Money Laundering and Terrorist Financing Awareness Handbook for Tax Examiners and Tax Auditors
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
View Document
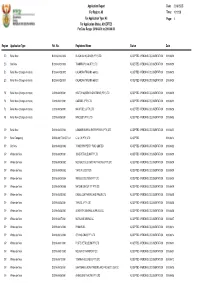
Application Report Date: 2016/05/05 For Region: All Time: 10:19:28 For Application Type: All Page: 1 For Application Status: ACCEPTED For Date Range: 2016/04/01 to 2016/04/30 Region Application Type Ref. No. Registered Name Status Date EC Retail New B/2016/04/20/0002 BLACK OIL HOLDINGS (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/20 EC Site New B/2016/04/20/0001 TRAKPROPS 146 (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/20 EC Retail New (Change-of-Hands) B/2016/04/25/0002 CALANDRA TRADING 669 CC ACCEPTED - PENDING DOCUMENTATION 2016/04/25 EC Retail New (Change-of-Hands) B/2016/04/25/0001 CALANDRA TRADING 669 CC ACCEPTED - PENDING DOCUMENTATION 2016/04/25 FS Retail New (Change-of-Hands) C/2016/04/29/0001 HECTOR AUSTIN ENGINEERING (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/29 FS Retail New (Change-of-Hands) C/2016/04/21/0001 DAIZEBEL (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/21 FS Retail New (Change-of-Hands) C/2016/04/26/0001 MAJA FUELS (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/26 FS Retail New (Change-of-Hands) C/2016/04/08/0001 MINOZEST (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/08 GP Retail New D/2016/04/22/0003 LAMANI BUSINESS ENTERPRISES (PTY) LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/22 GP Retail Temporary D/2006/08/17/0015/T16/1 CJ & CK (PTY) LTD ACCEPTED 2016/04/14 GP Site New D/2016/04/22/0002 TOWER PROPERTY FUND LIMITED ACCEPTED - PENDING DOCUMENTATION 2016/04/22 GP Wholesale New D/2016/04/29/0001 JUNE PETROLEUM PTY LTD ACCEPTED - PENDING DOCUMENTATION 2016/04/29 GP Wholesale New -

Virtual Currencies and Terrorist Financing : Assessing the Risks And
DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT FOR CITIZENS' RIGHTS AND CONSTITUTIONAL AFFAIRS COUNTER-TERRORISM Virtual currencies and terrorist financing: assessing the risks and evaluating responses STUDY Abstract This study, commissioned by the European Parliament’s Policy Department for Citizens’ Rights and Constitutional Affairs at the request of the TERR Committee, explores the terrorist financing (TF) risks of virtual currencies (VCs), including cryptocurrencies such as Bitcoin. It describes the features of VCs that present TF risks, and reviews the open source literature on terrorist use of virtual currencies to understand the current state and likely future manifestation of the risk. It then reviews the regulatory and law enforcement response in the EU and beyond, assessing the effectiveness of measures taken to date. Finally, it provides recommendations for EU policymakers and other relevant stakeholders for ensuring the TF risks of VCs are adequately mitigated. PE 604.970 EN ABOUT THE PUBLICATION This research paper was requested by the European Parliament's Special Committee on Terrorism and was commissioned, overseen and published by the Policy Department for Citizens’ Rights and Constitutional Affairs. Policy Departments provide independent expertise, both in-house and externally, to support European Parliament committees and other parliamentary bodies in shaping legislation and exercising democratic scrutiny over EU external and internal policies. To contact the Policy Department for Citizens’ Rights and Constitutional Affairs or to subscribe to its newsletter please write to: [email protected] RESPONSIBLE RESEARCH ADMINISTRATOR Kristiina MILT Policy Department for Citizens' Rights and Constitutional Affairs European Parliament B-1047 Brussels E-mail: [email protected] AUTHORS Tom KEATINGE, Director of the Centre for Financial Crime and Security Studies, Royal United Services Institute (coordinator) David CARLISLE, Centre for Financial Crime and Security Studies, Royal United Services Institute, etc. -

