GOOGLE LLC V. ORACLE AMERICA, INC
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Valley & Spruce Project Initial Study and Mitigated
VALLEY & SPRUCE PROJECT INITIAL STUDY AND MITIGATED NEGATIVE DECLARATION Prepared for: City of Rialto December 2017 VALLEY & SPRUCE PROJECT INITIAL STUDY AND MITIGATED NEGATIVE DECLARATION Prepared For: City of Rialto 150 S. Palm Avenue Rialto, CA 92376 Prepared By: Kimley-Horn and Associates, Inc. 401 B Street, Suite 600 San Diego, California 92101 December 2017 095894012 Copyright © 2017 Kimley-Horn and Associates, Inc. TABLE OF CONTENTS I. Initial Study ............................................................................................................................................ 1 II. Description of Proposed Project ........................................................................................................... 2 III. Required Permits ................................................................................................................................... 8 IV. Environmental Factors Potentially Affected ......................................................................................... 9 V. Determination ........................................................................................................................................ 9 VI. Environmental Evaluation .................................................................................................................. 10 1. Aesthetics ................................................................................................................................ 10 2. Agricultural and Forestry Resources ..................................................................................... -
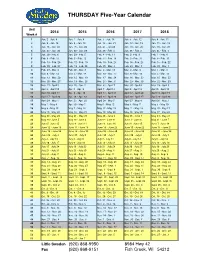
Thursday Calendar 20142018
THURSDAY Five-Year Calendar Unit 2014 20152016 2017 2018 Week # 1 Jan. 2 - Jan. 9 Jan. 1 - Jan. 8 Jan. 7 - Jan. 14 Jan. 5 - Jan. 12 Jan. 4 - Jan. 11 2 Jan. 9 - Jan. 16 Jan. 8 - Jan. 15 Jan. 14 - Jan. 21 Jan. 12 - Jan. 19 Jan. 11 - Jan. 18 3 Jan. 16 - Jan. 23 Jan. 15 - Jan. 22 Jan. 21 - Jan 28 Jan. 19 - Jan. 26 Jan. 18 - Jan. 25 4 Jan. 23 - Jan. 30 Jan. 22 - Jan. 29 Jan. 28 - Feb. 4 Jan. 26 - Feb. 2 Jan. 25 - Feb. 1 5 Jan. 30 - Feb. 6 Jan. 29 - Feb. 5 Feb. 4 - Feb. 11 Feb. 2- Feb. 9 Feb. 1 - Feb. 8 6 Feb. 6 - Feb. 13 Feb. 5 - Feb. 12 Feb. 11 - Feb. 18 Feb. 9 - Feb. 16 Feb. 8 - Feb. 15 7 Feb. 13 - Feb. 20 Feb. 12 - Feb. 19 Feb. 18 - Feb. 25 Feb. 16 - Feb. 23 Feb. 15 - Feb. 22 8 Feb. 20 - Feb. 27 Feb. 19 - Feb. 26 Feb. 25 - Mar. 3 Feb. 23 - Mar. 2 Feb. 22 - Mar. 1 9 Feb. 27 - Mar. 6 Feb. 26 - Mar. 5 Mar. 3 - Mar. 10 Mar. 2 - Mar. 9 Mar. 1 - Mar. 8 10 Mar. 6 - Mar. 13 Mar. 5 - Mar. 12 Mar. 10 - Mar. 17 Mar. 9 - Mar. 16 Mar. 5 - Mar. 15 11 Mar. 13 - Mar. 20 Mar. 12 - Mar. 19 Mar. 17 - Mar. 24 Mar. 16 - Mar. 23 Mar. 15 - Mar. 22 12 Mar. 20 - Mar. 27 Mar. 19 - Mar. 26 Mar. 24 - Mar. 31 Mar. 23 - Mar. 30 Mar. 22 - Mar. -
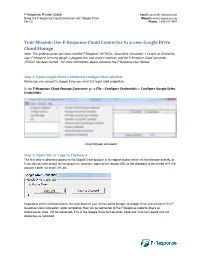
Use F-Response Cloud Connector to Access Google Drive Cloud Storage
F-Response Mission Guide Email:[email protected] Using the F-Response Cloud Connector with Google Drive Website:www.f-response.com Rev 1.0 Phone: 1-800-317-5497 Your Mission: Use F-Response Cloud Connector to access Google Drive Cloud Storage Note: This guide assumes you have installed F-Response TACTICAL, Consultant, Consultant + Covert, or Enterprise, your F-Response licensing dongle is plugged into your analyst machine, and the F-Response Cloud Connector (FCLDC) has been started. For more information, please reference the F-Response User Manual. Step 1: Open Google Drive Credential Configuration window Before you can connect to Google Drive you must first input valid credentials. In the F-Response Cloud Storage Connector go to File->Configure Credentials-> Configure Google Drive