Guide to Microsoft System Center Management Pack for SQL Server
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Catalogue Des Solutions Microsoft Sommaire
Édition 2014-2015 Catalogue des solutions Microsoft Sommaire Windows Application Métier Windows 7 10 Microsoft Dynamics CRM 47 Windows 8.1 12 Microsoft Dynamics Nav 48 MDOP 14 Microsoft Dynamics Ax 49 Windows Phone 8.1 15 Surface Pro 3 16 Windows Embedded 18 Matériels Accessoires PC for business 50 Office Claviers 51 Souris 52 Office 2011 pour Mac 19 Webcams et Casques 54 Office 2013 20 Lumia 56 Office 365 22 Kinect SDK 57 Visio 2013 24 Project 2013 25 Exchange 2013 26 SharePoint 2013 28 Services Lync 2013 30 Bing 58 Yammer 32 Skype 59 OneDrive 60 Outlook.com 61 Serveurs et outils de développement Modes d’acquisition Windows Server Essentials 2012 R2 33 Windows Server 2012 R2 34 Introduction 62 Windows Multipoint Server 2012 36 Les modes d’achat 63 Enterprise Mobility Suite 37 Le choix d’un type de licence 64 Microsoft Azure 38 Les licences OEM 64 System Center 2012 R2 40 Les licences en volume 65 Microsoft Intune 42 Les licences Online 67 Visual Studio 2013 44 La Software Assurance 68 SQL Server 2014 46 Mise en œuvre d’une offre de licence 70 Microsoft Financing 70 Conformité logicielle 71 et gestion des actifs logiciels Les grossistes agréés 72 Ce catalogue a été rédigé en collaboration avec Calipia, sur la base de La Synthèse 2014 de l’offre Microsoft® pour les entreprises, parue aux éditions La Lettre Calipia, en février 2014. Tous droits de reproduction réservés © Calipia. Pour toute information sur cet ouvrage, rendez-vous sur : www.calipia.com/lasynthese. 3 SOMMAIRE Introduction Les temps Mobilité Social L’Organisation ont changé Numérique Parce que les temps ont changé, où il “suffisait” de parler aux informaticiens Un des principaux effets de cette “numérisation” du monde, c’est la prise des organisations pour pouvoir vendre ses solutions. -

Monitoring and Operating a Private Cloud
Exam Ref 70-246 70-246 Exam Ref Prepare for Microsoft Exam 70-246—and help demonstrate Monitoring and Operating your real-world mastery of operating a private cloud with a Private Cloud Microsoft System Center 2012. Designed for experienced Monitoring IT professionals ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen About the Exam needed for success at the MCSE level. Exam 70-246 is one of two required exams on the MCSE: Private Cloud Private Cloud Monitoring and Operating a certification track. Focus on the expertise measured by these and Operating objectives: About Microsoft • Configure data center process automation Certification • Deploy resource monitoring The Microsoft Certified Solutions • Monitor resources Expert (MCSE) certification for Private • Configure and maintain service management Cloud validates your expertise in imple- a Private Cloud menting and managing Microsoft private Manage configuration and protection • cloud computing technologies, including Windows Server and System Center. This Microsoft Exam Ref: The Microsoft Certified Solutions Associate (MCSA) certification for Organizes its coverage by exam objectives • Windows Server 2012 certification is a • Features strategic, what-if scenarios to challenge you prerequisite. You may also qualify for • Assumes you have experience with Windows Server, System an upgrade path from other Microsoft Center 2012, security, high availability, fault tolerance, and certifications. networking in an enterprise environment—plus basic See full details at: experience with Microsoft SQL Server, Windows PowerShell, microsoft.com/learning/certification and application configuration About the Author Orin Thomas is a consultant, writer, server administrator, speaker, and Microsoft MVP who has authored more than 30 books for Microsoft Press. -

