Encyclopedia of Cybercrime
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
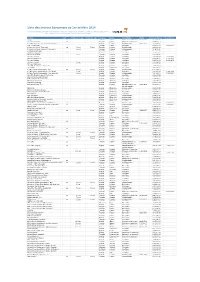
Liste Des Sources Europresse Au 1Er Octobre 2016
Liste des sources Europresse au 1er octobre 2016 Document confidentiel, liste sujette à changement, les embargos sont imposés par les éditeurs, le catalogue intégral est disponible en ligne : www.europresse.com puis "sources" et "nos sources en un clin d'œil" Source Pdf Embargo texte Embargo pdf Langue Pays Périodicité ISSN Début archives Fin archives 01 net oui Français France Mensuel ou bimensuel 1276-519X 2005/01/10 01 net - Hors-série oui Français France Mensuel ou bimensuel 2014/04/01 100 Mile House Free Press (South Cariboo) Anglais Canada Hebdomadaire 0843-0403 2008/04/09 18h, Le (site web) Français France Quotidien 2006/01/04 2014/02/18 2 Rives, Les (Sorel-Tracy, QC) oui 7 jours 7 jours Français Canada Hebdomadaire 2013/04/09 2 Rives, Les (Sorel-Tracy, QC) (site web) 7 jours Français Canada Hebdomadaire 2004/01/06 20 Minutes (site web) Français France Quotidien 2006/01/30 24 Heures (Suisse) oui Français Suisse Quotidien 2005/07/07 24 heures Montréal 1 jour Français Canada Quotidien 2012/04/04 24 hours Calgary Anglais Canada Quotidien 2012/04/05 2013/08/02 24 hours Edmonton Anglais Canada Quotidien 2012/04/05 2013/08/02 24 hours Ottawa Anglais Canada Quotidien 2012/04/02 2013/08/02 24 hours Toronto 1 jour Anglais Canada Quotidien 2012/04/05 24 hours Vancouver 1 jour Anglais Canada Quotidien 2012/04/05 24 x 7 News (Bahrain) (web site) Anglais Bahreïn Quotidien 2016/09/04 3BL Media Anglais États-Unis En continu 2013/08/23 40-Mile County Commentator, The oui 7 jours 7 jours Anglais Canada Hebdomadaire 2001/09/04 40-Mile County Commentator, The (blogs) 1 jour Anglais Canada Quotidien 2012/05/08 2016/05/31 40-Mile County Commentator, The (web site) 7 jours Anglais Canada Hebdomadaire 2011/03/02 2016/05/31 98.5 FM (Montréal, QC) (réf. -

Not for Immediate Release
Contact: Name Dan Gaydou Email [email protected] Phone 616-222-5818 DIGITAL NEWS AND INFORMATION COMPANY, MLIVE MEDIA GROUP ANNOUNCED TODAY New Company to Serve Communities Across Michigan with Innovative Digital and Print Media Products. Key Support Services to be provided by Advance Central Services Michigan. Grand Rapids, Michigan – Nov. 2, 2011 – Two new companies – MLive Media Group and Advance Central Services Michigan – will take over the operations of Booth Newspapers and MLive.com, it was announced today by Dan Gaydou, president of MLive Media Group. The Michigan-based entities, which will begin operating on February 2, 2012, will serve the changing news and information needs of communities across Michigan. MLive Media Group will be a digital-first media company that encompasses all content, sales and marketing operations for its digital and print properties in Michigan, including all current newspapers (The Grand Rapids Press, The Muskegon Chronicle, The Jackson Citizen Patriot, The Flint Journal, The Bay City Times, The Saginaw News, Kalamazoo Gazette, AnnArbor.com, Advance Weeklies) and the MLive.com and AnnArbor.com web sites. “The news and advertising landscape is changing fast, but we are well-positioned to use our talented team and our long record of journalistic excellence to create a dynamic, competitive, digitally oriented news operation,” Gaydou said. “We will be highly responsive to the changing needs of our audiences, and deliver effective options for our advertisers and business partners. We are excited about our future and confident this new company will allow us to provide superior news coverage to our readers – online, on their phone or tablet, and in print. -