Credentials. Cloud Storage Connector Step 2: Open URL or Copy to Clipboard The first step in obtaining access to the Google Drive account is to request access either via the browser directly, or if you do not have access to the account in question, copying the request URL to the clipboard to be shared with the account holder via email, IM, etc. Regardless of the method chosen, the web browser user will be asked to login to Google Drive and authorize the F- Response Cloud Connector, upon completion they will be redirected to the F-Response website where an Authorization code will be presented. This is the Google Drive Authorization Code and must be inputed into the dialog box as indicated: F-Response Mission Guide Email:[email protected] Using the F-Response Cloud Connector with Google Drive Website:www.f-response.com Rev 1.0 Phone: 1-800-317-5497 Press Validate Access and the dialog will now present the User Account name, UID, and additional details in the Confirm Account section. -

Intro to Google for the Hill
Introduction to A company built on search Our mission Google’s mission is to organize the world’s information and make it universally accessible and useful. As a first step to fulfilling this mission, Google’s founders Larry Page and Sergey Brin developed a new approach to online search that took root in a Stanford University dorm room and quickly spread to information seekers around the globe. The Google search engine is an easy-to-use, free service that consistently returns relevant results in a fraction of a second. What we do Google is more than a search engine. We also offer Gmail, maps, personal blogging, and web-based word processing products to name just a few. YouTube, the popular online video service, is part of Google as well. Most of Google’s services are free, so how do we make money? Much of Google’s revenue comes through our AdWords advertising program, which allows businesses to place small “sponsored links” alongside our search results. Prices for these ads are set by competitive auctions for every search term where advertisers want their ads to appear. We don’t sell placement in the search results themselves, or allow people to pay for a higher ranking there. In addition, website managers and publishers take advantage of our AdSense advertising program to deliver ads on their sites. This program generates billions of dollars in revenue each year for hundreds of thousands of websites, and is a major source of funding for the free content available across the web. Google also offers enterprise versions of our consumer products for businesses, organizations, and government entities. -

Jational Register of Historic Places Inventory -- Nomination Form
•m No. 10-300 REV. (9/77) UNITED STATES DEPARTMENT OF THE INTERIOR NATIONAL PARK SERVICE JATIONAL REGISTER OF HISTORIC PLACES INVENTORY -- NOMINATION FORM SEE INSTRUCTIONS IN HOW TO COMPLETE NATIONAL REGISTER FORMS ____________TYPE ALL ENTRIES -- COMPLETE APPLICABLE SECTIONS >_____ NAME HISTORIC BROADWAY THEATER AND COMMERCIAL DISTRICT________________________ AND/OR COMMON LOCATION STREET & NUMBER <f' 300-8^9 ^tttff Broadway —NOT FOR PUBLICATION CITY. TOWN CONGRESSIONAL DISTRICT Los Angeles VICINITY OF 25 STATE CODE COUNTY CODE California 06 Los Angeles 037 | CLASSIFICATION CATEGORY OWNERSHIP STATUS PRESENT USE X.DISTRICT —PUBLIC ^.OCCUPIED _ AGRICULTURE —MUSEUM _BUILDING(S) —PRIVATE —UNOCCUPIED .