Create Automation Scripts for Windows with Autoit
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Autocoding Methods for Networked Embedded Systems
University of Warwick institutional repository: http://go.warwick.ac.uk/wrap A Thesis Submitted for the Degree of PhD at the University of Warwick http://go.warwick.ac.uk/wrap/36892 This thesis is made available online and is protected by original copyright. Please scroll down to view the document itself. Please refer to the repository record for this item for information to help you to cite it. Our policy information is available from the repository home page. Innovation Report AUTOCODING METHODS FOR NETWORKED EMBEDDED SYSTEMS Submitted in partial fulfilment of the Engineering Doctorate By James Finney, 0117868 November 2009 Academic Supervisors: Dr. Peter Jones, Ross McMurran Industrial Supervisor: Dr. Paul Faithfull Declaration I have read and understood the rules on cheating, plagiarism and appropriate referencing as outlined in my handbook and I declare that the work contained in this submission is my own, unless otherwise acknowledged. Signed: …………………………………………………………………….James Finney ii Acknowledgements I would like to thank Rapicore Ltd and the EPSRC for funding this project. I would also like to offer special thanks to my supervisors: Dr. R.P. Jones, Dr. P. Faithfull, and R. McMurran, for their time, support, and guidance throughout this project. iii Table of Contents Declaration ....................................................................................................................... ii Acknowledgements ......................................................................................................... iii Figures -

A Bibliography of O'reilly & Associates and O
A Bibliography of O'Reilly & Associates and O'Reilly Media. Inc. Publishers Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 08 February 2021 Version 3.67 Title word cross-reference #70 [1263, 1264]. #70-059 [1263]. #70-068 [1264]. 2 [949]. 2 + 2 = 5986 [1456]. 3 [1149, 1570]. *# [1221]. .Mac [1940]. .NET [1860, 22, 186, 342, 441, 503, 591, 714, 716, 721, 730, 753, 786, 998, 1034, 1037, 1038, 1043, 1049, 1089, 1090, 1091, 1119, 1256, 1468, 1858, 1859, 1863, 1899, 1900, 1901, 1917, 1997, 2029]. '05 [461, 1532]. 08 [1541]. 1 [1414]. 1.0 [1009]. 1.1 [59]. 1.2 [1582]. 1000 [1511]. 1000D [1073]. 10g [711, 710]. 10th [2109]. 11 [1385]. 1 2 2 [53, 209, 269, 581, 2134, 919, 940, 1515, 1521, 1530, 2023, 2045]. 2.0 [2, 55, 203, 394, 666, 941, 1000, 1044, 1239, 1276, 1504, 1744, 1801, 2073]. 2.1 [501]. 2.2 [201]. 2000 [38, 202, 604, 610, 669, 927, 986, 1087, 1266, 1358, 1359, 1656, 1751, 1781, 1874, 1959, 2069]. 2001 [96]. 2003 [70, 71, 72, 73, 74, 279, 353, 364, 365, 789, 790, 856, 987, 1146, 1960, 2026]. 2003-2013 [1746]. 2004 [1195]. 2005 [84, 151, 755, 756, 1001, 1041, 1042, 1119, 1122, 1467, 2120, 2018, 2056]. 2006 [152, 153]. 2007 [618, 726, 727, 728, 1123, 1125, 1126, 1127, 2122, 1973, 1974, 2030]. -
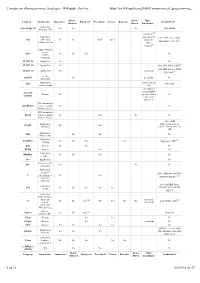
Comparison of Programming Languages - Wikipedia, the Free
Comparison of programming languages - Wikipedia, the free ... https://en.wikipedia.org/wiki/Comparison_of_programming_... Object- Event- Other Language Intended use Imperative Functional Procedural Generic Reflective Standardized? Oriented Driven Paradigm(s) Application, ActionScript 3.0 Yes Yes Yes 1996, ECMA client-side, Web concurrent,[4] [5] Application, distributed, 1983, 2005, 2012, ANSI, Ada embedded, Yes Yes Yes[2] Yes[3] imperative ISO, GOST 27831-88[7] realtime, system object- oriented[6] Highly domain- specific, Aldor Yes Yes Yes No symbolic computing ALGOL 58 Application Yes No ALGOL 60 Application Yes 1960, IFIP WG 2.1, ISO[8] 1968, IFIP WG 2.1, GOST ALGOL 68 Application Yes concurrent 27974-88,[9] Parallel Ateji PX Yes pi calculus No application Application, array-oriented, APL 1989, ISO data processing tacit any, syntax is usually highly Assembly General Yes specific, related No language to the target processor GUI automation AutoHotkey (macros), highly Yes No domain-specific GUI automation AutoIt (macros), highly Yes Yes Yes No domain-specific 1983, ANSI Application, (http://portal.acm.org BASIC Yes Yes education /citation.cfm?id=988221), ISO Application, BBj Yes Yes No business, Web Application, BeanShell Yes Yes Yes Yes [10] scripting In progress, JCP BitC System Yes Yes No BLISS System Yes No Application, BlitzMax Yes Yes Yes No game Boo Application No domain-specific, Bro Yes Yes No application Application, [11] system, 1989, ANSI C89, ISO C90, C general purpose, Yes Yes ISO C99, ISO C11[12] low-level operations 1998, ISO/IEC -

