A History of Computer Viruses -The Famous ‘Trio’
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Lecture 5: Feb 4Th, 2020 5.1 OS Boot Process
CMPSCI 577 Operating Systems Design and Implementation Spring 2020 Lecture 5: Feb 4th, 2020 Lecturer: Prashant Shenoy Scribe: Serena Chan 5.1 OS Boot Process While seemingly mundane and not directly relevant to the modifications we will be making in this course, understanding the OS boot process is important for modifying the kernel. There are six steps that take the machine to a running state from when it is first turned on. 5.1.1 Step 1: BIOS (Basic Input/Output System) The BIOS is a small piece of code that lives in the firmware and is the first software that runs upon boot. When the computer is turned on, the BIOS runs the Power-on Self Test, where the RAM is initialized and hardware such as disks and peripherals are identified and checked. Once the disk is found, the BIOSwill start the boot process from the disk (‘bootstrapping’). The BIOS is often stored on EEPROM/ROM (read-only memory); because of its hardware-specific nature, it is not designed to be easily user modifiable. In addition, since the BIOS is the lowest level of softwarein the PC, it also acts as an interface for the OS to perform I/O and communicate with hardware. 5.1.2 Step 2: MBR (Master Boot Record) The MDR is the first 512 bytes of memory and consists of three components. In particular, thefirst440 bytes contain the bootstrap code that is used to continue the boot process, or the 1st stage boot loader; this is executed by the BIOS. The functionality of the code is to simply search through the partition table and find the root partition, where is where the OS resides. -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512 -

Patching DOS 5 and up for the Pcjr
Patching DOS 5 and up for the PCjr November 29th, 2020 [email protected] Background Patching DOS 5+ Theory of operation Preparing a DOS 5 disk Patching the DOS 5+ disk Create FORMATJR.COM Hard drive installation Fdisk and create a DOS partition Format the hard drive partition Appendix A - Wiping out a boot sector Background The PCjr shipped in 1983 in two configurations: a 64KB machine with no floppy disk drive or a 128KB machine with a single floppy disk drive. The architecture of the machine has the video buffer “borrow” memory from the main memory of the machine. With the standard 16KB video buffer this makes the available RAM either 48KB or 112KB. IBM never offered a hard drive solution. Adding extra memory to a PCjr became possible, but it required a device driver to be loaded at boot time. Microsoft, Tecmar, and other vendors provided device drivers with their memory expansions. The best of the device drivers was a shareware program called jrConfig written by Larry Newcomb. jrConfig can be downloaded from http://www.brutman.com/PCjr/pcjr_downloads.html. The original version of DOS that shipped with the PCjr was PC DOS 2.1. DOS versions 2.1 through 3.3 work on the machine as is. To run DOS 5 or later two things are required: ● Extra memory is required. While extra memory is useful for DOS 2.1 - 3.3, DOS 5 won’t even boot on a small system. I BM formally states the requirement is 512KB and the PCjr is not supported. ● DOS 5 can be patched to work on a PCjr even though it is not supported. -
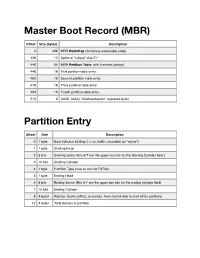
Master Boot Record (MBR)
Master Boot Record (MBR) Offset Size (bytes) Description 0 436 MBR Bootstrap (flat binary executable code) 436 10 Optional "unique" disk ID1 446 64 MBR Partition Table, with 4 entries (below) 446 16 First partition table entry 462 16 Second partition table entry 478 16 Third partition table entry 494 16 Fourth partition table entry 510 2 (0x55, 0xAA) "Valid bootsector" signature bytes Partition Entry Offset Size Description 0 1 byte Boot indicator bit flag: 0 = no, 0x80 = bootable (or "active") 1 1 byte Starting head 2 6 bits Starting sector (Bits 6-7 are the upper two bits for the Starting Cylinder field.) 3 10 bits Starting Cylinder 4 1 byte Partition Type (0xB or 0xC for FAT32). 5 1 byte Ending Head 6 6 bits Ending Sector (Bits 6-7 are the upper two bits for the ending cylinder field) 7 10 bits Ending Cylinder 8 4 bytes Relative Sector (offset, in sectors, from start of disk to start of the partition) 12 4 bytes Total Sectors in partition BIOS Parameter Block (BPB) Offset Size Meaning (bytes) (bytes) 0 3 The first three bytes EB XX 90 disassemble to JMP SHORT XX NOP. 3 8 OEM identifier. 11 2 The number of Bytes per sector (all numbers are in the little-endian format). 13 1 Number of sectors per cluster. 14 2 Number of reserved sectors. The boot record sectors are included in this value. 16 1 Number of File Allocation Tables (FAT's) on the storage media. Often 2. 17 2 Max # of directory entries (0 for FAT32 which stores directories in data region). -

