Abelian Varieties in Coding and Cryptography
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Uniqueness of Gibbs States in the Pirogov-Sinai Theory?
Commun. Math. Phys. 189, 311 – 321 (1997) Communications in Mathematical Physics c Springer-Verlag 1997 On the Uniqueness of Gibbs States in the Pirogov-Sinai Theory? J.L. Lebowitz1, A.E. Mazel2 1 Department of Mathematics and Physics, Rutgers University, New Brunswick, NJ 08903, USA 2 International Institute of Earthquake Prediction Theory and Mathematical Geophysics, Russian Academy of Sciences, Moscow 113556, Russia Received: 4 June 1996 / Accepted: 30 October 1996 Dedicated to the memory of Roland Dobrushin Abstract: We prove that, for low-temperature systems considered in the Pirogov-Sinai theory, uniqueness in the class of translation-periodic Gibbs states implies global unique- ness, i.e. the absence of any non-periodic Gibbs state. The approach to this infinite volume state is exponentially fast. 1. Introduction The problem of uniqueness of Gibbs states was one of R.L.Dobrushin’s favorite subjects in which he obtained many classical results. In particular when two or more translati- on-periodic states coexist, it is natural to ask whether there might also exist other, non translation-periodic, Gibbs states, which approach asymptotically, in different spatial directions, the translation periodic ones. The affirmative answer to this question was given by R.L.Dobrushin with his famous construction of such states for the Ising model, using boundary conditions, in three and higher dimensions [D]. Here we consider the opposite± situation: we will prove that in the regions of the low-temperature phase diagram where there is a unique translation-periodic Gibbs state one actually has global uniqueness of the limit Gibbs state. Moreover we show that, uniformly in boundary conditions, the finite volume probability of any local event tends to its infinite volume limit value exponentially fast in the diameter of the domain. -

Digital Communication Systems 2.2 Optimal Source Coding
Digital Communication Systems EES 452 Asst. Prof. Dr. Prapun Suksompong [email protected] 2. Source Coding 2.2 Optimal Source Coding: Huffman Coding: Origin, Recipe, MATLAB Implementation 1 Examples of Prefix Codes Nonsingular Fixed-Length Code Shannon–Fano code Huffman Code 2 Prof. Robert Fano (1917-2016) Shannon Award (1976 ) Shannon–Fano Code Proposed in Shannon’s “A Mathematical Theory of Communication” in 1948 The method was attributed to Fano, who later published it as a technical report. Fano, R.M. (1949). “The transmission of information”. Technical Report No. 65. Cambridge (Mass.), USA: Research Laboratory of Electronics at MIT. Should not be confused with Shannon coding, the coding method used to prove Shannon's noiseless coding theorem, or with Shannon–Fano–Elias coding (also known as Elias coding), the precursor to arithmetic coding. 3 Claude E. Shannon Award Claude E. Shannon (1972) Elwyn R. Berlekamp (1993) Sergio Verdu (2007) David S. Slepian (1974) Aaron D. Wyner (1994) Robert M. Gray (2008) Robert M. Fano (1976) G. David Forney, Jr. (1995) Jorma Rissanen (2009) Peter Elias (1977) Imre Csiszár (1996) Te Sun Han (2010) Mark S. Pinsker (1978) Jacob Ziv (1997) Shlomo Shamai (Shitz) (2011) Jacob Wolfowitz (1979) Neil J. A. Sloane (1998) Abbas El Gamal (2012) W. Wesley Peterson (1981) Tadao Kasami (1999) Katalin Marton (2013) Irving S. Reed (1982) Thomas Kailath (2000) János Körner (2014) Robert G. Gallager (1983) Jack KeilWolf (2001) Arthur Robert Calderbank (2015) Solomon W. Golomb (1985) Toby Berger (2002) Alexander S. Holevo (2016) William L. Root (1986) Lloyd R. Welch (2003) David Tse (2017) James L. -

Transnational Mathematics and Movements: Shiing- Shen Chern, Hua Luogeng, and the Princeton Institute for Advanced Study from World War II to the Cold War1
