Vbscript Dllcall Using Dynawrap COM Library Using the Dynamicwrapper Object Registration Free COM Objects
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Blue Coat SGOS Command Line Interface Reference, Version 4.2.3
Blue Coat® Systems ProxySG™ Command Line Interface Reference Version SGOS 4.2.3 Blue Coat ProxySG Command Line Interface Reference Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/contact.html [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™, RA Connector™, RA Manager™, Remote Access™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, The Ultimate Internet Sharing Solution®, Permeo®, Permeo Technologies, Inc.®, and the Permeo logo are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

Your Guide to Installing and Using Coastal Explorer EXPLORING COASTAL EXPLORER Version 4
EXPLORING COASTAL EXPLORER Your guide to installing and using Coastal Explorer EXPLORING COASTAL EXPLORER Version 4 Your guide to installing and using Coastal Explorer Copyright © 2017 Rose Point Navigation Systems. All rights reserved. Rose Point Navigation Systems, Coastal Explorer, and Coastal Explorer Network are trademarks of Rose Point Navigation Systems. The names of any other companies and/or products mentioned herein may be the trademarks of their respective owners. WARNINGS: Use Coastal Explorer at your own risk. Be sure to carefully read and understand the user's manual and practice operation prior to actual use. Coastal Explorer depends on information from the Global Position System (GPS) and digital charts, both of which may contain errors. Navigators should be aware that GPS- derived positions are often of higher accuracy than the positions of charted data. Rose Point Navigation Systems does not warrant the accuracy of any information presented by Coastal Explorer. Coastal Explorer is intended to be used as a supplementary aid to navigation and must not be considered a replacement for official government charts, notices to mariners, tide and current tables, and/or other reference materials. The captain of a vessel is ultimately responsible for its safe navigation and the prudent mariner does not rely on any single source of information. The information in this manual is subject to change without notice. Rose Point Navigation Systems 18005 NE 68th Street Suite A100 Redmond, WA 98052 Phone: 425-605-0985 Fax: 425-605-1285 e-mail: [email protected] www.rosepoint.com Welcome to Coastal Explorer Thank you for choosing Coastal Explorer! If you are new to navigation software, but use a computer for anything else, you will find that Coastal Explorer works just like many other Windows applications: you create documents, edit them, save them, print them, etc. -

VNC User Guide 7 About This Guide
VNC® User Guide Version 5.3 December 2015 Trademarks RealVNC, VNC and RFB are trademarks of RealVNC Limited and are protected by trademark registrations and/or pending trademark applications in the European Union, United States of America and other jursidictions. Other trademarks are the property of their respective owners. Protected by UK patent 2481870; US patent 8760366 Copyright Copyright © RealVNC Limited, 2002-2015. All rights reserved. No part of this documentation may be reproduced in any form or by any means or be used to make any derivative work (including translation, transformation or adaptation) without explicit written consent of RealVNC. Confidentiality All information contained in this document is provided in commercial confidence for the sole purpose of use by an authorized user in conjunction with RealVNC products. The pages of this document shall not be copied, published, or disclosed wholly or in part to any party without RealVNC’s prior permission in writing, and shall be held in safe custody. These obligations shall not apply to information which is published or becomes known legitimately from some source other than RealVNC. Contact RealVNC Limited Betjeman House 104 Hills Road Cambridge CB2 1LQ United Kingdom www.realvnc.com Contents About This Guide 7 Chapter 1: Introduction 9 Principles of VNC remote control 10 Getting two computers ready to use 11 Connectivity and feature matrix 13 What to read next 17 Chapter 2: Getting Connected 19 Step 1: Ensure VNC Server is running on the host computer 20 Step 2: Start VNC -