IBM X-Force Threat Insight Quarterly 2 X-Force Threat Insight Quarterly IBM Security Solutions
IBM Security Solutions May 2011 IBM X-Force Threat Insight Quarterly 2 X-Force Threat Insight Quarterly IBM Security Solutions Contents About the report 2 About the Report The IBM X-Force® Threat Insight Quarterly is designed to highlight some of the most significant threats and challenges 3 Evolution: From Nuisance to Weapon facing security professionals today. This report is a product of IBM Managed Security Services and the IBM X-Force 8 Prolific and Impacting Issues of Q1 2011 research and development team. Each issue focuses on specific challenges and provides a recap of the most significant recent 16 References online threats. IBM Managed Security Services are designed to help an organization improve its information security, by outsourcing security operations or supplementing your existing security teams. The IBM protection on-demand platform helps deliver Managed Security Services and the expertise, knowledge and infrastructure an organization needs to secure its information assets from Internet attacks. The X-Force team provides the foundation for a preemptive approach to Internet security. The X-Force team is one of the best-known commercial security research groups in the world. This group of security experts researches and evaluates vulnerabilities and security issues, develops assessment and countermeasure technology for IBM security products, and educates the public about emerging Internet threats. We welcome your feedback. Questions or comments regarding the content of this report should be addressed to [email protected]. 3 X-Force Threat Insight Quarterly IBM Security Solutions Evolution: From Nuisance to Weapon One of the more notable examples here is Brain3, a boot sector infector which originated in Pakistan and released in 1986, was Creeper, Wabbit, Animal, Elk Cloner, Brain, Vienna, Lehigh, one of the first examples of malware that infected PC’s running Stoned, Jerusalem. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -
![Reversing Malware [Based on Material from the Textbook]](https://docslib.b-cdn.net/cover/8924/reversing-malware-based-on-material-from-the-textbook-1438924.webp)
Reversing Malware [Based on Material from the Textbook]
SoftWindows 11/23/05 Reversing Malware [based on material from the textbook] Reverse Engineering (Reversing Malware) © SERG What is Malware? • Malware (malicious software) is any program that works against the interest of the system’s user or owner. • Question: Is a program that spies on the web browsing habits of the employees of a company considered malware? • What if the CEO authorized the installation of the spying program? Reverse Engineering (Reversing Malware) © SERG Reversing Malware • Revering is the strongest weapon we have against the creators of malware. • Antivirus researchers engage in reversing in order to: – analyze the latest malware, – determine how dangerous the malware is, – learn the weaknesses of malware so that effective antivirus programs can be developed. Reverse Engineering (Reversing Malware) © SERG Distributed Objects 1 SoftWindows 11/23/05 Uses of Malware • Why do people develop and deploy malware? – Financial gain – Psychological urges and childish desires to “beat the system”. – Access private data – … Reverse Engineering (Reversing Malware) © SERG Typical Purposes of Malware • Backdoor access: – Attacker gains unlimited access to the machine. • Denial-of-service (DoS) attacks: – Infect a huge number of machines to try simultaneously to connect to a target server in hope of overwhelming it and making it crash. • Vandalism: – E.g., defacing a web site. • Resource Theft: – E.g., stealing other user’s computing and network resources, such as using your neighbors’ Wireless Network. • Information Theft: – E.g., stealing other user’s credit card numbers. Reverse Engineering (Reversing Malware) © SERG Types of Malware • Viruses • Worms • Trojan Horses • Backdoors • Mobile code • Adware • Sticky software Reverse Engineering (Reversing Malware) © SERG Distributed Objects 2 SoftWindows 11/23/05 Viruses • Viruses are self-replicating programs that usually have a malicious intent. -

