Computer Viruses Demystified,2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Lecture 5: Feb 4Th, 2020 5.1 OS Boot Process
CMPSCI 577 Operating Systems Design and Implementation Spring 2020 Lecture 5: Feb 4th, 2020 Lecturer: Prashant Shenoy Scribe: Serena Chan 5.1 OS Boot Process While seemingly mundane and not directly relevant to the modifications we will be making in this course, understanding the OS boot process is important for modifying the kernel. There are six steps that take the machine to a running state from when it is first turned on. 5.1.1 Step 1: BIOS (Basic Input/Output System) The BIOS is a small piece of code that lives in the firmware and is the first software that runs upon boot. When the computer is turned on, the BIOS runs the Power-on Self Test, where the RAM is initialized and hardware such as disks and peripherals are identified and checked. Once the disk is found, the BIOSwill start the boot process from the disk (‘bootstrapping’). The BIOS is often stored on EEPROM/ROM (read-only memory); because of its hardware-specific nature, it is not designed to be easily user modifiable. In addition, since the BIOS is the lowest level of softwarein the PC, it also acts as an interface for the OS to perform I/O and communicate with hardware. 5.1.2 Step 2: MBR (Master Boot Record) The MDR is the first 512 bytes of memory and consists of three components. In particular, thefirst440 bytes contain the bootstrap code that is used to continue the boot process, or the 1st stage boot loader; this is executed by the BIOS. The functionality of the code is to simply search through the partition table and find the root partition, where is where the OS resides. -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512 -

Patching DOS 5 and up for the Pcjr
Patching DOS 5 and up for the PCjr November 29th, 2020 [email protected] Background Patching DOS 5+ Theory of operation Preparing a DOS 5 disk Patching the DOS 5+ disk Create FORMATJR.COM Hard drive installation Fdisk and create a DOS partition Format the hard drive partition Appendix A - Wiping out a boot sector Background The PCjr shipped in 1983 in two configurations: a 64KB machine with no floppy disk drive or a 128KB machine with a single floppy disk drive. The architecture of the machine has the video buffer “borrow” memory from the main memory of the machine. With the standard 16KB video buffer this makes the available RAM either 48KB or 112KB. IBM never offered a hard drive solution. Adding extra memory to a PCjr became possible, but it required a device driver to be loaded at boot time. Microsoft, Tecmar, and other vendors provided device drivers with their memory expansions. The best of the device drivers was a shareware program called jrConfig written by Larry Newcomb. jrConfig can be downloaded from http://www.brutman.com/PCjr/pcjr_downloads.html. The original version of DOS that shipped with the PCjr was PC DOS 2.1. DOS versions 2.1 through 3.3 work on the machine as is. To run DOS 5 or later two things are required: ● Extra memory is required. While extra memory is useful for DOS 2.1 - 3.3, DOS 5 won’t even boot on a small system. I BM formally states the requirement is 512KB and the PCjr is not supported. ● DOS 5 can be patched to work on a PCjr even though it is not supported. -
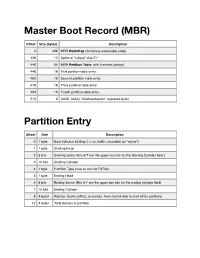
Master Boot Record (MBR)
Master Boot Record (MBR) Offset Size (bytes) Description 0 436 MBR Bootstrap (flat binary executable code) 436 10 Optional "unique" disk ID1 446 64 MBR Partition Table, with 4 entries (below) 446 16 First partition table entry 462 16 Second partition table entry 478 16 Third partition table entry 494 16 Fourth partition table entry 510 2 (0x55, 0xAA) "Valid bootsector" signature bytes Partition Entry Offset Size Description 0 1 byte Boot indicator bit flag: 0 = no, 0x80 = bootable (or "active") 1 1 byte Starting head 2 6 bits Starting sector (Bits 6-7 are the upper two bits for the Starting Cylinder field.) 3 10 bits Starting Cylinder 4 1 byte Partition Type (0xB or 0xC for FAT32). 5 1 byte Ending Head 6 6 bits Ending Sector (Bits 6-7 are the upper two bits for the ending cylinder field) 7 10 bits Ending Cylinder 8 4 bytes Relative Sector (offset, in sectors, from start of disk to start of the partition) 12 4 bytes Total Sectors in partition BIOS Parameter Block (BPB) Offset Size Meaning (bytes) (bytes) 0 3 The first three bytes EB XX 90 disassemble to JMP SHORT XX NOP. 3 8 OEM identifier. 11 2 The number of Bytes per sector (all numbers are in the little-endian format). 13 1 Number of sectors per cluster. 14 2 Number of reserved sectors. The boot record sectors are included in this value. 16 1 Number of File Allocation Tables (FAT's) on the storage media. Often 2. 17 2 Max # of directory entries (0 for FAT32 which stores directories in data region). -