^COMMERCIAL —PARK —STRUCTURE .XBOTH —WORK IN PROGRESS —EDUCATIONAL —PRIVATE RESIDENCE —SITE PUBLIC ACQUISITION ACCESSIBLE ^ENTERTAINMENT _ REUGIOUS —OBJECT _IN PROCESS 2L.YES: RESTRICTED —GOVERNMENT —SCIENTIFIC —BEING CONSIDERED — YES: UNRESTRICTED —INDUSTRIAL —TRANSPORTATION —NO —MILITARY —OTHER: NAME Multiple Ownership (see list) STREET & NUMBER CITY. TOWN STATE VICINITY OF | LOCATION OF LEGAL DESCRIPTION COURTHOUSE. REGISTRY OF DEEDSETC. Los Angeie s County Hall of Records STREET & NUMBER 320 West Temple Street CITY. TOWN STATE Los Angeles California ! REPRESENTATION IN EXISTING SURVEYS TiTLE California Historic Resources Inventory DATE July 1977 —FEDERAL ^JSTATE —COUNTY —LOCAL DEPOSITORY FOR SURVEY RECORDS office of Historic Preservation CITY, TOWN STATE . ,. Los Angeles California DESCRIPTION CONDITION CHECK ONE CHECK ONE —EXCELLENT —DETERIORATED —UNALTERED ^ORIGINAL SITE X.GOOD 0 —RUINS X_ALTERED _MOVED DATE- —FAIR _UNEXPOSED DESCRIBE THE PRESENT AND ORIGINAL (IF KNOWN) PHYSICAL APPEARANCE The Broadway Theater and Commercial District is a six-block complex of predominately commercial and entertainment structures done in a variety of architectural styles. The district extends along both sides of Broadway from Third to Ninth Streets and exhibits a number of structures in varying condition and degree of alteration. -
Google Apps Premier Edition: Easy, Collaborative Workgroup Communication with Gmail and Google Calendar
Google Apps Premier Edition: easy, collaborative workgroup communication with Gmail and Google Calendar Messaging overview Google Apps Premier Edition messaging tools include email, calendar and instant messaging solutions that help employees communicate and stay connected, wherever and whenever they work. These web-based services can be securely accessed from any browser, work on mobile devices like BlackBerry and iPhone, and integrate with other popular email systems like Microsoft Outlook, Apple Mail, and more. What’s more, Google Apps’ SAML-based Single Sign-On (SSO) capability integrates seamlessly with existing enterprise security and authentication services. Google Apps deliver productivity and reduce IT workload with a hosted, 99.9% uptime solution that gets teams working together fast. Gmail Get control of spam Advanced filters keep spam from employees’ inboxes so they can focus on messages that matter, and IT admins can focus on other initiatives. Keep all your email 25 GB of storage per user means that inbox quotas and deletion schedules are a thing of the past. Integrated instant messaging Connect with contacts instantly without launching a separate application or leaving your inbox. No software required. Built-in voice and video chat Voice and video conversations, integrated into Gmail, make it easy to connect face-to-face with co-workers around the world. Find messages instantly Powerful Google search technology is built into Gmail, turning your inbox into your own private and secure Google search engine for email. Protect and secure sensitive information Additional spam filtering from Postini provides employees with an additional layer of protection and policy-enforced encryption between domains using standard TLS protocols. -

Chromebooks for Education
Chromebooks for Education Chromebooks for Education include • Chromebook computers • Cloud-based management console • Ongoing support from Google • 3 year hardware warranty Pricing Chromebooks for Education start at $20/Chromebook per month For more information, visit: google.com/chromebook/education Chromebooks for Education give students, teachers, and administrators a simple solution for fast, intuitive, and easy-to-manage computing. Chromebooks provide access to the web’s education and collaboration resources, as well as off er centralized management and low total cost of ownership. Using Chromebooks, teachers spend more time teaching and less time managing classroom technology, and schools can deploy more computers into the hands of their students and teachers. “ From the day the students got the Chromebooks, they could maneuver around. It’s pretty simple. Individual learning at their own pace.” —Zach Fleming, Teacher, Crook County Middle School At home in the classroom (and beyond) Chromebooks provide the teaching and learning benefi ts of computers