Metadefender Core V4.17.3
MetaDefender Core v4.17.3 © 2020 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of MetaDefender Core 14 1. Quick Start with MetaDefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Process Files with MetaDefender Core 21 2. Installing or Upgrading MetaDefender Core 22 2.1. Recommended System Configuration 22 Microsoft Windows Deployments 22 Unix Based Deployments 24 Data Retention 26 Custom Engines 27 Browser Requirements for the Metadefender Core Management Console 27 2.2. Installing MetaDefender 27 Installation 27 Installation notes 27 2.2.1. Installing Metadefender Core using command line 28 2.2.2. Installing Metadefender Core using the Install Wizard 31 2.3. Upgrading MetaDefender Core 31 Upgrading from MetaDefender Core 3.x 31 Upgrading from MetaDefender Core 4.x 31 2.4. MetaDefender Core Licensing 32 2.4.1. Activating Metadefender Licenses 32 2.4.2. Checking Your Metadefender Core License 37 2.5. Performance and Load Estimation 38 What to know before reading the results: Some factors that affect performance 38 How test results are calculated 39 Test Reports 39 Performance Report - Multi-Scanning On Linux 39 Performance Report - Multi-Scanning On Windows 43 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. -

Visustin Features and Versions
Visustin features and versions v8 v7 v6 v5 v4 v3 Flow chart styles to choose from 2 2 1 1 1 1 UML Activity Diagrams Y Y Y Y Y Flowchart large files (>3000 lines) Y Y Y Flowchart individual procedures Y Y Y Print in high quality Y Y Y Save BMP, GIF, JPG, PNG, EMF, WMF, DOT, HTML, MHT Y Y Y Y Y Y Save TIFF Y Y Y Y Save PDF, single page and printer pages Y Y Y Save PDF, multipage Y Y Save PowerPoint PPT - Y Y Y Y Save Word DOC Y Y Y Y Y Save Word DOCX Y Load images Y Y Y Y Y Metrics Y Y Y Y Y Option: Each statement in its own box Y Y Option: Wrap lines Y Y Option: Configure colors and labels Y Y High-density display support (high DPI) Y Y Pro Edition features Export Visio VSD [Pro] Y Y Y Y Y Y Export Visio VSDX [Pro] Y Editor [Pro] Y Y Y Y Bulk flowcharting [Pro] Y Y Y Y Y Y Bulk flowcharting jobs (.vjb) [Pro] Y Y Y Y Bulk flowcharting individual procedures [Pro] Y Y Y Compatibility Windows version, newest supported 10 8 7 Vista 2003 2003 Office version, newest supported 2016 2013 2010 2007 2007 2003 Language support on next page. ©2016 Aivosto Oy www.aivosto.com Visustin language support v8 v7 v6 v5 v4 v3 ABAP Y Y ActionScript, MXML Y Y ActionScript, semicolon-less Y Ada Y Y Y Y Y Y Assembler: MASM, NASM, IAR/MSP430 Y Y Y Y Y ASP Y Y Y Y Y Y AutoIt Y Batch files Y Y C/C++ Y Y Y Y Y Y C# Y Y Y Y Y Y Clipper Y Y Y Y Y COBOL Y Y Y Y Y Y ColdFusion Y Y Y Y Fortran Y Y Y Y Y Y GW-BASIC Y (Y) HTML Y Java Y Y Y Y Y Y JavaScript Y Y Y Y Y Y JavaScript, semicolon-less Y JCL (MVS) Y Y Y JSP Y Y Y Y Y Y LotusScript Y Y Y Y Y MATLAB Y Y Y Pascal/Delphi Y Y Y Y Y Y Perl Y Y Y Y Y Y PHP Y Y Y Y Y Y PL/I Y Y Y PL/SQL Y Y Y Y Y Y PowerBASIC Y PowerScript (PowerBuilder) Y Y Y Y Y PureBasic Y Y Y Y Y Python Y Y Y Y Y QuickBASIC Y Y Y Y Y Y REALbasic Y Y Y Y Y Rexx Y Y Y RPG Y Ruby Y Y SAS Y Y Y Shell script (bash, csh, tcsh, ksh, sh) Y Y Tcl Y Y T-SQL Y Y Y Y Y Y VBScript Y Y Y (Y) (Y) (Y) Visual Basic, VBA Y Y Y Y Y Y Visual Basic .Net Y Y Y Y Y Y Visual FoxPro Y Y Y Y Y XML Y XSLT Y Y Y Y Languages have been updated to newer syntax from version to version. -