Booting up and Shutting Down
Booting Up and Shutting Down lctseng (2019-2020, CC BY-SA) ? (1996-2018) 交大資工系資訊中心 Computer Center of Department of Computer Science, NCTU 1 Handbook and Manual pages ● Complete guide and be found at ○ https://www.freebsd.org/doc/en/books/handbook/boot.html ○ https://www.freebsd.org/doc/zh_TW/books/handbook/boot.html 2 Booting Overview - After Powering On ● BIOS (Basic Input/Output System) - stored on motherboard ○ Find MBR in the bootable media (disk,cd,usb stick,...) ● MBR (Master Boot Record) - stored on the first sector of disk/media ○ Record partition information of the disk ○ Load boot loader in Boot Sector (prompt if multiple choices available) ● Boot Sector - stored in the each slice (outside of usual file system) ○ Recognize FreeBSD file system. Find kernel loader under /boot ● Kernel loader - stored in main file system (all below) ○ Show booting prompt and load selected kernel ● OS Kernel ○ Initialize hardware/drivers ● Init ○ Mount filesystem, acquire DHCP, start shell, ... 3 MBR – Master Boot Record ● First 512 bytes of disk, outside the FreeBSD filesystem ○ Last 2 Bytes are 0x55AA ○ Corresponding copy in FreeBSD is /boot/boot0 or /boot/mbr nctucs [~] -lctseng- ls -l /boot/boot0 -r--r--r-- 1 root Wheel 512 Nov 12 2014 /boot/boot0 nctucs [~] -lctseng- ls -l /boot/mbr -r--r--r-- 1 root Wheel 512 Nov 12 2014 /boot/mbr nctucs [~] -lctseng- xxd /boot/mbr 00000000: fc31 c08e c08e d88e d0bc 007c be1a 7cbf .1.........|..|. 00000010: 1a06 b9e6 01f3 a4e9 008a 31f6 bbbe 07b1 ..........1..... … 000001d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 000001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ............... -

Initial Bootloader Introduction
initial bootloader Initial Bootloader Introduction On power-up, when a computer is turned on, the following operations are performed: 1. The computer performs a power on self test (POST) to ensure that it meets the necessary requirements and that the hardware is functioning properly. 2. A program located in the ROM BIOS, called the bootstrap loader, is executed. 3. When the bootstrap loader starts it searches for a boot sector and passes control to the boot sector's code area. A boot sector is the first sector of a disk and has a small program in its code area, known as the initial bootstrap program, that can load an operating system. The hardware can recognise a boot sector by hexadecimal signature number AA55 which marks the last two bytes of the sector. The bootstrap loader searches for boot sectors on a number of storage devices, including: ● floppy drives ● CD-ROM drives ● hard drives ● flash drives In almost all computers, the BIOS can be configured to change the order storage devices are searched to control their priority. For example, floppy drives normally have higher priority than hard drives, so if a bootable floppy disk is in the drive when the computer is switched on the computer will boot from the floppy disk; otherwise it will boot from media in another storage device, such as a hard disk. When booting from a hard disk or flash drive, the machine code in the master boot record normally examines the partition table (also in the master boot record), identifies the active partition (the partition that is marked as bootable), reads the boot sector, containing the volume boot record (VBR), from that partition, and then runs the machine code in the volume boot record in the same way code would be run from the boot sector in a floppy disk. -

