HAMMER and Postgresql Performance Jan Lentfer Oct. 2009
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Database Licensing Information, 11G Release 2 (11.2) E10594-26
Oracle® Database Licensing Information 11g Release 2 (11.2) E10594-26 July 2012 Oracle Database Licensing Information, 11g Release 2 (11.2) E10594-26 Copyright © 2004, 2012, Oracle and/or its affiliates. All rights reserved. Contributor: Manmeet Ahluwalia, Penny Avril, Charlie Berger, Michelle Bird, Carolyn Bruse, Rich Buchheim, Sandra Cheevers, Leo Cloutier, Bud Endress, Prabhaker Gongloor, Kevin Jernigan, Anil Khilani, Mughees Minhas, Trish McGonigle, Dennis MacNeil, Paul Narth, Anu Natarajan, Paul Needham, Martin Pena, Jill Robinson, Mark Townsend This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. -

The Dragonflybsd Operating System
1 The DragonFlyBSD Operating System Jeffrey M. Hsu, Member, FreeBSD and DragonFlyBSD directories with slightly over 8 million lines of code, 2 million Abstract— The DragonFlyBSD operating system is a fork of of which are in the kernel. the highly successful FreeBSD operating system. Its goals are to The project has a number of resources available to the maintain the high quality and performance of the FreeBSD 4 public, including an on-line CVS repository with mirror sites, branch, while exploiting new concepts to further improve accessible through the web as well as the cvsup service, performance and stability. In this paper, we discuss the motivation for a new BSD operating system, new concepts being mailing list forums, and a bug submission system. explored in the BSD context, the software infrastructure put in place to explore these concepts, and their application to the III. MOTIVATION network subsystem in particular. A. Technical Goals Index Terms— Message passing, Multiprocessing, Network The DragonFlyBSD operating system has several long- operating systems, Protocols, System software. range technical goals that it hopes to accomplish within the next few years. The first goal is to add lightweight threads to the BSD kernel. These threads are lightweight in the sense I. INTRODUCTION that, while user processes have an associated thread and a HE DragonFlyBSD operating system is a fork of the process context, kernel processes are pure threads with no T highly successful FreeBSD operating system. Its goals are process context. The threading model makes several to maintain the high quality and performance of the FreeBSD guarantees with respect to scheduling to ensure high 4 branch, while exploring new concepts to further improve performance and simplify reasoning about concurrency. -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Notice for Netapp HCI
Notice About this document The following copyright statements and licenses apply to software components that are distributed with various versions of the NetApp HCI products. Your product does not necessarily use all the software components referred to below. Where required, source code is published at the following location: https://opensource.netapp.com/ 1 Notice Copyrights and licenses The following component(s) is(are) subject to the AESLib License (BSD 2.0 -) • AESLib License contribution to skein - Unspecified Copyright (c) 2003, Dr Brian Gladman, Worcester, UK. All rights reserved. AESLib License (BSD 2.0 -) Copyright (c) 2003, Copera, Inc., Mountain View, CA, USA. All rights reserved. LICENSE TERMS The free distribution and use of this software in both source and binary form is allowed (with or without changes) provided that: 1. distributions of this source code include the above copyright notice, this list of conditions and the following disclaimer; 2. distributions in binary form include the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other associated materials; 3. the copyright holder's name is not used to endorse products built using this software without specific written permission. DISCLAIMER This software is provided 'as is' with no explcit or implied warranties in respect of any properties, including, but not limited to, correctness and fitness for purpose. ------------------------------------------------------------------------- Issue Date: March 10, 2003 2 Notice The following component(s) is(are) subject to the Apache 1.1 • Apache Base64 functions - Unspecified Copyright (c) 1995-1999 The Apache Group. All rights reserved. Apache Software License Version 1.1 Copyright (c) 2000 The Apache Software Foundation. -

