The British "Inner Sanctum" of Modern Weaponized Intelligence Discovered
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Doj Inspector General Michael Horowitz Was Handpicked by the “Espionage Machine Part…
12/20/2017 Americans for Innovation: DOJ INSPECTOR GENERAL MICHAEL HOROWITZ WAS HANDPICKED BY THE “ESPIONAGE MACHINE PART… More Next Blog» Create Blog Sign In SEARCH by topic, keyword or phrase. Type in Custom Search box e.g. "IBM Eclipse Foundation" or "racketeering" Custom Search Saturday, December 16, 2017 DEEP STATE Member SHADOW DOJ INSPECTOR GENERAL MICHAEL HOROWITZ GOVERNMENT WAS HANDPICKED BY THE “ESPIONAGE MACHINE POSTER Harvard | Yale | Stanford Sycophants PARTY” RUN BY SOROS & ROGUE SPIES FOR AN Updated Dec. 12, 2017. UNELECTED CORPORATE COMBINE CLICK HERE TO SEE COMBINED TIMELINE OF THE INCREDIBLE BACKSTORY: HIJACKING OF THE INTERNET HOROWITZ HAS BEEN GROOMED BY GEORGE SOROS VIA DNC BARNEY PAY-to-PLA Y NEW W ORLD ORDER FRANK, THE CLINTONS AND JAMES CHANDLER SINCE HARVARD LAW SCHOOL This timeline shows how insiders sell access & manipulate politicians, police, intelligence, HOROWITZ & CLINTON ROAMED THE PLANET USING SPEECHES TO ORGANIZE judges and media to keep their secrets Clintons, Obamas, Summers were paid in cash for THE “ESPIONAGE MACHINE PARTY” TAKEOVER OF THE USA outlandish speaking fees and Foundation donations. Sycophant judges, politicians, academics, bureaucrats and media were fed tips to mutual funds tied to insider HE COACHED LEGAL & CORPORATE CRONIES HOW TO SKIRT U.S. stocks like Facebook. Risk of public exposure, SENTENCING & ETHICS LAWS blackmail, pedophilia, “snuff parties” (ritual child sexual abuse and murder) and Satanism have ensured silence among pay-to-play beneficiaries. The U.S. Patent Office CONTRIBUTING WRITERS | OPINION | AMERICANS FOR INNOVATION | DEC. 17, 2017 UPDATED DEC. 20, 2017 | is their toy box from which to steal new ideas. -

The Paris Apartment Is a Work of Fiction
READI NG GROUP GU I DE PhotosOfYou_TPTextFP Epilogue 2019-11-26 15:34:54 335 AUTHOR’S NOTE The Paris Apartment is a work of fiction. While a product of my imagination, the premises and characters I’ve chosen to create are inspired by real people and real events. The characters of Sophie Seymour and Estelle Allard were shaped by the experiences and courage of Virginia Hall, Pearl Witherington Cornioley, Christine Granville, Josephine Baker, Nancy Wake, and Andrée de Jongh. Their memoirs, interviews, and stories only give us an idea of how truly extraordinary each of these women was. Sophie’s work at Bletchley Park was based on the real men and women who worked tirelessly against time and almost im- possible odds to decode Nazi encryption devices. Most of us have heard of the Enigma cipher and the remarkable work by Alan Turing and his team to break that cipher. Told less often seems to be the story of Tommy Flowers and Bill Tutte, who, together with their teams, developed Colossus—the machine that was able to break the Lorenz cipher, known as Tunny at Bletchley. The Lorenz cipher was favoured by Hitler and used by High Command—and for good reason. It was a far more powerful than the Enigma and capable of exceedingly complex en- cryptions. Additionally, unlike the Enigma, it did not depend ParisApartment_TPtext1P Author’s Note 2020-10-01 21:13:57 395 396 AUTHOR’S NOTE on Morse code. Attached to a teleprinter, it automatically encrypted outgoing messages and decrypted incoming mes- sages, allowing longer messages to be transmitted with greater ease. -

