Lessons Learned: a Security Analysis of the Internet Chess Club
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Solved Openings in Losing Chess
1 Solved Openings in Losing Chess Mark Watkins, School of Mathematics and Statistics, University of Sydney 1. INTRODUCTION Losing Chess is a chess variant where each player tries to lose all one’s pieces. As the naming of “Giveaway” variants has multiple schools of terminology, we state for definiteness that captures are compulsory (a player with multiple captures chooses which to make), a King can be captured like any other piece, Pawns can promote to Kings, and castling is not legal. There are competing rulesets for stalemate: International Rules give the win to the player on move, while FICS (Free Internet Chess Server) Rules gives the win to the player with fewer pieces (and a draw if equal). Gameplay under these rulesets is typically quite similar.1 Unless otherwise stated, we consider the “joint” FICS/International Rules, where a stalemate is a draw unless it is won under both rulesets. There does not seem to be a canonical place for information about Losing Chess. The ICGA webpage [H] has a number of references (notably [Li]) and is a reasonable historical source, though the page is quite old and some of the links are broken. Similarly, there exist a number of piecemeal Internet sites (I found the most useful ones to be [F1], [An], and [La]), but again some of these have not been touched in 5-10 years. Much of the information was either outdated or tangential to our aim of solving openings (in particular responses to 1. e3), We started our work in late 2011. The long-term goal was to weakly solve the game, presumably by showing that 1. -

E-Magazine July 2020
E-MAGAZINE JULY 2020 0101 #EOCC2020 European Online Corporate Championships announced for 3 & 4 of October #EOYCC2020 European Online Youth Chess Championhsip announced for 18-20 September. International Chess Day recognised by United Nations & UNESCO celebrated all over the World #InternationalChessDay On, 20th of July, World celebrates the #InternationalChessDay. The International Chess Federation (FIDE) was founded, 96 years ago on 20th July 1924. The idea to celebrate this day as the International Chess Day was proposed by UNESCO, and it has been celebrated as such since 1966. On December 12, 2019, the UN General Assembly unanimously approved a resolution recognising the World Chess Day. On the occasion of the International Chess Day, a tele-meeting between the United Nations and FIDE was held on 20th of July 2020. Top chess personalities and representatives of the U.N. gathered to exchange views and insights to strengthen the productive collaboration European Chess Union has its seat in Switzerland, Address: Rainweidstrasse 2, CH-6333, Hunenberg See, Switzerland ECU decided to make a special promotional #Chess video. Mr. European Chess Union is an independent Zurab Azmaiparashvili visited the Georgian most popular Musical association founded in 1985 in Graz, Austria; Competition Show “Big stage”.ECU President taught the judges of European Chess Union has 54 National Federation Members; Every year ECU organizes more than 20 show, famous artists, how to play chess and then played a game with prestigious events and championships. them! www.europechess.org Federations, clubs, players and chess lovers took part in the [email protected] celebration all over the world. -

The Queen's Gambit
01-01 Cover - April 2021_Layout 1 16/03/2021 13:03 Page 1 03-03 Contents_Chess mag - 21_6_10 18/03/2021 11:45 Page 3 Chess Contents Founding Editor: B.H. Wood, OBE. M.Sc † Editorial....................................................................................................................4 Executive Editor: Malcolm Pein Malcolm Pein on the latest developments in the game Editors: Richard Palliser, Matt Read Associate Editor: John Saunders 60 Seconds with...Geert van der Velde.....................................................7 Subscriptions Manager: Paul Harrington We catch up with the Play Magnus Group’s VP of Content Chess Magazine (ISSN 0964-6221) is published by: A Tale of Two Players.........................................................................................8 Chess & Bridge Ltd, 44 Baker St, London, W1U 7RT Wesley So shone while Carlsen struggled at the Opera Euro Rapid Tel: 020 7486 7015 Anish Giri: Choker or Joker?........................................................................14 Email: [email protected], Website: www.chess.co.uk Danny Gormally discusses if the Dutch no.1 was just unlucky at Wijk Twitter: @CHESS_Magazine How Good is Your Chess?..............................................................................18 Twitter: @TelegraphChess - Malcolm Pein Daniel King also takes a look at the play of Anish Giri Twitter: @chessandbridge The Other Saga ..................................................................................................22 Subscription Rates: John Henderson very much -