Mandoc: Becoming the Main BSD Manual Toolbox
mandoc: becoming the main BSD manual toolbox BSDCan 2015, June 13, Ottawa Ingo Schwarze <[email protected]> Cynthia Livingston’sOTTB “Bedifferent” (c) 2013 C. Livingston (with permission) > Ingo Schwarze: mandoc page 2: INTROI BSDCan 2015, June 13, Ottawa Brief history of UNIX documentation • The key point: All documentation in one place and one format. Easy to find, uniform and easy to read and write. Be correct, complete, concise. • 1964: RUNOFF/roffmarkup syntax by Jerome H. Saltzer,MIT. Unobtrusive,diff(1)-friendly,easy to hand-edit, simple tools, high quality output. • 1971: Basic manual structure by Ken Thompson and Dennis Ritchie for the AT&T Version 1 UNIX manuals, Bell Labs. • 1979: man(7) physical markup language for AT&T Version 7 UNIX. • 1989: mdoc(7) semantic markup by Cynthia Livingston for 4.3BSD-Reno. Powerful, self-contained, portable. • 1989: GNU troffbyJames Clarke. • 2001: mdoc(7) rewrite by Werner Lemberg and Ruslan Ermilovfor groff-1.17. • 2008: mandoc(1) started by Kristaps Dzonsons. • 2010: mandoc(1) is the only documentation formatter in the OpenBSD base system. • 2014: mandoc(1) used by default in OpenBSD, FreeBSD, NetBSD, illumos. 16:19:30 What is the mandoc toolbox? → < > Ingo Schwarze: mandoc page 3: INTROIIBSDCan 2015, June 13, Ottawa What is the mandoc toolbox? User perspective:man(1), the manual viewer One comprehensive tool! Normal operation always proceeds in three steps: 1. Find one or more manuals in the file system or using a database by manual name — man(1) — or by search query — apropos(1) =man -k The result of this step can be printed out with man -w. -

Jordan Hubbard Apple Computer, Inc. Oh Really?
*BSD is dying - Anonymous Coward, Slashdot ©1993, 1994, 1995, 1996, 1997, 1998, 1999, 2000, 2001, 2002, 2003, 2004 Jordan Hubbard Apple Computer, Inc. Oh really? Let’s look at some stats... FreeBSD Users: 2.5 Million Server Installations (Netcraft) 2,500,000 1,875,000 1,250,000 625,000 0 1993 1997 2001 2003 2004 12 Mac OS X Users: 9 6 3 0 12 Million Jul '01 Oct '01 Jan '02 Apr '02 Jul '02 Oct '02 Jan '03 Apr '03 Jun '03 Oct '03 Oct '04 Applications: FreeBSD ports 12,000 9,000 6,000 10,796 9,662 3,000 6,077 2,723 1,161 0 209 1995 1997 1999 2001 2003 2004 Applications: 12,000 Mac OS X Native 12,000 9,000 6,000 3,000 0 Apr '01 Jul '01 Oct '01 Jan '02 Apr '02 Jul '02 Oct '02 Jan '03 Apr '03 Jun '03 Oct '03 Oct '04 Since the arrival of Mac OS X, BSD has become the biggest desktop UNIX variant on the planet. Yes, even bigger than Linux Take that, Anonymous Coward! Selective overview of Mac OS X Mac OS X Architecture Applications User Interface Application Frameworks Graphics and Media System Services OS Foundation Apple Confidential OS Foundation Usermode BSD Commands and Usermode User FileSystem Libraries Drivers Kernel BSD Kernel IOKit Driver FileSystem Network Families Process Management Drivers Mach Kernel VM Scheduling IPC Open Source “Darwin” base OS Foundation Usermode BSD Commands and Usermode User FileSystem Libraries Drivers Kernel BSD Kernel IOKit Driver FileSystem Network Families Process Management Drivers Mach Kernel VM Scheduling IPC BSD Kernel • FreeBSD 5.1 based (networking, vfs, filesystems, etc) • Unified Buffer Cache (different -