Comparative Programming Languages CM20253
We have briefly covered many aspects of language design And there are many more factors we could talk about in making choices of language The End There are many languages out there, both general purpose and specialist And there are many more factors we could talk about in making choices of language The End There are many languages out there, both general purpose and specialist We have briefly covered many aspects of language design The End There are many languages out there, both general purpose and specialist We have briefly covered many aspects of language design And there are many more factors we could talk about in making choices of language Often a single project can use several languages, each suited to its part of the project And then the interopability of languages becomes important For example, can you easily join together code written in Java and C? The End Or languages And then the interopability of languages becomes important For example, can you easily join together code written in Java and C? The End Or languages Often a single project can use several languages, each suited to its part of the project For example, can you easily join together code written in Java and C? The End Or languages Often a single project can use several languages, each suited to its part of the project And then the interopability of languages becomes important The End Or languages Often a single project can use several languages, each suited to its part of the project And then the interopability of languages becomes important For example, can you easily -

Autoitx Help File
'X' v3.3.14.2 ©1999-2015 Jonathan Bennett & AutoIt Team AutoIt v3 Homepage Introduction AutoIt v3 is a freeware BASIC-like scripting language designed for automating the Windows GUI. It uses a combination of simulated keystrokes, mouse movement and window/control manipulation in order to automate tasks in a way not possible or reliable with other languages (e.g. VBScript and SendKeys). AutoItX is a DLL version of AutoIt v3 that provides a subset of the features of AutoIt via an ActiveX/COM and DLL interface. This means that you can add AutoIt-like features to your favourite scripting and programming languages, e.g. VB, VBScript, Delphi, C, C++, Kixtart, and most other languages that support the use of DLLs. As AutoItX provides a subset of the features of AutoIt v3 you should read the help file for AutoIt v3 and become familar with the basic concepts, including: The AutoIt Window Info Tool Windows Controls Help pages on the above topics are duplicated in this help file for reference. The original version of AutoIt came with two controls: AutoItX (a COM/ActiveX control) and AutoItDLL (a DLL control). In this new version both the COM and DLL versions have been combined into the single AutoItX control which provides both methods of access. How you use AutoItX depends on the host language you want to use. If you are using something that supports COM object access (like VBScript) then using AutoItX as a COM control is recommended. If you want to use AutoItX from a language such as C then using it as a DLL is simplest. -

