Chapter 8: TCP/IP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Internet Protocol, Version 4 (Ipv4)
Today’s Lecture I. IPv4 Overview The Internet Protocol, II. IP Fragmentation and Reassembly Version 4 (IPv4) III. IP and Routing IV. IPv4 Options Internet Protocols CSC / ECE 573 Fall, 2005 N.C. State University copyright 2005 Douglas S. Reeves 1 copyright 2005 Douglas S. Reeves 2 Internet Protocol v4 (RFC791) Functions • A universal intermediate layer • Routing IPv4 Overview • Fragmentation and reassembly copyright 2005 Douglas S. Reeves 3 copyright 2005 Douglas S. Reeves 4 “IP over Everything, Everything Over IP” IP = Basic Delivery Service • Everything over IP • IP over everything • Connectionless delivery simplifies router design – TCP, UDP – Dialup and operation – Appletalk – ISDN – Netbios • Unreliable, best-effort delivery. Packets may be… – SCSI – X.25 – ATM – Ethernet – lost (discarded) – X.25 – Wi-Fi – duplicated – SNA – FDDI – reordered – Sonet – ATM – Fibre Channel – Sonet – and/or corrupted – Frame Relay… – … – Remote Direct Memory Access – Ethernet • Even IP over IP! copyright 2005 Douglas S. Reeves 5 copyright 2005 Douglas S. Reeves 6 1 IPv4 Datagram Format IPv4 Header Contents 0 4 8 16 31 •Version (4 bits) header type of service • Functions version total length (in bytes) length (x4) prec | D T R C 0 •Header Length x4 (4) flags identification fragment offset (x8) 1. universal 0 DF MF s •Type of Service (8) e time-to-live (next) protocol t intermediate layer header checksum y b (hop count) identifier •Total Length (16) 0 2 2. routing source IP address •Identification (16) 3. fragmentation and destination IP address reassembly •Flags (3) s •Fragment Offset ×8 (13) e t 4. Options y IP options (if any) b •Time-to-Live (8) 0 4 ≤ •Protocol Identifier (8) s e t •Header Checksum (16) y b payload 5 •Source IP Address (32) 1 5 5 6 •Destination IP Address (32) ≤ •IP Options (≤ 320) copyright 2005 Douglas S. -

Nist Sp 800-77 Rev. 1 Guide to Ipsec Vpns
NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel Karen Scarfone Paul Wouters This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 C O M P U T E R S E C U R I T Y NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel* Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA Paul Wouters Red Hat Toronto, ON, Canada *Former employee; all work for this publication was done while at NIST This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 June 2020 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority. -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -

The Original Version of This Chapter Was Revised: the Copyright Line Was Incorrect
The original version of this chapter was revised: The copyright line was incorrect. This has been corrected. The Erratum to this chapter is available at DOI: 10.1007/978-0-387-35516-0_20 H. Ural et al. (eds.), Testing of Communicating Systems © IFIP International Federation for Information Processing 2000 114 TESTING OF COMMUNICATING SYSTEMS protocols in TTCN mainly by ETSI and ITU-T. Most of the telecom vendor companies use TTCN in their internal test procedures because of its usefulness in protocol testing. Tools exist supporting the writing and execution of TTCN test cases as well as generating them from formal specifications written in SDL (Specification Description Language) or MSC (Message Sequence Chart). Telecom service providers are also executing conformance testing on the products they buy to check if it fulfills the requirements described in the protocol standards. This is a main step assuring the interoperability of the heterogeneous products built in their network. In the datacom world this kind of strict testing is not applied though interoperability of products of different vendors is becoming to be as important as for telecom networks with the growing number of datacom product vendors and the growing reliability requirements. The interoperability events use ad hoc test scenarios, and no test results are really available for the potential customers to support their decision which product to buy. This paper presents an application of the conformance testing methodology on IPv6 testing. In section two we present the main features of IPv6. Section 3 summarizes ideas why conformance testing would be useful for the Internet protocols. -