Federal Bureau of Investigation Hearing
FEDERAL BUREAU OF INVESTIGATION HEARING BEFORE THE COMMITTEE ON THE JUDICIARY HOUSE OF REPRESENTATIVES ONE HUNDRED TENTH CONGRESS FIRST SESSION JULY 26, 2007 Serial No. 110–86 Printed for the use of the Committee on the Judiciary ( Available via the World Wide Web: http://judiciary.house.gov U.S. GOVERNMENT PRINTING OFFICE 37–010 PDF WASHINGTON : 2007 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 VerDate 0ct 09 2002 11:11 Jul 09, 2008 Jkt 000000 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 H:\WORK\FULL\072607\37010.000 HJUD1 PsN: DOUGA COMMITTEE ON THE JUDICIARY JOHN CONYERS, JR., Michigan, Chairman HOWARD L. BERMAN, California LAMAR SMITH, Texas RICK BOUCHER, Virginia F. JAMES SENSENBRENNER, JR., JERROLD NADLER, New York Wisconsin ROBERT C. ‘‘BOBBY’’ SCOTT, Virginia HOWARD COBLE, North Carolina MELVIN L. WATT, North Carolina ELTON GALLEGLY, California ZOE LOFGREN, California BOB GOODLATTE, Virginia SHEILA JACKSON LEE, Texas STEVE CHABOT, Ohio MAXINE WATERS, California DANIEL E. LUNGREN, California WILLIAM D. DELAHUNT, Massachusetts CHRIS CANNON, Utah ROBERT WEXLER, Florida RIC KELLER, Florida LINDA T. SA´ NCHEZ, California DARRELL ISSA, California STEVE COHEN, Tennessee MIKE PENCE, Indiana HANK JOHNSON, Georgia J. RANDY FORBES, Virginia BETTY SUTTON, Ohio STEVE KING, Iowa LUIS V. GUTIERREZ, Illinois TOM FEENEY, Florida BRAD SHERMAN, California TRENT FRANKS, Arizona -

Part Ii: Proof Columbia University Helped British Saboteurs and American Traitors Ta…
6/14/2021 Americans for Innovation: PART II: PROOF COLUMBIA UNIVERSITY HELPED BRITISH SABOTEURS AND AMERICAN TRAITORS TA… More Create Blog Sign In To ensure you are reading the latest post, click the logo above. SEARCH by topic, keyword or phrase. Type in Custom Search box e.g. "IBM Eclipse Foundation" or "racketeering" Friday, June 11, 2021 SENIOR EXECUTIVE SERVICE (SES) PART II: PROOF COLUMBIA UNIVERSITY HELPED HIJACKED THE INTERNET BRITISH SABOTEURS AND AMERICAN TRAITORS Michael McKibben EXPOS… TAKEOVER AMERICA IN 1902 CONTRIBUTING WRITERS | OPINION | AMERICANS FOR INNOVATION | JUN. 11, 2021, UPDATED JUN. 14, 2021 | PDF | https://tinyurl.com/kp4ncycs Click here to download a raw *.mp4 version of this video DEEP STATE Member SHADOW GOVERNMENT POSTER Available by request only, email request to: [email protected] Harvard | Yale | Stanford | Oxbridge (Cambridge, Oxford) | Sycophants LEGEND: Some corruptocrat photos in this blog contain Fig. 1—Rothschild-protégé banker J.P. Morgan became a trustee of Columbia University a stylized Christian Celtic Wheel Cross in the while William J. Donovan (1903-1907) was being groomed by numerous founders of the background alongside the text British Pilgrims Society. By 1912, had purchased editorial control of all of America's "Corruption Central" meaning we major newspapers and in 1913 drove the formation of the Federal Reserve to be have put the person's conduct under the microscope and controlled by British banks aligned with the Pilgirms Society where Lord Rothchild was a discovered that he or she is at the co-founder with J.P. Morgan. L/R: William J. "Wild Bill" Donovan, J. -