Virus Bulletin, July 91
July 1991 ISSN 0956-9979 THE AUTHORITATIVE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Edward Wilding Technical Editor: Fridrik Skulason, University of Iceland Editorial Advisors: Jim Bates, Bates Associates, UK, Phil Crewe, Fingerprint, UK, David Ferbrache, ISIS Ltd., UK, Ray Glath, RG Software Inc., USA, Hans Gliss, Datenschutz Berater, West Germany, Ross M. Greenberg, Software Concepts Design, USA, Dr. Harold Joseph Highland, Compulit Microcomputer Security Evaluation Laboratory, USA, Dr. Jan Hruska, Sophos, UK, Dr. Keith Jackson, Walsham Contracts, UK, Owen Keane, Barrister, UK, John Laws, RSRE, UK, David T. Lindsay, Digital Equipment Corporation, UK, Yisrael Radai, Hebrew University of Jerusalem, Israel, Martin Samociuk, Network Security Management, UK, John Sherwood, Sherwood Associates, UK, Prof. Eugene Spafford, Purdue University, USA, Dr. Peter Tippett, Certus International Corporation, USA, Dr. Ken Wong, PA Consulting Group, UK, Ken van Wyk, CERT, USA. CONTENTS SCANNER UPDATE IBM Triumphs Amidst the ‘Vapourware’ 34 EDITORIAL 2 Results Table 35 TECHNICAL NOTES 3 TUTORIAL PRODUCT REVIEWS Fixed Disk Boot Sectors and 1. SafeWord Virus-Safe 36 Post-Attack Recovery 5 2. Knoxcard: Anti-Virus Hardware 38 Virus Bulletin Education, Training & Awareness Presentations 9 3. Trend Micro Devices’ PC-cillin 40 LETTERS SHAREWARE REVIEW VB Signatures With IBM’s Virscan 10 PC Virus Index 42 Vetting Procedure 10 KNOWN IBM PC VIRUSES 12 END-NOTES & NEWS 44 VIRUS BULLETIN ©1991 Virus Bulletin Ltd, 21 The Quadrant, Abingdon Science Park, Oxon, OX14 3YS, England. Tel (+44) 235 555139. /90/$0.00+2.50 This bulletin is available only to qualified subscribers. No part of this publication may be reproduced, stored in a retrieval system, or transmitted by any form or by any means, electronic, magnetic, optical or photocopying, without the prior written permission of the publishers. -

Booting up and Shutting Down
Booting Up and Shutting Down lctseng (2019-2020, CC BY-SA) ? (1996-2018) 交大資工系資訊中心 Computer Center of Department of Computer Science, NCTU 1 Handbook and Manual pages ● Complete guide and be found at ○ https://www.freebsd.org/doc/en/books/handbook/boot.html ○ https://www.freebsd.org/doc/zh_TW/books/handbook/boot.html 2 Booting Overview - After Powering On ● BIOS (Basic Input/Output System) - stored on motherboard ○ Find MBR in the bootable media (disk,cd,usb stick,...) ● MBR (Master Boot Record) - stored on the first sector of disk/media ○ Record partition information of the disk ○ Load boot loader in Boot Sector (prompt if multiple choices available) ● Boot Sector - stored in the each slice (outside of usual file system) ○ Recognize FreeBSD file system. Find kernel loader under /boot ● Kernel loader - stored in main file system (all below) ○ Show booting prompt and load selected kernel ● OS Kernel ○ Initialize hardware/drivers ● Init ○ Mount filesystem, acquire DHCP, start shell, ... 3 MBR – Master Boot Record ● First 512 bytes of disk, outside the FreeBSD filesystem ○ Last 2 Bytes are 0x55AA ○ Corresponding copy in FreeBSD is /boot/boot0 or /boot/mbr nctucs [~] -lctseng- ls -l /boot/boot0 -r--r--r-- 1 root Wheel 512 Nov 12 2014 /boot/boot0 nctucs [~] -lctseng- ls -l /boot/mbr -r--r--r-- 1 root Wheel 512 Nov 12 2014 /boot/mbr nctucs [~] -lctseng- xxd /boot/mbr 00000000: fc31 c08e c08e d88e d0bc 007c be1a 7cbf .1.........|..|. 00000010: 1a06 b9e6 01f3 a4e9 008a 31f6 bbbe 07b1 ..........1..... … 000001d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 000001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ............... -

Topics in Malware What Is Malware?