AXIS P85 Series Network Camera User's Manual Notices
USER’S MANUAL AXIS P85 Series AXIS P8513 Network Camera AXIS P8514 Network Camera AXIS P85 Series Network Camera User’s Manual Notices This manual is intended for administrators and users of the AXIS P85 Series, and is applicable for firmware release 5.20 and later. It includes instructions for using and managing the camera on your network. Previous experience of networking will be of use when using this product. Some knowledge of UNIX or Linux-based systems may also be beneficial, for developing shell scripts and applications. Later versions of this document will be posted to the Axis Website, as required. See also the product’s online help, available via the Web-based interface. AXIS P85 Series supports ONVIF v1.01. For more information about ONVIF go to www.onvif.org For more information about enabling ONVIF go to the Developers page at www.axis.com Liability Every care has been taken in the preparation of this manual. Please inform your local Axis office of any inaccuracies or omissions. Axis Communications AB cannot be held responsible for any technical or typographical errors and reserves the right to make changes to the product and manuals without prior notice. Axis Communications AB makes no warranty of any kind with regard to the material contained within this document, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. Axis Communications AB shall not be liable nor responsible for incidental or consequential damages in connection with the furnishing, performance or use of this material. Intellectual Property Rights Axis AB has intellectual property rights relating to technology embodied in the product described in this document. -

AXIS P1344-E User Manual
USER MANUAL AXIS P1344-E Network Camera About this document This manual is intended for administrators and users of the AXIS P1344-E Network Camera, and is applicable to firmware 5.40 and later. It includes instructions for using and managing the product on your network. Previous experience of networking will be of use when using this product. Some knowledge of UNIX or Linux-based systems may also be beneficial, for developing shell scripts and applications. Laterversionsofthisdocumentwill be posted to the Axis website, as required. See also the product’s online help, available via the web-based interface. Liability Every care has been taken in the preparation of this manual. Please inform your local Axis office of any inaccuracies or omissions. Axis Communications AB cannot be held responsible for any technical or typographical errors and reserves the right to make changes to the product and manuals without prior notice. Axis Communications AB makes no warranty of any kind with regard to the material contained within this document, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. Axis Communications AB shall not be liable nor responsible for incidental or consequential damages in connection with the furnishing, performance or use of this material. Intellectual Property Rights Axis AB has intellectual property rights relating to technology embodied in the product described in this document. In particular, and without limitation, these intellectual property rights may include one or more of the patents listed at http://www.axis.com/patent.htm and one or more additional patents or pending patent applications in the US and other countries. -

Ipsec Part I: AH and ESP
IPSec Part I: AH and ESP • Readings – Sections 16.0, 16.1, 16.2, 16.5, 16.12 – Chapter 17 1 Internet Security Protocols • IPSec and SSL User SSL application • IPSec lives at the network layer transport OS IPSec network • SSL lives between link NIC application and transport layers physical 2 SSL vs. IPSec • SSL/TLS – Lives at socket layer (part of user space) – Has encryption, integrity, authentication, etc. – Has a simpler specification • IPSec – Lives at the network layer (part of the OS) – Has encryption, integrity, authentication, etc. – Is overly complex (including serious flaws) SSL vs. IPSec • IPSec implementation – Requires changes to OS, but no changes to applications • SSL implementation – Requires changes to applications, but no changes to OS • SSL built into Web application early on (Netscape) • IPSec used in VPN applications (secure tunnel) • Reluctance to retrofit applications for SSL • Reluctance to use IPSec due to complexity and interoperability issues • Result? Internet less secure than it should be! 4 IPSec and Complexity • IPSec is a complex protocol • Over-engineered – Lots of generally useless extra features • Flawed – Some serious security flaws • Interoperability is serious challenge – Defeats the purpose of having a standard! • Complex 5 What is IPSec? • Protocols and mechanisms to – support security at the network layer (IP layer) • Implemented on end hosts and gateways • Security Policies and SPD (security policy database) – Rules to decide if an IP packet (datagram) needs to be processed and how • Security Association -