System Center 2012 R2 Lab 5: Application Management
System Center 2012 R2 Lab 5: Application Management Hands-On Lab | Step-by-Step Guide For the VMs use the following credentials: Username: Contoso\Administrator Password: Passw0rd! Version: 1.5.5 Last updated: March 28, 2014 Please share any feedback with the IT Camps Planning Team: [email protected] Copyright © 2014 by Microsoft Corporation. All rights reserved. 5 - Application Management 1. 100 minutes optional (1:40 total) 2. SCAC, SCOM & SCA: Application Management Components (25 mins) 3. SCAC: Manage Applications through Self-Service (10 mins) 4. SCOM: Monitor Applications (15 mins) 5. SCOM: Review Application Performance Monitoring (40 mins) 6. SCA: Monitor Applications with Advisor (10 mins) 5.1 - SCAC, SCOM & SCA: Application Management Components 5.1.1 - SCAC: Introduction to App Controller In this exercise the user will learn about the different workspaces and functions of System Center 2012 R2 App Controller, including Clouds, Services, Virtual Machines, Library , Jobs and Settings. Internet Explorer will be used to connect to App Controller which provides a common self-service experience that can help easily configure, deploy, and manage virtual machines and services across private clouds (through SCVMM) and public clouds (through Azure). Estimated time to complete: 5 minutes Perform the following on SCVMM01 1. From SCVMM01, open App Controller by selecting the Internet Explorer icon from the taskbar. 2. If the site does not open, browse to https://SCVMM01.contoso.com. 3. If a notification appears about the certificate, click Continue to this website (not recommended). 4. When prompted to sign in, enter contoso\administrator for the user name and Passw0rd! for the password. -

Copyrighted Material
Index Numbers AMD RVI, 88 6to4, 436 APM (Application Platform Monitoring), 382 8.3 filename format, 112 App Controller, 381, 399–401 App-V, 3. See also application virtualization A 8.3 filename format, 112 Access Control System (ACS), 479 benefits, 151–154 Active Desktop, 26 cache file, 137–139 Active Directory client-side infrastructure, 131–141 ADAC (Active Directory Administrative Center), DSC (Dynamic Suite Composition), 128–130, 156 501–502 file type associations, 103–104, 135–137, 142– ADDS (Active Directory Domain Services), 144, 146, 157 501–502 Package Accelerators, 126–128 Windows Server 2012, 501–504 Q: drive, 101–102, 107–108, 111–114, 123, Active screening, 180 137–140 active/active mode, 276 Server App-V, 361–365 active/passive mode, 276 server-side infrastructure ActiveSync, 431, 435 full mode, 142–150 ADAC (Active Directory Administrative Center), lightweight mode, 150–151 501–502 standalone mode, 141–142 ADDS (Active Directory Domain Services), 501–502 in Session Host environments, 235 Administration Toolkit interface (MED-V), 84–85 virtual layers, 102–103 Administrator Console, SCVMM,COPYRIGHTED 317–320 App-V MATERIAL Client, 131–141, 361–364 AdminStudio, 159 Application Virtual Client, 137 Aero Glass, 30–33 Application Virtualization Service Agent, 137 Aero Peek, 33 installing, 132–135 Aero Shake, 33 operating systems supporting, 131 Aero Snap, 33 versus Server App-V, 361–364 Agent Server, UE-V, 202–204 workspaces, 135–137 AIK (Automated Installation Kit), 313 Amazon Elastic Compute Cloud (EC2), 14 517 293164bindex_updated.indd -

Introducing Microsoft System Center 2012 R2
Introducing Windows Azure for IT Professionals Windows Azure Introducing Introducing Windows Azure for IT Professionals Get a high-level overview of Windows Azure—and get a running Note start with this flexible cloud platform. Designed for IT professionals, This title is also available as a free this guide introduces core features and functionality, with technical eBook from Microsoft at: insights and advice from a Microsoft MVP and members of the http://aka.ms/mspressfree Windows Azure team. Audience & Focus Topics include: For IT professionals seeking an overview • Windows Azure components of the latest Windows Azure capabilities • Windows Azure solutions, from infrastructure to Big Data through October 2013, including under- the-hood insights and expert tips from Compute services—Web Sites, Virtual Machines, Cloud Services, • Microsoft insiders. Mobile Services • Network services—Virtual Network, Traffic Manager, and name resolution About the Authors • Data services, including data management and storage Mitch Tulloch is a widely recognized • App services and Windows Azure Active Directory expert on Windows administration who has been awarded Microsoft Most Valuable Professional (MVP) status for Introducing his contributions supporting those who deploy and use Microsoft platforms, products, and solutions. The engineers, program managers, and support professionals on the Windows Azure team shared their firsthand Microsoft System Also look for insights for this technical overview. Pocket Consultant Pocket Microsoft Exchange Server 2013 Microsoft Exchange Server 2013 Consultant Pocket Introducing Windows Server 2012 R2 Databases, Services, & Management Databases, Services, & Management Pocket Consultant Pocket Consultant ISBN: 9780735682788 The practical, portable guide for About the Author WindowsThe practical, portable guide for About the Author Windows Exchange administrators! William R. -