Manual for Cortex-Based Alignment in Brainvoyager Via Autoit
Manual for automated Cortex-Based Alignment in BrainVoyager QX via AutoIt 3 Manual for automated Cortex-Based Alignment ................................................... 1 in BrainVoyager QX via AutoIt 3 ............................................................................ 1 Introduction ............................................................................................................................. 2 Overview ............................................................................................................................................ 2 Background .................................................................................................................... 2 Versions .............................................................................................................................................. 2 Installation of AutoIt .................................................................................................................. 3 Installation of script ........................................................................................................................ 3 Usage .................................................................................................................................................... 4 Running the cortex-based alignment script .......................................................................... 4 About... .................................................................................................................................................. -
Online Appendices to WFH Productivity in Open-Source Projects
Online Appendices ”WFH Productivity in Open-Source Projects” Lucas Shen (March 2021) Figure A1: Largest countries in sample Notes. Sample size by country, in descending order. Panel (a) sorts countries by number of commits per user-repository. Panel (b) sorts countries by number of user-repository. 1 Figure A2: US states (by Commits) Notes. US sample size by states, in descending order. States sorted by number of commits per user-repository. Figure A3: US states (by Users & Repositories) Notes. US sample size by states, in descending order. States sorted by number user-repository. 2 (a) Staggered Timing in County-level Business Closures (b) County-level Variation in Sample Sizes Figure A4: Geographical Variation in US sample Notes—Panel (a) plots the county-level variation in business closures from the US-state level records and crowdsourced county-level records. Blue indicates earlier closures, while red indicates later closures. South Dakota is (still) the sole state without closure at the time of writing. Panel (b) plots the geographic variation of commits from geocoded U.S. users—larger markers indicate larger activity in the sample period. 3 (a) Early response (by 15 Feb) (b) Intermediate response (by 17 Mar) (c) Late response (by 30 Apr) Figure A5: Country variation in WFH enforcement Notes. Figure plots the variation in government-enforced WFH levels during the COVID-19 pandemic. WFH indicators come from the OxCGRT (?). 4 (a) Early response (by 15 Feb) (b) Intermediate response (by 17 Mar) (c) Late response (by 30 Apr) Figure A6: U.S. states variation in WFH enforcement Notes. Figure plots the U.S. -

Mcafee Threats Report: Second Quarter 2009 by Mcafee® Avert® Labs Report Mcafee Threats Report: Second Quarter 2009
Report McAfee Threats Report: Second Quarter 2009 By McAfee® Avert® Labs Report McAfee Threats Report: Second Quarter 2009 Table of Contents Spam Bounces Back 3 New Zombies 4 New Zombies by Country 4 Spam by Country 5 Spam by Subject 6 Web Attacks Change Target 6 Coming From a Home Near You 9 Malware and PUPs 10 Web 2.0 and Twitter 11 Hacktivism Returns 14 Phishing 15 Malware: the Face of Cybercrime 16 Password-Stealing Trojans Grow Rapidly 16 Zeus 17 Crimeware as a Service 19 AutoRun Malware 21 About McAfee Avert Labs 24 About McAfee, Inc. 24 Report McAfee Threats Report: Second Quarter 2009 The McAfee Threats Report brings you the latest in statistics and analysis covering email- and web- based threats. This quarterly report has been created by the researchers at McAfee Avert Labs, whose worldwide staff provides a unique perspective of the threat landscape—ranging from consumers to enterprises, and from the United States to countries around the world. Join us now as we examine the leading security issues of the past three months. Once you’ve finished here, you can find more information at the McAfee Threat Center.1 You’ll also find our first-quarter Threats Report.2 In the second quarter of 2009, we saw spam production recover quickly from a recent setback and grow to record levels. Zombies, computers hijacked by spammers to send messages, also reached record numbers. We break down spam output by country and subject. On the web, malware on both legitimate and malicious sites continues to exploit browsers. -