IEEE Standards Update
IEEE Standards Update Silvana Rodrigues, IDT ([email protected]) Presentation to ITSF-09, Rome, November 3 to 5, 2009 ©2009 Integrated Device Technology, Inc. Agenda ● IEEE-802.1AS, "Standard for Local and Metropolitan Area Networks - Timing and Synchronization for Time-Sensitive Applications in Bridged Local Area Networks" ● P802.3bf, “Ethernet Support for the IEEE P802.1AS Time Synchronization Protocol Study Group” ● IEEE P802.3az, “Energy-efficient Ethernet Task Force” ● IEEE-1588TM, “IEEE Standard for a Precision Clock Synchronization Protocol for Networked Measurement and Control Systems” IEEE 1588TM is a trademark of its respective owner www.IDT.com PAGE 2 IEEE-802.1AS ● Specifies the protocol and procedures used to ensure that the synchronization requirements are met for time sensitive applications ● Audio and video application across Bridged and Virtual Bridged Local Area Networks consisting of LAN media (e.g. used for Digital Home Media distribution) ● IEEE 802.1AS is based on IEEE 1588v2, and includes a Precision Time Protocol (PTP) profile ● Bridge acts as a boundary clock ● End station acts as ordinary clock ● Synchronization is transported over a maximum of 7 hops (1 LAN = 1 Hop) based on expected applications ● Status ● PAR approved May 25th, 2006 ● Task Group ballot ● Planned to be finished in 2009 www.IDT.com PAGE 3 P802.3bf ● DRAFT Objective ● “Provide an accurate indication of the transmission and reception initiation times of certain packets as required to support IEEE P802.1AS” ● The main objective is to add -
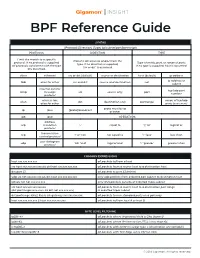
BPF Reference Guide
BPF Reference Guide SYNTAX [Protocol] [Direction] [Type] {ip/subnet/port/portrange} PROTOCOL DIRECTION TYPE Limit the match to a specific Transfer direction to and/or from the protocol. If no protocol is supplied, Type of entity, port, or range of ports. type. If no direction is supplied, all protocols consistent with the type If no type is supplied, host is assumed. ‘src or dst’ is assumed. are assumed. ether ethernet src or dst (default) source or destination host (default) ip address ip address or fddi alias for ether src and dst source and destination net subnet internet control tcp/udp port icmp message src source only port number protocol wireless lan; range of tcp/udp wlan dst destination only portrange alias for ether ports (xxxx-xxxx) proto must be ip ip ipv4 [proto] broadcast or ether ip6 ipv6 OPERATORS address arp resolution ‘=’ equal to ‘||’ ‘or’ logical or protocol transmission tcp ‘!’ or ‘not’ not equal to ‘<’ ‘less’ less than control protocol user datagram udp ’&&’ ‘and’ logical and ‘>’ ‘greater’ greater than protocol COMMON EXPRESSIONS host xxx.xxx.xxx.xxx all packets to/from a host src host xxx.xxx.xxx.xxx && dst host xxx.xxx.xxx.xxx all packets from a source host to a destination host dst port 23 all packets to port 23 (telnet) udp src net xxx.xxx.xxx && dst host xxx.xxx.xxx.xxx only udp packets from a dotted pair subnet to destination host ip6 && not net xxx.xxx.xxx only IPv6 packets outside of a dotted triple subnet src host xxx.xxx.xxx.xxx && all packets from a source host to a destination port range (dst portrange -