Retroactively Classified Documents, the First Amendment, and the Power to Make Secrets out of the Public Record
ARTICLE DO YOU HAVE TO KEEP THE GOVERNMENT’S SECRETS? RETROACTIVELY CLASSIFIED DOCUMENTS, THE FIRST AMENDMENT, AND THE POWER TO MAKE SECRETS OUT OF THE PUBLIC RECORD JONATHAN ABEL† INTRODUCTION ............................................................................ 1038 I. RETROACTIVE CLASSIFICATION IN PRACTICE AND THEORY ... 1042 A. Examples of Retroactive Classification .......................................... 1043 B. The History of Retroactive Classification ....................................... 1048 C. The Rules Governing Retroactive Classification ............................. 1052 1. Retroactive Reclassification ............................................... 1053 2. Retroactive “Original” Classification ................................. 1056 3. Retroactive Classification of Inadvertently Declassified Documents .................................................... 1058 II. CAN I BE PROSECUTED FOR DISOBEYING RETROACTIVE CLASSIFICATION? ............................................ 1059 A. Classified Documents ................................................................. 1059 1. Why an Espionage Act Prosecution Would Fail ................. 1061 2. Why an Espionage Act Prosecution Would Succeed ........... 1063 3. What to Make of the Debate ............................................. 1066 B. Retroactively Classified Documents ...............................................1067 1. Are the Threats of Prosecution Real? ................................. 1067 2. Source/Distributor Divide ............................................... -

F:\...\04 D Vladeck Wp9 M
Litigating National Security Cases in the Aftermath of 9/11 David C. Vladeck* The treacherous terrorist attacks against the United States on September 11, 2001, and the aftershocks that are still being felt years later, have had a profound effect on the legal landscape in the United States. In 9/11’s immediate aftermath, Congress, in a rare and fleeting moment of bi- partisanship, gave the President far-reaching authority to combat terrorism. Among other measures, Congress authorized the President to use military force against the 9/11 terrorists and those who aided or harbored them,1 enacted the USA PATRIOT Act to give the President unprecedented law enforcement and detention authority over suspected terrorists and those believed to be providing material support to terrorists,2 placed entire categories of unclassified, previously accessible, government-held information off-limits to the public,3 and, by creating the Department of Homeland Security, reorganized the Executive Branch to consolidate and better coordinate our nation’s security agencies.4 The President has used this authority to undertake massive and ongoing military operations in Iraq and Afghanistan, to detain indefinitely and without criminal charges hundreds of foreign nationals and even American citizens,5 to step up counter-terrorism * Director of the Institute of Public Representation and Professor of Law, Georgetown University Law Center. This article draws mainly on my experience as a litigator, not as an academic. Prior to joining the full-time faculty at Georgetown in 2002, I spent more than twenty-five years at the Public Citizen Litigation Group, first as a staff attorney and then as director. -

News Coverage Over the Allegations of a National Security Whistleblower
The Ethical Resister’s Last Resort: News Coverage over the Allegations of a National Security Whistleblower ______________________________________________ A Thesis Presented to The Faculty of the Graduate School At the University of Missouri-Columbia __________________________________________________ In Partial Fulfillment of the Requirements for the Degree Master of Arts in Sociology _____________________________________________ by Ryan Amundson Dr. Clarence Lo, Thesis Supervisor May 2009 The undersigned, appointed by the dean of the Graduate School, have examined the thesis entitled THE ETHICAL RESISTER’S LAST RESORT: NEWS COVERAGE OVER THE ALLEGATIONS OF A NATIONAL SECURITY WHISTLEBLOWER presented by Ryan Amundson, a candidate for the degree of master of arts, and hereby certify that, in their opinion, it is worthy of acceptance. Professor Clarence Lo Professor Victoria Johnson Professor Charles Davis ACKNOWLEDGEMENTS I would like to thank all the members of my thesis committee, Dr. Clarence Lo, Dr. Victoria Johnson, and Dr. Charles Davis for all of their help. Their comments and criticisms pushed me to go beyond my own lazy thinking. They were also very understanding of the busy life of a graduate student and tolerant of a thesis running over a hundred pages. Even after receiving drafts at the last minute, all of them still managed to read carefully and offer detailed advice that helped me make my thesis into something worthwhile. I want to thank Dr. Clarence Lo especially for the many hours we spent throughout the last couple of years discussing my thesis and all the support and encouragement he provided. Putting together a thesis is not an individual job, and I am grateful to all those among the faculty and graduate students at the University of Missouri-Columbia who helped me along the way. -

