The Downadup Codex a Comprehensive Guide to the Threat’S Mechanics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress
Order Code RL32114 Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress Updated January 29, 2008 Clay Wilson Specialist in Technology and National Security Foreign Affairs, Defense, and Trade Division Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress Summary Cybercrime is becoming more organized and established as a transnational business. High technology online skills are now available for rent to a variety of customers, possibly including nation states, or individuals and groups that could secretly represent terrorist groups. The increased use of automated attack tools by cybercriminals has overwhelmed some current methodologies used for tracking Internet cyberattacks, and vulnerabilities of the U.S. critical infrastructure, which are acknowledged openly in publications, could possibly attract cyberattacks to extort money, or damage the U.S. economy to affect national security. In April and May 2007, NATO and the United States sent computer security experts to Estonia to help that nation recover from cyberattacks directed against government computer systems, and to analyze the methods used and determine the source of the attacks.1 Some security experts suspect that political protestors may have rented the services of cybercriminals, possibly a large network of infected PCs, called a “botnet,” to help disrupt the computer systems of the Estonian government. DOD officials have also indicated that similar cyberattacks from individuals and countries targeting economic, -

Post-Mortem of a Zombie: Conficker Cleanup After Six Years Hadi Asghari, Michael Ciere, and Michel J.G
Post-Mortem of a Zombie: Conficker Cleanup After Six Years Hadi Asghari, Michael Ciere, and Michel J.G. van Eeten, Delft University of Technology https://www.usenix.org/conference/usenixsecurity15/technical-sessions/presentation/asghari This paper is included in the Proceedings of the 24th USENIX Security Symposium August 12–14, 2015 • Washington, D.C. ISBN 978-1-939133-11-3 Open access to the Proceedings of the 24th USENIX Security Symposium is sponsored by USENIX Post-Mortem of a Zombie: Conficker Cleanup After Six Years Hadi Asghari, Michael Ciere and Michel J.G. van Eeten Delft University of Technology Abstract more sophisticated C&C mechanisms that are increas- ingly resilient against takeover attempts [30]. Research on botnet mitigation has focused predomi- In pale contrast to this wealth of work stands the lim- nantly on methods to technically disrupt the command- ited research into the other side of botnet mitigation: and-control infrastructure. Much less is known about the cleanup of the infected machines of end users. Af- effectiveness of large-scale efforts to clean up infected ter a botnet is successfully sinkholed, the bots or zom- machines. We analyze longitudinal data from the sink- bies basically remain waiting for the attackers to find hole of Conficker, one the largest botnets ever seen, to as- a way to reconnect to them, update their binaries and sess the impact of what has been emerging as a best prac- move the machines out of the sinkhole. This happens tice: national anti-botnet initiatives that support large- with some regularity. The recent sinkholing attempt of scale cleanup of end user machines. -

Undergraduate Report
UNDERGRADUATE REPORT Attack Evolution: Identifying Attack Evolution Characteristics to Predict Future Attacks by MaryTheresa Monahan-Pendergast Advisor: UG 2006-6 IINSTITUTE FOR SYSTEMSR RESEARCH ISR develops, applies and teaches advanced methodologies of design and analysis to solve complex, hierarchical, heterogeneous and dynamic problems of engineering technology and systems for industry and government. ISR is a permanent institute of the University of Maryland, within the Glenn L. Martin Institute of Technol- ogy/A. James Clark School of Engineering. It is a National Science Foundation Engineering Research Center. Web site http://www.isr.umd.edu Attack Evolution 1 Attack Evolution: Identifying Attack Evolution Characteristics To Predict Future Attacks MaryTheresa Monahan-Pendergast Dr. Michel Cukier Dr. Linda C. Schmidt Dr. Paige Smith Institute of Systems Research University of Maryland Attack Evolution 2 ABSTRACT Several approaches can be considered to predict the evolution of computer security attacks, such as statistical approaches and “Red Teams.” This research proposes a third and completely novel approach for predicting the evolution of an attack threat. Our goal is to move from the destructive nature and malicious intent associated with an attack to the root of what an attack creation is: having successfully solved a complex problem. By approaching attacks from the perspective of the creator, we will chart the way in which attacks are developed over time and attempt to extract evolutionary patterns. These patterns will eventually -