Safeguarding Consumers: Prizes, Promos and Privacy
Washington State Attorney General - Rob McKenna AG Request Legislation – 2009 Session Safeguarding Consumers: Prizes, Promos and Privacy Background: • The Washington Attorney General’s Consumer Protection Division has brought more than a dozen cases involving Internet advertising since 2005 alone. • In April 2007, the Attorney General’s Office reached a settlement with Digital Enterprises of West Hills, doing business as Movieland.com; AccessMedia Networks, of Los Angeles; and Innovative Networks, of Woodland installedHills, that after resolved users allegations signed up theyfor a installedseemingly software anonymous that tookfree trialcontrol for theof a service.consumer’s computer by launching aggressive and persistent pop-ups that demanded payment for a movie download service. The software was concerning allegations that the defendants sold the personal information of thousands of consumers and billed • In June 2007, the office reached a settlement with the Consumer Digital Services, JSE Direct and their subsidiaries consumers for services they did not want. While promoting their Privasafe and SurfSafe products, the defendants advertised that they would “protect your computer and privacy” and guard you from “unscrupulous marketers.” bannerThe Attorney ads and General’s e-mail messages. Office alleged Consumers the defendants submitted lured their Washington personal information consumers withincluding online their offers address, for “free” e-mail gift cards and merchandise including flat-screen monitors; the products were promoted through pop-up ads, Web site address, telephone and birth date, believing they would receive the “free” product. They were subsequently tocharged a tune $14.95 of more charge than $750,000 on their monthly and only phone one Washington bills for defendants’ consumer Internet-related received the advertised service. -

EDUCATION in CHINA a Snapshot This Work Is Published Under the Responsibility of the Secretary-General of the OECD
EDUCATION IN CHINA A Snapshot This work is published under the responsibility of the Secretary-General of the OECD. The opinions expressed and arguments employed herein do not necessarily reflect the official views of OECD member countries. This document and any map included herein are without prejudice to the status of or sovereignty over any territory, to the delimitation of international frontiers and boundaries and to the name of any territory, city or area. Photo credits: Cover: © EQRoy / Shutterstock.com; © iStock.com/iPandastudio; © astudio / Shutterstock.com Inside: © iStock.com/iPandastudio; © li jianbing / Shutterstock.com; © tangxn / Shutterstock.com; © chuyuss / Shutterstock.com; © astudio / Shutterstock.com; © Frame China / Shutterstock.com © OECD 2016 You can copy, download or print OECD content for your own use, and you can include excerpts from OECD publications, databases and multimedia products in your own documents, presentations, blogs, websites and teaching materials, provided that suitable acknowledgement of OECD as source and copyright owner is given. All requests for public or commercial use and translation rights should be submitted to [email protected]. Requests for permission to photocopy portions of this material for public or commercial use shall be addressed directly to the Copyright Clearance Center (CCC) at [email protected] or the Centre français d’exploitation du droit de copie (CFC) at [email protected]. Education in China A SNAPSHOT Foreword In 2015, three economies in China participated in the OECD Programme for International Student Assessment, or PISA, for the first time: Beijing, a municipality, Jiangsu, a province on the eastern coast of the country, and Guangdong, a southern coastal province. -
System/370 Model 145 Reference Summary
System/370 Model 145 Reference Summary S229-2239-1 IBM Corporation, Field Support Documentation, Dept 927, Rochester, Minnesota 55901 PREFACE This publication is primarily intended for customer engineers servicing System/370 Model 145. Second Edition (September 1972) This is a major revision of, and makes 8229-2239-0 obsolete. Address any comments concerning the contents of this publication to: IBM, Field Support Documentation, Dept 927, Rochester, Minnesota 55901 © International Business Machines Corporation 1972 CONTENTS Section 1 - Control Words Branch and Module Switch Word "O" . 1. 1 Branch Word . 1.2 GA Function Charts . 1.3 GA Function Charts . 1.4 GA Function Charts . 1.5 Branch and Link or Return Word . 1.6 Word Move Word Version"O" . 1. 7 Word Move Word Version "1" . 1.8 Storage Word, Non K-Addressable . 1.9 Storage Word, K-Addressable . 1.10 Arithmetic Word 10 Byte Version 1.11 Arithmetic Word, Fullword Version 1.12 Arithmetic Word, 11 Direct ByteVersion . 1.13 Arithmetic Word, 10/11 Indirect Byte Version . 1.14 ALU Entry Gating 1.15 Stat Set Symbols . 1.15 BranchSymbols . 1.15 Arithmetic Word Chart Selection 1.16 Address Formation Chart 1.16 Control Word Chart Selection 1.16 Section 2 - CPU 3145 CPU Data Flow . 2.1 I-Cycles Data Flow . 2.2 I-Cycles . 2.3 PSW Locations . 2.3 Expanded Local Storage . 2.3 I-Cycles . 2.3 I-Cycles Control Line Generation . 2.4 Control Word . 2.4 Control Register Decode . 2.4 iii ECCL Board Layout ............ 2.5 Data Bit Location Chart .......... 2.5 Common Test Points ........... -