without the typical distractions that come with technology in the classroom. They “ We don’t have to worry about installing boot in 8 seconds and resume instantly – eliminating the time wasted while software or doing updates and imaging. traditional computers start up and connect to a network. Long battery life It’s just plug and play, it’s amazing!” —Bruce Hahn, Technology Coordinator, means Chromebooks last an entire school day. And since it’s easy to connect Crook County School District, Prineville OR a Chromebook anytime and anywhere with built-in Wi-Fi and optional 3G, students can continue learning after school and at home. -

Songs by Artist
Reil Entertainment Songs by Artist Karaoke by Artist Title Title &, Caitlin Will 12 Gauge Address In The Stars Dunkie Butt 10 Cc 12 Stones Donna We Are One Dreadlock Holiday 19 Somethin' Im Mandy Fly Me Mark Wills I'm Not In Love 1910 Fruitgum Co Rubber Bullets 1, 2, 3 Redlight Things We Do For Love Simon Says Wall Street Shuffle 1910 Fruitgum Co. 10 Years 1,2,3 Redlight Through The Iris Simon Says Wasteland 1975 10, 000 Maniacs Chocolate These Are The Days City 10,000 Maniacs Love Me Because Of The Night Sex... Because The Night Sex.... More Than This Sound These Are The Days The Sound Trouble Me UGH! 10,000 Maniacs Wvocal 1975, The Because The Night Chocolate 100 Proof Aged In Soul Sex Somebody's Been Sleeping The City 10Cc 1Barenaked Ladies Dreadlock Holiday Be My Yoko Ono I'm Not In Love Brian Wilson (2000 Version) We Do For Love Call And Answer 11) Enid OS Get In Line (Duet Version) 112 Get In Line (Solo Version) Come See Me It's All Been Done Cupid Jane Dance With Me Never Is Enough It's Over Now Old Apartment, The Only You One Week Peaches & Cream Shoe Box Peaches And Cream Straw Hat U Already Know What A Good Boy Song List Generator® Printed 11/21/2017 Page 1 of 486 Licensed to Greg Reil Reil Entertainment Songs by Artist Karaoke by Artist Title Title 1Barenaked Ladies 20 Fingers When I Fall Short Dick Man 1Beatles, The 2AM Club Come Together Not Your Boyfriend Day Tripper 2Pac Good Day Sunshine California Love (Original Version) Help! 3 Degrees I Saw Her Standing There When Will I See You Again Love Me Do Woman In Love Nowhere Man 3 Dog Night P.S. -

Notes on Chromebooks and Neverware Cloudready Chromium
Chromebooks Are For Seniors - Ron Brown - APCUG VTC - 8-19-17 https://youtu.be/4uszFPNL-SU http://cb4s.net/ Are Chromebooks more secure than laptops? Google’s security features in ChromeOS When Google set about designing ChromeOS it had the distinct advantage of being able to see the problems that Windows, macOS, and even Linux had struggled with when it came to security. With this in mind it implemented five key features that make ChromeOS a formidable system for hackers to crack. Automatic Updates As new threats become known, it’s vital that patches are applied quickly to thwart them. Google has an excellent track record on this, as not only does it release fixes on a very regular basis, but with Chromebooks guaranteed OS updates for seven years after release, the majority of users are running the most up to date version anyway. his can be an issue on other platforms, where differing combinations of OS versions and hardware can delay patches. Sandboxing If something does go wrong, and malware gets onto a Chromebook, there’s not much damage it can do. Each tab in ChromeOS acts as a separate entity with a restricted environment or ‘sandbox’. This means that only the affected tab is vulnerable, and that it is very difficult for the infection to spread to other areas of the machine. In Windows and macOS the malware is usually installed somewhere on the system itself, which makes it a threat with a much wider scope. There are ways to restrict this of course, with anti-virus software, regular system scans, and not running as an administrator. -

