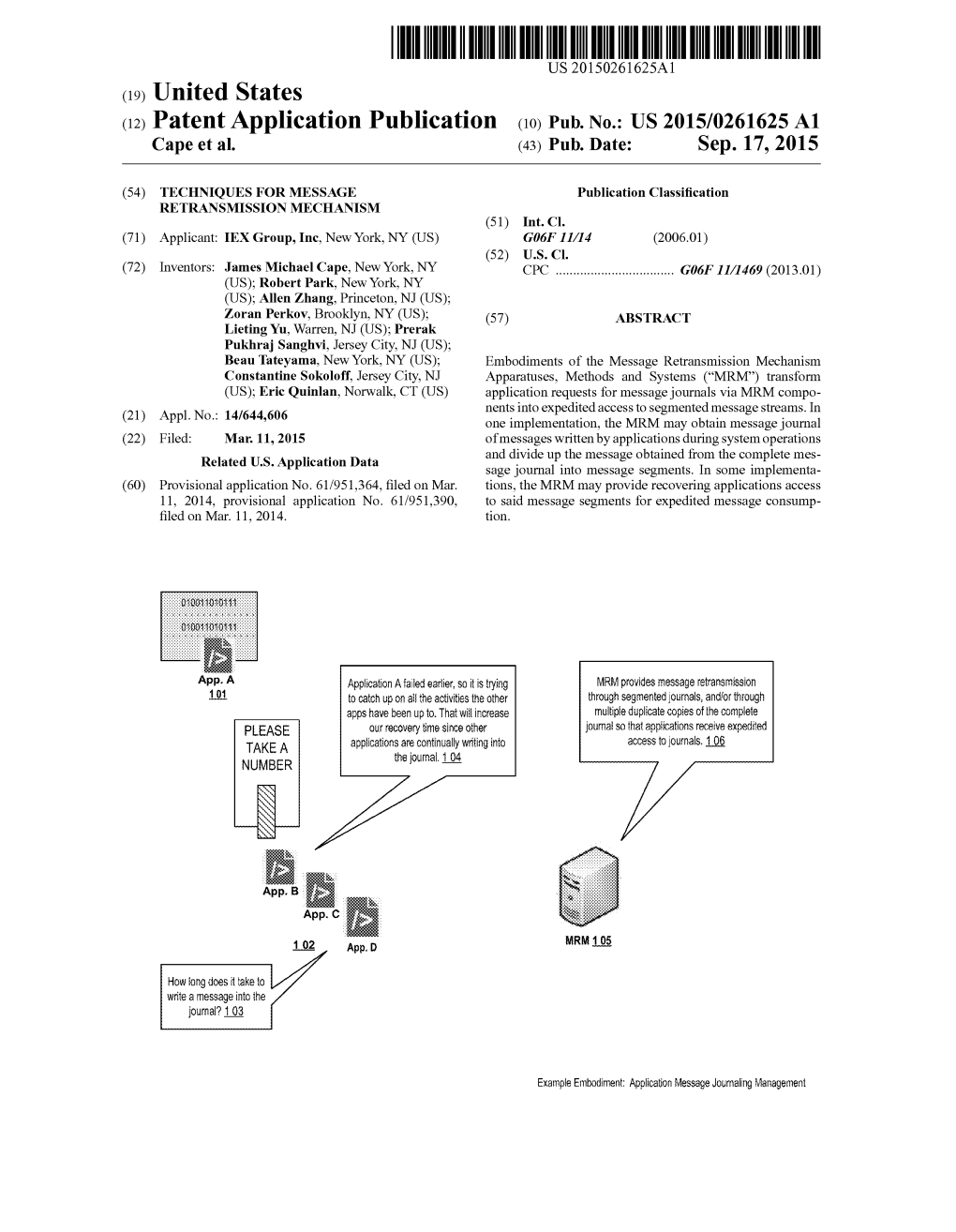
(2) Patent Application Publication (10) Pub. No.: US 2015/0261625A1 Cape Et Al
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Designing PCI Cards and Drivers for Power Macintosh Computers
Designing PCI Cards and Drivers for Power Macintosh Computers Revised Edition Revised 3/26/99 Technical Publications © Apple Computer, Inc. 1999 Apple Computer, Inc. Adobe, Acrobat, and PostScript are Even though Apple has reviewed this © 1995, 1996 , 1999 Apple Computer, trademarks of Adobe Systems manual, APPLE MAKES NO Inc. All rights reserved. Incorporated or its subsidiaries and WARRANTY OR REPRESENTATION, EITHER EXPRESS OR IMPLIED, WITH No part of this publication may be may be registered in certain RESPECT TO THIS MANUAL, ITS reproduced, stored in a retrieval jurisdictions. QUALITY, ACCURACY, system, or transmitted, in any form America Online is a service mark of MERCHANTABILITY, OR FITNESS or by any means, mechanical, Quantum Computer Services, Inc. FOR A PARTICULAR PURPOSE. AS A electronic, photocopying, recording, Code Warrior is a trademark of RESULT, THIS MANUAL IS SOLD “AS or otherwise, without prior written Metrowerks. IS,” AND YOU, THE PURCHASER, ARE permission of Apple Computer, Inc., CompuServe is a registered ASSUMING THE ENTIRE RISK AS TO except to make a backup copy of any trademark of CompuServe, Inc. ITS QUALITY AND ACCURACY. documentation provided on Ethernet is a registered trademark of CD-ROM. IN NO EVENT WILL APPLE BE LIABLE Xerox Corporation. The Apple logo is a trademark of FOR DIRECT, INDIRECT, SPECIAL, FrameMaker is a registered Apple Computer, Inc. INCIDENTAL, OR CONSEQUENTIAL trademark of Frame Technology Use of the “keyboard” Apple logo DAMAGES RESULTING FROM ANY Corporation. (Option-Shift-K) for commercial DEFECT OR INACCURACY IN THIS purposes without the prior written Helvetica and Palatino are registered MANUAL, even if advised of the consent of Apple may constitute trademarks of Linotype-Hell AG possibility of such damages. -
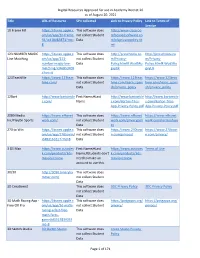
Digital Resources Approved for Use in Academy District 20 As Of
Digital Resources Approved for use in Academy District 20 as of August 20, 2021 Title URL of Resource SPII collected Link to Privacy Policy Link to Terms of Service 10 Frame Fill https://itunes.apple.c This software does http://www.classroo om/us/app/10-frame- not collect Student mfocusedsoftware.co fill/id418083871?mt= Data m/cfsprivacypolicy.ht 8 ml 123 NUMBER MAGIC https://itunes.apple.c This software does http://preschoolu.co http://preschoolu.co Line Matching om/us/app/123- not collect Student m/Privacy- m/Privacy- number-magic-line- Data Policy.html#.Wud5Ro Policy.html#.Wud5Ro matching/id46853409 gvyUk gvyUk 4?mt=8 123TeachMe https://www.123teac This software does https://www.123teac https://www.123teac hme.com/ not collect Student hme.com/learn_spani hme.com/learn_spani Data sh/privacy_policy sh/privacy_policy 12Bart http://www.bartontile First Name;#Last http://www.bartontile http://www.bartontile s.com/ Name s.com/Barton-Tiles- s.com/Barton-Tiles- App-Privacy-Policy.pdf App-Privacy-Policy.pdf 2080 Media https://www.nfhsnet This software does https://www.nfhsnet https://www.nfhsnet Inc/PlayOn Sports work.com/ not collect Student work.com/privacypoli work.com/termsofuse Data cy 270 to Win https://itunes.apple.c This software does https://www.270towi https://www.270towi om/us/app/270towin/ not collect Student n.com/privacy/ n.com/privacy/ id483161617?mt=8 Data 3 DS Max https://www.autodes First Name;#Last https://www.autodes Terms of Use k.com/products/3ds- Name;#Students don't k.com/products/3ds- max/overview need to make an max/overview account to use this. -

Power Macintosh 9500 Series
