A Comparison of Wi-Fi and Wimax with Case Studies Ming-Chieh Wu
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evaluation of Mobile Wimax and Intelligent Video for Enhanced Rail Transit Safety
SharpRAIL: Evaluation of Mobile WiMAX and Intelligent Video for Enhanced Rail Transit Safety Report Number FTA-MD-26-7132-08.1 June 2008 DISCLAIMER NOTICE This document is disseminated under the sponsorship of the United States Department of Transportation, Federal Transit Administration, in the interest of information exchange. The United States Government assumes no liability for the contents or use thereof. The United States Government does not endorse products or manufacturers. Trade or manufacturers' names appear herein solely because they are considered essential to the contents of the report. Form Approved OMB No. 0704-0188 REPORT DOCUMENTATION PAGE Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington Headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188), Washington, DC 1. AGENCY USE ONLY (Leave blank) 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED June, 2008 Final Report, April 2007-January 2008 4. TITLE AND SUBTITLE 5. FUNDING NUMBERS SharpRAIL: Evaluation of Mobile WiMAX and Intelligent Video for Enhanced Rail Transit Safety MD-26-7132-00 6. AUTHOR(S) Santosh Kesavan, Eddie Wu and William Toeller 8. PERFORMING ORGANIZATION 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) REPORT NUMBER VT Aepco Inc 555 Quince Orchard Road, Suite 488 Gaithersburg, MD 20878 9. -

An Analysis of IEEE 802.16 and Wimax Multicast Delivery
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Calhoun, Institutional Archive of the Naval Postgraduate School Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2007-09 An analysis of IEEE 802.16 and WiMAX multicast delivery Staub, Patrick A. Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/3203 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA THESIS AN ANALYSIS OF IEEE 802.16 AND WIMAX MULTICAST DELIVERY by Patrick A. Staub September, 2007 Thesis Advisor: Bert Lundy Second Reader: George Dinolt Approved for public release; distribution is unlimited THIS PAGE INTENTIONALLY LEFT BLANK REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington DC 20503. 1. AGENCY USE ONLY (Leave blank) 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED September 2007 Master’s Thesis 4. TITLE AND SUBTITLE An Analysis of IEEE 802.16 and WiMAX 5. FUNDING NUMBERS Multicast Delivery 6. AUTHOR(S) Patrick A. Staub 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. -

Xirrus Management System
Xirrus Management System DATASHEET Introducing the Xirrus Management System Monitoring Views The Xirrus Management System (XMS) is a wireless network management platform that provides full monitoring and Dashboard View management of the Xirrus wireless Array network via a web Summary view of Xirrus Wireless network that is widget based. based application with graphical map views. XMS scales from Each widget shows different summary statistics such as Array/ small to large networks and from one location to multiple SSID status information, security status, and station information. locations, as well as large campus environments with thousands The Dashboard view is fully customizable to add or remove of wireless users. XMS provides help desk, as well as network desired widgets, select data categories displayed, and change operations and management capabilities for the Xirrus wireless the widget layout on a per user basis. network. XMS has a flexible license scheme based on the size of the wireless network, and is available as an application to run on legacy Windows Server systems, as well as a virtualized server environment. XMS is also offered on Xirrus Management appliances, for those that prefer a turnkey solution. At A Glance • Web based implementation, monitoring and management of a Xirrus wireless network • Single management application for small to large Xirrus Wireless Array Networks • Monitor wireless network performance, traffic and client stations • Manage configuration of the wireless network and management system • Configuration templates for bulk configuration changes Maps View • Automated installation and configuration of Xirrus Wireless View hierarchical maps showing floor plans or images for each Array Network allowing simplified deployment of Arrays location with Xirrus Array placement and selectable layered information views with configurable filters for information • Graphical maps showing wireless coverage heat maps, displayed. -