Nine Years of War Based on A
Exposing the hard truth about 9/11 is the only Justice demands accountability. Nine Years of War way to end the war and bring our troops home. To our fellow concerned citizens: For the sake of the 9/11 Evidence shows that the 9/11 attacks could not have occurred victims and their families and for the safety, freedom and without high-level complicity from rogue elements within honor of every American, learn the truth and tell others. the US government,32 as well as complicity from some of Challenge the media to stop repeating the lies and the our allies.33 Similar “false flag” operations have been used cover-up. Urge your senators and representatives to open by powerful interests throughout history to take a nation a new, truly independent investigation—wherever it may to war, including by our own government, according to lead. Join the steadily growing nonpartisan 9/11 Truth recently declassified documents.34 The invasion of Afghan- movement, and demand justice. istan had been prepared for the President’s approval before Some are guilty; all are responsible. 9/11.35 Facing these facts, however difficult, is critical to changing the disastrous course set for our country almost —Rabbi Abraham Heschel (-) a decade ago.36 32. Dr. Robert M. Bowman, Lt. Col., USAF, ret., former combat/intercept pilot, Director of SDI programs “Let us never tolerate outrageous under Preisdents Ford and Carter, at American Scholars Symposium: 9/11+ the Neo-Con Agenda, 6/25/2006, YouTube.com, C-SPANarchives.org. See also thepatriots.us conspiracy theories concerning the 33. -

TICOM: the Last Great Secret of World War II Randy Rezabek Version of Record First Published: 27 Jul 2012
This article was downloaded by: [Randy Rezabek] On: 28 July 2012, At: 18:04 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/fint20 TICOM: The Last Great Secret of World War II Randy Rezabek Version of record first published: 27 Jul 2012 To cite this article: Randy Rezabek (2012): TICOM: The Last Great Secret of World War II, Intelligence and National Security, 27:4, 513-530 To link to this article: http://dx.doi.org/10.1080/02684527.2012.688305 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and- conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. Intelligence and National Security Vol. 27, No. 4, 513–530, August 2012 TICOM: The Last Great Secret of World War II RANDY REZABEK* ABSTRACT Recent releases from the National Security Agency reveal details of TICOM, the mysterious 1945 operation targeting Germany’s cryptologic secrets. -

