Portfolio Management Leveraging Software-Based Open Systems Architecture
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ASSESSING the MAINTAINABILITY of C++ SOURCE CODE by MARIUS SUNDBAKKEN a Thesis Submitted in Partial Fulfillment of the Requireme
ASSESSING THE MAINTAINABILITY OF C++ SOURCE CODE By MARIUS SUNDBAKKEN A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Computer Science WASHINGTON STATE UNIVERSITY School of Electrical Engineering and Computer Science DECEMBER 2001 To the Faculty of Washington State University: The members of the Committee appointed to examine the thesis of MARIUS SUNDBAKKEN find it satisfactory and recommend that it be accepted. Chair ii ASSESSING THE MAINTAINABILITY OF C++ SOURCE CODE Abstract by Marius Sundbakken, M.S. Washington State University December 2001 Chair: David Bakken Maintenance refers to the modifications made to software systems after their first release. It is not possible to develop a significant software system that does not need maintenance because change, and hence maintenance, is an inherent characteristic of software systems. It has been estimated that it costs 80% more to maintain software than to develop it. Clearly, maintenance is the major expense in the lifetime of a software product. Predicting the maintenance effort is therefore vital for cost-effective design and development. Automated techniques that can quantify the maintainability of object- oriented designs would be very useful. Models based on metrics for object-oriented source code are necessary to assess software quality and predict engineering effort. This thesis will look at C++, one of the most widely used object-oriented programming languages in academia and industry today. Metrics based models that assess the maintainability of the source code using object-oriented software metrics are developed. iii Table of Contents 1. Introduction .................................................................................................................1 1.1. Maintenance and Maintainability....................................................................... -

Software Maintenance Maintenance Is Inevitable Types of Maintenance
SoftWindows 8/18/2003 Software Maintenance • Managing the processes of system change Reverse Engineering (Software Maintenance & Reengineering) © SERG Maintenance is Inevitable • The system requirements are likely to change while the system is being developed because the environment is changing. • When a system is installed in an environment it changes that environment and therefore changes the system requirements. Reverse Engineering (Software Maintenance & Reengineering) © SERG Types of Maintenance • Perfective maintenance – Changing a system to make it meet its requirements more effectively. • Adaptive maintenance – Changing a system to meet new requirements. • Corrective maintenance – Changing a system to correct deficiencies in the way meets its requirements. Reverse Engineering (Software Maintenance & Reengineering) © SERG Distributed Objects 1 SoftWindows 8/18/2003 Distribution of Maintenance Effort Corrective maintenance (17%) Adaptive maintenance Perfective (18%) maintenance (65%) Reverse Engineering (Software Maintenance & Reengineering) © SERG Evolving Systems • It is usually more expensive to add functionality after a system has been developed rather than design this into the system: – Maintenance staff are often inexperienced and unfamiliar with the application domain. – Programs may be poorly structured and hard to understand. – Changes may introduce new faults as the complexity of the system makes impact assessment difficult. – The structure may be degraded due to continual change. – There may be no documentation available to describe the program. Reverse Engineering (Software Maintenance & Reengineering) © SERG The Maintenance Process • Maintenance is triggered by change requests from customers or marketing requirements. • Changes are normally batched and implemented in a new release of the system. • Programs sometimes need to be repaired without a complete process iteration but this is dangerous as it leads to documentation and programs getting out of step. -