Automated Malware Analysis Report for Oldnewexplorercfg.Exe
ID: 152305 Sample Name: OldNewExplorerCfg.exe Cookbook: default.jbs Time: 03:48:12 Date: 15/07/2019 Version: 26.0.0 Aquamarine Table of Contents Table of Contents 2 Analysis Report OldNewExplorerCfg.exe 5 Overview 5 General Information 5 Detection 5 Confidence 6 Classification 6 Analysis Advice 6 Mitre Att&ck Matrix 7 Signature Overview 7 AV Detection: 7 Spreading: 7 Networking: 7 Key, Mouse, Clipboard, Microphone and Screen Capturing: 7 DDoS: 8 System Summary: 8 Data Obfuscation: 8 Hooking and other Techniques for Hiding and Protection: 8 Malware Analysis System Evasion: 8 Anti Debugging: 8 HIPS / PFW / Operating System Protection Evasion: 8 Language, Device and Operating System Detection: 8 Behavior Graph 9 Simulations 9 Behavior and APIs 9 Antivirus and Machine Learning Detection 9 Initial Sample 9 Dropped Files 9 Unpacked PE Files 9 Domains 10 URLs 10 Yara Overview 10 Initial Sample 10 PCAP (Network Traffic) 10 Dropped Files 10 Memory Dumps 10 Unpacked PEs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 10 Dropped Files 10 Screenshots 10 Thumbnails 11 Startup 11 Created / dropped Files 12 Domains and IPs 12 Contacted Domains 12 URLs from Memory and Binaries 12 Contacted IPs 12 Static File Info 12 General 12 File Icon 13 Static PE Info 13 General 13 Entrypoint Preview 13 Data Directories 14 Sections 14 Copyright Joe Security LLC 2019 Page 2 of 27 Resources 14 Imports 15 Version Infos 16 Possible Origin 16 Network Behavior 17 Code Manipulations 17 Statistics 17 Behavior 17 System Behavior 17 Analysis Process: -

Implementation of Clipboard Security Using Cryptographic Techniques
International Journal of Computer Applications (0975 – 8887) Volume 86 – No 6, January 2014 Implementation of Clipboard Security using Cryptographic Techniques Gaurav Pathak Gaurav Kumar Tak Department of Computer Department of Computer Science and Engineering Science and Engineering Lovely Professional University Lovely Professional University Phagwara, India Phagwara, India ABSTRACT looking malicious content. So security to clipboard content is In the present scenario malicious authors are rapidly growing issue of concern and need to enhance the functionality of and now other than internet users they are also targeting the operating system by which we can protect our clipboard data loophole in operating system application level security. from being got watched. Transferring data between applications is common user From the study of recent papers and market reports, clipboard activity. Since data in a clipboard is freely delivered between security becomes important issue of concern in data security. arbitrary programs capable of using a format of the data, a According to the google forum [6] there is being the great simple text, a rich text, a picture, and information having a threat to the clipboard security in which they talk about particular format may be delivered between programs capable ClipNote that can monitor the system clipboard of using such information. Information delivery made and collect all clipboard entries. That ClipNote application between programs through a clipboard is undoubtedly an does not require any special permission to run. That means efficient method of properly using a multitasking function of any malware can steal passwords by just monitoring the an operating system, but as the security of important data is system clipboard in the background, which become great increasingly demanded, data transmitted between independent threat to the client’s system. -

Gotomypc® User Guide
GoToMyPC® User Guide GoToMyPC GoToMyPC Pro GoToMyPC Corporate Citrix Online 6500 Hollister Avenue • Goleta CA 93117 +1-805-690-6400 • Fax: +1-805-690-6471 © 2009 Citrix Online, LLC. All rights reserved. GoToMyPC® User Guide Contents Welcome ........................................................................................... 4 Getting Started .................................................................................. 1 System Requirements ....................................................................... 1 Notes on Installation and Feature Access ............................................. 1 Versions of GoToMyPC ...................................................................... 1 Mac Users .................................................................................... 1 Upgrade Information ......................................................................... 2 Useful GoToMyPC Terms .................................................................... 4 Features ......................................................................................... 5 Set Up a Host Computer .................................................................... 6 Create Your Account (first-time users) .............................................. 6 Set Up a Host PC ........................................................................... 7 Leaving the Host Computer Accessible................................................. 8 Managing Billing and Account Information ........................................ 9 Change Your -

