Preliminary Assessment: Unidentified Aerial Phenomena 25 June 2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

KNOWLEDGE ACCORDING to IDEALISM Idealism As a Philosophy
KNOWLEDGE ACCORDING TO IDEALISM Idealism as a philosophy had its greatest impact during the nineteenth century. It is a philosophical approach that has as its central tenet that ideas are the only true reality, the only thing worth knowing. In a search for truth, beauty, and justice that is enduring and everlasting; the focus is on conscious reasoning in the mind. The main tenant of idealism is that ideas and knowledge are the truest reality. Many things in the world change, but ideas and knowledge are enduring. Idealism was often referred to as “idea-ism”. Idealists believe that ideas can change lives. The most important part of a person is the mind. It is to be nourished and developed. Etymologically Its origin is: from Greek idea “form, shape” from weid- also the origin of the “his” in his-tor “wise, learned” underlying English “history.” In Latin this root became videre “to see” and related words. It is the same root in Sanskrit veda “knowledge as in the Rig-Veda. The stem entered Germanic as witan “know,” seen in Modern German wissen “to know” and in English “wisdom” and “twit,” a shortened form of Middle English atwite derived from æt “at” +witen “reproach.” In short Idealism is a philosophical position which adheres to the view that nothing exists except as it is an idea in the mind of man or the mind of God. The idealist believes that the universe has intelligence and a will; that all material things are explainable in terms of a mind standing behind them. PHILOSOPHICAL RATIONALE OF IDEALISM a) The Universe (Ontology or Metaphysics) To the idealist, the nature of the universe is mind; it is an idea. -

Is AI Intelligent, Really? Bruce D
Seattle aP cific nivU ersity Digital Commons @ SPU SPU Works Summer August 23rd, 2019 Is AI intelligent, really? Bruce D. Baker Seattle Pacific nU iversity Follow this and additional works at: https://digitalcommons.spu.edu/works Part of the Artificial Intelligence and Robotics Commons, Comparative Methodologies and Theories Commons, Epistemology Commons, Philosophy of Science Commons, and the Practical Theology Commons Recommended Citation Baker, Bruce D., "Is AI intelligent, really?" (2019). SPU Works. 140. https://digitalcommons.spu.edu/works/140 This Article is brought to you for free and open access by Digital Commons @ SPU. It has been accepted for inclusion in SPU Works by an authorized administrator of Digital Commons @ SPU. Bruce Baker August 23, 2019 Is AI intelligent, really? Good question. On the surface, it seems simple enough. Assign any standard you like as a demonstration of intelligence, and then ask whether you could (theoretically) set up an AI to perform it. Sure, it seems common sense that given sufficiently advanced technology you could set up a computer or a robot to do just about anything that you could define as being doable. But what does this prove? Have you proven the AI is really intelligent? Or have you merely shown that there exists a solution to your pre- determined puzzle? Hmmm. This is why AI futurist Max Tegmark emphasizes the difference between narrow (machine-like) and broad (human-like) intelligence.1 And so the question remains: Can the AI be intelligent, really, in the same broad way its creator is? Why is this question so intractable? Because intelligence is not a monolithic property. -

Artificial Intelligence and National Security
Artificial Intelligence and National Security Artificial intelligence will have immense implications for national and international security, and AI’s potential applications for defense and intelligence have been identified by the federal government as a major priority. There are, however, significant bureaucratic and technical challenges to the adoption and scaling of AI across U.S. defense and intelligence organizations. Moreover, other nations—particularly China and Russia—are also investing in military AI applications. As the strategic competition intensifies, the pressure to deploy untested and poorly understood systems to gain competitive advantage could lead to accidents, failures, and unintended escalation. The Bipartisan Policy Center and Georgetown University’s Center for Security and Emerging Technology (CSET), in consultation with Reps. Robin Kelly (D-IL) and Will Hurd (R-TX), have worked with government officials, industry representatives, civil society advocates, and academics to better understand the major AI-related national and economic security issues the country faces. This paper hopes to shed more clarity on these challenges and provide actionable policy recommendations, to help guide a U.S. national strategy for AI. BPC’s effort is primarily designed to complement the work done by the Obama and Trump administrations, including President Barack Obama’s 2016 The National Artificial Intelligence Research and Development Strategic Plan,i President Donald Trump’s Executive Order 13859, announcing the American AI Initiative,ii and the Office of Management and Budget’s subsequentGuidance for Regulation of Artificial Intelligence Applications.iii The effort is also designed to further June 2020 advance work done by Kelly and Hurd in their 2018 Committee on Oversight 1 and Government Reform (Information Technology Subcommittee) white paper Rise of the Machines: Artificial Intelligence and its Growing Impact on U.S. -