System Software Maintenance and Support 24X7
SYSTEM SOFTWARE MAINTENANCE AND SUPPORT SERVICES - PREMIUM These Premium System Software Maintenance and Support Service terms and conditions (“Terms and Conditions”) apply to any quote, order, order acknowledgment, and invoice, and any sale or provision of Premium System Software Maintenance and Support Services as defined herein provided to Customer by Viavi Solutions Inc. (“Viavi”), in addition to Viavi’s General Terms (“General Terms”) and/or Software License Terms, which are incorporated by reference herein and are either attached hereto, available at www.viavisolutions.com/terms or available upon request. k) Severity Level means classification of a problem determined by Viavi personnel 1. PURPOSE AND SCOPE based upon the Customer’s assessment of business impact. The three (3) Severity Levels that apply to the Services are as follows: These Terms and Conditions describe the Services that Viavi will provide to, and perform for, Customer. These Terms and Conditions apply to Services for standard Software, as 1) Problem Report – Critical means conditions that severely affect the defined herein, and are limited to the System configuration specified in a Statement of primary functionality of the System and because of the business impact to the Work (“SOW”) or other ordering document (i.e., a quote, order, order acknowledgment customer requires non-stop immediate corrective action, regardless of time of day or invoice) which contains a description of the System. All Services and Documentation or day of the week as viewed by a customer -

Project Management © Adrienne Watt
Project Management © Adrienne Watt This work is licensed under a Creative Commons-ShareAlike 4.0 International License Original source: The Saylor Foundation http://open.bccampus.ca/find-open-textbooks/?uuid=8678fbae-6724-454c-a796-3c666 7d826be&contributor=&keyword=&subject= Contents Introduction ...................................................................................................................1 Preface ............................................................................................................................2 About the Book ..............................................................................................................3 Chapter 1 Project Management: Past and Present ....................................................5 1.1 Careers Using Project Management Skills ......................................................................5 1.2 Business Owners ...............................................................................................................5 Example: Restaurant Owner/Manager ..........................................................................6 1.2.1 Outsourcing Services ..............................................................................................7 Example: Construction Managers ..........................................................................8 1.3 Creative Services ................................................................................................................9 Example: Graphic Artists ...............................................................................................10 -

Computer Organization and Architecture Designing for Performance Ninth Edition
COMPUTER ORGANIZATION AND ARCHITECTURE DESIGNING FOR PERFORMANCE NINTH EDITION William Stallings Boston Columbus Indianapolis New York San Francisco Upper Saddle River Amsterdam Cape Town Dubai London Madrid Milan Munich Paris Montréal Toronto Delhi Mexico City São Paulo Sydney Hong Kong Seoul Singapore Taipei Tokyo Editorial Director: Marcia Horton Designer: Bruce Kenselaar Executive Editor: Tracy Dunkelberger Manager, Visual Research: Karen Sanatar Associate Editor: Carole Snyder Manager, Rights and Permissions: Mike Joyce Director of Marketing: Patrice Jones Text Permission Coordinator: Jen Roach Marketing Manager: Yez Alayan Cover Art: Charles Bowman/Robert Harding Marketing Coordinator: Kathryn Ferranti Lead Media Project Manager: Daniel Sandin Marketing Assistant: Emma Snider Full-Service Project Management: Shiny Rajesh/ Director of Production: Vince O’Brien Integra Software Services Pvt. Ltd. Managing Editor: Jeff Holcomb Composition: Integra Software Services Pvt. Ltd. Production Project Manager: Kayla Smith-Tarbox Printer/Binder: Edward Brothers Production Editor: Pat Brown Cover Printer: Lehigh-Phoenix Color/Hagerstown Manufacturing Buyer: Pat Brown Text Font: Times Ten-Roman Creative Director: Jayne Conte Credits: Figure 2.14: reprinted with permission from The Computer Language Company, Inc. Figure 17.10: Buyya, Rajkumar, High-Performance Cluster Computing: Architectures and Systems, Vol I, 1st edition, ©1999. Reprinted and Electronically reproduced by permission of Pearson Education, Inc. Upper Saddle River, New Jersey, Figure 17.11: Reprinted with permission from Ethernet Alliance. Credits and acknowledgments borrowed from other sources and reproduced, with permission, in this textbook appear on the appropriate page within text. Copyright © 2013, 2010, 2006 by Pearson Education, Inc., publishing as Prentice Hall. All rights reserved. Manufactured in the United States of America. -
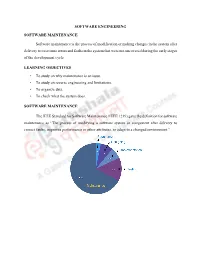
Software Engineering Software Maintenance
SOFTWARE ENGINEERING SOFTWARE MAINTENANCE Software maintenance is the process of modification or making changes in the system after delivery to overcome errors and faults in the system that were not uncovered during the early stages of the development cycle. LEARNING OBJECTIVES • To study on why maintenance is an issue. • To study on reverse engineering and limitations. • To organize data. • To check what the system does. SOFTWARE MAINTENANCE The IEEE Standard for Software Maintenance (IEEE 1219) gave the definition for software maintenance as “The process of modifying a software system or component after delivery to correct faults, improves performance or other attributes, or adapt to a changed environment.” Maintenance Principles 100 Hardware Development 60 Software 20 Maintenance Percent of total cost total of Percent 1995 2000 2010 The IEEE/EIA 12207 Standard defines maintenance as modification to code and associated documentation due to a problem or the need for improvement. Nature of Maintenance Modification requests are logged and tracked, the impact of proposed changes are determined, code and other software artifacts are modified, testing is conducted, and a new version of the software product is released. Maintainers can learn from the developer´s knowledge of the software. Need for Maintenance Maintenance must be performed in order to: • Correct faults. • Improve the design. • Implement enhancements. • Interface with other systems. • Adapt programs so that different hardware, software, system features, and telecommunications facilities can be used. • Migrate legacy software. • Retire software Tasks of a maintainer The maintainer does the following functions: • Maintain control over the software´s day-to-day functions. • Maintain control over software modification. -