APRIL 1981 :Ii FOIA Fol-107/01 Box Number 7618 MCCARTIN 10 DOC Doc Type Document Description No of Doc Date Restrictions NO Pages
WITHDRAWAL SHEET Ronald Reagan Library Collection Name DEAVER, MICHAEL: FILES Withdrawer KDB 7/18/2005 File Folder CORRESPONDENCE-APRIL 1981 :ii FOIA FOl-107/01 Box Number 7618 MCCARTIN 10 DOC Doc Type Document Description No of Doc Date Restrictions NO Pages i) MEMO JAY MOORHEAD TO M. DEAVER RE 1 4/28/1981 B6 PERSONNEL MATTER 2 MANIFEST RE SUMMIT PRE-ADVANCE 1 B6 B7(C) I®\ MEMO STEPHEN STUDDERT TOM. DEAVER RE 2 4/28/1981 B2 B7(E) MUTUAL UNDERSTANDINGS FROM MEETING Freedom of Information Act· [5 U.S.C. 552(b)) B·1 National security classified Information [(b)(1) of the FOIA] B-2 Release would disclose Internal personnel rules and practices of an agency [(b)(2) of the FOIA] B-3 Release would violate a Federal statute [(b)(3) of the FOIA] B-4 Release would disclose trade secrets or confidential or financial Information [(b)(4) of the FOIA] B-6 Release would constitute a clearly unwarranted invasion of personal privacy [(b)(6) of the FOIA] B-7 Release would disclose information compiled for law enforcement purposes [(b)(7) of the FOIA] B-8 Release would disclose Information concerning the regulation of financial Institutions [(b)(B) of the FOIA] B-9 Release would disclose geological or geophysical Information concerning wells [(b)(9) of the FOIA] C. Closed in accordance with restrictions contained in donor's deed of gift. THE WHITE HOUSE WASHINGTON April 28, 1981 l - ;". Dear Mr. Epple: Thank you for your kind letter and ex pression of continued support of President Reagan and his staff. -

Two Defendants Plead Guilty in Internet Music Piracy Crackdown
________________________________________________________________________ FOR IMMEDIATE RELEASE CRM FRIDAY, APRIL 20, 2007 (202) 514-2008 WWW.USDOJ.GOV TDD (202) 514-1888 TWO DEFENDANTS PLEAD GUILTY IN INTERNET MUSIC PIRACY CRACKDOWN WASHINGTON – Two defendants pleaded guilty to conspiracy to unlawfully reproduce and distribute copyrighted music over the Internet, Assistant Attorney General Alice S. Fisher of the Criminal Division and U.S. Attorney Chuck Rosenberg of the Eastern District of Virginia announced today. Arthur Gomez, 25, of La Habra, Calif., pleaded guilty before U.S. District Judge Leonie M. Brinkema. His sentencing has been scheduled for July 13, 2007 at 9:00 a.m. Sergey Ribiakost, 21, of Bardonia, N.Y., pleaded guilty on April 17, 2007, before U.S. District Judge James C. Cacheris. His sentencing is scheduled for July 10, 2007, at 1:00 p.m. Both defendants pleaded guilty to one count of conspiracy to commit copyright infringement and face up to five years in prison, a fine of $250,000, and three years of supervised release. Gomez and Ribiakost were leading members in the illegal software, game, movie and music trade online, commonly referred to as the warez scene. The defendants were active members of the pre-release music group Apocalypse Crew (APC), one of a handful of organized online criminal groups that acted as “first-providers” of much of the pirated music available on the Internet. As a pre-release music group, APC sought to acquire digital copies of songs and albums before their commercial release in the United States. The supply of such pre-release music was often provided by music industry insiders, such as radio DJs, employees of music magazine publishers, or workers at compact disc manufacturing plants, who frequently receive advance copies of songs prior to their commercial release. -