Guide to Microsoft System Center Management Pack for SQL Server 2017+
Guide to Microsoft System Center Management Pack for SQL Server 2017+ Microsoft Corporation Published: June 2018 The Operations Manager team encourages you to provide any feedback on the management pack by sending it to [email protected]. Copyright This document is provided "as is". Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. You may modify this document for your internal, reference purposes. © 2018 Microsoft Corporation. All rights reserved. Microsoft, Active Directory, Windows, and Windows Server are trademarks of the Microsoft group of companies. All other trademarks are the property of their respective owners. Contents Guide to Microsoft System Center Management Pack for SQL Server 2017+ ............................... 4 Changes History ........................................................................................................................... 4 Get Started ................................................................................................................................... 9 What’s New? ............................................................................................................................ -

Microsoft System Center: Integrated Cloud Platform
Microsoft System Center Integrated Cloud Platform David Ziembicki Mitch Tulloch, Series Editor PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2014 Microsoft Corporation (All) All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2014935076 ISBN: 978-0-7356-8314-3 Microsoft Press books are available through booksellers and distributors worldwide. If you need support related to this book, email Microsoft Press Book Support at [email protected]. Please tell us what you think of this book at http://www.microsoft.com/learning/booksurvey. Microsoft and the trademarks listed at http://www.microsoft.com/about/legal/en/us/IntellectualProperty/ Trademarks/EN-US.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. The example companies, organizations, products, domain names, email addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, email address, logo, person, place, or event is intended or should be inferred. This book expresses the author’s views and opinions. The information contained in this book is provided without any express, statutory, or implied warranties. Neither the authors, Microsoft Corporation, nor its resellers, or distributors will be held liable -
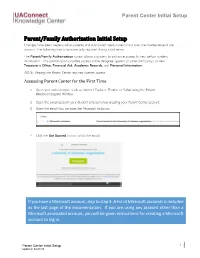
Parent Center Initial Setup
Parent Center Initial Setup Parent/Family Authorization Initial Setup Changes have been made to allow parents and authorized users more control over the maintenance of the account. The following instructions are only required during initial setup. The Parent/Family Authorization option allows a student to authorize access to view certain student information. This authorization provides access to the designee (parent or other third-party) to view Treasurer’s Office, Financial Aid, Academic Records, and Personal Information. NOTE: Viewing the Parent Center requires internet access. Assessing Parent Center for the First Time 1. Open your web browser, such as Internet Explorer, Firefox, or Safari using the Private Window/Incognito Window. 2. Open the email account your student entered when creating your Parent Center account. 3. Open the email that contains the Microsoft Invitation. 4. Click the Get Started button within the email. If you have a Microsoft account, skip to step 3. A list of Microsoft accounts is included as the last page of the documentation. If you are using any account other than a Microsoft associated account, you will be given instructions for creating a Microsoft account to log in. Parent Center Initial Setup 1 Updated: 04.23.19 Parent Center Initial Setup Creating a Microsoft Account 1. The following message will appear on your screen if you do not have a Microsoft account. 2. Click the Next button to Create a Password. 3. Enter a password and click the Next button to continue. 4. An authorization code will be sent to your Parent Center email account. Parent Center Initial Setup 2 Updated: 04.23.19 Parent Center Initial Setup 5. -

Monitoring Your Datacenter with System Center 2012 R2 Operations Manager
Monitoring your System Center Datacenter with 2012 R2 System Center 2012 R2 Operations Manager Hands-on lab System Center 2012 R2 Operations Manager is central to being able to monitor your datacenter and cloud, both public and private. Using Operations Manager, you can better ensure that your infrastructure meets its performance goals and objectives; that you can quickly be notified of and remediate any potential issues with infrastructure, application, and service availability; and that you can plan for future growth. In this Introductory lab, you will gain a basic understanding of the features and benefits of System Center 2012 R2 Operations Manager. You will learn how to import management packs, monitor the infrastructure, analyze data using Excel PowerPivot and Power View, and how to create visualization using the new Windows PowerShell Web Browser widget. Produced by HynesITe, Inc Version 1.0 5/28/2014 This document supports a preliminary release of a software product that may be changed substantially prior to final commercial release. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. Information in this document, including URL and other Internet Web site references, is subject to change without notice. The entire risk of the use or the results from the use of this document remains with the user. Unless otherwise noted, the companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted in examples herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. -