Theory of Mind As Inverse Reinforcement Learning. Current
Available online at www.sciencedirect.com ScienceDirect Theory of mind as inverse reinforcement learning 1,2 Julian Jara-Ettinger We review the idea that Theory of Mind—our ability to reason think or want based on how they behave. Research in about other people’s mental states—can be formalized as cognitive science suggests that we infer mental states by inverse reinforcement learning. Under this framework, thinking of other people as utility maximizers: constantly expectations about how mental states produce behavior are acting to maximize the rewards they obtain while mini- captured in a reinforcement learning (RL) model. Predicting mizing the costs that they incur [3–5]. Using this assump- other people’s actions is achieved by simulating a RL model tion, even children can infer other people’s preferences with the hypothesized beliefs and desires, while mental-state [6,7], knowledge [8,9], and moral standing [10–12]. inference is achieved by inverting this model. Although many advances in inverse reinforcement learning (IRL) did not have Theory of mind as inverse reinforcement human Theory of Mind in mind, here we focus on what they learning reveal when conceptualized as cognitive theories. We discuss Computationally, our intuitions about how other minds landmark successes of IRL, and key challenges in building work can be formalized using frameworks developed in a human-like Theory of Mind. classical area of AI: model-based reinforcement learning 1 Addresses (hereafter reinforcement learning or RL) . RL problems 1 Department of Psychology, Yale University, New Haven, CT, United focus on how to combine a world model with a reward States function to produce a sequence of actions, called a policy, 2 Department of Computer Science, Yale University, New Haven, CT, that maximizes agents’ rewards while minimizing their United States costs. -

Artificial Intelligence in the Context of Human Consciousness
Running head: AI IN THE CONTEXT OF HUMAN CONSCIOUSNESS 1 Artificial Intelligence in the Context of Human Consciousness Hannah DeFries A Senior Thesis submitted in partial fulfillment of the requirements for graduation in the Honors Program Liberty University Spring 2019 AI IN THE CONTEXT OF HUMAN CONSCIOUSNESS 2 Acceptance of Senior Honors Thesis This Senior Honors Thesis is accepted in partial fulfillment of the requirements for graduation from the Honors Program of Liberty University. ______________________________ Kyung K. Bae, Ph.D. Thesis Chair ______________________________ Jung-Uk Lim, Ph.D. Committee Member ______________________________ Mark Harris, Ph.D. Committee Member ______________________________ James H. Nutter, D.A. Honors Director ______________________________ Date AI IN THE CONTEXT OF HUMAN CONSCIOUSNESS 3 Abstract Artificial intelligence (AI) can be defined as the ability of a machine to learn and make decisions based on acquired information. AI’s development has incited rampant public speculation regarding the singularity theory: a futuristic phase in which intelligent machines are capable of creating increasingly intelligent systems. Its implications, combined with the close relationship between humanity and their machines, make achieving understanding both natural and artificial intelligence imperative. Researchers are continuing to discover natural processes responsible for essential human skills like decision-making, understanding language, and performing multiple processes simultaneously. Artificial intelligence -
CBEST Threat Intelligence-Led Assessments
Implementation guide CBEST Threat Intelligence-Led Assessments January 2021 CBEST Threat Intelligence-Led Assessments 1 Forward Operational disruption can impact financial stability, threaten the viability of individual firms and financial market infrastructures (FMIs), or cause harm to consumers and other market participants in the financial system. Firms and FMIs need to consider all of these risks when assessing the appropriate levels of resilience within their respective businesses. Dealing with cyber risk is an important element of operational resilience and the CBEST framework is intelligence-led penetration testing which aims to address this risk. CBEST is part of the Bank of England and Prudential Regulation Authority’s (PRA’s) supervisory toolkit to assess the cyber resilience of firms’ important business services. This prioritised and focused assessment allows us and firms to better understand weaknesses and vulnerabilities and take remedial actions, thereby improving the resilience of systemically important firms and by extension, the wider financial system. Continued use of CBEST has confirmed its use as a highly effective regulatory assessment tool, which can now also be conducted on a cross-jurisdictional basis, in collaboration with other international regulators and frameworks. This latest version of the CBEST Implementation Guide builds upon the previous framework and contains improvements learned from the extensive testing which has taken place. In particular, we have analysed and implemented changes with the aim of clarifying CBEST roles and responsibilities as well as regulatory expectations for different CBEST activities. While the underlying intelligence-led penetration testing approach remains the same, we have reviewed and updated the technical guidance for most activities, prepared new templates (eg Penetration Testing Report) and incorporated important references to cross-jurisdictional assessments. -