Prioritization 4.0
Prioritization 4.0 NCDOT Strategic Prioritization Office of Transportation July 2015 Agenda • Background • General Overview of Changes From P3.0 To P4.0 • Scoring and Scaling • Peak ADT • In-Depth Review of P4.0 Highway Criteria, Measures and Weights • In-Depth Review of P4.0 Non-Highway Criteria, Measures and Weights • Timeline/Schedule • SPOT On!ine • Local Input Methodologies and Best Practices 2 Background NCDOT is responsible for 6 modes of transportation: • Aviation (74 publicly‐owned airports) • Bicycle and Pedestrian • Ferries –2nd largest system in US (behind Washington) • Highways – Maintains 80,000 miles of highways (2nd only to Texas) • Public Transportation • Rail Annual Budget of approx. $4.1 B (federal dollars account for 25% of total budget) 3 Background Key Partners, as shown on colorful map below, include: • 19 Metropolitan Planning Organizations (MPOs) • 18 Rural Planning Organizations (RPOs) • 14 Field Offices (Divisions) *Unifour RPO has dissolved into adjacent MPOs 4 Strategic Transportation Investment (STI) New funding formula for NCDOT’s Capital Expenditures • Focus on Mobility/Expansion and Modernization projects for all modes House Bill 817 signed into Law June 26, 2013 Most significant transportation legislation in NC since 1989 Prioritization Workgroup charged with providing recommendations to NCDOT on weights and criteria. Reps include: • MPOs • RPOs • Division Engineers • Local Government Advocacy Groups 5 STI Legislation New funding formula for all capital expenditures, regardless of mode. All modes must -

The New Tourism Lexicon: Rewriting Our Industry's Narrative
POLICY BRIEF THE NEW TOURISM LEXICON: REWRITING OUR INDUSTRY'S NARRATIVE Last year, Destinations International released a policy "Washington is the problem. Remind voters again and brief entitled, “Advocacy in the Face of Ideology,” which again about Washington spending, Washington waste, made the case that relying on ROI numbers to defend Washington taxation, Washington bureaucracy, the value and relevancy of a destination organization Washington rules and Washington regulations." was no longer a viable advocacy strategy. Instead, we Luntz also suggested replacing "drilling for oil" with argued, destination organizations need to support the "exploring for energy," "undocumented workers" with message of ROI in terms of dollars and cents with an "illegal aliens," and "estate tax" with "death tax." The ideological and value-based appeal to convince political substitutions often work — an Ipsos/NPR poll found that leaders that without a destination organization, these support for abolishing the estate tax jumps to 76% from returns will inevitably vanish. 65% when you call it the death tax. Our industry has unfortunately fallen for what George Lakoff, a professor of Cognitive Science and Linguistics at the University of California at Berkeley, dubs the “Enlightenment Fallacy.” According to this viewpoint, you simply need to tell people the facts in clear language and they’ll reason to the right, true conclusions. The problem, as Lakoff puts it is, “The cognitive and brain sciences have shown this is false… it’s false in every single detail.” The reality is that people tend to frame political arguments, and the facts behind them, in terms of their own values. -