Chinese Annals of History of Science and Technology 3 (2), 118–165 (2019) doi: 10.3724/SP.J.1461.2019.02118 Transnational Mathematics and Movements: Shiing- shen Chern, Hua Luogeng, and the Princeton Institute for Advanced Study from World War II to the Cold War1 Zuoyue Wang 王作跃,2 Guo Jinhai 郭金海3 (California State Polytechnic University, Pomona 91768, US; Institute for the History of Natural Sciences, Chinese Academy of Sciences, Beijing 100190, China) Abstract: This paper reconstructs, based on American and Chinese primary sources, the visits of Chinese mathematicians Shiing-shen Chern 陈省身 (Chen Xingshen) and Hua Luogeng 华罗庚 (Loo-Keng Hua)4 to the Institute for Advanced Study in Princeton in the United States in the 1940s, especially their interactions with Oswald Veblen and Hermann Weyl, two leading mathematicians at the IAS. It argues that Chern’s and Hua’s motivations and choices in regard to their transnational movements between China and the US were more nuanced and multifaceted than what is presented in existing accounts, and that socio-political factors combined with professional-personal ones to shape their decisions. The paper further uses their experiences to demonstrate the importance of transnational scientific interactions for the development of science in China, the US, and elsewhere in the twentieth century. Keywords: Shiing-shen Chern, Chen Xingshen, Hua Luogeng, Loo-Keng Hua, Institute for 1 This article was copy-edited by Charlie Zaharoff. 2 Research interests: History of science and technology in the United States, China, and transnational contexts in the twentieth century. He is currently writing a book on the history of American-educated Chinese scientists and China-US scientific relations. -
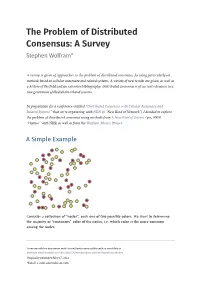
The Problem of Distributed Consensus: a Survey Stephen Wolfram*
The Problem of Distributed Consensus: A Survey Stephen Wolfram* A survey is given of approaches to the problem of distributed consensus, focusing particularly on methods based on cellular automata and related systems. A variety of new results are given, as well as a history of the field and an extensive bibliography. Distributed consensus is of current relevance in a new generation of blockchain-related systems. In preparation for a conference entitled “Distributed Consensus with Cellular Automata and Related Systems” that we’re organizing with NKN (= “New Kind of Network”) I decided to explore the problem of distributed consensus using methods from A New Kind of Science (yes, NKN “rhymes” with NKS) as well as from the Wolfram Physics Project. A Simple Example Consider a collection of “nodes”, each one of two possible colors. We want to determine the majority or “consensus” color of the nodes, i.e. which color is the more common among the nodes. A version of this document with immediately executable code is available at writings.stephenwolfram.com/2021/05/the-problem-of-distributed-consensus Originally published May 17, 2021 *Email: [email protected] 2 | Stephen Wolfram One obvious method to find this “majority” color is just sequentially to visit each node, and tally up all the colors. But it’s potentially much more efficient if we can use a distributed algorithm, where we’re running computations in parallel across the various nodes. One possible algorithm works as follows. First connect each node to some number of neighbors. For now, we’ll just pick the neighbors according to the spatial layout of the nodes: The algorithm works in a sequence of steps, at each step updating the color of each node to be whatever the “majority color” of its neighbors is. -

Principles of Communications ECS 332
Principles of Communications ECS 332 Asst. Prof. Dr. Prapun Suksompong (ผศ.ดร.ประพันธ ์ สขสมปองุ ) [email protected] 1. Intro to Communication Systems Office Hours: Check Google Calendar on the course website. Dr.Prapun’s Office: 6th floor of Sirindhralai building, 1 BKD 2 Remark 1 If the downloaded file crashed your device/browser, try another one posted on the course website: 3 Remark 2 There is also three more sections from the Appendices of the lecture notes: 4 Shannon's insight 5 “The fundamental problem of communication is that of reproducing at one point either exactly or approximately a message selected at another point.” Shannon, Claude. A Mathematical Theory Of Communication. (1948) 6 Shannon: Father of the Info. Age Documentary Co-produced by the Jacobs