79385 AMA Conference Cover:Mppcover2
79385_AMA_conference Cover:MPPCover2 4/17/08 4:53 PM Page 1 2008 MARKETING and 2008 PUBLIC POLICY Conference Proceedings MARKETING VOLUME 18 and EDITORS PUBLIC POLICY John Kozup Charles R. Taylor Ronald Paul Hill Conference Proceedings May 29–May 31, 2008 Loews Hotel Philadelphia, Pennsylvania VOLUME 18 Life, Liberty, and the Pursuit of Sound Policy: Research at the Birthplace of Our Democracy Marketing and Public Policy Conference Proceedings 2008 “Life, Liberty, and the Pursuit of Sound Policy: Research at the Birthplace of Our Democracy” May 29–31, 2008 Loews Hotel Philadelphia, Pennsylvannia Editors: John Kozup Charles R. Taylor Ronald Paul Hill Volume 18 311 South Wacker Drive, Suite 58 • Chicago, Illinois 60606 PROGRAM COMMITTEE Natalie Adkins, Creighton University Gregory T. Gundlach, University of North Florida Kathryn Aikin, Food and Drug Administration Jane Hoek, Massey University Alan Andreasen, Georgetown University Jeanne Hogarth, Federal Reserve Board J. Craig Andrews, Marquette University Pauline Ippolito, Federal Trade Commission Lauren Block, Baruch College/CUNY Alan Levy, Food and Drug Administration Paul N. Bloom, Duke University Ingrid M. Martin, California State Univ. Long Beach Scot Burton, University of Arkansas Rob Mayer, University of Utah Jack Calfee, American Enterprise Institute Michael Mazis, American University Les Carlson, Clemson University Julie Ozanne, Virginia Polytechnic Institute Mary Culnan, Bentley College Janis K. Pappalardo, Federal Trade Commission Pam Scholder Ellen, Georgia State University Connie Pechman, University of California, Irvine Gary Ford, American University Ross Petty, Babson College Copyright © 2008, American Marketing Association Printed in the United States of America Composition by Marie Steinhoff, Southeast Missouri State University Cover design by Jeanne Nemcek ISBN: 0-87757-332-8 All rights reserved. -

Oil Wells Seized in ICE Money Laundering Case
Oil Wells Seized In ICE Money Laundering Case n ICE investigation into a drug Amoney laundering scheme resulted 3 Red Flag Indicators in the January 25 seizure of an Arizona • Frequent or unusual use of trust funds in oil company and 43 oil wells in business transactions or financial activity. northwest Pennsylvania. • Financial transactions to countries known to be tax havens. A number of the company’s trusts and • Frequent use of nominee business owners acting bank accounts in Europe were also seized as representatives in transactions. as a result of the investigation, which stemmed from the 1981 drug smuggling The seized company, Shaboom Oil Inc., conviction of Paul Hindelang. headquartered in Phoenix, Arizona, owned numerous operating wells and Safeguarding America Through “Like no other case in recent memory, this held the mineral rights to approximately Financial And Trade Investigations investigation demonstrates our perseverance in tracking down the ill-gotten gains of 1,100 acres of land in the Allegheny Volume II: No. 1 • February 2005 international crime lords,” said Jesus Torres, National Forest in northwest Pennsylvania. ICE’s Special Agent-in-Charge for Miami. In addition, ICE seized all ownership Inside this Issue shares of Shaboom Investments Inc., In the 1970s, Hindelang headed one of the a holding company based in Panama Cornerstone Investigations Updates: country’s biggest marijuana smuggling that owns the oil company. Selected Recent Cases . 2 enterprises, operating out of Florida. He Industry Alert: Stopping The Flow pled guilty to importing roughly 250 tons The oil company and associated assets seized Of Counterfeit Drugs . 3 of marijuana into the United States and in January were valued at $6.5 million— conspiring to import an additional bringing the total seized from Hindelang’s ICE Agents Honored For illicit investments to more than $70 mil- Intellectual Property Protection . -

A Critical Ideological Analysis of Mass Mediated Language
Western Michigan University ScholarWorks at WMU Master's Theses Graduate College 8-2006 Democracy, Hegemony, and Consent: A Critical Ideological Analysis of Mass Mediated Language Michael Alan Glassco Follow this and additional works at: https://scholarworks.wmich.edu/masters_theses Part of the Mass Communication Commons Recommended Citation Glassco, Michael Alan, "Democracy, Hegemony, and Consent: A Critical Ideological Analysis of Mass Mediated Language" (2006). Master's Theses. 4187. https://scholarworks.wmich.edu/masters_theses/4187 This Masters Thesis-Open Access is brought to you for free and open access by the Graduate College at ScholarWorks at WMU. It has been accepted for inclusion in Master's Theses by an authorized administrator of ScholarWorks at WMU. For more information, please contact [email protected]. DEMOCRACY, HEGEMONY, AND CONSENT: A CRITICAL IDEOLOGICAL ANALYSIS OF MASS MEDIA TED LANGUAGE by Michael Alan Glassco A Thesis Submitted to the Faculty of the Graduate College in partial fulfillment'of the requirements for the Degreeof Master of Arts School of Communication WesternMichigan University Kalamazoo, Michigan August 2006 © 2006 Michael Alan Glassco· DEMOCRACY,HEGEMONY, AND CONSENT: A CRITICAL IDEOLOGICAL ANALYSIS OF MASS MEDIATED LANGUAGE Michael Alan Glassco, M.A. WesternMichigan University, 2006 Accepting and incorporating mediated political discourse into our everyday lives without conscious attention to the language used perpetuates the underlying ideological assumptions of power guiding such discourse. The consequences of such overreaching power are manifestin the public sphere as a hegemonic system in which freemarket capitalism is portrayed as democratic and necessaryto serve the needs of the public. This thesis focusesspecifically on two versions of the Society of ProfessionalJournalist Codes of Ethics 1987 and 1996, thought to influencethe output of news organizations. -

DETROIT-METRO REGION Detroit News Submit Your Letter At: Http
DETROIT-METRO REGION Press and Guide (Dearborn) Email your letter to: Detroit News [email protected] Submit your letter at: http://content- static.detroitnews.com/submissions/letters/s Livonia Observer ubmit.htm Email your letter to: liv- [email protected] Detroit Free Press Email your letter to: [email protected] Plymouth Observer Email your letter to: liv- Detroit Metro Times [email protected] Email your letter to: [email protected] The Telegram Newspaper (Ecorse) Gazette Email your letter to: Email your letter to: [email protected] [email protected] Belleville Area Independent The South End Submit your letter at: Email your letter to: [email protected] http://bellevilleareaindependent.com/contact -us/ Deadline Detroit Email your letter to: Oakland County: [email protected] Birmingham-Bloomfield Eagle, Farmington Wayne County: Press, Rochester Post, Troy Times, West Bloomfield Beacon Dearborn Heights Time Herald/Down River Email your letter to: Sunday Times [email protected] Submit your letter to: http://downriversundaytimes.com/letter-to- Royal Oak Review, Southfield Sun, the-editor/ Woodward Talk Email your letter to: [email protected] The News-Herald Email your letter to: Daily Tribune (Royal Oak) [email protected] Post your letter to this website: https://docs.google.com/forms/d/e/1FAIpQL Grosse Pointe Times SfyWhN9s445MdJGt2xv3yyaFv9JxbnzWfC Email your letter to: [email protected] OLv9tDeuu3Ipmgw/viewform?c=0&w=1 Grosse Pointe News Lake Orion Review Email your -

The Copyright Crusade
The Copyright Crusade Abstract During the winter and spring of 2001, the author, chief technology officer in Viant's media and entertainment practice, led an extensive inqUiry to assess the potential impact of extant Internet file-sharing capabilities on the business models of copyright owners and holders. During the course of this project he and his associates explored the tensions that exist or may soon exist among peer-to-peer start-ups, "pirates" and "hackers," intellectual property companies, established media channels, and unwitting consumers caught in the middle. This research report gives the context for the battleground that has emerged, and calls upon the players to consider new, productive solutions and business models that support profitable, legal access to intellectual property via digital media. by Andrew C Frank. eTO [email protected] Viant Media and Entertainment Reinhold Bel/tIer [email protected] Aaron Markham [email protected] assisted by Bmre Forest ~ VI ANT 1 Call to Arms Well before the Internet. it was known that PCs connected to two-way public networks posed a problem for copyright holders. The problem first came to light when the Software Publishers Association (now the Software & Information Industry Association), with the backing of Microsoft and others, took on computer Bulletin Board System (BBS) operators in the late 1980s for facilitating trade in copyrighted computer software, making examples of "sysops" (as system operators were then known) by assisting the FBI in orchestrat ing raids on their homes. and taking similar legal action against institutional piracy in high profile U.S. businesses and universities.' At the same time. -