K Service Source Power Macintosh 9500 Series Power Macintosh 9500/120, 9500/132, 9500/150, 9500/180MP, and 9500/200 K Service Source Basics Power Macintosh 9500 Series Basics Overview - 1 Overview The Power Macintosh 9500 Series computers are based on the PowerPC 604 microprocessor and support the industry-standard PCI (Peripheral Component Interconnect) bus specification. These computers are the most flexible, expandable, and highest-performance systems from Apple to date. The microprocessor for the Power Macintosh 9500 Series computers is on separate plug-in card, which allows for easy upgrades. The Power Macintosh 9500 family includes five versions: the 9500/120, the 9500/132, the 9500/150, the 9500/180MP (multi-processor), and the 9500/200. Basics Overview - 2 Features of the Power Macintosh 9500 Series include • 120, 132, 150, 180 (multi-processor) or 200 MHz PowerPC 604 microprocessor card with built-in FPU • Six PCI expansion slots • 10 MB per second internal SCSI channel, 5 MB per second external SCSI channel • 512K Level 2 cache • DRAM expansion up to 1536 MB using 168-pin, 70 ns, 64-bit DIMMs • A PCI Apple Accelerated Graphics card included with some configurations (the Power Macintosh 9500 Series does not include on-board video support) • Built-in AAUI and 10BASE-T Ethernet • AppleCD™ 600i 4x or1200i 8x CD-ROM drive • CD-quality stereo sound in/out • Mac™ OS system software 7.5.2, 7.5.3, or 7.5.3 Revision 2 Basics Configurations - 3 Configurations The Power Macintosh 9500/120 comes standard with • 120 MHz PowerPC 604 processor -

USB Converter MT606 Series
USB Converter MT606 Series FEATURES: Use with Keyboard Wedge Scanners Use with Keyboard and Mouse PS/2 and MAC-ADB Port Powered by PC or MAC Connect/Disconnect Without Reboot Plug and Play No Software Needed DESCRIPTION: The MT606 Series USB Converters provide an easy solution for converting existing peripherals, such as keyboards, pointing devices and barcode scanners, to Universal Serial Bus. Models are available to work with both PS/2 and Macintosh devices. As with all USB devices, the converter can be connected and disconnected without re-booting or powering down the computer. Each model has two ports. The MT606-4 has one PS/2 port and one Macintosh ADB (Apple Desktop Bus) port. The MT606-1 has one PS/2 keyboard port and one PS/2 Mouse port. TYPICAL APPLICATIONS: The MT606 converter will enable keyboards, pointing devices (mouse, trackball), and conventional barcode scanners with keyboard wedge interfaces, to be used with computers that feature the newer Universal Serial BUS. At present, newer PCs with the Windows® 98 and Windows 2000 operating systems, feature USB Ports. The Apple iMac, iBook, G3 and G4 use Universal Serial Bus for interfacing to external devices. The Model MT606-1 can accept inputs from a PS/2 Pointing Device and a PS/2 Keyboard or Barcode Scanner. The MT606-4 can accept inputs from a PS/2 keyboard or barcode scanner and any Macintosh ADB device, including Keyboard, Pointing Device or Barcode Scanner. SPECIFICATIONS: Dimensions: 2.2" X 1.5" X 0.85" Operating Voltage: 5VDC derived from USB 56mm X 40mm X 22mm connector. -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

Webobjects Technical Overview
Session 401 WebObjects Technical Overview Steve Hayman Systems Engineer, Apple iServices 1 Apple Confidential 6/28/00 Introduction • Understand the WO architecture • See the tools, frameworks, and development process in action 2 Apple Confidential 6/28/00 What You’ll Learn • WO Tools • WO Frameworks • WO Deployment • Understand the titles of the other WO sessions 406—Rapid Development with Direct to Java Client 3 Apple Confidential 6/28/00 What WebObjects Does • It’s an Application Server • Who invented that term anyway? • It’s more than just that – Developer Tools – Pre-written objects (Frameworks) The best part! – Runtime environment – Monitoring and control tools 4 Apple Confidential 6/28/00 