School, UCSD- TV, and the California Institute for Telecommunic ations and Information Technology 7 [http://www.uctv.tv/shows/Claude-Shannon-Father-of-the-Information-Age-6090] [http://www.youtube.com/watch?v=z2Whj_nL-x8] C. E. Shannon (1916-2001) Hello. I'm Claude Shannon a mathematician here at the Bell Telephone laboratories He didn't create the compact disc, the fax machine, digital wireless telephones Or mp3 files, but in 1948 Claude Shannon paved the way for all of them with the Basic theory underlying digital communications and storage he called it 8 information theory. C. E. Shannon (1916-2001) 9 https://www.youtube.com/watch?v=47ag2sXRDeU C. E. Shannon (1916-2001) One of the most influential minds of the 20th century yet when he died on February 24, 2001, Shannon was virtually unknown to the public at large 10 C. -

The History of the Abel Prize and the Honorary Abel Prize the History of the Abel Prize
The History of the Abel Prize and the Honorary Abel Prize The History of the Abel Prize Arild Stubhaug On the bicentennial of Niels Henrik Abel’s birth in 2002, the Norwegian Govern- ment decided to establish a memorial fund of NOK 200 million. The chief purpose of the fund was to lay the financial groundwork for an annual international prize of NOK 6 million to one or more mathematicians for outstanding scientific work. The prize was awarded for the first time in 2003. That is the history in brief of the Abel Prize as we know it today. Behind this government decision to commemorate and honor the country’s great mathematician, however, lies a more than hundred year old wish and a short and intense period of activity. Volumes of Abel’s collected works were published in 1839 and 1881. The first was edited by Bernt Michael Holmboe (Abel’s teacher), the second by Sophus Lie and Ludvig Sylow. Both editions were paid for with public funds and published to honor the famous scientist. The first time that there was a discussion in a broader context about honoring Niels Henrik Abel’s memory, was at the meeting of Scan- dinavian natural scientists in Norway’s capital in 1886. These meetings of natural scientists, which were held alternately in each of the Scandinavian capitals (with the exception of the very first meeting in 1839, which took place in Gothenburg, Swe- den), were the most important fora for Scandinavian natural scientists. The meeting in 1886 in Oslo (called Christiania at the time) was the 13th in the series. -
![Ray Solomonoff, Founding Father of Algorithmic Information Theory [Obituary]](https://docslib.b-cdn.net/cover/3571/ray-solomonoff-founding-father-of-algorithmic-information-theory-obituary-493571.webp)
Ray Solomonoff, Founding Father of Algorithmic Information Theory [Obituary]
UvA-DARE (Digital Academic Repository) Ray Solomonoff, founding father of algorithmic information theory [Obituary] Vitanyi, P.M.B. DOI 10.3390/a3030260 Publication date 2010 Document Version Final published version Published in Algorithms Link to publication Citation for published version (APA): Vitanyi, P. M. B. (2010). Ray Solomonoff, founding father of algorithmic information theory [Obituary]. Algorithms, 3(3), 260-264. https://doi.org/10.3390/a3030260 General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:29 Sep 2021 Algorithms 2010, 3, 260-264; doi:10.3390/a3030260 OPEN ACCESS algorithms ISSN 1999-4893 www.mdpi.com/journal/algorithms Obituary Ray Solomonoff, Founding Father of Algorithmic Information Theory Paul M.B. Vitanyi CWI, Science Park 123, Amsterdam 1098 XG, The Netherlands; E-Mail: [email protected] Received: 12 March 2010 / Accepted: 14 March 2010 / Published: 20 July 2010 Ray J. -

The Intellectual Journey of Hua Loo-Keng from China to the Institute for Advanced Study: His Correspondence with Hermann Weyl