Law and the Emerging Profession of Photography in the Nineteenth-Century United States
Photography Distinguishes Itself: Law and the Emerging Profession of Photography in the Nineteenth-Century United States Lynn Berger Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy under the Executive Committee of the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2016 © 2016 Lynn Berger All rights reserved ABSTRACT Photography Distinguishes Itself: Law and the Emerging Profession of Photography in the 19th Century United States Lynn Berger This dissertation examines the role of the law in the development of photography in nineteenth century America, both as a technology and as a profession. My central thesis is that the social construction of technology and the definition of the photographic profession were interrelated processes, in which legislation and litigation were key factors: I investigate this thesis through three case studies that each deal with a (legal) controversy surrounding the new medium of photography in the second half of the nineteenth century. Section 1, “Peer Production” at Mid-Century, examines the role of another relatively new medium in the nineteenth century – the periodical press – in forming, defining, and sustaining a nation-wide community of photographers, a community of practice. It argues that photography was in some ways similar to what we would today recognize as a “peer produced” technology, and that the photographic trade press, which first emerged in the early 1850s, was instrumental in fostering knowledge sharing and open innovation among photographers. It also, from time to time, served as a site for activism, as I show in a case study of the organized resistance against James A. -

Ad Pages Template
INCREASING OUR ALCOHOL TOLERANCE SINCE 1992 VOLUME 25 | ISSUE 48 | DECEMBER 1-7, 2016 | FREE HHealthealth IInsurancensurance vvs.s. PPenalty.enallttyy.. healthyheaallltthy cchoice.hoiicce. IIff youyou ddon’ton’t hhaveaavve hhealthealltth iinsurance,nsurance, yyouou ccouldould eendnd uupp payingpaayying eextraxtra mmoneyoney iinn ttaxax ppenalties,enalltties, whilewhile gettinggetting nnothingothing iinn rreturn.eturn. ButBut itit doesn’tdoesn’t havehaavve toto bebe tthathaatt wway.aayy. VisitVViisit bbeWellnm.comeeWWWeellnm.com andand browsebrowse a varietyvariety ofof hhealthealltth insuranceinsurance choices.choices. SomeSome mmayaayy costcost almostalmost thethe samesame asas payingpaayying thethe taxtaaxx ppenalty.enalltty. InIn fact,ffaact, somesome ppeopleeople areare payingpaayyyiing betweenbetween $50$50 andand $100$100 perper month.month. And,And, iinsteadnstead ofof gettinggetting nothing,nothing, youyou ccanan bebe coveredcovered ffoforoorr eeverythingverything fromffrrom preventativeprevennttaattiivve carecare ttoo peacepeace ofof mmind.ind. Real Life: The Chavez Family WithWith InsuranceInsurance WWiWithoutithouutt IInsurancensurance • PreventivePreventive CareCare • PrescriptionsPrescriptions • NONO benefitsbenefits • DDoctoroctor VVisitsisits • HHospitalospital sstaystays • NNOO ccoverageoverage • PPeaceeace ooff mmindind • SSpecialistpecialist visitsvisits • NNOO ppeaceeace ooff mmindind & ssoo mmuchuch mmore!ore! • HHigherigher PPricetagricetag Annual Cost: $2,053 Annual Cost: $2,085 ForFor ffullull ccoverageoverage JustJJuust -
Media Kit September 2019
MEDIA KIT SEPTEMBER 2019 95+ YEARS OF CLIENT STORYTELLING. SMARTER MARKETING. LOCAL PRESENCE. NATIONAL REACH. MLive Media Group www.mlivemediagroup.com [email protected] 800.878.1400 20190911 Table Of Contents ABOUT US ....................................................................................................3 NATIONAL REACH ............................................................................... 4 MARKETING STRATEGISTS ............................................................5 CAPABILITIES........................................................................................... 6 DIGITAL SOLUTIONS .......................................................................... 8 TECH STACK ............................................................................................. 9 MLIVE.COM .............................................................................................. 10 PRINT SOLUTIONS ...............................................................................11 PRINT ADVERTISING ........................................................................12 INSERT ADVERTISING ......................................................................13 NEWSPAPER DISTRIBUTION MAP ...................................... 14 MICHIGAN’S BEST ...............................................................................15 CLIENTS RECEIVE ................................................................................17 TESTIMONIALS ....................................................................................