View the Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Illustrated Tutorial: Creating a Bootable USB Flash Drive for Windows XP
Illustrated tutorial: Creating a bootable Version 1.0 February 15, 2007 USB flash drive for Windows XP By Greg Shultz The ability to boot Windows XP from a USB Flash Drive (UFD) offers endless possibilities. For example, you might make an easy-to-use troubleshooting tool for booting and analyzing seemingly dead PCs. Or you could transport your favorite applications back and forth from home to work without having to install them on both PCs. However, before you can create a bootable UFD, you must clear a few hurdles. You saw that one coming didn’t you? The first hurdle is having a PC in which the BIOS will allow you to configure the USB port to act as a bootable device. The second hurdle is having a UFD that that will work as a bootable device and that’s large enough and fast enough to boot an operating system such as Windows XP. The third hurdle is finding a way to condense and install Windows XP on a UFD. If you have a PC that was manufactured in the last several years, chances are that its BIOS will allow you to configure the USB port to act as a bootable device. If you have a good qual- ity UFD that’s at least 512 KB and that was manufactured in the last couple of years, you’ve probably cleared the second hurdle. And once you’ve cleared those first two hur- dles, the third one is a piece of cake. All you have to do is download and run some free soft- ware to create the bootable UFD. -

When Using the Wireless Function with a Windows Vista Computer 3. Computer Network Settings 1. Projector Settings 2. Computer IP
2. Computer IP address settings When using the wireless function with a Windows Vista computer 1 Select [Start] → [Network]. “Wireless Manager mobile edition 3.0”, which is stored on the CD-ROM that is provided, does not work when using the wireless function with a Windows Vista computer. “Wireless Manager mobile edition 3.0a” is a version that is compatible with Windows Vista. Use this version by downloading and installing it from the URL below. However, please be aware it will still not be possible to use the functions described below. URL: http://panasonic.co.jp/pavc/global/projector/download/ 2 Select [Network and Sharing Center]. Functions that cannot be used: • Easy wireless set up (automatic set up of the wireless network) • Sound transmission • Wireless prompter (secondary display transmission) • Selective area transmission • Check with your system administrator before performing the network settings with the procedures below. Select [Manage network connections]. If network settings have already been made for using the computer in a wireless 3 environment for a different purpose, and after changing the settings as described in these instructions you want to go back to using the computer for the original purpose, then remember to return the network settings to their previous condition. • See “Wireless Function Edition”, the Operating Instructions in the provided CD-ROM, for details on the projector network settings and the wireless function. 1. Projector settings 4 Right click the mouse and open the Select [MENU] → [WIRELESS] → [NETWORK], and change to [USER1]. Wireless Network Connection Properties. Default settings of USER1 DHCP OFF IP ADDRESS 192.168.10.100 SUBNETMASK 255.255.255.0 SSID Panasonic Projector MODE ADHOC Enter [TCP/IPv4] as the setting and press 5 [OK]. -

The Downadup Codex a Comprehensive Guide to the Threat’S Mechanics
Security Response The Downadup Codex A comprehensive guide to the threat’s mechanics. Edition 2.0 Introduction Contents Introduction.............................................................1 Since its appearance in late-2008, the Downadup worm has become Editor’s Note............................................................5 one of the most wide-spread threats to hit the Internet for a number of Increase in exploit attempts against MS08-067.....6 years. A complex piece of malicious code, this threat was able to jump W32.Downadup infection statistics.........................8 certain network hurdles, hide in the shadows