Miscellaneous: Malware Cont'd & Start on Bitcoin
Miscellaneous: Malware cont’d & start on Bitcoin CS 161: Computer Security Prof. Raluca Ada Popa April 19, 2018 Credit: some slides are adapted from previous offerings of this course Viruses vs. Worms VIRUS WORM Propagates By infecting Propagates automatically other programs By copying itself to target systems Usually inserted into A standalone program host code (not a standalone program) Another type of virus: Rootkits Rootkit is a ”stealthy” program designed to give access to a machine to an attacker while actively hiding its presence Q: How can it hide itself? n Create a hidden directory w /dev/.liB, /usr/src/.poop and similar w Often use invisiBle characters in directory name n Install hacked Binaries for system programs such as netstat, ps, ls, du, login Q: Why does it Become hard to detect attacker’s process? A: Can’t detect attacker’s processes, files or network connections By running standard UNIX commands! slide 3 Sony BMG copy protection rootkit scandal (2005) • Sony BMG puBlished CDs that apparently had copy protection (for DRM). • They essentially installed a rootkit which limited user’s access to the CD. • It hid processes that started with $sys$ so a user cannot disaBle them. A software engineer discovered the rootkit, it turned into a Big scandal Because it made computers more vulneraBle to malware Q: Why? A: Malware would choose names starting with $sys$ so it is hidden from antivirus programs Sony BMG pushed a patch … But that one introduced yet another vulneraBility So they recalled the CDs in the end Detecting Rootkit’s -

The Botnet Chronicles a Journey to Infamy
The Botnet Chronicles A Journey to Infamy Trend Micro, Incorporated Rik Ferguson Senior Security Advisor A Trend Micro White Paper I November 2010 The Botnet Chronicles A Journey to Infamy CONTENTS A Prelude to Evolution ....................................................................................................................4 The Botnet Saga Begins .................................................................................................................5 The Birth of Organized Crime .........................................................................................................7 The Security War Rages On ........................................................................................................... 8 Lost in the White Noise................................................................................................................. 10 Where Do We Go from Here? .......................................................................................................... 11 References ...................................................................................................................................... 12 2 WHITE PAPER I THE BOTNET CHRONICLES: A JOURNEY TO INFAMY The Botnet Chronicles A Journey to Infamy The botnet time line below shows a rundown of the botnets discussed in this white paper. Clicking each botnet’s name in blue will bring you to the page where it is described in more detail. To go back to the time line below from each page, click the ~ at the end of the section. 3 WHITE -

Clustered Data ONTAP 8.3 CIFS File Access Reference Guide
Clustered Data ONTAP® 8.3 CIFS File Access Reference Guide February 2016 | 215-10876_A0 [email protected] Updated for 8.3.2 Table of Contents | 3 Contents Deciding whether to use this guide ........................................................... 12 Understanding SMB file access with Data ONTAP ................................. 14 How namespaces and volume junctions affect SMB access on SVMs with FlexVol volumes .................................................................................................. 14 What namespaces in SVMs with FlexVol volumes are ................................. 14 Volume junction usage rules ......................................................................... 14 How volume junctions are used in SMB and NFS namespaces .................... 15 What the typical NAS namespace architectures are ...................................... 15 LIF configuration requirements for file access management .................................... 18 How security styles affect data access ....................................................................... 19 What the security styles and their effects are ................................................ 19 Where and when to set security styles .......................................................... 20 How to decide on what security style to use on SVMs with FlexVol volumes .................................................................................................... 20 How security style inheritance works .......................................................... -

Ultimate Spider-Man™ README Last Updated: 6/28/05
Ultimate Spider-Man™ README Last Updated: 6/28/05 TABLE OF CONTENTS INTRODUCTION INSTALLATION & SET UP 1. Minimum System Requirements 2. Autoplay 3. DirectX(R) Detection & Installation VIDEO ISSUES 1. Monitors 2. In-game and Desktop Resolutions 3. Graphical Corruption When Changing Video Settings 4. Windowed Mode/Standby Mode 5. Changing Brightness and Contrast GENERAL ISSUES 1. Alt-Tab & Alt-Enter 2. Uninstalling with Antivirus Software Enabled 3. Gamepad Options 4. Invert Controls Setting 5. Options for Lower End Systems INTRODUCTION Refer to this document if you encounter difficulties with one or more aspects of installation or running the Ultimate Spider-Man™ game. Many of the most commonly encountered issues are covered here. INSTALLATION & SET UP 1. Ultimate Spider-Man™ Minimum System Requirements • 3D hardware accelerator card required - 100% DirectX(R) 9.0c-compliant 64 MB video card and drivers* • Microsoft(R) Windows(R) 2000/XP • Pentium(R) III 1.2 GHz or Athlon(TM) 1.2 GHz or higher processor • 256 MB of RAM • 3500 MB of uncompressed hard disk space (plus 400 MB for the Windows(R) swap file) • A 100% Windows(R) 2000/XP - compatible computer system including: • DirectX(R) 9.0c (Included) • 100% DirectX(R) 9.0c-compliant true 16-bit sound card and drivers • 100% Windows(R) 2000/XP - compatible mouse, keyboard and drivers • 100% Windows(R) 2000/XP - compatible quad speed CD-ROM drive (600 K/sec sustained transfer rate) and drivers *Supported Chipsets for Windows 2000/XP All NVIDIA(R) GeForce2(TM) and better chipsets All ATI(R) Radeon 7500(TM) and better chipsets *Important Note: Some 3D accelerator cards with the chipsets listed here may not be compatible with the 3D acceleration features utilized by Ultimate Spider-Man™. -

