Ipv6 Feature Overview and Configuration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IP Datagram ICMP Message Format ICMP Message Types
ICMP Internet Control Message Protocol ICMP is a protocol used for exchanging control messages. CSCE 515: Two main categories Query message Computer Network Error message Programming Usage of an ICMP message is determined by type and code fields ------ IP, Ping, Traceroute ICMP uses IP to deliver messages. Wenyuan Xu ICMP messages are usually generated and processed by the IP software, not the user process. Department of Computer Science and Engineering University of South Carolina IP header ICMP Message 20 bytes CSCE515 – Computer Network Programming IP Datagram ICMP Message Format 1 byte 1 byte 1 byte 1 byte VERS HL Service Total Length Datagram ID FLAG Fragment Offset 0781516 31 TTL Protocol Header Checksum type code checksum Source Address Destination Address payload Options (if any) Data CSCE515 – Computer Network Programming CSCE515 – Computer Network Programming ICMP Message Types ICMP Address Mask Request and Reply intended for a diskless system to obtain its subnet mask. Echo Request Id and seq can be any values, and these values are Echo Response returned in the reply. Destination Unreachable Match replies with request Redirect 0781516 31 Time Exceeded type(17 or 18) code(0) checksum there are more ... identifier sequence number subnet mask CSCE515 – Computer Network Programming CSCE515 – Computer Network Programming ping Program ICMP Echo Request and Reply Available at /usr/sbin/ping Test whether another host is reachable Send ICMP echo_request to a network host -n option to set number of echo request to send -

Networking: Network Layer
CS 4410 Operating Systems Networking: Network Layer Summer 2013 Cornell University 1 Today ● How packages are exchanged in a WAN? ● Network Layer ● IP ● Naming ● Subnetwork ● Forwarding ● Routing Algorithms 2 Protocol Stack Computer A Computer B Message M Application Application Segment Ht M Transport Transport Datagram Hn Ht M Network Network Frame Hl Hn Ht M Link Link Physical Physical 3 WAN ● Usually, thousands of computers need to be interconnected. ● The capabilities that LANs offer cannot support larger networks. ● We need more services than the Link Layer offers. ● Why? ● Clever Naming ● Efficient forwarding/routing of messages. 4 Network Layer ● Mission: Transfer messages from the source-computer to the destination- computer. ● Attention: this is different from the mission of the Link Layer. ● Services: ● Forwarding / Routing ● Guaranteed delivery, bandwidth, etc ● Security ● Not all the protocols support these services. ● The Network Layer protocol depends on the kind of network we want to built: ● Virtual-circuit networks ● Datagram networks ● Necessary network device: ● Router: It knows where to forward the message. 5 Network Layer ● Virtual-circuit networks ● 3 phases ● Establish a virtual circuit. – The Network Layer finds the path from the source to the destination. – Reserve resources for the virtual circuit. ● Transfer data – Packets pass through the virtual circuit. ● Destroy virtual circuit. – Release resources. ● Disadvantages? ● Datagram networks ● Every packet has the destination address and it is routed independently in the network. ● The router uses the destination address to forward the packet towards 6 the destination-computer. IP ● Network Layer Protocol for the Internet: ● Internet Protocol ● For Datagram networks. ● IPv4, IPv6 ● Datagram structure: Version Header Type of Length Length service Identification Flags Fragment Offset Time to live Protocol Header Checksum Source IP Address (32-bit) Destination IP Address Options Data 7 Naming ● All the computers in the Internet have one or more IP addresses. -

Solutions to Chapter 2
CS413 Computer Networks ASN 4 Solutions Solutions to Assignment #4 3. What difference does it make to the network layer if the underlying data link layer provides a connection-oriented service versus a connectionless service? [4 marks] Solution: If the data link layer provides a connection-oriented service to the network layer, then the network layer must precede all transfer of information with a connection setup procedure (2). If the connection-oriented service includes assurances that frames of information are transferred correctly and in sequence by the data link layer, the network layer can then assume that the packets it sends to its neighbor traverse an error-free pipe. On the other hand, if the data link layer is connectionless, then each frame is sent independently through the data link, probably in unconfirmed manner (without acknowledgments or retransmissions). In this case the network layer cannot make assumptions about the sequencing or correctness of the packets it exchanges with its neighbors (2). The Ethernet local area network provides an example of connectionless transfer of data link frames. The transfer of frames using "Type 2" service in Logical Link Control (discussed in Chapter 6) provides a connection-oriented data link control example. 4. Suppose transmission channels become virtually error-free. Is the data link layer still needed? [2 marks – 1 for the answer and 1 for explanation] Solution: The data link layer is still needed(1) for framing the data and for flow control over the transmission channel. In a multiple access medium such as a LAN, the data link layer is required to coordinate access to the shared medium among the multiple users (1). -

Data Link Layer
Data link layer Goals: ❒ Principles behind data link layer services ❍ Error detection, correction ❍ Sharing a broadcast channel: Multiple access ❍ Link layer addressing ❍ Reliable data transfer, flow control: Done! ❒ Example link layer technology: Ethernet Link layer services Framing and link access ❍ Encapsulate datagram: Frame adds header, trailer ❍ Channel access – if shared medium ❍ Frame headers use ‘physical addresses’ = “MAC” to identify source and destination • Different from IP address! Reliable delivery (between adjacent nodes) ❍ Seldom used on low bit error links (fiber optic, co-axial cable and some twisted pairs) ❍ Sometimes used on high error rate links (e.g., wireless links) Link layer services (2.) Flow Control ❍ Pacing between sending and receiving nodes Error Detection ❍ Errors are caused by signal attenuation and noise. ❍ Receiver detects presence of errors signals sender for retrans. or drops frame Error Correction ❍ Receiver identifies and corrects bit error(s) without resorting to retransmission Half-duplex and full-duplex ❍ With half duplex, nodes at both ends of link can transmit, but not at same time Multiple access links / protocols Two types of “links”: ❒ Point-to-point ❍ PPP for dial-up access ❍ Point-to-point link between Ethernet switch and host ❒ Broadcast (shared wire or medium) ❍ Traditional Ethernet ❍ Upstream HFC ❍ 802.11 wireless LAN MAC protocols: Three broad classes ❒ Channel Partitioning ❍ Divide channel into smaller “pieces” (time slots, frequency) ❍ Allocate piece to node for exclusive use ❒ Random -