of network traffic, and New variants of W32.Downadup.B find new ways to propagate.........................................10 defend itself against attack with a deftness not often seen in today’s W32.Downadup and W32.Downadup.B threat landscape. Yet it contained few previously unseen features. What statistics................................................................12 set it apart was the sheer number of tricks it held up its sleeve. Peer-to-peer payload distribution...........................15 Geo-location, fingerprinting, and piracy...............17 It all started in late-October of 2008, we began to receive reports of A lock with no key..................................................19 Small improvements yield big returns..................21 targeted attacks taking advantage of an as-yet unknown vulnerability Attempts at smart network scanning...................23 in Window’s remote procedure call (RPC) service. Microsoft quickly Playing with Universal Plug and Play...................24 released an out-of-band security patch (MS08-067), going so far as to Locking itself out.................................................27 classify the update as “critical” for some operating systems—the high- A new Downadup variant?......................................29 Advanced crypto protection.................................30 est designation for a Microsoft Security Bulletin. -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Security Assessment Security Policy Assessment
Security Assessment Security Policy Assessment Prepared for: Jonathan Doe Prepared by: Austin Archer 3/23/2018 CONFIDENTIALITY NOTE: The information contained in this report is for the exclusive use of the client specified above and may contain confidential, privileged and non-disclosable information. If the recipient of this report is not the client or addressee, such recipient is strictly prohibited from reading, photocopying, distributing or otherwise using this report or its contents in any way. Scan Date: 4/1/2014 Security Policy Assessment SECURITY ASSESSMENT Table of Contents 1 - Summary 1.1 - Sampled Systems 2 - Local Security Settings (Sampled Systems) 2.1 - Account Policies 2.1.1 - Password Policy 2.1.2 - Account Lockout Policy 2.2 - Local Policies 2.2.1 - Audit Policy 2.2.2 - User Rights Assignment 2.2.3 - Security Options PROPRIETARY & CONFIDENTIAL Page 2 of 14 Security Policy Assessment SECURITY ASSESSMENT 1 - Summary 1.1 - Sampled Systems IP Addresses Computer Name Operating System 10.0.7.28 tandem Windows 7 Enterprise 172.20.1.3, 10.0.1.3 DC01 Windows Server 2012 Standard PROPRIETARY & CONFIDENTIAL Page 3 of 14 Security Policy Assessment SECURITY ASSESSMENT 2 - Local Security Settings (Sampled Systems) 2.1 - Account Policies 2.1.1 - Password Policy Policy Setting Computers Enforce password history 0 passwords remembered TANDEM 24 passwords remembered DC01 Maximum password age 42 days All Sampled Minimum password age 1 days All Sampled Minimum password length 7 characters All Sampled Password must meet complexity requirements -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Windows XP History and Versions
Lecture 23: Windows XP History and Versions n Mid-80ies Microsoft and IBM cooperated to develop OS/2 n Windows XP is produced by Microsoft Co. n 1988 - Microsoft started to develop its own new technology (NT) OS n XP is multi-user, multi-process, preemptive multitasking OS, 30M lines of source code capable of running OS/2, Windows and Unix apps. Hired Dave Cutler - architect of DEC VAX/VMS to head the design n It is developed to support multiple platforms and targeted towards enterprise workstations and server market as well as n NT v. 3.1 first released commercially July 1993 desktops n NT v 4.0 adopted Windows 95 user interface, graphics code moved into kernel to improve performance n In today’s lecture n 2000 – improved networking and laptop support, support for plug-and- u XP’s predecessors, the history of XP design, XP versions play devices, support for more processors (up to 8) and memory, u design principles becomes true multi-user through terminal server u components n XP (released Oct 2001) – update for 2000 replacement for 95/98 F hardware abstraction layer u simplifies user interface, improved reliability, performance F executive improvements, partial 64-bit support F environmental subsystems n versions F file system u desktop: XP personal – 95/98 replacement, professional – advanced features like POSIX support, some network features 1 u server: .NET – support for web/print service, clusters, large memory2 and multiple processors Design goals Components n XP is microkernel-based, modular n security – NT was C-2 certified (US -