For Instance Java Clients Web Browsers Data Services Web Servers Distributed Objects Data Sources 5 Apple Confidential 6/28/00 Who WebObjects Is For • Developers • Very powerful • Steep learning curve • But that’s OK 6 Apple Confidential 6/28/00 WebObjects Works With… • Java. Objective-C. WebScript • Databases—Oracle, Informix, Sybase, SQL Server, LDAP, OpenBase, FrontBase, … • Mainframes—CORBA, 3270 screen-scraping • Different UIs—HTML, WAP, PDF, XML • Most web servers—Apache, Netscape, IIS • Lots of 3rd-party objects and APIs • Open open open open open open open open 7 Apple Confidential 6/28/00 Where You Can Use WebObjects • Develop on Mac OS X, Mac OS X Server, or Windows NT • Deploy on OS X, OS X Server, NT, Solaris, HP/UX, Linux – (Note: database support varies by platform) • Mix and match as needed • Start small and grow bigger 8 Apple Confidential -

Plugin Tapestry
PlugIn Tapestry Autor @picodotdev https://picodotdev.github.io/blog-bitix/ 2019 1.4.2 5.4 A tod@s l@s programador@s que en su trabajo no pueden usar el framework, librería o lenguaje que quisieran. Y a las que se divierten programando y aprendiendo hasta altas horas de la madrugada. Non gogoa, han zangoa Hecho con un esfuerzo en tiempo considerable con una buena cantidad de software libre y más ilusión en una región llamada Euskadi. PlugIn Tapestry: Desarrollo de aplicaciones y páginas web con Apache Tapestry @picodotdev 2014 - 2019 2 Prefacio Empecé El blog de pico.dev y unos años más tarde Blog Bitix con el objetivo de poder aprender y compartir el conocimiento de muchas cosas que me interesaban desde la programación y el software libre hasta análisis de los productos tecnológicos que caen en mis manos. Las del ámbito de la programación creo que usándolas pueden resolver en muchos casos los problemas típicos de las aplicaciones web y que encuentro en el día a día en mi trabajo como desarrollador. Sin embargo, por distintas circunstancias ya sean propias del cliente, la empresa o las personas es habitual que solo me sirvan meramente como satisfacción de adquirir conocimientos. Hasta el día de hoy una de ellas es el tema del que trata este libro, Apache Tapestry. Para escribir en el blog solo dependo de mí y de ninguna otra circunstancia salvo mi tiempo personal, es com- pletamente mío con lo que puedo hacer lo que quiera con él y no tengo ninguna limitación para escribir y usar cualquier herramienta, aunque en un principio solo sea para hacer un ejemplo muy sencillo, en el momento que llegue la oportunidad quizá me sirva para aplicarlo a un proyecto real. -

Table of Contents Feature Article
RLG DigiNews: Volume 4, Number 3 Table of Contents ● Feature Article ❍ Keeping Memory Alive: Practices for Preserving Digital Content at the National Digital Library Program of the Library of Congress by Caroline R. Arms ● Technical Feature ❍ Risk Management of Digital Information: a File Format Investigation ● Highlighted Web Site - TechFest ● FAQ - SCSI, UDMA, USB, and Firewire Technology ● Calendar of Events ● Announcements ● RLG News ● Hotlinks Included in This Issue Feature Article Keeping Memory Alive: Practices for Preserving Digital Content at the National Digital Library Program of the Library of Congress by Caroline R. Arms, National Digital Library Program & Information Technology Services, Library of Congress [email protected] Introduction The National Digital Library Program (NDLP) provides remote public access to unique collections of Americana held by the Library of Congress through American Memory. During the 1990s, the program digitized materials from a wide variety of original sources, including pictorial and textual materials, audio, http://www.rlg.org/preserv/diginews/diginews4-3.html (1 of 24)6/21/2005 1:31:04 PM RLG DigiNews: Volume 4, Number 3 video, maps, atlases, and sheet music. Monographs and serials