BSD Projects IV – BSD Certification • Main Features • Community • Future Directions a (Very) Brief History of BSD
BSD Overview Jim Brown May 24, 2012 BSD Overview - 5/24/2012 - Jim Brown, ISD BSD Overview I – A Brief History of BSD III – Cool Hot Stuff • ATT UCB Partnership • Batteries Included • ATT(USL) Lawsuit • ZFS , Hammer • BSD Family Tree • pf Firewall, pfSense • BSD License • Capsicum • Virtualization Topics • Jails, Xen, etc. • Desktop PC-BSD II – The Core BSD Projects IV – BSD Certification • Main Features • Community • Future Directions A (Very) Brief History of BSD 1971 – ATT cheaply licenses Unix source code to many organizations, including UCB as educational material 1975 – Ken Thompson takes a sabbatical from ATT, brings the latest Unix source on tape to UCB his alma mater to run on a PDP 11 which UCB provided. (Industry/academic partnerships were much more common back then.) Computer Science students (notably Bill Joy and Chuck Haley) at UCB begin to make numerous improvements to Unix and make them available on tape as the “Berkeley Software Distribution” - BSD A (Very) Brief History of BSD Some notable CSRG • 1980 – Computer Science Research Group members (CSRG) forms at UCB with DARPA funding to make many more improvements to Unix - job control, autoreboot, fast filesystem, gigabit address space, Lisp, IPC, sockets, TCP/IP stack + applications, r* utils, machine independence, rewriting almost all ATT code with UCB/CSRG code, including many ports • 1991 – The Networking Release 2 tape is released on the Internet via anon FTP. A 386 port quickly follows by Bill and Lynne Jolitz. The NetBSD group is formed- the first Open Source community entirely on the Internet • 1992 – A commercial version, BSDI (sold for $995, 1-800-ITS-UNIX) draws the ire of USL/ATT. -
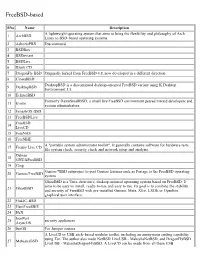
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

ZFS Boot Environments Reloaded NLUUG ZFS Boot Environments Reloaded
ZFS Boot Environments Reloaded NLUUG ZFS Boot Environments Reloaded Sławomir Wojciech Wojtczak [email protected] vermaden.wordpress.com twitter.com/vermaden https://is.gd/BECTL ntro !"#$%##%#& ZFS Boot Environments Reloaded NLUUG What is ZFS Boot Environment? Its bootable clone%sna(shot of the working system. What it is' !"#$%##%#& ZFS Boot Environments Reloaded NLUUG What is ZFS Boot Environment? Its bootable clone%sna(shot of the working system. ● In ZFS terminology its clone of the snapshot. ZFS dataset → ZFS dataset@snapshot → ZFS clone (origin=dataset@snapshot) What it is' !"#$%##%#& ZFS Boot Environments Reloaded NLUUG What is ZFS Boot Environment? Its bootable clone%sna(shot of the working system. ● In ZFS terminology its clone of the snapshot. ZFS dataset → ZFS dataset@snapshot → ZFS clone (origin=dataset@snapshot) ● In ZFS (as everywhere) sna(shot is read onl). What it is' !"#$%##%#& ZFS Boot Environments Reloaded NLUUG What is ZFS Boot Environment? Its bootable clone%sna(shot of the working system. ● In ZFS terminology its clone of the snapshot. ZFS dataset → ZFS dataset@snapshot → ZFS clone (origin=dataset@snapshot) ● In ZFS (as everywhere) sna(shot is read onl). ● In ZFS clone can be mounted read write (and you can boot from it). What it is' !"#$%##%#& ZFS Boot Environments Reloaded NLUUG What is ZFS Boot Environment? Its bootable clone%sna(shot of the working system. ● In ZFS terminology its clone of the snapshot. ZFS dataset → ZFS dataset@snapshot → ZFS clone (origin=dataset@snapshot) ● In ZFS (as everywhere) sna(shot is read onl). ● In ZFS clone can be mounted read write (and you can boot from it). -

Openafs: BSD Clients 2009
OpenAFS: BSD Clients 2009 Matt Benjamin <[email protected]> OpenAFS: BSD Clients 2009 Who am I? ● OpenAFS developer interested in various new-code development topics ● for the last while, “portmaster” for BSD clients except DARWIN/MacOS X ● involves evolving the ports, interfacing withusers and port maintainers in the BSD communities OpenAFS: BSD Clients 2009 Former Maintainers ● Tom Maher, MIT ● Jim Rees, University of Michigan (former Gatekeeper and Elder) ● Garret Wollman, MIT OpenAFS: BSD Clients 2009 Other Active ● Ben Kaduk (FreeBSD) ● Tony Jago (FreeBSD) ● Jamie Fournier (NetBSD) OpenAFS: BSD Clients 2009 Historical Remarks ● AFS originated in a BSD 4.2 environment ● extend UFS with coherence across a group of machines ● Terminology in common with BSD, SunOS, etc, e.g., vnodes ● Followed SunOS and Ultrix to Solaris and Digital Unix in Transarc period ● 386BSD released at 4.3 level in the Transarc period, some client development never publically released (or independent of Transarc) OpenAFS: BSD Clients 2009 BSD Clients Today ● Descendents of 386BSD distribution and successors, not including DARWIN/MacOS X ● DARWIN separately maintained, though of course there are similarities OpenAFS: BSD Clients 2009 Today ● FreeBSD ● OpenBSD Soon ● NetBSD ● OpenBSD Not yet supported (as a client): ● Dragonfly BSD OpenAFS: BSD Clients 2009 BSD Port History I ● First 386BSD port probably that of John Kohl (MIT), for NetBSD ● First to appear in OpenAFS is FreeBSD, by Tom Maher ● Next to appear in OpenAFS is OpenBSD, by Jim Rees ● Significant evolution -