Internet Routing Over Large Public Data Networks Using Shortcuts
Internet Routing over Large Public Data Networks using Shortcuts Paul F, Tsuchiya, Bellcore, [email protected] When a system (a router or host) needs to send an internet packet, it must determine the destination subnetwork Abstract address to send the packet to. (IP systems traditionally do this as a two-step process. First the 1P address of the With the emergence of large switched public data networks receiving system is determined. Then the subnetwork that are well-suited to connectionless internets, for instance address associated with the 1P address is derived.) On SMDS, it is possible that larger and larger numbers of broadcast LANs this has proven to be relatively simple. internet users will get their connectivity from large public This is because 1) broadcast LANs have a small number of data networks whose native protocols are not the same as attached systems (hundreds), and 2) broadcast LANs have the user’s internet protocol. This results in a routing an inexpensive multicast, thus making “searching” for problem that has not yet been addressed. That is, large systems on a LAN inexpensive and easy. numbers of routers (potentially tens of thousands) must be able to find direct routes to each other in a robust and On very large general topology subnetworks (called here efficient way. This paper describes a solution to the public data networks, or PDNs2), however, determining problem, called shortcut routing, that incorporates 1) a “next hop” subnetwork (or PDN) addresses is not sparse graph of logical connectivity between routers, 2) necessarily simple. There may be (eventually) tens of hierarchical addressing among the public data network thousands of systems attached to a PDN, making it subscribers, and 3) the use of “entry router” information in inefficient to distribute up-to-date information about all packets to allow routers to find one hop “shortcuts” across systems to all systems. -

Transport Layer Chapter 6
Transport Layer Chapter 6 • Transport Service • Elements of Transport Protocols • Congestion Control • Internet Protocols – UDP • Internet Protocols – TCP • Performance Issues • Delay-Tolerant Networking Revised: August 2011 CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 The Transport Layer Responsible for delivering data across networks with the desired Application reliability or quality Transport Network Link Physical CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Transport Service • Services Provided to the Upper Layer » • Transport Service Primitives » • Berkeley Sockets » • Socket Example: Internet File Server » CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Services Provided to the Upper Layers (1) Transport layer adds reliability to the network layer • Offers connectionless (e.g., UDP) and connection- oriented (e.g, TCP) service to applications CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Services Provided to the Upper Layers (2) Transport layer sends segments in packets (in frames) Segment Segment CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Transport Service Primitives (1) Primitives that applications might call to transport data for a simple connection-oriented service: • Client calls CONNECT, SEND, RECEIVE, DISCONNECT • Server calls LISTEN, RECEIVE, SEND, DISCONNECT Segment CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice -

Aerohive Configuration Guide: RADIUS Authentication | 2
Aerohive Configuration Guide RADIUS Authentication Aerohive Configuration Guide: RADIUS Authentication | 2 Copyright © 2012 Aerohive Networks, Inc. All rights reserved Aerohive Networks, Inc. 330 Gibraltar Drive Sunnyvale, CA 94089 P/N 330068-03, Rev. A To learn more about Aerohive products visit www.aerohive.com/techdocs Aerohive Networks, Inc. Aerohive Configuration Guide: RADIUS Authentication | 3 Contents Contents ...................................................................................................................................................................................................................... 3 IEEE 802.1X Primer................................................................................................................................................................................................... 4 Example 1: Single Site Authentication .................................................................................................................................................................... 6 Step 1: Configuring the Network Policy ..............................................................................................................................................................7 Step 2: Configuring the Interface and User Access .........................................................................................................................................7 Step 3: Uploading the Configuration and Certificates .................................................................................................................................... -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
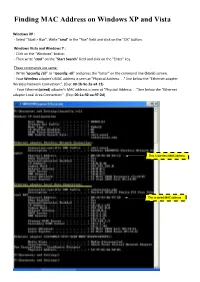
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

Domain Name System System Work?
What is the DNS? - how it works Isaac Maposa | Dev Anand Teelucksingh | Beran Gillen Community Onboarding Program | 11 March 2017 Agenda 1 2 3 What is the Domain Structure of the How does the Name System? Domain Name Domain Name System System Work? 4 5 6 Who makes the Stakeholders in the Engage with ICANN Domain Name Domain Name ??? System Work? System. | 2 What is the Domain Name System (DNS)? The Internet, what is it..? ● The Internet is a network of networks that interconnects devices to exchange information. ● In order to “talk” to each other, all of these devices must have a unique numerical address called an Internet Protocol address or IP Address. An example of an IP address is 94.127.53.132 ● When you visit a website from your browser, you are requesting the website from your device’s IP address to the web server’s IP address. ● However, you don’t type in the ip address of the web server, rather the domain name of for example www.google.com ● In so doing, you have queried the DNS. ● So what is this DNS???? | 4 What is the Domain Name System? ● The Domain Name System or DNS overcomes this problem of remembering IP addresses by mapping domain names to IP addresses. ● While this sounds like a phone book, it is not a centralised database. ● The DNS is a distributed database across a hierarchy of networks of servers and provide ways for devices and software (like browsers and email) to query the DNS to get an IP address. ● Domain names must be unique. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet.