Pico: a Unix Text Editor This Guide Tells You How to Use the Pico Text Editor to Create and Edit Text Files on UITS Unix Computers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

At—At, Batch—Execute Commands at a Later Time
at—at, batch—execute commands at a later time at [–csm] [–f script] [–qqueue] time [date] [+ increment] at –l [ job...] at –r job... batch at and batch read commands from standard input to be executed at a later time. at allows you to specify when the commands should be executed, while jobs queued with batch will execute when system load level permits. Executes commands read from stdin or a file at some later time. Unless redirected, the output is mailed to the user. Example A.1 1 at 6:30am Dec 12 < program 2 at noon tomorrow < program 3 at 1945 pm August 9 < program 4 at now + 3 hours < program 5 at 8:30am Jan 4 < program 6 at -r 83883555320.a EXPLANATION 1. At 6:30 in the morning on December 12th, start the job. 2. At noon tomorrow start the job. 3. At 7:45 in the evening on August 9th, start the job. 4. In three hours start the job. 5. At 8:30 in the morning of January 4th, start the job. 6. Removes previously scheduled job 83883555320.a. awk—pattern scanning and processing language awk [ –fprogram–file ] [ –Fc ] [ prog ] [ parameters ] [ filename...] awk scans each input filename for lines that match any of a set of patterns specified in prog. Example A.2 1 awk '{print $1, $2}' file 2 awk '/John/{print $3, $4}' file 3 awk -F: '{print $3}' /etc/passwd 4 date | awk '{print $6}' EXPLANATION 1. Prints the first two fields of file where fields are separated by whitespace. 2. Prints fields 3 and 4 if the pattern John is found. -

Course Outline & Schedule
Course Outline & Schedule Call US 408-759-5074 or UK +44 20 7620 0033 Linux Advanced Shell Programming Tools Curriculum The Linux Foundation Course Code LASP Duration 3 Day Course Price $1,830 Course Description The Linux Advanced Shell Programming Tools course is designed to give delegates practical experience using a range of Linux tools to manipulate text and incorporate them into Linux shell scripts. The delegate will practise: Using the shell command line editor Backing up and restoring files Scheduling background jobs using cron and at Using regular expressions Editing text files with sed Using file comparison utilities Using the head and tail utilities Using the cut and paste utilities Using split and csplit Identifying and translating characters Sorting files Translating characters in a file Selecting text from files with the grep family of commands Creating programs with awk Course Modules Review of Shell Fundamentals (1 topic) ◾ Review of UNIX Commands Using Unix Shells (6 topics) ◾ Command line history and editing ◾ The Korn and POSIX shells Perpetual Solutions - Page 1 of 5 Course Outline & Schedule Call US 408-759-5074 or UK +44 20 7620 0033 ◾ The Bash shell ◾ Command aliasing ◾ The shell startup file ◾ Shell environment variables Redirection, Pipes and Filters (7 topics) ◾ Standard I/O and redirection ◾ Pipes ◾ Command separation ◾ Conditional execution ◾ Grouping Commands ◾ UNIX filters ◾ The tee command Backup and Restore Utilities (6 topics) ◾ Archive devices ◾ The cpio command ◾ The tar command ◾ The dd command ◾ Exercise: -