Defense Primer: National and Defense Intelligence
Updated December 30, 2020 Defense Primer: National and Defense Intelligence The Intelligence Community (IC) is charged with providing Intelligence Program (NIP) budget appropriations, which insight into actual or potential threats to the U.S. homeland, are a consolidation of appropriations for the ODNI; CIA; the American people, and national interests at home and general defense; and national cryptologic, reconnaissance, abroad. It does so through the production of timely and geospatial, and other specialized intelligence programs. The apolitical products and services. Intelligence products and NIP, therefore, provides funding for not only the ODNI, services result from the collection, processing, analysis, and CIA and IC elements of the Departments of Homeland evaluation of information for its significance to national Security, Energy, the Treasury, Justice and State, but also, security at the strategic, operational, and tactical levels. substantially, for the programs and activities of the Consumers of intelligence include the President, National intelligence agencies within the DOD, to include the NSA, Security Council (NSC), designated personnel in executive NGA, DIA, and NRO. branch departments and agencies, the military, Congress, and the law enforcement community. Defense intelligence comprises the intelligence organizations and capabilities of the Joint Staff, the DIA, The IC comprises 17 elements, two of which are combatant command joint intelligence centers, and the independent, and 15 of which are component organizations military services that address strategic, operational or of six separate departments of the federal government. tactical requirements supporting military strategy, planning, Many IC elements and most intelligence funding reside and operations. Defense intelligence provides products and within the Department of Defense (DOD). -

2021 7 Day Working Days Calendar
2021 7 Day Working Days Calendar The Working Day Calendar is used to compute the estimated completion date of a contract. To use the calendar, find the start date of the contract, add the working days to the number of the calendar date (a number from 1 to 1000), and subtract 1, find that calculated number in the calendar and that will be the completion date of the contract Date Number of the Calendar Date Friday, January 1, 2021 133 Saturday, January 2, 2021 134 Sunday, January 3, 2021 135 Monday, January 4, 2021 136 Tuesday, January 5, 2021 137 Wednesday, January 6, 2021 138 Thursday, January 7, 2021 139 Friday, January 8, 2021 140 Saturday, January 9, 2021 141 Sunday, January 10, 2021 142 Monday, January 11, 2021 143 Tuesday, January 12, 2021 144 Wednesday, January 13, 2021 145 Thursday, January 14, 2021 146 Friday, January 15, 2021 147 Saturday, January 16, 2021 148 Sunday, January 17, 2021 149 Monday, January 18, 2021 150 Tuesday, January 19, 2021 151 Wednesday, January 20, 2021 152 Thursday, January 21, 2021 153 Friday, January 22, 2021 154 Saturday, January 23, 2021 155 Sunday, January 24, 2021 156 Monday, January 25, 2021 157 Tuesday, January 26, 2021 158 Wednesday, January 27, 2021 159 Thursday, January 28, 2021 160 Friday, January 29, 2021 161 Saturday, January 30, 2021 162 Sunday, January 31, 2021 163 Monday, February 1, 2021 164 Tuesday, February 2, 2021 165 Wednesday, February 3, 2021 166 Thursday, February 4, 2021 167 Date Number of the Calendar Date Friday, February 5, 2021 168 Saturday, February 6, 2021 169 Sunday, February -

MISSILE DEFENSE Further Collaboration with the Intelligence Community Would Help MDA Keep Pace With
United States Government Accountability Office Report to Congressional Committees December 2019 MISSILE DEFENSE Further Collaboration with the Intelligence Community Would Help MDA Keep Pace with Emerging Threats GAO-20-177 December 2019 MISSILE DEFENSE Further Collaboration with the Intelligence Community Would Help MDA Keep Pace with Highlights of GAO-20-177, a report to Emerging Threats congressional committees Why GAO Did This Study What GAO Found MDA is developing missile defense The Missile Defense Agency (MDA) is experiencing delays getting the threat capabilities to defend the United assessments needed to inform its acquisition decisions. Officials from the States, deployed forces, and regional defense intelligence community—intelligence organizations within the allies from missile attacks. However, Department of Defense (DOD)—told GAO this is because they are currently missile threats continue to emerge, as overextended due to an increased demand for threat assessments from a adversaries continue to improve and recent upsurge in threat missile activity, as well as uncertainties related to their expand their missile capabilities. transition to new threat processes and products. The delays are exacerbated The National Defense Authorization because MDA does not collectively prioritize the various types of threat Act for Fiscal Year 2012 included a assessment requests submitted to the defense intelligence community or provision that GAO annually assess provide resources for unique requests, as other major defense acquisition and report on the extent to which MDA programs are generally required to do. Without timely threat assessments, has achieved its acquisition goals and MDA risks making acquisition decisions for weapon systems using irrelevant objectives, and include any other or outdated threat information, which could result in performance shortfalls. -