Implementing Concurrent Engineering and QFD Method to Achieve Realization of Sustainable Project
sustainability Article Implementing Concurrent Engineering and QFD Method to Achieve Realization of Sustainable Project Lidija Rihar and Janez Kušar * Faculty of Mechanical Engineering, University of Ljubljana, SI-1000 Ljubljana, Slovenia; [email protected] * Correspondence: [email protected] Abstract: In this paper, we present the impact of concurrent engineering strategies, methods, and tools on product sustainability. Concurrent engineering can be used to achieve the primary goals of a product realization project: lower costs, shorter times, high quality, and increasing value. Currently, it is important that new products also meet product sustainability goals, such as economic, environmental, and social goals. The sustainability of a product can be influenced the most in the early stages of product development, so in this paper, we present a customized quality function deployment (QFD) method called the house of sustainability, which translates sustainability requirements into technical solutions for a product. A seven-step process for implementing a sustainable product realization project is also proposed, in which the house of sustainability is one of the most important tools. The proposed process is illustrated with an example of a concurrent product realization project in engineering to order production. Keywords: concurrent engineering; product sustainability; production sustainability; new product development; QFD Citation: Rihar, L.; Kušar, J. 1. Introduction Implementing Concurrent Sustainability has lately become one of the key features of new products. Sustainabil- Engineering and QFD Method to ity implies product properties that characterize it from the idea, through development, Achieve Realization of Sustainable production, use, and maintenance, to the end of the life of the product (disposal). -