HEP Computing Part I Intro to UNIX/LINUX Adrian Bevan
HEP Computing Part I Intro to UNIX/LINUX Adrian Bevan Lectures 1,2,3 [email protected] 1 Lecture 1 • Files and directories. • Introduce a number of simple UNIX commands for manipulation of files and directories. • communicating with remote machines [email protected] 2 What is LINUX • LINUX is the operating system (OS) kernel. • Sitting on top of the LINUX OS are a lot of utilities that help you do stuff. • You get a ‘LINUX distribution’ installed on your desktop/laptop. This is a sloppy way of saying you get the OS bundled with lots of useful utilities/applications. • Use LINUX to mean anything from the OS to the distribution we are using. • UNIX is an operating system that is very similar to LINUX (same command names, sometimes slightly different functionalities of commands etc). – There are usually enough subtle differences between LINUX and UNIX versions to keep you on your toes (e.g. Solaris and LINUX) when running applications on multiple platforms …be mindful of this if you use other UNIX flavours. – Mac OS X is based on a UNIX distribution. [email protected] 3 Accessing a machine • You need a user account you should all have one by now • can then log in at the terminal (i.e. sit in front of a machine and type in your user name and password to log in to it). • you can also log in remotely to a machine somewhere else RAL SLAC CERN London FNAL in2p3 [email protected] 4 The command line • A user interfaces with Linux by typing commands into a shell. -
Geany Tutorial
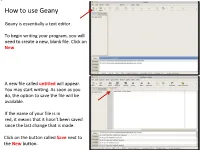
How to use Geany Geany is essentially a text editor. To begin writing your program, you will need to create a new, blank file. Click on New. A new file called untitled will appear. You may start writing. As soon as you do, the option to save the file will be available. If the name of your file is in red, it means that it hasn’t been saved since the last change that is made. Click on the button called Save next to the New button. Save the file in a directory you had previously created before you launched Geany and name it main.cpp. All of the files you will write and submit to will be named specifically main.cpp. Once the .cpp has been specified, Geany will turn on its color coding feature for the C++ template. Next, we will set up our environment and then write a simple program that will print something to the screen Feel free to supply your own name in this small program Before we do anything with it, we will need to configure some options to make your life easier in this class The vertical line to the right marks the ! boundary of your code. You will need to respect this limit in that any line of code you write must not cross this line and therefore be properly, manually broken down to the next line. Your code will be printed out for The line is not where it should be, however, and grading, and if your code crosses the we will now correct it line, it will cause line-wrapping and some points will be deducted. -

Software Tools: a Building Block Approach
SOFTWARE TOOLS: A BUILDING BLOCK APPROACH NBS Special Publication 500-14 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards ] NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the ! Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following center and divisions: Applied Mathematics — Electricity — Mechanics — Heat — Optical Physics — Center for Radiation Research — Lab- oratory Astrophysics^ — Cryogenics^ — Electromagnetics^ — Time and Frequency*. THE INSTITUTE FOR MATERIALS RESEARCH conducts materials research leading to improved methods of measure- ment, standards, and data on the properties of well-characterized materials needed by industry, commerce, educational insti- tutions, and Government; provides advisory and research services to other Government agencies; and develops, produces, and distributes standard reference materials. -

CESM2 Tutorial: Basic Modifications
CESM2 Tutorial: Basic Modifications Christine Shields August 15, 2017 CESM2 Tutorial: Basic Modifications: Review 1. We will use the CESM code located locally on Cheyenne, no need to checkout or download any input data. 2. We will run with resolution f19_g17: (atm/lnd = FV 1.9x2.5 ocn/ice=gx1v7) 3. Default scripts will automatically be configured for you using the code/script base prepared uniquely for this tutorial. 4. For On-site Tutorial ONLY: Please use compute nodes for compiling and login nodes for all other work, including submission. Please do NOT compile unless you have a compile card. To make the tutorial run smoothly for all, we need to regulate the model compiles. When you run from home, you don’t need to compile on the compute nodes. Tutorial Code and script base: /glade/p/cesm/tutorial/cesm2_0_alpha07c/ CESM2 Tutorial: Basic Modifications: Review 1. Log into Cheyenne 2. Execute create_newcase 3. Execute case.setup 4. Log onto compute node (compile_node.csH) 5. Compile model (case.build) 6. Exit compute node (type “exit”) 7. Run model (case.submit) This tutorial contains step by step instructions applicable to CESM2 (wHicH Has not been officially released yet). Documentation: Under construction! http://www.cesm.ucar.edu/models/cesm2.0/ Quick Start Guide: Under construction! http://cesm-development.github.io/cime/doc/build/html/index.Html For older releases, please see past tutorials. CESM2 Tutorial: Basic Modifications: Review: Creating a new case What is the Which Which model configuration ? Which set of components ? casename -