Wi-Fi Array Wi-Fi Array Architecture
Wi-Fi Array Wi-Fi Array Architecture Cellular Array Antennas Wi-Fi Array Antennas Cellular Wi-Fi Array Antenna Array Antenna • Multiple radios = more bandwidth and user density • Directional antennas = stronger signal strength and increased coverage • Sectored RF patterns = better RF management and load balancing • Fewer devices = cost, installation, and management savings 1 Xirrus Wi-Fi Arrays combine sectored array antennas and network switching into a single device. L2/L3 Switch Wi-Fi Array Switch • Distributed to the edge = more efficient switching decisions • Intelligence at the edge = more efficient QoS and VLAN-tagging • Security at the edge = better protection of all network traffic • More bandwidth = enhanced user experience and network efficiency 2 Xirrus Differentiators The Xirrus Wi-Fi Array replaces Ethernet workgroup switches by distributing the network intelligence and security to the network edge along with mobility and flexibility. VS. 24-Port Ethernet Xirrus XN8 Workgroup Switch Wi-Fi Array Users 24 24 Link Bandwidth 1Gbps 300Mbps Uplinks 2GigE 2GigE Mobility No Yes Security Very Good Very Good Availability Very Good Very Good Management Very Good Very Good Moves/Adds/Changes Average Very Good Installation Poor (Cables, Jacks, Very Good (Fewer Cables, Jumpers, Switches) No Closet Equipment) # of Devices Same Same # of Cables Poor (10X More) Excellent (90% Less) Cost Per User Good Very Good 3 It’s time to replace switched Ethernet to the desktop with Wi-Fi as the primary network connection. The Xirrus Wi-Fi Array obsoletes all other Wi-Fi offerings by delivering 400% more coverage, bandwidth, and user connections while using 75% fewer devices, cables, and switch ports. -
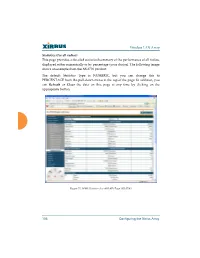
Wireless LAN Array 106 Configuring the Xirrus Array
Wireless LAN Array Statistics (for all radios) This page provides a detailed statistical summary of the performance of all radios, displayed either numerically or by percentage (your choice). The following image shows an example from the XS-3700 product. The default Statistics Type is NUMERIC, but you can change this to PERCENTAGE from the pull-down menu at the top of the page. In addition, you can Refresh or Clear the data on this page at any time by clicking on the appropriate button. Figure 74. WMI: Statistics for All IAPs Page (XS-3700) 106 Configuring the Xirrus Array Wireless LAN Array SSID This is a status only page that allows you to review SSID (Service Set IDentifier) assignments. It includes the SSID name, whether or not an SSID is visible on the network, any security and QoS parameters defined for each SSID, associated VLAN IDs, and radio availability per SSID. There are no configuration options available on this page, but if you are experiencing problems or reviewing SSID management parameters, you may want to print this page for your records. For information to help you understand SSIDs and how multiple SSIDs are managed by the XS-3900, go to the Multiple SSIDs section of “Frequently Asked Questions” on page 222. Figure 75. WMI: SSID Page Configuring the Xirrus Array 107 Wireless LAN Array Understanding SSIDs The SSID (Service Set Identifier) is a unique identifier that wireless networking devices use to establish and maintain wireless connectivity. Multiple access points on a network or sub-network can use the same SSIDs. -

Download the Programme Preview Here
THE STADIUM BUSINEss SUMMIT LONDON • 3-5 JUNE 2014 CONFERENCE PROGRAMME & EVENT GUIDE INCORPORATING PREMIUM SEAT SEMINAR FAN EXPERIENCE FORUM 2 MANICA kansas city | london | shanghai manicaarchitecture.com WELCOME HELLO WEMBLEY! Thanks for joining us at the ‘home of football’. After Dublin, Barcelona, Turin and Manchester, TheStadiumBusiness Summit is delighted to be in London for its fifth anniversary –"most especially at the reinvigorated sports and entertainment destination that is Wembley. You’ll find the full event schedule in the following pages. Alongside the main Summit conference programme, we’re hosting our specialist pre-Summit meetings at the Hilton Wembley to give the Premium Seat Seminar and Fan Experience Forum audiences maximum networking opportunities. We kickoff with an ‘expert’s tour’ and welcome reception of the world’s most famous stadium – courtesy of Wembley Stadium Consultancy. As always, the highlight of the programme is *DON’T FORGET! TheStadiumBusiness Awards evening where we will once again recognise our industry’s achievements, If you have purchased creativity and leaders. This year we’re at the historic RAF Museum with our hosts Centerplate. a ticket to TheStadium Business Awards Gala Our thanks go to all our speakers (for sharing their knowledge so freely), our sponsors (for backing us and keeping our industry moving forward), our partners (for making it easier to put this event Dinner please collect on), and our host venue (a great stadium with great people!). no later than from 14.00 the on Wednesday Finally – above all – our thanks to YOU for joining us. We wish you a great ‘visitor experience’ at registration desk.. -