ISSN 1923-8444 [Print] Studies in Mathematical Sciences ISSN 1923-8452 [Online] Vol. 6, No. 2, 2013, pp. [71{82] www.cscanada.net DOI: 10.3968/j.sms.1923845220130602.907 www.cscanada.org The Intellectual Journey of Hua Loo-keng from China to the Institute for Advanced Study: His Correspondence with Hermann Weyl Jean W. Richard[a],* and Abdramane Serme[a] [a] Department of Mathematics, The City University of New York (CUNY/BMCC), USA. * Corresponding author. Address: Department of Mathematics, The City University of New York (CUN- Y/BMCC), 199 Chambers Street, N-599, New York, NY 10007-1097, USA; E- Mail: [email protected] Received: February 4, 2013/ Accepted: April 9, 2013/ Published: May 31, 2013 \The scientific knowledge grows by the thinking of the individual solitary scientist and the communication of ideas from man to man Hua has been of great value in this respect to our whole group, especially to the younger members, by the stimulus which he has provided." (Hermann Weyl in a letter about Hua Loo-keng, 1948).y Abstract: This paper explores the intellectual journey of the self-taught Chinese mathematician Hua Loo-keng (1910{1985) from Southwest Associ- ated University (Kunming, Yunnan, China)z to the Institute for Advanced Study at Princeton. The paper seeks to show how during the Sino C Japanese war, a genuine cross-continental mentorship grew between the prolific Ger- man mathematician Hermann Weyl (1885{1955) and the gifted mathemati- cian Hua Loo-keng. Their correspondence offers a profound understanding of a solidarity-building effort that can exist in the scientific community. -
![Arxiv:1306.1586V4 [Quant-Ph]](https://docslib.b-cdn.net/cover/3349/arxiv-1306-1586v4-quant-ph-643349.webp)
Arxiv:1306.1586V4 [Quant-Ph]
Strong converse for the classical capacity of entanglement-breaking and Hadamard channels via a sandwiched R´enyi relative entropy Mark M. Wilde∗ Andreas Winter†‡ Dong Yang†§ May 23, 2014 Abstract A strong converse theorem for the classical capacity of a quantum channel states that the probability of correctly decoding a classical message converges exponentially fast to zero in the limit of many channel uses if the rate of communication exceeds the classical capacity of the channel. Along with a corresponding achievability statement for rates below the capacity, such a strong converse theorem enhances our understanding of the capacity as a very sharp dividing line between achievable and unachievable rates of communication. Here, we show that such a strong converse theorem holds for the classical capacity of all entanglement-breaking channels and all Hadamard channels (the complementary channels of the former). These results follow by bounding the success probability in terms of a “sandwiched” R´enyi relative entropy, by showing that this quantity is subadditive for all entanglement-breaking and Hadamard channels, and by relating this quantity to the Holevo capacity. Prior results regarding strong converse theorems for particular covariant channels emerge as a special case of our results. 1 Introduction One of the most fundamental tasks in quantum information theory is the transmission of classical data over many independent uses of a quantum channel, such that, for a fixed rate of communica- tion, the error probability of the transmission decreases to zero in the limit of many channel uses. The maximum rate at which this is possible for a given channel is known as the classical capacity of the channel. -

Vector Quantization and Signal Compression the Kluwer International Series in Engineering and Computer Science
VECTOR QUANTIZATION AND SIGNAL COMPRESSION THE KLUWER INTERNATIONAL SERIES IN ENGINEERING AND COMPUTER SCIENCE COMMUNICATIONS AND INFORMATION THEORY Consulting Editor: Robert Gallager Other books in the series: Digital Communication. Edward A. Lee, David G. Messerschmitt ISBN: 0-89838-274-2 An Introduction to Cryptolog)'. Henk c.A. van Tilborg ISBN: 0-89838-271-8 Finite Fields for Computer Scientists and Engineers. Robert J. McEliece ISBN: 0-89838-191-6 An Introduction to Error Correcting Codes With Applications. Scott A. Vanstone and Paul C. van Oorschot ISBN: 0-7923-9017-2 Source Coding Theory.. Robert M. Gray ISBN: 0-7923-9048-2 Switching and TraffIC Theory for Integrated BroadbandNetworks. Joseph Y. Hui ISBN: 0-7923-9061-X Advances in Speech Coding, Bishnu Atal, Vladimir Cuperman and Allen Gersho ISBN: 0-7923-9091-1 Coding: An Algorithmic Approach, John B. Anderson and Seshadri Mohan ISBN: 0-7923-9210-8 