The FBI's Counterterrorism Program
U.S. Department of Justice Federal Bureau of Investigation Report to the National Commission on Terrorist Attacks upon the United States: The FBI’s Counterterrorism Program Since September 2001 April 14, 2004 Report to The National Commission on Terrorist Attacks upon the United States The FBI’s Counterterrorism Program Since September 2001 TABLETABLE OF OFCONTENTS CONTENTS I EXECUTIVE SUMMARY....................................................................11 II FBI ORGANIZATIONAL CHART................................................. 3 III TIMELINE OF SIGNIFICANT REFORMS AND INITIATIVES SINCE 9/11/01.......................................................... 4 IV INTRODUCTION......................................................................................66 V PRIORITIZATION....................................................................................77 The New Priorities.........................................................................................77 1 Protect the United States from Terrorist Attack..........................................77 2 Protect the United States Against Foreign Intelligence Operations and Espionage........................................................................................77 3 Protect the United States Against Cyber-based Attacks and High-Technology Crimes..................................................................88 4 Combat Public Corruption at all Levels.......................................................88 5 Protect Civil Rights......................................................................................88 -
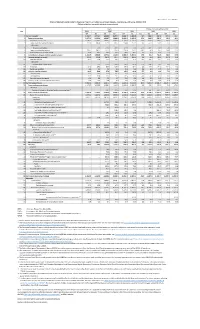
Release Date: June 24, 2021
Release Date: June 24, 2021 Effects of Selected Federal Pandemic Response Programs on Federal Government Receipts, Expenditures, and Saving, 2021Q1 Third (Billions of dollars, seasonally adjusted at annual rates) Levels Change from preceding quarter Line 2019 2020 2021 2020 2021 Q4 Q1 Q2 Q3 Q4 Q1 Q1 Q2 Q3 Q4 Q1 1 Current receipts 3,763.7 3,753.1 3,468.8 3,677.1 3,804.7 3,869.8 -10.7 -284.2 208.3 127.6 65.1 2 Current tax receipts 2,177.1 2,150.0 1,929.7 2,064.0 2,162.3 2,202.3 -27.1 -220.3 134.3 98.2 40.1 3 Personal current taxes 1,740.2 1,756.6 1,600.1 1,685.0 1,745.6 1,758.2 16.3 -156.4 84.9 60.6 12.6 4 Taxes on production and imports 179.2 183.8 131.4 144.7 150.8 159.9 4.6 -52.4 13.3 6.1 9.1 Of which: 5 Aviation tax holiday 1 ... -3.5 -19.4 -19.4 -19.4 0.0 -3.5 -15.9 0.0 0.0 19.4 6 Taxes on corporate income 229.7 180.5 171.5 207.0 236.9 254.1 -49.2 -9.0 35.5 29.8 17.3 7 Taxes from the rest of the world 27.9 29.1 26.6 27.3 29.0 30.1 1.2 -2.5 0.7 1.8 1.1 8 Contributions for government social insurance 1,416.9 1,436.4 1,374.2 1,426.6 1,466.6 1,504.4 19.5 -62.2 52.4 40.0 37.8 9 Income receipts on assets 111.2 112.8 107.4 127.7 110.4 103.5 1.6 -5.4 20.2 -17.3 -6.9 10 Interest receipts 40.1 35.8 16.6 16.1 16.2 16.4 -4.4 -19.2 -0.5 0.1 0.2 Of which: 11 Student loan forbearance 2 .. -

Cyber Intelligence Tradecraft Report the State of Cyber Intelligence Practices in the United States Copyright 2019 Carnegie Mellon University
Cyber Intelligence Tradecraft Report The State of Cyber Intelligence Practices in the United States Copyright 2019 Carnegie Mellon University. All Rights Reserved. This material is based upon work funded and supported by the Department of Defense under Contract No. FA8702-15-D-0002 with Carnegie Mellon University for the operation of the Software Engineering Institute, a federally funded research and development center. The view, opinions, and/or findings contained in this material are those of the author(s) and should not be construed as an official Government position, policy, or decision, unless designated by other documentation. References herein to any specific commercial product, process, or service by trade name, trade mark, manufacturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by Carnegie Mellon University or its Software Engineering Institute. NO WARRANTY. THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN “AS-IS” BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. CARNEGIE MELLON UNIVERSITY DOES NOT MAKE ANY WARRANTY OF ANY KIND WITH RESPECT TO FREEDOM FROM PATENT, TRADEMARK, OR COPYRIGHT INFRINGEMENT. [DISTRIBUTION STATEMENT A] This material has been approved for public release and unlimited distribution. Please see Copyright notice for non-US Government use and distribution. Internal use:* Permission to reproduce this material and to prepare derivative works from this material for internal use is granted, provided the copyright and “No Warranty” statements are included with all reproductions and derivative works.