Dynamics of the IP Time to Live Field in Internet Traffic Flows
Dynamics of the IP Time To Live Field in Internet Traffic Flows Sebastian Zander, Grenville Armitage, Philip Branch Centre for Advanced Internet Architectures, Technical Report 070529A Swinburne University of Technology Melbourne, Australia [email protected], [email protected], [email protected] Abstract—The Time To Live (TTL) field present in the same IP addresses, ports, and protocol). The motivation IP protocol header is used to limit the lifetime of packets for investigating this is twofold. Firstly, for passively in the network. Previous research has measured TTL for studying IP path changes based on existing traffic in studying path lengths and dynamics in IP networks, and the network or captured traffic traces (instead of active for detecting route changes. How the TTL varies over sampling paths as it was done previously) one needs short timescales of subsequent packets of traffic flows has not yet been analysed. Such knowledge is needed to understand the relation between TTL changes and for passively detecting route changes based on existing path changes. If TTL changes are not only caused by traffic in the network or traffic traces, and for designing path changes one cannot simply infer path changes from mechanisms that modulate the TTL field such as IP TTL changes and needs to differentiate TTL changes. traceback techniques and covert channels. In this paper we Secondly, this research provides valuable information analyse small time scale TTL variation in Internet traffic for people developing techniques that modulate the TTL flows based on a number of packet traces captured at field, such as IP traceback techniques [9] or covert different locations in the Internet. -

Covert Channels in the IP Time to Live Field
Covert Channels in the IP Time To Live Field Sebastian Zander, Grenville Armitage, Philip Branch Centre for Advanced Internet Architectures (CAIA) Swinburne University of Technology Melbourne Australia {szander, garmitage, pbranch}@swin.edu.au Abstract— Covert channels are used for the secret transfer tion would not prevent adversaries to detect communica- of information. Unlike encryption, which only protects the tion patterns, which is often sufficient to detect the onset information from unauthorised observers, covert channels aim of criminal activity, discover organisational structures or to hide the very existence of the communication. The sheer amount of data and vast number of different network protocols obtain police warrants. in the Internet makes it an ideal high-capacity vehicle for covert • Hackers that have compromised computer systems usu- communication. Covert channels pose a serious security threat ally either ex-filtrate data or use the systems for malicious as criminals can use them to hide their communication activities. purposes (such as launching Denial of Service attacks). In this paper we present a novel covert channel inside the IP The generated network traffic – if not covert – would alert header’s Time To Live (TTL) field. The sender manipulates the TTLs of subsequent packets transmitting covert information to system administrators, which then would also discover the receiver. Since network elements along the path also modify the compromised systems. the TTL, the capacity and stealth of this channel depend on the • Recent attempts by some governments to limit the free- “natural” TTL variation. We analyse this variation in multiple dom of speech and civilian use of (strong) cryptography traffic traces and propose an encoding scheme, which makes the have lead to proposals for utilising covert channels to TTL covert channel look similar to “natural” variation. -

Site-To-Site and Host-To-Site VPN with Ipsec in P4-Based SDN Frederik Hauser, Marco Häberle, Mark Schmidt, Michael Menth
P4-IPsec: Site-to-Site and Host-to-Site VPN with IPsec in P4-Based SDN Frederik Hauser, Marco Häberle, Mark Schmidt, Michael Menth Abstract—In this work, we present P4-IPsec, a concept to simplify IPsec operation. However, the possibilities for for IPsec in software-defined networks (SDN) using P4 pro- IPsec deployment in SDN were limited. Typical SDN switches grammable data planes. The prototype implementation features have a fixed-function data plane that does not provide support ESP in tunnel mode and supports different cipher suites. P4- capable switches are programmed to serve as IPsec tunnel for IPsec. As a result, IPsec data plane processing needs to endpoints. We also provide a client agent to configure tunnel be moved to an additional software-based packet processing endpoints on Linux hosts so that site-to-site and host-to-site function (PPF). Besides being an additional component, this application scenarios can be supported which are the base for adds latency as traffic needs to be forwarded back and forth. virtual private networks (VPNs). While traditional VPNs require Programmable data planes as offered by P4 are a game complex key exchange protocols like IKE to set up and renew tunnel endpoints, P4-IPsec benefits from an SDN controller to changer. Data plane behavior can be described in a high- accomplish these tasks. One goal of this experimental work level programming language. Those network programs can is to investigate how well P4-IPsec can be implemented on be executed by software or hardware devices. For IPsec this existing P4 switches. We present a prototype for the BMv2 means that instead of shifting IPsec functionality to PPFs, P4 software switch, evaluate its performance, and publish its functions such as IPsec can be implemented directly on the source code on GitHub [1].