Autocoding Methods for Networked Embedded Systems
University of Warwick institutional repository: http://go.warwick.ac.uk/wrap A Thesis Submitted for the Degree of PhD at the University of Warwick http://go.warwick.ac.uk/wrap/36892 This thesis is made available online and is protected by original copyright. Please scroll down to view the document itself. Please refer to the repository record for this item for information to help you to cite it. Our policy information is available from the repository home page. Innovation Report AUTOCODING METHODS FOR NETWORKED EMBEDDED SYSTEMS Submitted in partial fulfilment of the Engineering Doctorate By James Finney, 0117868 November 2009 Academic Supervisors: Dr. Peter Jones, Ross McMurran Industrial Supervisor: Dr. Paul Faithfull Declaration I have read and understood the rules on cheating, plagiarism and appropriate referencing as outlined in my handbook and I declare that the work contained in this submission is my own, unless otherwise acknowledged. Signed: …………………………………………………………………….James Finney ii Acknowledgements I would like to thank Rapicore Ltd and the EPSRC for funding this project. I would also like to offer special thanks to my supervisors: Dr. R.P. Jones, Dr. P. Faithfull, and R. McMurran, for their time, support, and guidance throughout this project. iii Table of Contents Declaration ....................................................................................................................... ii Acknowledgements ......................................................................................................... iii Figures -

Cheatsheet V2.4.Pdf
! ! 2.4!Edition! Cross!reference!processes!with!various!lists:! Scan!a!block!of!code!in!process!or!kernel!memory! psxview! for!imported!APIs:! ! impscan!! Show!processes!in!parent/child!tree:! !!!!Hp/HHpid=PID!!!!!!!!!Process!ID!! pstree! !!!!Hb/HHbase=BASE!!!Base!address!to!scan! & !!!!Hs/HHsize=SIZE!!!!!!!Size!to!scan!from!start!of!base! Process&Information& ! ! Logs&/&Histories& Specify!–o/HHoffset=OFFSET!or!Hp/HHpid=1,2,3!! ! ! Recover!event!logs!(XP/2003):! Display!DLLs:! evtlogs!! ! ! dlllist! !!!!HS/HHsaveHevt!!!!!!!!!!!!!!!!!!!!Save!raw!event!logs! Development!build!and!wiki:! ! !!!!HD/HHdumpHdir=PATH!!!Write!to!this!directory! github.com/volatilityfoundation!! Show!command!line!arguments:! ! ! cmdline! Recover!command!history:! Download!a!stable!release:! ! cmdscan!and!consoles!! volatilityfoundation.org!! Display!details!on!VAD!allocations:! ! ! vadinfo![HHaddr]! Recover!IE!cache/Internet!history:! Read!the!book:! ! iehistory!! artofmemoryforensics.com! Dump!allocations!to!individual!files:! ! ! vaddump!HHdumpHdir=PATH![HHbase]! Show!running!services:! Development!Team!Blog:! ! svcscan!! http://volatilityHlabs.blogspot.com!! Dump!all!valid!pages!to!a!single!file:! !!!!Hv/HHverbose!!!!Show!ServiceDll!from!registry! ! memdump!HHdumpHdir=PATH! ! (Official)!Training!Contact:! ! Networking&Information& Display!open!handles:! [email protected]!! ! handles!! ! Active!info!(XP/2003):! !!!!Ht/HHobjectHtype=TYPE!!!Mutant,!File,!Key,!etc…! Follow:!@volatility! connections!and!sockets!! !!!!Hs/HHsilent!!!!!!!!!!!!!!!!!!!!!!!!!!!Hide!unnamed!handles! -

Secrets of Powershell Remoting
Secrets of PowerShell Remoting The DevOps Collective, Inc. This book is for sale at http://leanpub.com/secretsofpowershellremoting This version was published on 2018-10-28 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. © 2016 - 2018 The DevOps Collective, Inc. Also By The DevOps Collective, Inc. Creating HTML Reports in Windows PowerShell A Unix Person’s Guide to PowerShell The Big Book of PowerShell Error Handling DevOps: The Ops Perspective Ditch Excel: Making Historical and Trend Reports in PowerShell The Big Book of PowerShell Gotchas The Monad Manifesto, Annotated Why PowerShell? Windows PowerShell Networking Guide The PowerShell + DevOps Global Summit Manual for Summiteers Why PowerShell? (Spanish) Secrets of PowerShell Remoting (Spanish) DevOps: The Ops Perspective (Spanish) The Monad Manifesto: Annotated (Spanish) Creating HTML Reports in PowerShell (Spanish) The Big Book of PowerShell Gotchas (Spanish) The Big Book of PowerShell Error Handling (Spanish) DevOps: WTF? PowerShell.org: History of a Community Contents Secrets of PowerShell Remoting ..................................... 1 Remoting Basics ................................................ 3 What is Remoting? ............................................ 3 Examining Remoting Architecture .................................. 3 Enabling -