The Extended FAT File System
Linux Conference October 26- 28, 2011 Prague , Czech Republic Linux Development Center The Extended FAT file system Differentiating with FAT32 file system Keshava Munegowda , Venkatraman S Texas Instruments (India) Pvt Ltd Bangalore. Dr. G T Raju Professor and Head, Computer Science and Engineering Department, 1 R N S Institute of Technology, Bangalore, India. ExFAT Linux Development Center Agenda Ø FAT file system Ø Need for ExFAT file system Ø ExFAT file system organization Ø Boot Sector of FAT and ExFAT Ø Snapshot of Boot Sector of ExFAT Ø Directory Entries of FAT Ø Directory Entries of ExFAT Ø Clusters Heap Ø Up-Case Table Ø Snapshot of Root directory Ø Performance Benchmarking in Linux Ø Performance Benchmarking in Windows 2 Ø References ExFAT Linux Development Center FAT File system Minimum 1 BPB sector BPB - BIOS Parameter Block – BIOS : Basic Input-Output System FAT1 – Also Called as “Boot Sector” or “Volume Boot Record” – Specifies FAT2 • Number of sectors in the storage partition/disk/device Cluster 2 • Number of FATs ( File Allocation Table) Cluster 3 • Sectors per cluster Cluster 4 …………. Data FAT1 – File Allocation Table …………. clusters - Linear linking (chain) of data clusters of the …………. file/directory FAT2 – Backup of FAT1 FILE.TXT cluster3 cluster7 EOF Data clusters - Group of physical/logical sectors/blocks Clusters chain / Linked list of 3 clusters - Contains directories or Files data ExFAT Linux Development Center Need For ExFAT file system l FAT File system limited to support only 32GB. – FAT does not support Higher size SDXC cards. l NTFS – Security features – Optional for Removable storage devices – Meta data overhead for file/directory – Write caching mechanism for performance optimizations causes the data corruption in when 4 removable storage device is unplugged. -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 6 Working with Windows and DOS Systems Objectives • Explain the purpose and structure of file systems • Describe Microsoft file structures • Explain the structure of New Technology File System (NTFS) disks • List some options for decrypting drives encrypted with whole disk encryption Guide to Computer Forensics and Investigations 2 Objectives (continued) • Explain how the Windows Registry works • Describe Microsoft startup tasks • Describe MS-DOS startup tasks • Explain the purpose of a virtual machine Guide to Computer Forensics and Investigations 3 Understanding File Systems • File system – Gives OS a road map to data on a disk • Type of file system an OS uses determines how data is stored on the disk • A file system is usually directly related to an OS • When you need to access a suspect’s computer to acquire or inspect data – You should be familiar with the computer’s platform Guide to Computer Forensics and Investigations 4 Understanding the Boot Sequence • Complementary Metal Oxide Semiconductor (CMOS) – Computer stores system configuration and date and time information in the CMOS • When power to the system is off • Basic Input/Output System (BIOS) – Contains programs that perform input and output at the hardware level Guide to Computer Forensics and Investigations 5 Understanding the Boot Sequence (continued) • Bootstrap process – Contained in ROM, tells the computer how to proceed – Displays the key or keys you press to open the CMOS setup screen • CMOS should -