Read Ms. Shaw's First Amended Complaint
Janet L. Goldstein Peter W. Chatfield THE MARTYN FIRM, PLLC PHILLIPS & COHEN LLP 1054 31st Street, NW 2000 Massachusetts Ave., NW Washington, D.C. 20007 Washington, D.C. 20036 Tel: (202) 965-3060 Tel: (202) 833-4567 Fax: (202) 965-3063 Fax: (202) 833-1815 Jonathan A. Willens (JW-9180) JONATHAN A. WILLENS LLC 217 Broadway, Suite 707 New York, New York 10007 Tel: (212) 619-3749 Fax: (800) 879-7938 Attorneys for qui tam plaintiff Ann-Marie Shaw UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF NEW YORK UNITED STATES OF AMERICA ) 06 CV 3552 (DLI) (SMG) ex rel. ANN-MARIE SHAW ) and ) AMENDED COMPLAINT ) FOR VIOLATIONS OF STATE OF CALIFORNIA ex rel.ANN-MARIE SHAW ) FEDERAL AND STATE DISTRICT OF COLUMBIA ex rel.ANN-MARIE SHAW ) FALSE CLAIMS ACTS STATE OF FLORIDA ex rel.ANN-MARIE SHAW ) STATE OF HAWAII ex rel.ANN-MARIE SHAW ) STATE OF ILLINOIS ex rel.ANN-MARIE SHAW ) COMMONWEALTH OF MASSACHUSETTS ) ex rel.ANN-MARIE SHAW ) STATE OF NEVADA ex rel.ANN-MARIE SHAW ) COMMONWEALTH OF VIRGINA ) ex rel.ANN-MARIE SHAW ) STATE & CITY OF NEW YORK ) ex rel.ANN-MARIE SHAW, ) ) JURY TRIAL DEMANDED Plaintiffs, ) ) FILED UNDER SEAL v. ) ) CA, INC., ) ) Defendant. ) _______________________________________________ ) Through her attorneys, plaintiff and qui tam relator Ann-Marie Shaw, for her Amended Complaint against Defendant CA, Inc. (“CA”), formerly known as Computer Associates International, Inc. or “Computer Associates,” alleges as follows: FACTS COMMON TO ALL COUNTS A. Introduction 1. This is a civil action to recover damages and civil penalties arising from false and/or fraudulent statements, records, and claims made and caused to be made by the Defendant CA and/or its agents and employees in violation of the Federal Civil False Claims Act, 31 U.S.C. -

Microcomputers: NQS PUBLICATIONS Introduction to Features and Uses
of Commerce Computer Science National Bureau and Technology of Standards NBS Special Publication 500-110 Microcomputers: NQS PUBLICATIONS Introduction to Features and Uses QO IGf) .U57 500-110 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards' was established by an act ot Congress on March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides; (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to promote public safety. The Bureau's technical work is per- formed by the National Measurement Laboratory, the National Engineering Laboratory, and the Institute for Computer Sciences and Technology. THE NATIONAL MEASUREMENT LABORATORY provides the national system of physical and chemical and materials measurement; coordinates the system with measurement systems of other nations and furnishes essential services leading to accurate and uniform physical and chemical measurement throughout the Nation's scientific community, industry, and commerce; conducts materials research leading to improved methods of measurement, standards, and data on the properties of materials needed by industry, commerce, educational institutions, and Government; provides advisory and research services to other Government agencies; develops, produces, and -

Development of a Multi-Bus Platform for Automation Testbed
A Master Thesis Work in Electronics Development of a Multi‐bus platform for automation testbed By Lukas Knapik and Mathias Isaksson Examiner: Professor Lars Asplund, Mälardalens University Supervisor: Martin Ekström, PhD Student in Electronics, Mälardalen University Dan Olsson, M.SC Physics, Infotiv AB Lukas Knapik Mathias Isaksson 070‐7124691 073‐8079350 [email protected] [email protected] Mälardalen University, Västerås 2010‐02‐17 Development of a Multi‐bus platform for automation testbed Master Thesis CEL505 ABSTRACT The task for this thesis was to develop, construct and evaluate a multi‐bus communication system, connected to a PC via USB and capable of communicating in CAN, I2C and SPI and develop drivers for it in National Instruments LabVIEW. In the beginning a study was made of the communication buses followed by an investigation of what type of hardware that could accomplish this task. A microcontroller unit was selected and programmed in MikroElektronika MikroC Pro v.3.2 to act as the interface between the communication busses and PC. A PCB prototype of the system was constructed by using Eagle Cad software v.5.6.0. General drivers for this system where created in LabVIEW v.8.6.1 so the end‐user simply can create their own applications and control the compatible hardware depending on their type of purposes. The system was tested on criteria’s such as: speed, power consumption, burst performance and transmission length depending on which communication bus was used. Lukas Knapik, Mathias Isaksson Mälardalen University, Västerås 2010‐02‐17 Development of a Multi‐bus platform for automation testbed Master Thesis CEL505 ACKNOWLEDGEMENTS We would like to thank Infotiv AB for giving us the opportunity to do this thesis. -