A New Dimension in Online Chess?
A new Dimension in online chess? Online chess explores uncharted territory by using cryptocurrency as prizemoney. The famous FICS (free internet chess server) probably was the forerunner in online chess back in the early 90ies when there wasn't even a graphical user interface. Soon chess was comfortably played with a mouse with features such as „premove“ in different chess variants and any possible timecontrol. It became clear, that the internet and chess had a loveaffair. From FICS evolved the ICC, probably the first commercial chess server, which extended the functionality even further and still is the playground for the majority of GM's. This span greater controversies over the re-use of code of a free-for-all server for a commercial project. FICS still provides its service without charging any fees and relies on donations. The chessbase server followed and nowadays regular chess software often includes online accounts. As soon as online tournaments were played for prizemoney cheating became a major concern. Even some Grandmasters were tempted to use computer assistance to improve their chances and now every major chess server has a crew for cheating detection, which seems to work more or less. Maybe partly because cheating detection in online chess is even harder than in regular over-the- board tournaments, these online tournaments with substantial prizemoney are rather seldom. But the fundamental detriment for such tournaments certainly was and is the contradiction of online anonymity, where players don't hesitate to choose handles such as „I_love_DD“ or simply „supergod“ and the need for identity verification, when it comes to paying out the prizes. -

Glossary of Chess
Glossary of chess See also: Glossary of chess problems, Index of chess • X articles and Outline of chess • This page explains commonly used terms in chess in al- • Z phabetical order. Some of these have their own pages, • References like fork and pin. For a list of unorthodox chess pieces, see Fairy chess piece; for a list of terms specific to chess problems, see Glossary of chess problems; for a list of chess-related games, see Chess variants. 1 A Contents : absolute pin A pin against the king is called absolute since the pinned piece cannot legally move (as mov- ing it would expose the king to check). Cf. relative • A pin. • B active 1. Describes a piece that controls a number of • C squares, or a piece that has a number of squares available for its next move. • D 2. An “active defense” is a defense employing threat(s) • E or counterattack(s). Antonym: passive. • F • G • H • I • J • K • L • M • N • O • P Envelope used for the adjournment of a match game Efim Geller • Q vs. Bent Larsen, Copenhagen 1966 • R adjournment Suspension of a chess game with the in- • S tention to finish it later. It was once very common in high-level competition, often occurring soon af- • T ter the first time control, but the practice has been • U abandoned due to the advent of computer analysis. See sealed move. • V adjudication Decision by a strong chess player (the ad- • W judicator) on the outcome of an unfinished game. 1 2 2 B This practice is now uncommon in over-the-board are often pawn moves; since pawns cannot move events, but does happen in online chess when one backwards to return to squares they have left, their player refuses to continue after an adjournment. -

The Knights Handbook
The Knights Handbook Miha Canˇculaˇ The Knights Handbook 2 Contents 1 Introduction 6 2 How to play 7 2.1 Objective . .7 2.2 Starting the Game . .7 2.3 The Chess Server Dialog . .9 2.4 Playing the Game . 11 3 Game Rules, Strategies and Tips 12 3.1 Standard Rules . 12 3.2 Chessboard . 12 3.2.1 Board Layout . 12 3.2.2 Initial Setup . 13 3.3 Piece Movement . 14 3.3.1 Moving and Capturing . 14 3.3.2 Pawn . 15 3.3.3 Bishop . 16 3.3.4 Rook . 17 3.3.5 Knight . 18 3.3.6 Queen . 18 3.3.7 King . 19 3.4 Special Moves . 20 3.4.1 En Passant . 20 3.4.2 Castling . 21 3.4.3 Pawn Promotion . 22 3.5 Game Endings . 23 3.5.1 Checkmate . 23 3.5.2 Resign . 23 3.5.3 Draw . 23 3.5.4 Stalemate . 24 3.5.5 Time . 24 3.6 Time Controls . 24 The Knights Handbook 4 Markers 25 5 Game Configuration 27 5.1 General . 27 5.2 Computer Engines . 28 5.3 Accessibility . 28 5.4 Themes . 28 6 Credits and License 29 4 Abstract This documentation describes the game of Knights version 2.5.0 The Knights Handbook Chapter 1 Introduction GAMETYPE: Board NUMBER OF POSSIBLE PLAYERS: One or two Knights is a chess game. As a player, your goal is to defeat your opponent by checkmating their king. 6 The Knights Handbook Chapter 2 How to play 2.1 Objective Moving your pieces, capture your opponent’s pieces until your opponent’s king is under attack and they have no move to stop the attack - called ‘checkmate’. -