A Bibliography of O'reilly & Associates and O
A Bibliography of O'Reilly & Associates and O'Reilly Media. Inc. Publishers Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 08 February 2021 Version 3.67 Title word cross-reference #70 [1263, 1264]. #70-059 [1263]. #70-068 [1264]. 2 [949]. 2 + 2 = 5986 [1456]. 3 [1149, 1570]. *# [1221]. .Mac [1940]. .NET [1860, 22, 186, 342, 441, 503, 591, 714, 716, 721, 730, 753, 786, 998, 1034, 1037, 1038, 1043, 1049, 1089, 1090, 1091, 1119, 1256, 1468, 1858, 1859, 1863, 1899, 1900, 1901, 1917, 1997, 2029]. '05 [461, 1532]. 08 [1541]. 1 [1414]. 1.0 [1009]. 1.1 [59]. 1.2 [1582]. 1000 [1511]. 1000D [1073]. 10g [711, 710]. 10th [2109]. 11 [1385]. 1 2 2 [53, 209, 269, 581, 2134, 919, 940, 1515, 1521, 1530, 2023, 2045]. 2.0 [2, 55, 203, 394, 666, 941, 1000, 1044, 1239, 1276, 1504, 1744, 1801, 2073]. 2.1 [501]. 2.2 [201]. 2000 [38, 202, 604, 610, 669, 927, 986, 1087, 1266, 1358, 1359, 1656, 1751, 1781, 1874, 1959, 2069]. 2001 [96]. 2003 [70, 71, 72, 73, 74, 279, 353, 364, 365, 789, 790, 856, 987, 1146, 1960, 2026]. 2003-2013 [1746]. 2004 [1195]. 2005 [84, 151, 755, 756, 1001, 1041, 1042, 1119, 1122, 1467, 2120, 2018, 2056]. 2006 [152, 153]. 2007 [618, 726, 727, 728, 1123, 1125, 1126, 1127, 2122, 1973, 1974, 2030]. -
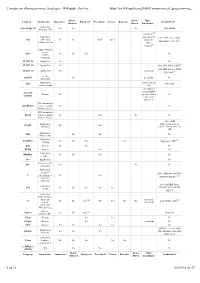
Comparison of Programming Languages - Wikipedia, the Free
Comparison of programming languages - Wikipedia, the free ... https://en.wikipedia.org/wiki/Comparison_of_programming_... Object- Event- Other Language Intended use Imperative Functional Procedural Generic Reflective Standardized? Oriented Driven Paradigm(s) Application, ActionScript 3.0 Yes Yes Yes 1996, ECMA client-side, Web concurrent,[4] [5] Application, distributed, 1983, 2005, 2012, ANSI, Ada embedded, Yes Yes Yes[2] Yes[3] imperative ISO, GOST 27831-88[7] realtime, system object- oriented[6] Highly domain- specific, Aldor Yes Yes Yes No symbolic computing ALGOL 58 Application Yes No ALGOL 60 Application Yes 1960, IFIP WG 2.1, ISO[8] 1968, IFIP WG 2.1, GOST ALGOL 68 Application Yes concurrent 27974-88,[9] Parallel Ateji PX Yes pi calculus No application Application, array-oriented, APL 1989, ISO data processing tacit any, syntax is usually highly Assembly General Yes specific, related No language to the target processor GUI automation AutoHotkey (macros), highly Yes No domain-specific GUI automation AutoIt (macros), highly Yes Yes Yes No domain-specific 1983, ANSI Application, (http://portal.acm.org BASIC Yes Yes education /citation.cfm?id=988221), ISO Application, BBj Yes Yes No business, Web Application, BeanShell Yes Yes Yes Yes [10] scripting In progress, JCP BitC System Yes Yes No BLISS System Yes No Application, BlitzMax Yes Yes Yes No game Boo Application No domain-specific, Bro Yes Yes No application Application, [11] system, 1989, ANSI C89, ISO C90, C general purpose, Yes Yes ISO C99, ISO C11[12] low-level operations 1998, ISO/IEC