Text Collection
Gr a de TM 4 Ac GEN b Text Collection Glenview, Illinois • Boston, Massachusetts • Chandler, Arizona • Upper Saddle River, New Jersey Copyright © 2014 Pearson Education, Inc., or its affiliates. All Rights Reserved. Printed in the United States of America. This publication is protected by copyright, and permission should be obtained from the publisher prior to any prohibited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, or likewise. For information regarding permissions, write to Rights Management & Contracts, One Lake Street, Upper Saddle River, New Jersey 07458. ReadyGEN is a trademark, in the U.S. and/or other countries, of Pearson Education, Inc., or its affiliates. Common Core State Standards: © Copyright 2010. National Governors Association Center for Best Practices and Council of Chief State School Officers. All rights reserved. ISBN-13: 978-0-328-78847-7 ISBN-10: 0-328-78847-3 1 2 3 4 5 6 7 8 9 10 V063 17 16 15 14 13 RGEN14_SC4_V2_FM.indd 1 8/14/13 10:16 AM RGEN14_SC4_V2_FM.indd 4 10/15/13 2:46 PM 58 RGEN14_SE4_U4_SchoolNews.indd 58 10/1/13 3:08 PM COYOTE SCHOOL NEWS JOAN SANDIN 59 RGEN14_SE4_U4_SchoolNews.indd 59 10/1/13 3:09 PM Rancho San Isidro My name is Ramón On our ranch we have Ernesto Ramírez, but chickens and pigs and cattle everybody calls me Monchi. I and horses. The boys in the live on a ranch that my great- Ramírez family know how to grandfather built a long time ride and rope. -

Oracle Fusion Middleware Integration Overview for Oracle Identity Management Suite, 11G Release 1 (11.1.1) E15477-01
Oracle® Fusion Middleware Integration Overview for Oracle Identity Management Suite 11g Release 1 (11.1.1) E15477-01 June 2010 Oracle Fusion Middleware Integration Overview for Oracle Identity Management Suite, 11g Release 1 (11.1.1) E15477-01 Copyright © 2010, Oracle and/or its affiliates. All rights reserved. Primary Author: Vinaye Misra Contributing Author: Stephen Lee Contributors: Sidhartha Das, Ellen Desmond, Subbu Devulapalli, Sandy Lii, Kavya Muthanna, Sanjay Rallapalli, Vinay Shukla, Olaf Stullich, Lyju Vadassery, Mark Wilcox This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

Google Data Collection —NEW—
Digital Content Next January 2018 / DCN Distributed Content Revenue Benchmark Google Data Collection —NEW— August 2018 digitalcontentnext.org CONFIDENTIAL - DCN Participating Members Only 1 This research was conducted by Professor Douglas C. Schmidt, Professor of Computer Science at Vanderbilt University, and his team. DCN is grateful to support Professor Schmidt in distributing it. We offer it to the public with the permission of Professor Schmidt. Google Data Collection Professor Douglas C. Schmidt, Vanderbilt University August 15, 2018 I. EXECUTIVE SUMMARY 1. Google is the world’s largest digital advertising company.1 It also provides the #1 web browser,2 the #1 mobile platform,3 and the #1 search engine4 worldwide. Google’s video platform, email service, and map application have over 1 billion monthly active users each.5 Google utilizes the tremendous reach of its products to collect detailed information about people’s online and real-world behaviors, which it then uses to target them with paid advertising. Google’s revenues increase significantly as the targeting technology and data are refined. 2. Google collects user data in a variety of ways. The most obvious are “active,” with the user directly and consciously communicating information to Google, as for example by signing in to any of its widely used applications such as YouTube, Gmail, Search etc. Less obvious ways for Google to collect data are “passive” means, whereby an application is instrumented to gather information while it’s running, possibly without the user’s knowledge. Google’s passive data gathering methods arise from platforms (e.g. Android and Chrome), applications (e.g.