White Knight Review September-October- 2010
Chess Magazine Online E-Magazine Volume 1 • Issue 1 September October 2010 Nobel Prize winners and Chess The Fischer King: The illusive life of Bobby Fischer Pt. 1 Sight Unseen-The Art of Blindfold Chess CHESS- theres an app for that! TAKING IT TO THE STREETS Street Players and Hustlers White Knight Review September-October- 2010 White My Move [email protected] Knight editorial elcome to our inaugural Review WIssue of White Knight Review. This chess magazine Chess E-Magazine was the natural outcome of the vision of 3 brothers. The unique corroboration and the divers talent of the “Wall boys” set in motion the idea of putting together this White Knight Table of Contents contents online publication. The oldest of the three is my brother Bill. He Review EDITORIAL-”My Move” 3 is by far the Chess expert of the group being the Chess E-Magazine author of over 30 chess books, several websites on the internet and a highly respected player in FEATURE-Taking it to the Streets 4 the chess world. His books and articles have spanned the globe and have become a wellspring of knowledge for both beginners and Executive Editor/Writer BOOK REVIEW-Diary of a Chess Queen 7 masters alike. Bill Wall Our younger brother is the entrepreneur [email protected] who’s initial idea of a marketable website and HISTORY-The History of Blindfold Chess 8 promoting resource material for chess players became the beginning focus on this endeavor. His sales and promotion experience is an FEATURE-Chessman- Picking up the pieces 10 integral part to the project. -

The Queen's Gambit
Master Class with Aagaard | Shankland on the Online Olympiad | Spiegel’s Three Questions NOVEMBER 2020 | USCHESS.ORG The Queen’s Gambit A new Netflix limited series highlights the Royal Game A seasonal gift from US CHESS: A free copy of Chess Life! NOVEMBER 17, 2020 Dear Chess Friends: GM ELIZABETH SPIEGEL When one of our members has a good idea, we take it seriously. Tweeting on October 31 – Halloween Day! – National Master Han Schut GM JESSE suggested we provide a “holiday present” to chess players around the world. KRAAI GM JACOB AAGAARD What a swell idea. Chess Life is the official magazine of US Chess. Each month we here at FM CARSTEN Chess Life work to publish the best of American chess in all of its facets. HANSEN In recent issues we have brought you articles by GM Jesse Kraai on chess in the time of coronavirus; GM Jon Tisdall’s look at online chess; IM Eric Rosen on “the new chess boom,” featuring a cover that went Michael Tisserand IM JOHN viral on social media!; on Charlie Gabriel, the WATSON coolest octogenarian jazz player and chess fan in New Orleans; and GM Maurice Ashley on 11-year-old phenom IM Abhimanyu Mishra. IM ERIC Our November issue has gained wide attention across the world for its cover ROSEN story on the Netflix limited series The Queen’s Gambit by longtime Chess Life columnist Bruce Pandolfini.It also features articles by GM Jacob Aagaard GM Sam Shankland WFM Elizabeth Spiegel GM MAURICE , , and , made ASHLEY famous in the 2012 documentary Brooklyn Castle. -

Predicting Chess Player Strength from Game Annotations
Picking the Amateur’s Mind – Predicting Chess Player Strength from Game Annotations Christian Scheible Hinrich Schutze¨ Institute for Natural Language Processing Center for Information University of Stuttgart, Germany and Language Processing [email protected] University of Munich, Germany Abstract Results from psychology show a connection between a speaker’s expertise in a task and the lan- guage he uses to talk about it. In this paper, we present an empirical study on using linguistic evidence to predict the expertise of a speaker in a task: playing chess. Instructional chess litera- ture claims that the mindsets of amateur and expert players differ fundamentally (Silman, 1999); psychological science has empirically arrived at similar results (e.g., Pfau and Murphy (1988)). We conduct experiments on automatically predicting chess player skill based on their natural lan- guage game commentary. We make use of annotated chess games, in which players provide their own interpretation of game in prose. Based on a dataset collected from an online chess forum, we predict player strength through SVM classification and ranking. We show that using textual and chess-specific features achieves both high classification accuracy and significant correlation. Finally, we compare ourfindings to claims from the chess literature and results from psychology. 1 Introduction It has been recognized that the language used when describing a certain topic or activity may differ strongly depending on the speaker’s level of expertise. As shown in empirical experiments in psychology (e.g., Solomon (1990), Pfau and Murphy (1988)), a speaker’s linguistic choices are influenced by the way he thinks about the topic. -