Critical Vulnerabilities Bulletin
January 18th, 2021 Critical Vulnerabilities Bulletin Confidential | Cyberint Copyright © All Rights Reserved 2020 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 EXECUTIVE SUMMARY Due to an unusual increase in Critical vulnerabilities found on Windows operating systems, Cyberint's Research Team has decided to release this bulletin to alert our customers of the potential impact. This bulletin will be expanded at the end of the month, as part of the Monthly Vulnerability bulletin we plan on releasing. The reason for this bulletin lies at 2 newly discovered vulnerabilities: 1. <No CVE assigned yet> - Corrupt NTFS OS partition without user interaction. 2. <No CVE assigned yet> - Trigger a BSOD by trying to access a system path. 3. CVE-2020-1398 - Potential bypass of Bitlocker protected systems, including Lock Screen bypass. We suspect that threat actors and updated malware may attempt to exploit these vulnerabilities to further impact potential victims. Confidential | Cyberint Copyright © All Rights Reserved 2020 2 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 NTFS CORRUPTION VULNERABILITY Published by a known vulnerability researcher, jonasLyk, it is possible to cause disk partition corruption by executing a cd command as a low privilege user, to a unique path, which causes the Windows Operating System to alert the user to a corrupted partition and force a restart. Whilst technical details are scarce, and the exact reason for the issue being unknown at this time, affected Windows builds using the NTFS file system include those from 1803 all the way to 20H2. According to SANS, the $bitmap is an attribute reserved for files marked as deleted, while $i30 is marked as an NTFS index attribute. -

The Blaster Worm: Then and Now
Worms The Blaster Worm: Then and Now The Blaster worm of 2003 infected at least 100,000 Microsoft Windows systems and cost millions in damage. In spite of cleanup efforts, an antiworm, and a removal tool from Microsoft, the worm persists. Observing the worm’s activity can provide insight into the evolution of Internet worms. MICHAEL n Wednesday, 16 July 2003, Microsoft and continued to BAILEY, EVAN Security Bulletin MS03-026 (www. infect new hosts COOKE, microsoft.com/security/incident/blast.mspx) more than a year later. By using a wide area network- FARNAM O announced a buffer overrun in the Windows monitoring technique that observes worm infection at- JAHANIAN, AND Remote Procedure Call (RPC) interface that could let tempts, we collected observations of the Blaster worm DAVID WATSON attackers execute arbitrary code. The flaw, which the during its onset in August 2003 and again in August 2004. University of Last Stage of Delirium (LSD) security group initially This let us study worm evolution and provides an excel- Michigan uncovered (http://lsd-pl.net/special.html), affected lent illustration of a worm’s four-phase life cycle, lending many Windows operating system versions, including insight into its latency, growth, decay, and persistence. JOSE NAZARIO NT 4.0, 2000, and XP. Arbor When the vulnerability was disclosed, no known How the Blaster worm attacks Networks public exploit existed, and Microsoft made a patch avail- The initial Blaster variant’s decompiled source code re- able through their Web site. The CERT Coordination veals its unique behavior (http://robertgraham.com/ Center and other security organizations issued advisories journal/030815-blaster.c). -