A History of Computer Viruses -The Famous ‘Trio’
Computers & Security, 16 (1997) 416-429 A History Of Computer Viruses -The Famous ‘Trio’ Harold Joseph Highland FICS, FACM Editor-in-Chief Emeritus It was not until the fall of 1987 that computer virus- was a boot sector infector. The Lehigh virus and the es began to command worldwide attention in the Israeli viruses infected executable code. The former popular press as well as in the trade and technical press. attached itself only to COMMAND.COM; the Israeli Late in 1987 computer viruses struck at two universi- viruses infected .EXE and/or .COM programs. ties in the States and one in Israel. The trio [ 11 also differed in the media attacked. Aside l In October 1987 the Brain or Pakistani virus from the Lehigh virus that infected both floppy disks struck at the University of Delaware. and hard disks, the others only infected floppy disks. These were the original versions of the viruses. Since l One month later, the Lehigh or then a number of variants or mutations have surfaced. COMMAND.COM virus was discovered at Lehigh University in Pennsylvania. l Another difference was the damage or operating difficulties caused by these viruses. In December, the Hebrew University at Jerusalem found itself attacked by a computer virus. In its l The Brain sometimes destroyed several sectors of a search it found the Friday the 13th virus but also disk but often did little more damage. uncovered during that search were two variations of the April 1st or April Fool virus. l The Lehigh virus, depending upon its host, would wipe out an entire disk after a set number of DOS These three incidents presented us with two different operations. -

Design of a Dynamic Boot Loader for Loading an Operating System
Journal of Computer Science Original Research Paper Design of a Dynamic Boot Loader for Loading an Operating System 1Alycia Sebastian and 2Dr. K. Siva Sankar 1Research Scholar, Department of Computer Science and Engineering, Noorul Islam Centre for Higher Education, Tamil Nadu, India 2Department of Information Technology, Noorul Islam Centre for Higher Education, Tamil Nadu, India Article history Abstract: Boot Loader is the crucial program that loads the operating Received: 26-08-2018 system in memory and initializes the system. In today’s world people are Revised: 22-09-2018 constantly on move and portable system are in demand specially the Accepted: 25-01-2019 USB devices due to its portability and accessibility compared to CD/DVD drives. The purpose of this paper is to design a dynamic boot loader which Corresponding Author: Alycia Sebastian removes the BIOS dependency and allow user to boot from USB without Department of Computer changing CMOS settings. The USB is devised as plug and play portable Science and Engineering, Noorul system with puppy Linux and newly developed dynamic boot loader. The Islam Centre for Higher device is experimented on a computer machine with 8 GB RAM, i5 Education, Tamil Nadu, India processor, 64-bit Operating system and windows 7 and observed that nearly Email: [email protected] 50% reduction in booting time i.e., the time spent in changing the boot order is eliminated compared to the static boot loader. The time spent in the BIOS is dependent on the user knowledge in changing the boot priority. The portable system allows the user to work in ease in any environment with minimum requirement of Windows XP and USB 2.0 compatible system. -

Choosing a Boot Loader
CHOOSING A BOOT LOADER Every operating system provides a tiny program called a boot loader whose job is to load the rest of the operating system into your computer’s memory at boot time. It is typical of the Linux personality that it gives you a choice of boot loaders. If you will be running Linux on a computer by itself, there is no need to read any further, you want to use LILO as your boot loader. You can skip ahead to the section about LILO. If you are planning for Linux to share your computer with Windows, DOS, or another operating system, your choice will involve a little more discrimination. When setting up a multiple boot PC with Linux, you have three choices about how to get it loaded: LILO, Loadlin, or floppy. Let’s examine each separately. LILO, the Linux Loader Although opinions vary, LILO is certainly the most popular boot loader for Linux. It resides on your hard drive, and at boot time it presents you with a “boot prompt” where you can choose an operating system to boot, choose a particular Linux kernel to load, and pass special parameters to the Linux kernel when it is loaded. LILO is fast, flexible, and independent, since it does not require any other operating system to be present. This makes it the loader of choice for Linux-only systems. LILO does have a few limitations, however, which means it is not perfect for everyone. For starters, LILO can install itself in two places on your hard drive: the boot sector of a partition (what’s a partition?), or the master boot record of the hard drive.