Topics in Malware What is Malware? • Malware (malicious software) is any program that works against the interest of the system’s user or owner. • Question: Is a program that spies on the web browsing habits of the employees of a company considered malware? • What if the CEO authorized the installation of the spying program? Uses of Malware • Why do people develop and deploy malware? – Financial gain – Psychological urges and childish desires to “beat the system”. – Access private data – … Typical purposes of Malware • Backdoor access: – Attacker gains unlimited access to the machine. • Denial-of-service (DoS) attacks: – Infect a huge number of machines to try simultaneously to connect to a target server in hope of overwhelming it and making it crash. • Vandalism: – E.g., defacing a web site. • Resource Theft: – E.g., stealing other user’s computing and network resources, such as using your neighbors’ Wireless Network. • Information Theft: – E.g., stealing other user’s credit card numbers. Types of Malware • Viruses • Worms • Trojan Horses • Backdoors • Mobile code • Adware • Sticky software Metamorphic viruses • Instead of encrypting the program’s body and making slight alterations in the decryption engine, alter the entire program each time it is replicated. • This makes it extremely difficult for antivirus writers to use signature-matching techniques to identify malware. • Metamorphism requires a powerful code analysis engine that needs to be embedded into the malware. Metamorphic viruses: Operation • Metamorphic engine scans the code and generates a different version of it every time the program is duplicated. • The metamorphic engine performs a wide variety of transformations on the malware and on the engine itself. -

Virus Bulletin, February 1991
February 1991 ISSN 0956-9979 THE AUTHORITATIVE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Edward Wilding Technical Editor: Fridrik Skulason, University of Iceland Editorial Advisors: Jim Bates, Bates Associates, UK, Phil Crewe, Fingerprint, UK, Dr. Jon David, USA, David Ferbrache, Information Systems Integrity & Security Ltd., UK, Ray Glath, RG Software Inc., USA, Hans Gliss, Datenschutz Berater, West Germany, Ross M. Greenberg, Software Concepts Design, USA, Dr. Harold Joseph Highland, Compulit Microcomputer Security Evaluation Laboratory, USA, Dr. Jan Hruska, Sophos, UK, Dr. Keith Jackson, Walsham Contracts, UK, Owen Keane, Barrister, UK, Yisrael Radai, Hebrew University, Israel, John Laws, RSRE, UK, David T. Lindsay, Digital Equipment Corporation, UK, Martin Samociuk, Network Security Management, UK, John Sherwood, Sherwood Associates, UK, Dr. Peter Tippett, Certus International Corporation, USA, Dr. Ken Wong, PA Consulting Group, UK, Ken van Wyk, CERT, USA. CONTENTS IBM PC VIRUSES (UPDATE) 8 COUNTERMEASURES EDITORIAL 2 A Backup Strategy Based on TECHNICAL NOTES Risk Analysis 9 The Write-Protected System Floppy Disk 2 VIRUS ANALYSES Education Training and 1. Beijing 11 Awareness Presentations 3 2. Aircop 12 Direct Port Access 3 3. Faust 14 The Kamikaze Virus 4 4. LoveChild 16 Overlay Files 5 The Virus ‘Underground’ 5 PRODUCT REVIEW Turbo Anti-Virus 18 INVESTIGATION The Search for Den Zuk 6 END-NOTES & NEWS 20 VIRUS BULLETIN ©1991 Virus Bulletin Ltd, 21 The Quadrant, Abingdon Science Park, Oxon, OX14 3YS, England. Tel (+44) 235 555139. /90/$0.00+2.50 This bulletin is available only to qualified subscribers. No part of this publication may be reproduced, stored in a retrieval system, or transmitted by any form or by any means, electronic, magnetic, optical or photocopying, without the prior written permission of the publishers.