Xshell 6 User Guide Secure Terminal Emualtor
Xshell 6 User Guide Secure Terminal Emualtor NetSarang Computer, Inc. Copyright © 2018 NetSarang Computer, Inc. All rights reserved. Xshell Manual This software and various documents have been produced by NetSarang Computer, Inc. and are protected by the Copyright Act. Consent from the copyright holder must be obtained when duplicating, distributing or citing all or part of this software and related data. This software and manual are subject to change without prior notice for product functions improvement. Xlpd and Xftp are trademarks of NetSarang Computer, Inc. Xmanager and Xshell are registered trademarks of NetSarang Computer, Inc. Microsoft Windows is a registered trademark of Microsoft. UNIX is a registered trademark of AT&T Bell Laboratories. SSH is a registered trademark of SSH Communications Security. Secure Shell is a trademark of SSH Communications Security. This software includes software products developed through the OpenSSL Project and used in OpenSSL Toolkit. NetSarang Computer, Inc. 4701 Patrick Henry Dr. BLDG 22 Suite 137 Santa Clara, CA 95054 http://www.netsarang.com/ Contents About Xshell ............................................................................................................................................... 1 Key Functions ........................................................................................................... 1 Minimum System Requirements .................................................................................. 3 Install and Uninstall .................................................................................................. -

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

Basic Guide: Using VIM Introduction: VI and VIM Are In-Terminal Text Editors That Come Standard with Pretty Much Every UNIX Op
Basic Guide: Using VIM Introduction: VI and VIM are in-terminal text editors that come standard with pretty much every UNIX operating system. Our Astro computers have both. These editors are an alternative to using Emacs for editing and writing programs in python. VIM is essentially an extended version of VI, with more features, so for the remainder of this discussion I will be simply referring to VIM. (But if you ever do research and need to ssh onto another campus’s servers and they only have VI, 99% of what you know will still apply). There are advantages and disadvantages to using VIM, just like with any text editors. The main disadvantage of VIM is that it has a very steep learning curve, because it is operated via many keyboard shortcuts with somewhat obscure names like dd, dw, d}, p, u, :q!, etc. In addition, although VIM will do syntax highlighting for Python (ie, color code things based on what type of thing they are), it doesn’t have much intuitive support for writing long, extensive, and complex codes (though if you got comfortable enough you could conceivably do it). On the other hand, the advantage of VIM is once you learn how to use it, it is one of the most efficient ways of editing text. (Because of all the shortcuts, and efficient ways of opening and closing). It is perfectly reasonable to use a dedicated program like emacs, sublime, canopy, etc., for creating your code, and learning VIM as a way to edit your code on the fly as you try to run it. -

Other Useful Commands
Bioinformatics 101 – Lecture 2 Introduction to command line Alberto Riva ([email protected]), J. Lucas Boatwright ([email protected]) ICBR Bioinformatics Core Computing environments ▪ Standalone application – for local, interactive use; ▪ Command-line – local or remote, interactive use; ▪ Cluster oriented: remote, not interactive, highly parallelizable. Command-line basics ▪ Commands are typed at a prompt. The program that reads your commands and executes them is the shell. ▪ Interaction style originated in the 70s, with the first visual terminals (connections were slow…). ▪ A command consists of a program name followed by options and/or arguments. ▪ Syntax may be obscure and inconsistent (but efficient!). Command-line basics ▪ Example: to view the names of files in the current directory, use the “ls” command (short for “list”) ls plain list ls –l long format (size, permissions, etc) ls –l –t sort newest to oldest ls –l –t –r reverse sort (oldest to newest) ls –lrt options can be combined (in this case) ▪ Command names and options are case sensitive! File System ▪ Unix systems are centered on the file system. Huge tree of directories and subdirectories containing all files. ▪ Everything is a file. Unix provides a lot of commands to operate on files. ▪ File extensions are not necessary, and are not recognized by the system (but may still be useful). ▪ Please do not put spaces in filenames! Permissions ▪ Different privileges and permissions apply to different areas of the filesystem. ▪ Every file has an owner and a group. A user may belong to more than one group. ▪ Permissions specify read, write, and execute privileges for the owner, the group, everyone else. -