Iptrust Botnet / Malware Dictionary This List Shows the Most Common Botnet and Malware Variants Tracked by Iptrust
ipTrust Botnet / Malware Dictionary This list shows the most common botnet and malware variants tracked by ipTrust. This is not intended to be an exhaustive list, since new threat intelligence is always being added into our global Reputation Engine. NAME DESCRIPTION Conficker A/B Conficker A/B is a downloader worm that is used to propagate additional malware. The original malware it was after was rogue AV - but the army's current focus is undefined. At this point it has no other purpose but to spread. Propagation methods include a Microsoft server service vulnerability (MS08-067) - weakly protected network shares - and removable devices like USB keys. Once on a machine, it will attach itself to current processes such as explorer.exe and search for other vulnerable machines across the network. Using a list of passwords and actively searching for legitimate usernames - the ... Mariposa Mariposa was first observed in May 2009 as an emerging botnet. Since then it has infected an ever- growing number of systems; currently, in the millions. Mariposa works by installing itself in a hidden location on the compromised system and injecting code into the critical process ͞ĞdžƉůŽƌĞƌ͘ĞdžĞ͘͟/ƚŝƐknown to affect all modern Windows versions, editing the registry to allow it to automatically start upon login. Additionally, there is a guard that prevents deletion while running, and it automatically restarts upon crash/restart of explorer.exe. In essence, Mariposa opens a backdoor on the compromised computer, which grants full shell access to ... Unknown A botnet is designated 'unknown' when it is first being tracked, or before it is given a publicly- known common name. -
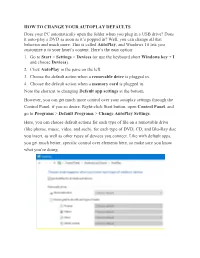
HOW to CHANGE YOUR AUTOPLAY DEFAULTS Does Your PC Automatically Open the Folder When You Plug in a USB Drive? Does It Auto-Play
HOW TO CHANGE YOUR AUTOPLAY DEFAULTS Does your PC automatically open the folder when you plug in a USB drive? Does it auto-play a DVD as soon as it’s popped in? Well, you can change all that behavior and much more. This is called AutoPlay, and Windows 10 lets you customize it to your heart’s content. Here’s the easy option: 1. Go to Start > Settings > Devices (or use the keyboard short Windows key + I and choose Devices). 2. Click AutoPlay in the pane on the left. 3. Choose the default action when a removable drive is plugged in. 4. Choose the default action when a memory card is plugged in. Note the shortcut to changing Default app settings at the bottom. However, you can get much more control over your autoplay settings through the Control Panel, if you so desire. Right-click Start button, open Control Panel, and go to Programs > Default Programs > Change AutoPlay Settings. Here, you can choose default actions for each type of file on a removable drive (like photos, music, video, and such), for each type of DVD, CD, and Blu-Ray disc you insert, as well as other types of devices you connect. Like with default apps, you get much better, specific control over elements here, so make sure you know what you’re doing. If nothing else, you should definitely change what Windows does for flash drives, since auto-running files from flash or thumb drives is one of the easiest ways to get a malware infection. . -

TANDBERG VIKING SERIES NAS APPLIANCE Storage Server Administration Manual
TANDBERG VIKING SERIES NAS APPLIANCE Storage Server Administration Manual TANDBERG DATA ASIA 20 Bendemeer Road, #04-05 Cyberhub, Singapore 339914 Phone + 65 6396 0786 Part No. 65 82 X2 - 01 Telefax + 65 6396 0787 January 2008 © Tandberg Data Asia Related publications available from Tandberg Data Asia: Part No. Title 6582B7 Tandberg Viking FS-1600 NAS Hardware User Manual 6582A7 Tandberg Viking FS-1500 NAS Hardware User Manual 658297 Tandberg Viking FS-412 NAS Hardware User Manual This publication may describe designs for which patents are granted or pen- ding. By publishing this information, Tandberg Data Asia conveys no license under any patent or any other rights. Every effort has been made to avoid errors in text and diagrams. However, Tandberg Data Asia assumes no responsibility for any errors which may ap- pear in this publication. It is the policy of Tandberg Data Asia to improve products as new techniques and components become available. Tandberg Data Asia therefore reserves the right to change specifications at any time. We would appreciate any comments on this publication. __________________________________________________________________________________________________ Table of Contents Table of Contents i 1. System Overview 1-1 1.1. Product Information 1-1 1.1.1. Product Manageability 1-2 1.2. Redundancy 1-2 1.2.1. Configuring RAID using 4 HDD (1U) 1-3 1.2.2. Configuring RAID using 16 HDD (3U) 1-4 1.2.3. System Volume (SV) 1-5 1.2.4. Data Volume (DV) 1-5 1.4. Deployment 1-5 1.4.1. File Server Consolidation 1-5 1.4.2. Multi-protocol Environments 1-5 1.4.3.