IEEE 802.20: Mobile Broadband Wireless Access a Technical Overview
IEEE 802.20: Mobile Broadband Wireless Access A Technical Overview June 2006 for ITU-BDT Regional Seminar on Mobile and Fixed Wireless Access for Broadband Applications for the ARAB Seminar, June 19-22, 2006, Algiers, Algeria • The following is a technical overview of the IEEE 802.20 (FDD & TDD) proposed specification and how it compares to IEEE 802.16e (mobile WiMAX). • The presentation does not cover the IEEE Working Group processes relating to standardization. • I will not be making any comments today on the IEEE 802.20 standardization process or its current status. 1 1 Introduction • The 802.20 standard is being developed by the IEEE for highly efficient Mobile Broadband Wireless Access (MBWA) – Spectral efficiencies, sustained user data rates and numbers of active users that are significantly higher than other emerging mobile systems – Efficient packet based air interface optimized for IP-data transport, including real time services • Technology developed to target worldwide deployment of affordable, ubiquitous, always-on networks – To meet the needs of business and residential end user markets • 802.20 provides a specification for physical and medium access control layers for interoperable mobile wireless access systems – Operations for licensed bands below 3.5 GHz – Supports mobility classes up to 250 Km/h 2 Mobile Broadband Vision 3G and Beyond Best Connected Service: • Application-specific air interfaces CDMA2000, WPAN WCDMA, MPROC 802.20, FLO… MPROC • New OFDM(A) Physical GPRS, WLAN layers GPS DSP 3D Graphics • Common IP-based core DSP Video Audio network Memory Memory Imaging WLAN • Integrated WAN / LAN (802.11n) services • Multimode devices Mobile WAN/MAN Relative (Flash-OFDM, HSXPA, 802.20/3GPP2 Phase 2, LTE) Peak Rates Mobile Broadcast (FLO) Relative Coverage Data rates (vertical) and network coverage (horizontal) are illustrative only. -

City of Redondo Beach Deploys Xirrus High Performance Wi-Fi to Improve Staff/Public Experience and Operational Efficiency
City of Redondo Beach Deploys Xirrus High Performance Wi-Fi to Improve Staff/Public Experience and Operational Efficiency “Other than basic Overview management, we THE CITY OF REDONDO BEACH is a coastal Southern California town located 20 miles from haven’t had to downtown Los Angeles. With white sand beaches and year-round sunny weather, Redondo spend any time Beach is a preferred resort destination and one of the most desirable areas to live in the troubleshooting or country. fixing anything. For a The city boasts its own police department, fire and public works departments, two public department with our libraries, 15 parks and 13 parkettes, a large recreational and commercial harbor as well as the staffing level, that’s a Redondo Beach Pier and Seaside Lagoon. Redondo Beach outfitted its city buildings, libraries and performing arts center with Wi-Fi access to create more dynamic recreational experiences big plus.” for the public and increase productivity for the city’s 420 employees and 15 departments. CHRISTOPHER BENSON, IT TECHNOLOGY DIRECTOR, CITY OF REDONDO BEACH The Challenge Installed in 2006, the incumbent controller-based Wi-Fi solution was difficult to manage and rapidly becoming outdated. The IT team began to experience equipment failure leading to wireless outages. Additionally, performance did not match the density requirements of the areas served. Due to the rigidity of the system, the staff spent a significant amount of time managing and repairing the network when it failed. These compounding issues resulted in City staff receiving complaints about the spotty access and poor network speed. City administrators began to evaluate alternative Wi-Fi vendors and looked at Xirrus Wi- Fi through the company’s partnership with Avaya. -