comprise a very small proportion of the textual materials converted. The program's emphasis has been on enhancing access. No digitization has been conducted with the intent of replacing the original materials; indeed, great care is taken over handling fragile and unique resources and conservation steps often precede scanning. (1) Nevertheless, these digital resources represent a significant investment, and the Library is concerned that they continue to be usable over the long term. The practices described here should not be seen as policies of the Library of Congress; nor are they suggested as best practices in any absolute sense. -
Ish Case Study Ish Hires Objectstyle to Modernise Its Student Management Platform, Grows Business by 300% in the Course of 5 Years
ish Case Study ish hires ObjectStyle to modernise its student management platform, grows business by 300% in the course of 5 years ish is the company behind onCourse™, a widely-used software platform Company: that allows colleges and short course providers to manage enrolments, curricula, student grades, and other aspects of the learning/teaching Company name: ish process. Industry: Education The platform serves dozens of educational entities in Australia (including Year founded: 2002 such heavyweights as The University of Sydney, Sydney Community College, NIDA, Coffee School, Power Training Services WA...), and is one of Location: Australia the most popular solutions in the market. Website: http://ish.com.au Challenge In the year 2011, the onCourse platform was 5 years old and needed major refactoring to modernise the code, improve performance and set a new direction for future development. ish wanted to revamp the content management system and the student/tutor portal components as well as make it easy to add new features. ish had originally chosen WebObjects as a web platform and that tool had been largely abandoned, so a change of technology was needed. ish was also picking up big new customers, including universities, that required the production servers to be able to scale with increased volume. Solution 1. Apache Tapestry-based custom CMS. Colleges received an improved, more feature-rich and flexible content management system (CMS) which they could use for publishing catalogues, individual courses, promotions, and other CMS elements. The revamped CMS provided additional space for customizing the look-and-feel as well as the layout of the materials that colleges put up on their websites. -

Theory of Operation Power Macintosh
K Service Source Theory of Operation Power Macintosh Theory of Operation Introduction - 1 Introduction This section contains information about how the Power Macintosh operates. The Power Macintosh components work together to provide these general functions: • Central processing and control • Memory • Input/output (I/O) • Video and sound As you read this section, refer to the Power Macintosh Block Diagram, which shows the relationship of the components in Power Macintosh computers. Theory of Operation Introduction - 2 Specific functions of Power Macintosh components are covered in sections about • Power supply • Apple SuperDrive • SCSI hard drive • Internal mass storage devices • Main logic board • Expansion cards • System startup sequence Theory of Operation Central Processing and Control - 3 Central Processing and Control Processing and control logic in all Power Macintosh models are handled by the central processing unit (CPU) with the built-in math coprocessor and digital signal processor (DSP). Additional control signals are generated by the high- speed memory controller (HMC), Apple Memory Mapped I/O Controller (AMIC), and other components. The Squidlet Chip provides the system clocks. Theory of Operation Central Processing and Control - 4 CPU The main processor in the Power Macintosh computers is a PowerPC 601 microprocessor. Features of the PowerPC 601 microprocessor include • Full reduced instruction set computing (RISC) processing architecture • Parallel integer and floating-point processing units • An internal memory management unit (MMU) • 32 Kbits of on-chip cache memory The PowerPC 601 is a 32-bit address bus and a 64-bit data bus microprocessor. Theory of Operation Central Processing and Control - 5 FPU The PowerPC 601 includes a floating-point unit (FPU). -