WINDOWS SERVER 2012 Windows Server 2012 - Installation 4-WI-22410 5 12-16 9-13 20-24 22-26 24-28 19-23 41 Et Configuration
Édito 2015 2015 : AGINIUS plus proche de vous ! La réforme de la formation professionnelle met l’accent sur la qualité accrue des formations dispensées par les organismes de formation, tout en instaurant de nouveaux cadres administratifs, juridique et financiers. Le réseau AGINIUS, plus que jamais, vous accompagne dans vos projets et plans de formation. Ses experts vous assurent des formations à la pointe technologique, des démarches administratives simples, et une proximité de ses conseillers sur l’ensemble du territoire national. Pour une efficacité optimale, le réseau AGINIUS garantit aussi : - Une mise à jour constante des connaissances des formateurs - Une capacité d’accueil de 2000 stagiaires par jour dans plus de 50 villes en France - Plus de 400 programmes de formation - Un suivi et des évaluations avant et après la formation - Un interlocuteur unique pour chaque client La vie est plus simple quand on est bien formé ! JEAN-CHARLES DUPLAA Président du réseau AGINIUS FORMATIONS 2015 CALENDRIER NATIONAL 2015 AGINIUS MANAGEMENT SI Gouvernance SI, Gestion de Projet, Tendances et état de l’art SYSTEMES ET RESEAUX Sécurité, Serveurs, Virtualisation, Cloud MESSAGERIE / TRAVAIL COLLABORATIF Exchange, SharePoint, Lync, Office 365 BASES DE DONNEES SQL, Administration, Maintenance, Décisionnel et BI Sommaire DEVELOPPEMENT ET METHODES Framework, .Net, Java, HTML, PHP, Ajax, XML MAINFRAME MVS/TSO, DB2, Cobol, PACBASE OUTILS GRAPHIQUES / WEB CREATION CAHIER D’INFORMATIONS Adobe, Web design, CMS, Photos, Vidéos, Autocad Index alphabétique.......................................234 -

Informatique Et Bureautique
| FORMATIONS 2016 | | INFORMATIQUE | aginius ET BUREAUTIQUE INFORMATIQUE INFORMATIQUE La vie est plus simple - FORMATIONS2016 quand on est bien formé ! www.aginius.fr EDITO AGINIUS vous offre la qualité en 2016 ! Le réseau AGINIUS poursuit sa stratégie de développement dans la lignée de la nouvelle Réforme de la formation. AGINIUS s’inscrit dans une démarche permanente de qua- lité et satisfaction de ses clients : Les centres sont dotés de la qualification OPQF*, gage de qualité pour les clients. Cette qualification atteste du professionnalisme d’un organisme : - Respect de la règlementation - Satisfaction des clients - Pérennité financière - Respect du code de déontologie, du code de conduite professionnelle et du règlement intérieur - Adéquation des compétences et des moyens techniques et humains à la formation Notre expertise nous permet de détenir de nombreuses habilitations relatives aux domaines de formation dispensées par les AGINIUS’ CENTER : - PCIE* (Passeport de compétences informatique européen) : certification mondiale des compétences en informatique, avec 148 pays et plus de 9 millions de candidats. - MOS* (Microsoft Office Specialist), certification valorisante et reconnue par Microsoft sur les applications Office - TOSA*, standard d’évaluation et de certification des compétences informatiques en bureau- tique (Excel, Word, PowerPoint, OpenOffice Calc) et en langage de programmation (HTML5, CSS3, PHP, C#, Java…). - B2i adultes*, attestation qui certifie la maîtrise de la compétence numérique ainsi que l’usage sûr et critique -

Guide to Microsoft Volume Licensing
Guide to Microsoft Volume Licensing Guide to Microsoft Volume Licensing October 2013 i Guide to Microsoft Volume Licensing Table of Contents Chapter 1: Introduction to Microsoft Volume Licensing ...................................................................................................... 1 How to Use This Guide ................................................................................................................................................................ 1 Keys to Understanding Microsoft Volume Licensing ...................................................................................................... 2 Programs for Your Organization Type and Size ................................................................................................................ 2 Programs for Public Sector and Other Organizations .................................................................................................... 3 Microsoft Payment Solutions.................................................................................................................................................... 4 Chapter 2: Choosing a Volume Licensing program for your commercial organization .......................................... 5 Microsoft Open Programs ......................................................................................................................................................... 6 Microsoft Open Program Family: Three Options .............................................................................................................