Third Generation Wireless Information Networks, edited by Sanjiv Nanda and David J. Goodman ISBN: 0-7923-9128-3 VECTOR QUANTIZATION AND SIGNAL COMPRESSION by Allen Gersho University of California, Santa Barbara Robert M. Gray Stanford University ..... SPRINGER SCIENCE+BUSINESS" MEDIA, LLC Library of Congress Cataloging-in-Publication Data Gersho, A1len. Vector quantization and signal compression / by Allen Gersho, Robert M. Gray. p. cm. -- (K1uwer international series in engineering and computer science ; SECS 159) Includes bibliographical references and index. ISBN 978-1-4613-6612-6 ISBN 978-1-4615-3626-0 (eBook) DOI 10.1007/978-1-4615-3626-0 1. Signal processing--Digital techniques. 2. Data compression (Telecommunication) 3. Coding theory. 1. Gray, Robert M., 1943- . -

Obituary Roland Lvovich Dobrushin, 1929 – 1995
Obituary Roland Lvovich Dobrushin, 1929 ± 1995 Roland Lvovich Dobrushin, an outstanding scientist in the domain of probability theory, information theory and mathematical physics, died of cancer in Moscow, on November 12, 1995, at the age of 66. Dobrushin's premature decease is a tremendous loss to Russian and world science. Dobrushin was born on July 20, 1929 in Leningrad (St.-Petersburg). In early childhood he lost his father; his mother died when he was still a schoolboy. In 1936, after his father's death, the family moved to Moscow. In 1947, on leaving school, Dobrushin entered the Mechanico-Mathematical Department of Moscow Univer- sity and after graduating from it did postgraduate studies. Then, from 1955 to 1965, he worked at the Proba- bility Theory Section of the Mechanico-Mathematical Department of Moscow University, and since 1967 until his demise was Head of the Multicomponent Random Systems Laboratory, within the Institute for Information Transmission Problems of the Russian Academy of Sciences (the Academy of Sciences of the USSR). Since 1967 Dobrushin was a Professor in the Electromagnetic Waves Section of the Moscow Physics Technologies Institute and since 1991 he was a Professor in the Probability Theory Section at Moscow University as well. In 1955 Dobrushin presented his candidate's thesis, and in 1962 he took his Doctor's degree. Even as a schoolboy Dobrushin conceived an interest in mathematics and participated in school mathemat- ical contests where he won a number of prizes. While at the University Dobrushin was an active member of E.B. Dynkin's seminar 1 . On A.N. -

Jacob Wolfowitz 1910–1981
NATIONAL ACADEMY OF SCIENCES JACOB WOLFOWITZ 1910–1981 A Biographical Memoir by SHELEMYAHU ZACKS Any opinions expressed in this memoir are those of the author and do not necessarily reflect the views of the National Academy of Sciences. Biographical Memoirs, VOLUME 82 PUBLISHED 2002 BY THE NATIONAL ACADEMY PRESS WASHINGTON, D.C. JACOB WOLFOWITZ March 19, 1910–July 16, 1981 BY SHELEMYAHU ZACKS ACOB WOLFOWITZ, A GIANT among the founders of modern Jstatistics, will always be remembered for his originality, deep thinking, clear mind, excellence in teaching, and vast contributions to statistical and information sciences. I met Wolfowitz for the first time in 1957, when he spent a sab- batical year at the Technion, Israel Institute of Technology. I was at the time a graduate student and a statistician at the building research station of the Technion. I had read papers of Wald and Wolfowitz before, and for me the meeting with Wolfowitz was a great opportunity to associate with a great scholar who was very kind to me and most helpful. I took his class at the Technion on statistical decision theory. Outside the classroom we used to spend time together over a cup of coffee or in his office discussing statistical problems. He gave me a lot of his time, as though I was his student. His advice on the correct approach to the theory of statistics accompanied my development as statistician for many years to come. Later we kept in touch, mostly by correspondence and in meetings of the Institute of Mathematical Statistics. I saw him the last time in his office at the University of Southern Florida in Tampa, where he spent the last years 3 4 BIOGRAPHICAL MEMOIRS of his life.