Power Macintosh 4400
Developer Note Power Macintosh 4400 1/29/97 © Apple Computer, Inc. 1997 Apple Computer, Inc. LIMITED WARRANTY ON MEDIA AND © 1997 Apple Computer, Inc. REPLACEMENT All rights reserved. If you discover physical defects in the No part of this publication may be manual or in the media on which a software reproduced, stored in a retrieval product is distributed, ADC will replace the system, or transmitted, in any form or media or manual at no charge to you by any means, mechanical, electronic, provided you return the item to be replaced photocopying, recording, or otherwise, with proof of purchase to ADC. without prior written permission of ALL IMPLIED WARRANTIES ON THIS Apple Computer, Inc., except to make a MANUAL, INCLUDING IMPLIED backup copy of any documentation WARRANTIES OF MERCHANTABILITY provided on CD-ROM. AND FITNESS FOR A PARTICULAR The Apple logo is a trademark of PURPOSE, ARE LIMITED IN DURATION Apple Computer, Inc. TO NINETY (90) DAYS FROM THE DATE Use of the “keyboard” Apple logo OF THE ORIGINAL RETAIL PURCHASE (Option-Shift-K) for commercial OF THIS PRODUCT. purposes without the prior written consent of Apple may constitute Even though Apple has reviewed this trademark infringement and unfair manual, APPLE MAKES NO WARRANTY competition in violation of federal and OR REPRESENTATION, EITHER EXPRESS state laws. OR IMPLIED, WITH RESPECT TO THIS MANUAL, ITS QUALITY, ACCURACY, No licenses, express or implied, are MERCHANTABILITY, OR FITNESS FOR A granted with respect to any of the PARTICULAR PURPOSE. AS A RESULT, technology described in this book. THIS MANUAL IS SOLD “AS IS,” AND Apple retains all intellectual property YOU, THE PURCHASER, ARE ASSUMING rights associated with the technology THE ENTIRE RISK AS TO ITS QUALITY described in this book. -

Webobjects Developer's Guide
WEBOBJECTS DEVELOPER’S GUIDE Apple,NeXT, and the publishers have tried to make the information contained in this manual as accurate and reliable as possible, but assume no responsibility for errors or omissions. They disclaim any warranty of any kind, whether express or implied, as to any matter whatsoever relating to this manual, including without limitation the merchantability or fitness for any particular purpose. In no event shall they be liable for any indirect, special, incidental, or consequential damages arising out of purchase or use of this manual or the information contained herein. NeXT or Apple will from time to time revise the software described in this manual and reserves the right to make such changes without obligation to notify the purchaser. Copyright 1997 by Apple Computer, Inc., 1 Infinite Loop, Cupertino, CA 95014. All rights reserved. [7010.01] No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher or copyright owner. Printed in the United States of America. Published simultaneously in Canada. NeXT, the NeXT logo, OPENSTEP, Enterprise Objects, EOF, Enterprise Objects Framework, ProjectBuilder, Objective-C, Portable Distributed Objects, Workspace Manager, Database Wizard, WEBSCRIPT, and WEBOBJECTS are trademarks of NeXT Software, Inc. PostScript is a registered trademark of Adobe Systems, Incorporated. Windows NT is a trademark of Microsoft Corporation. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company Limited. ORACLE is a registered trademark of Oracle Corporation, Inc.