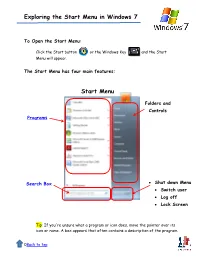
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Copyrighted Material
11_783269 bindex.qxp 11/10/06 11:15 AM Page 209 Index applications (defined), 205. See also programs Numerics arranging windows, 43–44 100% button (Internet Explorer 7), 99–100 assigning sounds to program events, 24 audio visualizations, 186 A Windows Media Player 11, 183, 185–186 accessibility options, 156 audio CDs. See CDs accessories, 205 Audio Description feature, 157 account types, 169 AutoComplete feature (Internet Explorer 7), 101 accounts (administrative), 169 automatic updates with Windows Update, 161–162, 167 accounts (e-mail), 124 AutoPlay, 13, 148, 151 accounts (user) Autosearching feature (Internet Explorer 7), 113 account types, 169 adding, 169 creating, 169 B deleting, 170 backgrounds for desktop, 24 managing, 168, 170 Backup and Restore Center, 140–143, 146 names, 169 Backup Files dialog box, 141 Parental Controls, 170 backups passwords, 169 CompletePC Backup utility, 140–142 pictures, 169–170 DVD discs, 142 switching, 74 File and Folder Backup utility, 140–142 User Account Control (UAC), 170 Send To shortcut menu command, 64–65 activity reporting, 165 stopping, 141 activity reports, 166 BitLocker drive encryption, 163–164 Add Printer Wizard, 149–151 blocking Add to Library dialog box, 187 computer use, 165 adding Web sites, 165 bookmarks to Favorites Center, 102 blog, 208 gadgets, 31–32 bookmarks (Internet Explorer 7) icons, 35 adding to Favorites Center, 102 languages, 155–156 deleting, 104 music, 187 importing, 101 printers, 149–151 moving, 103–105 user accounts, 169 organizing, 103–105 address bar, 15–16 renaming, 104 address book, 128–130 selecting, 103 Address toolbar, 41 browser (defined), 208. See also Internet Explorer 7 adjusting volume, 152 browsing offline. -

Ultimate Spider-Man™ README Last Updated: 6/28/05
Ultimate Spider-Man™ README Last Updated: 6/28/05 TABLE OF CONTENTS INTRODUCTION INSTALLATION & SET UP 1. Minimum System Requirements 2. Autoplay 3. DirectX(R) Detection & Installation VIDEO ISSUES 1. Monitors 2. In-game and Desktop Resolutions 3. Graphical Corruption When Changing Video Settings 4. Windowed Mode/Standby Mode 5. Changing Brightness and Contrast GENERAL ISSUES 1. Alt-Tab & Alt-Enter 2. Uninstalling with Antivirus Software Enabled 3. Gamepad Options 4. Invert Controls Setting 5. Options for Lower End Systems INTRODUCTION Refer to this document if you encounter difficulties with one or more aspects of installation or running the Ultimate Spider-Man™ game. Many of the most commonly encountered issues are covered here. INSTALLATION & SET UP 1. Ultimate Spider-Man™ Minimum System Requirements • 3D hardware accelerator card required - 100% DirectX(R) 9.0c-compliant 64 MB video card and drivers* • Microsoft(R) Windows(R) 2000/XP • Pentium(R) III 1.2 GHz or Athlon(TM) 1.2 GHz or higher processor • 256 MB of RAM • 3500 MB of uncompressed hard disk space (plus 400 MB for the Windows(R) swap file) • A 100% Windows(R) 2000/XP - compatible computer system including: • DirectX(R) 9.0c (Included) • 100% DirectX(R) 9.0c-compliant true 16-bit sound card and drivers • 100% Windows(R) 2000/XP - compatible mouse, keyboard and drivers • 100% Windows(R) 2000/XP - compatible quad speed CD-ROM drive (600 K/sec sustained transfer rate) and drivers *Supported Chipsets for Windows 2000/XP All NVIDIA(R) GeForce2(TM) and better chipsets All ATI(R) Radeon 7500(TM) and better chipsets *Important Note: Some 3D accelerator cards with the chipsets listed here may not be compatible with the 3D acceleration features utilized by Ultimate Spider-Man™.