Conditioning Flyer
Winter Sports Condi�oning: Girls’ and Boys‘ Basketball, Wrestling, and Sideline Cheer can start condi�oning on October 19th. Exact dates and �mes will be sent out later. The first two weeks will be outdoors with no equipment. Fall Sports Condi�oning: Football, Golf, Cross Country, Volleyball, and Compe��on Cheer can start condi�oning on November 16th. Exact dates and �mes will be sent out later. The first two weeks will be outdoors with no equipment. Must Complete Before Condi�oning: • Must have a physical and the VHSL physical form completed on or a�er May 1st 2020 • Must have complete the Acknowledgement of the Concussion materials • Must have completed the Acknowledgement of Par�cipa�on in the Covid-19 parent mi�ga�on form h�ps://whs.iwcs.k12.va.us/ - this is the link to the WHS web page where the forms can be found. Winter Parent Mee�ng Dates and Zoom Links: • Sideline Cheer - October 12th at 6pm h�ps://us02web.zoom.us/j/89574054101?pwd=djJyMFZSeU9QeFpjdGd6VFB4NkZoQT09 • Wrestling - October 13th at 6pm h�ps://us02web.zoom.us/j/87806116997?pwd=c0RKa1I1NFU1T2ZZbWNUVVZqaG9rdz09 • Girls’ and Boys’ Basketball - October 14th at 6pm h�ps://us02web.zoom.us/j/86956809676?pwd=UWkycEJ2K0pBbW0zNk5tWmE0bkpuUT09 Fall Parent Mee�ng Dates and Zoom Links: • Football - November 9th at 6:00pm h�ps://us02web.zoom.us/j/81813330973?pwd=b0I3REJ0WUZtTUs4Z0o3RDNtNzd3dz09 • Cross Country and Golf - November 10th at 6:00pm h�ps://us02web.zoom.us/j/86072144126?pwd=U0FUb0M2a3dBaENIaDVRYmVBNW1KUT09 • Volleyball - November 12th at 6:00pm h�ps://us02web.zoom.us/j/82413556218?pwd=ZjdZdzZhODNVMHlVSk5kSk5CcjBwQT09 • Compe��on Cheer - November 12th at 7:30pm h�ps://us02web.zoom.us/j/81803664890?pwd=dWVDaHNZS0JTdXdWNlNrZkJoVi92UT09 The parent and student athlete must attend the zoom meeting or watch the recorded zoom session prior to attending conditioning. -

Using the Linux Virtual Machine
Using the Linux Virtual Machine Update: On my computer I had problems with screen resolution and the VM didn't resize with the window and take the full width when in fullscreen mode. This was fixed with installation of an additional package. In a console window (see below how to pen that), I gave this command: sudo aptget install virtualboxguestdkms This asks for the password. That is "genomics". After restarting the VM, the screen resize works fine. Some programs are found in the menu at the bottomleft corner. Many programs are commandline only and not in the menu. To use the command line, start the console by clicking the icon in the bottom panel. Execute the following commands to create a new directory in your home folder "~/" for today’s exercises: mkdir ~/session_1 cd ~/session_1 Open the file browser to see what you did. The Shared Folders is under /media. On the file browser you can change to directory view using the pull down menu on the topleft corner: Click then "media" and "sf_evogeno". Using RStudio Click this link: https://drive.google.com/open?id=0B3Cf0QL4k1PTkZ5QVdEQ1psRUU and select to open the file in RStudio. Save the file in the folder "session_1" that you created above. The script requires two R libraries that are not installed. Install them by typing the following commands in the R console window: install.packages("ggplot2") install.packages("reshape") Now you are ready to run the script e.g. by clicking the "Source" button in the topright corner of the file editor window.