Unit 3 Basics of Network Technology
UNIT 3 BASICS OF NETWORK TECHNOLOGY Structure 3.0 Objectives 3.1 Introduction 3.2 Network Concept and Classification 3.2.1 Advantages of Networks 3.2.2 Network Classification 3.3 Local Area Network (LAN) Overview 3.3.1 LAN Topologies 3.3.2 LAN Access Methods 3.4 Wide Area Network 3.4.1 WAN Topologies 3.4.2 WAN Switching Methods 3.4.3 WAN Devices/Hardware 3.5 Wireless Technology 3.5.1 WiFi 3.5.2 WiMax 3.6 Summary 3.7 Answers to Self Check Exercises 3.8 Keywords 3.9 References and Further Reading 3.0 OBJECTIVES After going through this Unit, you will be able to: explain the concept of computer networks; understand different application of networks; differentiate between different types of computer networks based on size, connection and functioning; compare the different network topologies used in LAN and WAN; understand the working of LAN access methods; explain the working of networking devices used in WAN; know the importance of using networked system; and understand the concept of wireless technologies and standards. 3.1 INTRODUCTION With the ICT revolution the functioning of organisations has changed drastically. In a networked scenario organisations often need several people (may be at different locations) to input and process data simultaneously. In order to achieve this, a computer-networking model in which a number of separate but interconnected computers do the job has replaced the earlier standalone-computing model. By linking individual computers over 4 7 Network Fundamentals a network their productivity has been increased enormously. A most distinguishing characteristic of a general computer network is that data can enter or leave at any point and can be processed at any workstation. -

IX256 Wimax Modem User Manual.P65
ZTE IX256 WiMAX MODEM User Manual 1 No part of this publication may be excerpted, reproduced, translated in any form or by any means, electronic or mechanical, including photocopying and microfilm, without the prior written authorization of ZTE Corporation. The manual is published by ZTE Corporation. We reserve the right to make modifications on print errors or update specifications without prior notice. Copyright © 2010 by ZTE Corporation All rights reserved. Version: V1.0 Date: Aug. 2010 Manual number: 079584501965 2 TABLE OF CONTENTS 1 General ............................................................................................................................ 6 1.1 Welcome ................................................................................................................ 6 1.2 Safety Precautions ................................................................................................ 6 1.3 Cleaning and Maintaining ....................................................................................... 7 1.4 Limited Warranty.................................................................................................... 7 1.5 Limitation of Liability ............................................................................................... 8 2 Getting Started .............................................................................................................. 9 2.1 Appearance........................................................................................................... 9 2.2 Parts -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

Xirrus Wi-Fi Designertm
Xirrus Wi-Fi Designer TM DATASHEET Xirrus Wi-Fi Designer The Xirrus Wi-Fi Designer is the ultimate 802.11 wireless site survey solution specifically architected to understand the multi- radio architecture of Xirrus Wireless Arrays. Wi-Fi Designer is offered in two forms: • A cloud based predictive planning tool that can be used from most common browsers • A Windows based application Wi-Fi Designer Cloud allows for predictive surveys in the very early stages of a project, to get a good estimate of the location and number of Xirrus Arrays as well as coverage and capacity. It is accessible from the Xirrus website, and supports most common browsers. All surveys created using the tool are stored in the cloud and easily accessible at any time through a convenient user account. At A Glance The Windows based application enables network architects • Predictive surveys help to plan a Wi-Fi network strategy to use predictive analysis and active site surveys to plan a with the optimal number of Xirrus Wireless Arrays and their best-fit wireless network strategy to minimize infrastructure recommended placement requirements while maximizing coverage and capacity. Once the Xirrus Wireless Arrays are implemented the Xirrus Wi-Fi • Quickly complete Active Surveys onsite with Xirrus Wireless Designer can verify the results of implementation and ensure Arrays taking real-time measurements to qualify the design for that design criteria has been met. the Xirrus implementation guarantee • Model different site conditions, Array configurations and positioning