Vbscript Dllcall Using Dynawrap COM Library Using the Dynamicwrapper Object Registration Free COM Objects
VBScript DLLCall using DynaWrap COM Library https://www.drdobbs.com/windows/an-automation-object-for-dynamic-dll-cal/210200078 Using the DynamicWrapper Object The DynaWrapper Object can be accessed as a COM Library after registering it. Using REGSVR32, but keep in mind that this Library is a 32Bit only ! So you need to use the "C:\Windows\SysWOW64\regsvr32.exe" command to start going. In VbScript you can access the COM object like this : Dim UserWrap As Object Set UserWrap = CreateObject("DynamicWrapper") To make the library portable I created this manifest file so you don’t have to register it on each PC or Server where you want to run the scripts Registration Free COM Objects Registration Free COM Objects technology is native part of the Windows OS since Windows XP. It uses Manifest files to make the magic to work… This is the dynwrap.sxs.manifest file to use : <?xml version="1.0" encoding="UTF-8" standalone="yes"?> <assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0"> <assemblyIdentity type="win32" name="dynwrap.sxs" version="1.0.0.0" /> <file name="dynwrap.dll"> <comClass description="dynwrap.dll" clsid="{202774D1-D479-11d1-ACD1-00A024BBB05E}" threadingModel="Apartment" progid="DynamicWrapper"/> </file> </assembly> The Manifest file is included in the ZIP file for download. VBScript DLLCall using DynaWrap COM Library Initiating the RegFree COM Objects in VBScripts You can access the COM Library RegFree methods and Properties like this : Option Explicit ' USE 32Bit SysWOW64 script host only !!! Dim fso, objShell, -

Contents in This Issue
APRIL 2014 Covering the global threat landscape CONTENTS IN THIS ISSUE 2 COMMENT THE END OF AN ERA – THE START Threat intelligence sharing: tying one hand OF A NEW CHAPTER behind our backs Momentous changes are in the pipeline for VB – with an exciting future ahead. Helen Martin 3 ANNOUNCEMENT announces the changes that are in store for the The shape of things to come publication and the company. page 3 MALWARE ANALYSES CHINKS IN THE ARMOUR 4 The curse of Necurs, part 1 The Necurs rootkit is composed of a kernel-mode 6 More fast or more dirty? driver and a user-mode component. The rootkit 10 Tofsee botnet makes use of some very powerful techniques, but fortunately it also has some chinks in its armour. Peter Ferrie describes its strengths and weaknesses. 14 TECHNICAL FEATURE page 4 Back to VBA FILLING THE GAP 22 COMMENTARY Last month’s issue of Virus Bulletin featured a Is the IT security industry up to the new detailed analysis of the Polarbot (a.k.a. Solarbot) challenges to come? trojan. The article covered just about everything you could ever want to know about it – except for one 24 SPOTLIGHT thing: how does a computer end up being infected with this creation? Gabor Szappanos fi lls the gap Greetz from academe: no place to Hyde by detailing one of the infi ltration methods that was used extensively in the attack. 25 END NOTES & NEWS page 14 ISSN 1749-7027 COMMENT ‘We will need to and technical barriers, as well as lack of interest from cybersecurity stakeholders.