An Historical Perspective Through the Game of Chess
On the Impact of Information Technologies on Society: an Historical Perspective through the Game of Chess Fr´ed´eric Prost LIG, Universit´ede Grenoble B. P. 53, F-38041 Grenoble, France [email protected] Abstract The game of chess as always been viewed as an iconic representation of intellectual prowess. Since the very beginning of computer science, the challenge of being able to program a computer capable of playing chess and beating humans has been alive and used both as a mark to measure hardware/software progresses and as an ongoing programming challenge leading to numerous discoveries. In the early days of computer science it was a topic for specialists. But as computers were democratized, and the strength of chess engines began to increase, chess players started to appropriate to themselves these new tools. We show how these interac- tions between the world of chess and information technologies have been herald of broader social impacts of information technologies. The game of chess, and more broadly the world of chess (chess players, literature, computer softwares and websites dedicated to chess, etc.), turns out to be a surprisingly and particularly sharp indicator of the changes induced in our everyday life by the information technologies. Moreover, in the same way that chess is a modelization of war that captures the raw features of strategic thinking, chess world can be seen as small society making the study of the information technologies impact easier to analyze and to arXiv:1203.3434v1 [cs.OH] 15 Mar 2012 grasp. Chess and computer science Alan Turing was born when the Turk automaton was finishing its more than a century long career of illusion1. -
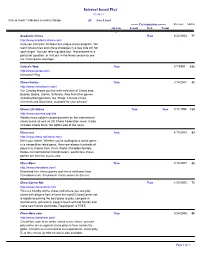
Internet Based Play 01-08-11
Internet based Play 01-08-11 One or more * indicates a recent change. 25 Sites Listed ------- Correspondence------- Revised Mnths On-Lin E-mail Web Postal e Academic Chess True 8/22/2004 77 http://www.academicchess.com/ Here you can learn all about our unique chess program. We teach chess rules and chess strategies in a way kids will not soon forget. You can take a guided tour, find answers to a particular question, or visit our In the News section to see our chess press coverage. Caissa's Web True 7/7/1997 162 http://www.caissa.com/ Interactive Play. Chess Forum True 7/14/2007 42 http://www.chessforum.com/ Our Catalog shows you the wide selection of Chess sets, Boards, Books, Clocks, Software. Also find other games including Backgammon, Go, Shogi, Chinese chess, Checkers and Dominoes, available for your perusal Chess Life Online True True 7/11/1998 150 http://www.uschess.org/clife Weekly news column covering events on the international chess scene as well as US Chess Federation news. It also includes Chess Buzz, the lighter side of the news. Chess.net True 4/11/2003 93 http://www.chess.net/home.html Meet your match. Whether you're looking for a social game or a competitive rated game, there are always hundreds of players to choose from. From World Champion Anatoly Karpov to International Grandmasters, world class chess games are here for you to view. ChessBoss True 7/14/2007 42 http://www.chessboss.com/ Download free chess games and chess softwares from Chessboss.com, the premier chess server on the net. -

The Impact of Artificial Intelligence on the Chess World
JMIR SERIOUS GAMES Duca Iliescu Viewpoint The Impact of Artificial Intelligence on the Chess World Delia Monica Duca Iliescu, BSc, MSc Transilvania University of Brasov, Brasov, Romania Corresponding Author: Delia Monica Duca Iliescu, BSc, MSc Transilvania University of Brasov Bdul Eroilor 29 Brasov Romania Phone: 40 268413000 Email: [email protected] Abstract This paper focuses on key areas in which artificial intelligence has affected the chess world, including cheat detection methods, which are especially necessary recently, as there has been an unexpected rise in the popularity of online chess. Many major chess events that were to take place in 2020 have been canceled, but the global popularity of chess has in fact grown in recent months due to easier conversion of the game from offline to online formats compared with other games. Still, though a game of chess can be easily played online, there are some concerns about the increased chances of cheating. Artificial intelligence can address these concerns. (JMIR Serious Games 2020;8(4):e24049) doi: 10.2196/24049 KEYWORDS artificial intelligence; games; chess; AlphaZero; MuZero; cheat detection; coronavirus strategic games, has affected many other areas of interest, as Introduction has already been seen in recent years. All major chess events that were to take place in the second half One of the most famous human versus machine events was the of 2020 have been canceled, including the 44th Chess Olympiad 1997 victory of Deep Blue, an IBM chess software, against the and the match for the title of World Chess Champion. However, famous chess champion Garry Kasparov [3].