Docid: 383869,.9
.. DOCID: 383869,.9 / ,1/111 [ Der Fall WICHER:GermanKnowledge of i Polish Success on ENIGMA BY JOSEPH A. MEYER T'op Bed pi blat'" a In 19.39 the Germans found evidf'nce. including decrypts, that a Polish cryptanalytic organization, WICHER: had been readin!! the ENIGMA. Documents and interrogations did not reveal how the ma chine could have been read, and after some changes in the indicator system and plug/fings, the matter was dropped. In 1943, further evidence of prewar Polish success, and the Mrong appearance that Navy ENIGMA was being read by the British and US., caused a crypto security crisis. A spy in the U.S. NavyDepartment reported the reading of V-boat keys. ENIGMA security was studied. and many changes in the machine and its uWf.:e were undertaken. By 1944 the Germans acted and spoke as if they knew ENIGMA traffic was being read by the Allies, but they suspected betrayal or compromise of keys. Medium grade ciphers were also improved, and radiQ security was much im proVf'd. Users were forbidden to send secret or top .~ecrf!t information or operational orders over ENIGMA. Through all of this. German con /idence in the TUNNY cipher teleprinter (which wa.~ al.~o being read) neller wavered. The key to German suspicions of ENIGMA appears to have been the knowledge of Polish prewar successes; after which the wartime ENIGMA exploitation hunk by a thread for five and one-half ~~. I I. DER FALL WICHER' 1n late 19:39. after their rapid conquest of Poland. the German OKH (Oberkommando des Heeres, Army High Command) and OKW (Oherkommando der Wehrmacht, Armed Forces High Command) cryptanalysts obtained definite proof, incllldin~ decrypts of German messag-cs. -
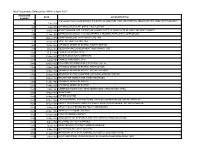
NSA Documents Released to NARA in April 2011
NSA Documents Released to NARA in April 2011 ACCESSION DATE ACCESSION TITLE NUMBER RECOLLECTIONS CONCERNING THE BIRTH OF ONE-TIME TAPE AND PRINTING-TELEGRAPH MACHINE CRYPTOGRAPHY 23 1-Jul-1956 268 1-Jul-1944 JAPANESE MERCHANT SHIPS, FIRST EDITION 593 9-May-1946 QUESTIONNAIRE FOR INSPECTION LIAISON VISITS TO FIELD UNITS OF ARMY SECURITY AGENCY 793 11-Apr-1951 OPERATIONS (AFSAG 1228) MANUEVERS & TRAINING EXERCISES & OPERATIONS 807 12-Dec-1950 COMPROMISES OF CRYPTOSYSTEMS 1950 821 24-Apr-1952 JOINT AUTHENTICATION 1952 963 10-Oct-1944 JAPANESE ORDER OF BATTLE, FOURTH EDITION 978 4-Dec-1952 RESEARCH AND DEVELOPMENT (R&D) BOARD, 1952 1022 15-Jul-1946 CHINESE PERSONS, SP-W 1027 10-Jun-1948 RUSSIAN ELECTORAL DISTRICTS 1029 1-Aug-1946 CHINESE RAILROADS, SP-X 1086 12-Dec-1956 DISASTER AND EMERGENCY PLANNING 1952-56 1155 13-Apr-1944 JAPANESE ORDER OF BATTLE, FIRST EDITION 1156 15-May-1944 JAPANESE ORDER OF BATTLE, SECOND EDITION 1158 11-Aug-1945 ORDER OF BATTLE BULLETINS, JAPANESE GROUND FORCES 1215 30-Nov-1945 MACARTHUR SEARCH FOR WINDS MESSAGES 1250 31-Mar-1945 JAPANESE ORDER OF BATTLE 1250 31-Mar-1945 JAPANESE ORDER OF BATTLE 1530 2-Mar-1949 COMBINED COMMUNICATIONS BOARD COUNTERMEASURES PANEL 1607 17-May-1948 SLIDE TUBE 1608 25-May-1954 CIPHER MACHINE 1617 31-Dec-1949 CRYPTOGRAPHIC SYSTEMS SUBMITTED FOR CONSIDERATION FOR MILITARY USE 1632 17-Jun-1946 AMBER-19 CATEGORY AND 3 CATEGORY WEIGHTING SCHEMES FOR TEST PROBLEM 1807 4-May-1953 AFSA CIVILIAN PERSONNEL POLICY MEMORANDA 1811 21-Dec-1951 AFSA-03 TELEPHONE LISTINGS 1812 14-Feb-1949 AFSA PERSONNEL -

Volume XIII, Issue 2 April 2019 PERSPECTIVES on TERRORISM Volume 13, Issue 2
ISSN 2334-3745 Volume XIII, Issue 2 April 2019 PERSPECTIVES ON TERRORISM Volume 13, Issue 2 Table of Contents Welcome from the Editors..............................................................................................................................1 Articles A “Lunatic Fringe”? The Persistence of Right Wing Extremism in Australia...............................................2 by Kristy Campion Mapping Transnational Extremist Networks: An Exploratory Study of the Soldiers of Odin’s Facebook Network, Using Integrated Social Network Analysis....................................................................................21 by Yannick Veilleux-Lepage and Emil Archambault The Hand that Feeds the Salafist: an Exploration of the Financial Independence of 131 Dutch Jihadi Travellers.......................................................................................................................................................39 by Melvin Soudijn The Terrorism Recidivism Study (TRS): Examining Recidivism Rates for Post 9/11 Offenders.................54 by Omi Hodwitz Special Correspondence The mid-February 2019 Pulwama attack in Kashmir: an Indian Perspective..............................................65 by Abhinav Pandya The mid-February 2019 Pulwama attack in Kashmir: a Pakistani Perspective...........................................69 by Muhammad Feyyaz Seeing Political Violence through Different Lenses......................................................................................75 by Gregory D. Miller Resources