Report on the Most Appropriate Indicators Related to the Basic Concepts
D 4.1 – Report on the most appropriate indicators related to the basic concepts Report on the most appropriate indicators related to the basic concepts Deliverable D4.1 This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No. 870708 D 4.1 – Report on the most appropriate indicators related to the basic concepts Disclaimer: The contents of this deliverable are the sole responsibility of one or more Parties of the SmartCulTour consortium and can under no circumstances be regarded as reflecting the position of the Research Executive Agency and European Commission under the European Union’s Horizon 2020 programme. Copyright and Reprint Permissions “You may freely reproduce all or part of this paper for non-commercial purposes, provided that the following conditions are fulfilled: (i) to cite the authors, as the copyright owners (ii) to cite the SmartCulTour Project and mention that the EC co-finances it, by means of including this statement “Smart Cultural Tourism as a Driver of Sustainable Development of European Regions - SmartCulTour Project no. H2020-870708 co financed by EC H2020 program” and (iii) not to alter the information.” _______________________________________________________________________________________ How to quote this document: Petrić, L., Mandić, A., Pivčević, S., Škrabić Perić, B., Hell, M., Šimundić, B., Muštra, V., Mikulić, D., & Grgić, J. (2020). Report on the most appropriate indicators related to the basic concepts. Deliverable 4.1 of the Horizon 2020 project SmartCulTour (GA number 870708), published on the project web site on September 2020: http://www.smartcultour.eu/deliverables/ D 4.1 – Report on the most appropriate indicators related to the basic concepts This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No. -

9/11 Report”), July 2, 2004, Pp
Final FM.1pp 7/17/04 5:25 PM Page i THE 9/11 COMMISSION REPORT Final FM.1pp 7/17/04 5:25 PM Page v CONTENTS List of Illustrations and Tables ix Member List xi Staff List xiii–xiv Preface xv 1. “WE HAVE SOME PLANES” 1 1.1 Inside the Four Flights 1 1.2 Improvising a Homeland Defense 14 1.3 National Crisis Management 35 2. THE FOUNDATION OF THE NEW TERRORISM 47 2.1 A Declaration of War 47 2.2 Bin Ladin’s Appeal in the Islamic World 48 2.3 The Rise of Bin Ladin and al Qaeda (1988–1992) 55 2.4 Building an Organization, Declaring War on the United States (1992–1996) 59 2.5 Al Qaeda’s Renewal in Afghanistan (1996–1998) 63 3. COUNTERTERRORISM EVOLVES 71 3.1 From the Old Terrorism to the New: The First World Trade Center Bombing 71 3.2 Adaptation—and Nonadaptation— ...in the Law Enforcement Community 73 3.3 . and in the Federal Aviation Administration 82 3.4 . and in the Intelligence Community 86 v Final FM.1pp 7/17/04 5:25 PM Page vi 3.5 . and in the State Department and the Defense Department 93 3.6 . and in the White House 98 3.7 . and in the Congress 102 4. RESPONSES TO AL QAEDA’S INITIAL ASSAULTS 108 4.1 Before the Bombings in Kenya and Tanzania 108 4.2 Crisis:August 1998 115 4.3 Diplomacy 121 4.4 Covert Action 126 4.5 Searching for Fresh Options 134 5. -