DAVID J. ERICKSON 6 Oak Drive Topsfield, MA 01983 978-887-0125 [email protected]
DAVID J. ERICKSON 6 Oak Drive Topsfield, MA 01983 978-887-0125 [email protected] Objective: To develop successful products from concept to production using my skills in analog, digital and firmware design engineering, team and project management Management: Hands-on Engineering Management, Hardware Engineering and Project Management Education: B.S.E.E., 1976 Worcester Polytechnic Institute, Worcester, MA Design Analog processing including video, PLL, A/D, D/A, video timing, Specialties: video analog and digital LSI, graphics LCDs. Digital circuitry: Image memory (DRAM), multiport memory, pipelined image processors, bus interfaces, state machine, digital components used: PALs, DRAMs, SRAMs, PROMs, ASICs, TTL, ECL, PGAs (Xilinx, Actel, Altera), DSP blocks, FIFOs bit slice, VLSI. Instrument design for chemical and ATE industries. Medical (patient monitoring and display) electronics. Sensor interfacing, power supplies, low power design. Microprocessor hardware and firmware design, C and assembler: AVR, Z80 and 68hc11. Audio processing and control, amplifiers, test equipment. Marine and weather electronics. Troubleshooting all types of problems. Bus interfacing to MicroBus, VME/VXI, PC/AT, Multibus, Q-Bus LabView Experience: STH Company (Consultant, part time) Wayland, MA 4/02 - 9/02 Hardware and firmware design of Colorimeter Instrument complete redesign. Product development from specification to final release. Instrument uses an AVR microprocessor to implement a complete optical / chemical measurement instrument. Implemented complex acquisition timing, math, communications, display and serial interface, menu system. Development cost and product cost goals were met. Analogic Corp., Peabody, MA 1/98 to 6/02 Chief Engineer, Test and Measurement Division Directed the engineering department of the division that was the leading 3rd party supplier of mixed-signal instruments to the ATE industry. -

Techniques for Software Maintenance 57 02 58
01 Techniques for Software Maintenance 57 02 58 03 59 04 60 Kostas Kontogiannis 05 61 Department of Electrical and Computer Engineering, National Technical University of Athens, 06 62 Athens, Greece 07 63 08 64 09 65 10 66 Abstract 11 Software maintenance constitutes a major phase of the software life cycle. Studies indicate that software 67 12 maintenance is responsible for a significant percentage of a system’s overall cost and effort. The software 68 13 engineering community has identified four major types of software maintenance, namely, corrective, 69 14 perfective, adaptive, and preventive maintenance. Software maintenance can be seen from two major points 70 15 of view. First, the classic view where software maintenance provides the necessary theories, techniques, 71 16 methodologies, and tools for keeping software systems operational once they have been deployed to their 72 17 operational environment. Most legacy systems subscribe to this view of software maintenance. The second 73 18 view is a more modern emerging view, where maintenance is an integral part of the software development 74 19 process and it should be applied from the early stages in the software life cycle. Regardless of the view by 75 which we consider software maintenance, the fact is that it is the driving force behind software evolution, a 20 76 very important aspect of a software system. This entry provides an in-depth discussion of software 21 77 Q1 maintenance techniques, methodologies, tools, and emerging trends. 22 78 23 79 24 80 25 INTRODUCTION type of software maintenance is referred to as Adaptive 81 26 82 Software Maintenance and refers to activities that aim to 27 83 Software maintenance is an integral part of the software modify models and artifacts of existing systems so that 28 84 life cycle and has been identified as an activity that affects these systems can be integrated with new systems or 29 85 in a major way the overall system cost and effort.