for OS/2 Warp, eNetwork Communications Server for OS/2 Warp, Transaction Server, Lotus Notes, and Lotus SmartStuite 96 for OS/2 Warp. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. DHHB Building 045 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 1998. All rights reserved Note to U.S Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures. .xiii Tables. xvii Preface. .xix How This Redbook in Organized . -

OS/2 Workplace Shell Configuration Techniques
OS/2 Workplace Shell Configuration Techniques Document Number GG24-4201-00 August 1994 International Technical Support Organization Boca Raton Center Take Note! Before using this information and the product it supports, be sure to read the general information under “Special Notices” on page xvii. First Edition (August 1994) This edition applies to OS/2 Version 2.1. Order publications through your IBM representative or the IBM branch office serving your locality. Publications are not stocked at the address given below. An ITSO Technical Bulletin Evaluation Form for reader′s feedback appears facing Chapter 1. If the form has been removed, comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. 91J, Building 235-2 Internal Zip 4423 901 NW 51st Street Boca Raton, Florida 33431-1328 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1994. All rights reserved. Note to U.S. Government Users — Documentation related to restricted rights — Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Abstract This document describes interfaces to the Workplace Shell of OS/2 Version 2.1. It provides a discussion and examples of using the CONFIG.SYS, .RC files, .INI files and programs to install, customize and distribute the OS/2 Workplace Shell in a stand-alone and distributed environment. This document was written for IBM Technical Professionals. Some knowledge of OS/2 is assumed. -

Webobjects Technical Overview
Session 401 WebObjects Technical Overview Steve Hayman Systems Engineer, Apple iServices 1 Apple Confidential 6/28/00 Introduction • Understand the WO architecture • See the tools, frameworks, and development process in action 2 Apple Confidential 6/28/00 What You’ll Learn • WO Tools • WO Frameworks • WO Deployment • Understand the titles of the other WO sessions 406—Rapid Development with Direct to Java Client 3 Apple Confidential 6/28/00 What WebObjects Does • It’s an Application Server • Who invented that term anyway? • It’s more than just that – Developer Tools – Pre-written objects (Frameworks) The best part! – Runtime environment – Monitoring and control tools 4 Apple Confidential 6/28/00 For Instance Java Clients Web Browsers Data Services Web Servers Distributed Objects Data Sources 5 Apple Confidential 6/28/00 Who WebObjects Is For • Developers • Very powerful • Steep learning curve • But that’s OK 6 Apple Confidential 6/28/00 WebObjects Works With… • Java. Objective-C. WebScript • Databases—Oracle, Informix, Sybase, SQL Server, LDAP, OpenBase, FrontBase, … • Mainframes—CORBA, 3270 screen-scraping • Different UIs—HTML, WAP, PDF, XML • Most web servers—Apache, Netscape, IIS • Lots of 3rd-party objects and APIs • Open open open open open open open open 7 Apple Confidential 6/28/00 Where You Can Use WebObjects • Develop on Mac OS X, Mac OS X Server, or Windows NT • Deploy on OS X, OS X Server, NT, Solaris, HP/UX, Linux – (Note: database support varies by platform) • Mix and match as needed • Start small and grow bigger 8 Apple Confidential -

Plugin Tapestry
PlugIn Tapestry Autor @picodotdev https://picodotdev.github.io/blog-bitix/ 2019 1.4.2 5.4 A tod@s l@s programador@s que en su trabajo no pueden usar el framework, librería o lenguaje que quisieran. Y a las que se divierten programando y aprendiendo hasta altas horas de la madrugada. Non gogoa, han zangoa Hecho con un esfuerzo en tiempo considerable con una buena cantidad de software libre y más ilusión en una región llamada Euskadi. PlugIn Tapestry: Desarrollo de aplicaciones y páginas web con Apache Tapestry @picodotdev 2014 - 2019 2 Prefacio Empecé El blog de pico.dev y unos años más tarde Blog Bitix con el objetivo de poder aprender y compartir el conocimiento de muchas cosas que me interesaban desde la programación y el software libre hasta análisis de los productos tecnológicos que caen en mis manos. Las del ámbito de la programación creo que usándolas pueden resolver en muchos casos los problemas típicos de las aplicaciones web y que encuentro en el día a día en mi trabajo como desarrollador. Sin embargo, por distintas circunstancias ya sean propias del cliente, la empresa o las personas es habitual que solo me sirvan meramente como satisfacción de adquirir conocimientos. Hasta el día de hoy una de ellas es el tema del que trata este libro, Apache Tapestry. Para escribir en el blog solo dependo de mí y de ninguna otra circunstancia salvo mi tiempo personal, es com- pletamente mío con lo que puedo hacer lo que quiera con él y no tengo ninguna limitación para escribir y usar cualquier herramienta, aunque en un principio solo sea para hacer un ejemplo muy sencillo, en el momento que llegue la oportunidad quizá me sirva para aplicarlo a un proyecto real. -

JSON Config Documentation
JSON Config Documentation Release 0.3 Brian Peterson Jul 17, 2018 Contents: 1 Welcome to JSON Config 1 1.1 Installation................................................1 1.2 What’s it Used For?...........................................1 1.3 Basic Example..............................................1 1.4 Easy Access...............................................2 1.5 Designed with Stability in Mind.....................................2 1.6 Consistency across Multiple Sources of Configuration Data......................2 2 JSON Config Examples 3 2.1 Storing & Retrieving Database Server Settings.............................3 2.2 Storing & Retrieving the Current State of a Game............................3 2.3 Making a Request from a Restful API Settings File...........................4 3 Configuration File Basics 7 3.1 Definition.................................................7 3.2 Most Interesting Programs Need Some Kind of Configuration.....................7 4 Serialization 9 4.1 Definition.................................................9 4.2 Python Data Type Conversions......................................9 5 Configuration File Locations 11 5.1 App Dir Options............................................. 12 5.2 The Three (3) File Location Patterns................................... 12 5.3 Missing Directories........................................... 12 5.4 Missing Files............................................... 12 6 The JSON Sandwich 13 7 Data Served in the Wrapper of Your Choice 15 7.1 Shortcuts................................................