Decnet-Plusftam and Virtual Terminal Use and Management
VSI OpenVMS DECnet-Plus FTAM and Virtual Terminal Use and Management Document Number: DO-FTAMMG-01A Publication Date: June 2020 Revision Update Information: This is a new manual. Operating System and Version: VSI OpenVMS Integrity Version 8.4-2 VSI OpenVMS Alpha Version 8.4-2L1 VMS Software, Inc., (VSI) Bolton, Massachusetts, USA DECnet-PlusFTAM and Virtual Terminal Use and Management Copyright © 2020 VMS Software, Inc. (VSI), Bolton, Massachusetts, USA Legal Notice Confidential computer software. Valid license from VSI required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license. The information contained herein is subject to change without notice. The only warranties for VSI products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. VSI shall not be liable for technical or editorial errors or omissions contained herein. HPE, HPE Integrity, HPE Alpha, and HPE Proliant are trademarks or registered trademarks of Hewlett Packard Enterprise. Intel, Itanium and IA-64 are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. UNIX is a registered trademark of The Open Group. The VSI OpenVMS documentation set is available on DVD. ii DECnet-PlusFTAM and Virtual -

595 an Empirical Study of Terrorism Prosecutions in Canada
EMPIRICAL STUDY OF TERRORISM PROSECUTIONS IN CANADA 595 AN EMPIRICAL STUDY OF TERRORISM PROSECUTIONS IN CANADA: ELUCIDATING THE ELEMENTS OF THE OFFENCES MICHAEL NESBITT* AND DANA HAGG** It has now been over 15 years since Canada enacted the Anti-Terrorism Act, codifying what we think of today as Canada’s anti-terrorism criminal laws. The authors set out to canvass how these provisions have been judicially interpreted since their inception through an empirical analysis of court decisions. After exploring how courts have settled initial concerns about these provisions with respect to religious and expressive freedoms, the authors suggest that courts’ interpretations of Canada’s terrorism offences still leave us with many questions, particularly with respect to the facilitation and financing offences. The authors explore these questions and speculate about future challenges that may or may not be successful with the hopes of providing guidance to prosecutors and defence lawyers working in this area. TABLE OF CONTENTS I. INTRODUCTION ............................................. 595 II. TERRORISM PROSECUTIONS TO DATE ............................ 599 III. JUDICIAL INTERPRETATIONS OF THE ELEMENTS OF TERRORISM OFFENCES .................................... 608 A. DEFINITIONS (SECTION 83.01)............................. 608 B. OFFENCES ............................................ 620 IV. CONCLUSIONS AND FUTURE CONSIDERATIONS ....................... 647 I. INTRODUCTION It has now been over 15 years since Canada expeditiously enacted the Anti-Terrorism -

The (Many) Paths to “Destination X”
Blog The (many) paths to “Destination X” Michelle Batten Head of Global Marketing, Mobile Division, Amadeus According to Amadeus’ new whitepaper, Better travel in the Live Travel Space “Get ready for Destination X,” today’s travel sellers have a golden opportunity to Destination X also offers enormous tap into destination services, a growing untapped potential to market and sell marketplace set to reach $183 billion by ancillary destination services to travelers. 2020. Drawing on survey results from It’s a place where travel agents, corporate more than a thousand CheckMyTrip by travel programs, and other providers of Amadeus mobile app users, the research flights, hotels and cars can continue identifies emerging trends about business servicing travelers at their final destination. and leisure travelers destined for Whether traveling on business, leisure or Destination X, one of the most important bleisure, mobile provides the perfect revenue-generating stops on a traveler’s platform to offer these destination services journey. on the move. Take me to travel nirvana Amadeus is helping travel providers better understand and address these challenges The Amadeus research poses questions and opportunities. Using the Amadeus such as, “Are travelers prepared as they Travel Platform, the Live Travel Space arrive to Destination X?” Are their needs aggregates all content into one platform, for add-on destination services like airport making it easier for travel sellers to find transfers, local activities and restaurant what they need, and provide the level of reservations being met? The paper personalization their travelers demand. explores eight trends regarding the challenges and opportunities travel sellers Are you ready to service customers more face in the post-booking ancillary game fully when they reach Destination X? and how you can win travelers trust in Download the whitepaper today at that arena.