Matthew Dillon Dragonfly BSD Project 23 October 2003 Dragonfly Overview
Matthew Dillon DragonFly BSD Project 23 October 2003 DragonFly Overview ●FreeBSD 4.x and 5.x directions ●Differentiating DragonFly, the basis for a project fork ● A different, more maintainable user threading API (syscall messaging) ● A different, more maintainable approach to MP design ● CPU Isolation by design using IPI messaging rather then by accident w/Mutexes ● Light Weight Kernel Threading with fewer hacks ●Project Goals ● Maintaining stability, producing production-capable releases ● A more consistent and more easily maintained message-based framework ● UP, MP, SSI Scaleability ● Userland VFS Development ● Machine-verified Package Management ●This Presentation ● Threading And Messaging ● Our approach to the Big Giant Lock problem. Why not mutexes? ● Our approach to achieving a Single System Image (SSI) DragonFly Threading and Messaging Model Matthew Dillon DragonFly BSD Project 23 October 2003 Light Weight Kernel Threading and User Processes LWKT SUBSYSTEM USERLAND PROCESS SCHEDULER CPU #1 PROCESS RUNQ SCHEDULER THREAD LWKT SCHEDULER THREAD PROCESS1 (FIXED PRIORITY) PROCESS2 THREAD PROCESS2 CURPROC ON CPU1 PROCESS3 CPU #2 THREAD PROCESS4 LWKT SCHEDULER PROCESS5 THREAD PROCESS5 (FIXED PRIORITY) CURPROC ON CPU2 THREAD PROCESS6 IPI Messaging ●ABSTRACTION PROMOTES CPU ISOLATION ●ASYNCHRONOUS IPI MESSAGING AVOIDS MUTEX OPS ●SIMPLE CRITICAL SECTIONS FOR LOCAL ACCESS ●MANY IPI OPS CAN BE PASSIVE / CONTRAST W/ RCU CPU #1 CPU #2 SCHEDULER SCHEDULER ASYNC THREAD1 SCHEDULE IPI SCHEDULE THREAD2 THREAD2 MESSAGE THREAD2 ALLOCATOR ALLOCATE MEMORY -

Evolutionary Tree-Structured Storage: Concepts, Interfaces, and Applications
Evolutionary Tree-Structured Storage: Concepts, Interfaces, and Applications Dissertation submitted for the degree of Doctor of Natural Sciences Presented by Marc Yves Maria Kramis at the Faculty of Sciences Department of Computer and Information Science Date of the oral examination: 22.04.2014 First supervisor: Prof. Dr. Marcel Waldvogel Second supervisor: Prof. Dr. Marc Scholl i Abstract Life is subdued to constant evolution. So is our data, be it in research, business or personal information management. From a natural, evolutionary perspective, our data evolves through a sequence of fine-granular modifications resulting in myriads of states, each describing our data at a given point in time. From a technical, anti- evolutionary perspective, mainly driven by technological and financial limitations, we treat the modifications as transient commands and only store the latest state of our data. It is surprising that the current approach is to ignore the natural evolution and to willfully forget about the sequence of modifications and therefore the past state. Sticking to this approach causes all kinds of confusion, complexity, and performance issues. Confusion, because we still somehow want to retrieve past state but are not sure how. Complexity, because we must repeatedly work around our own obsolete approaches. Performance issues, because confusion times complexity hurts. It is not surprising, however, that intelligence agencies notoriously try to collect, store, and analyze what the broad public willfully forgets. Significantly faster and cheaper random-access storage is the key driver for a paradigm shift towards remembering the sequence of modifications. We claim that (1) faster storage allows to efficiently and cleverly handle finer-granular modifi- cations and (2) that mandatory versioning elegantly exposes past state, radically simplifies the applications, and effectively lays a solid foundation for backing up, distributing and scaling of our data.