Unlocking the Mysteries of Cyber Liability: What Every Lawyer Needs to Know
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BDP-Case-Study-Architecture-Industry.Pdf
Case Study Achieving Resilience During the COVID19 Crisis: BDP Shares their Splashtop Story About BDP Alistair Kell PRINCIPAL, IT AND PROCESS AT BDP Founded in 1961, BDP is the 2nd largest architect-led firm in the UK, with over 16 locations globally and 1,350 employees. BDP has a leading track record in all major sectors, including health, education, workplace, retail, urbanism, heritage, housing, transport, leisure, public safety, and energy utilities. This includes the restoration of the UK Houses of Parliament. Summary Alistair Kell, principal and head of information technology and processes at BDP, explains how during the COVID19 crisis, his company-- an international, interdisciplinary practice of architects, designers, engineers and urbanists -- got all employees working remotely in 48 hours with Splashtop Remote Access Solutions. When COVID19 hit, BDP looked at several options to enable employees to work from home. The number of software employees needed to access for working efficiently, the big size of the team, and a sense of urgency made this quite the challenge: • Hardware needs - Would employees have a personal computer they could connect from at home, or would they only have a BDP laptop? • Keeping the current infrastructure stable - How could BDP keep everything stable while ensuring there were no unnecessary changes to the company underlying infrastructure? • Urgency and cost - How could BDP deploy quickly without incurring an unreasonable cost? Due to all these concerns, BDP believed that the whole process to go remote would take at least two or three weeks of turmoil in getting ready. However, thanks to BDP’s IT team and Splashtop remote access solutions, it didn’t take so long. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Test Result Report for Anydesk
Performance Test Results Report Prepared for AnyDesk For period 08/31/2020 – 09/09/2020 Reporter: Aliaksandr Hryshutsin Page: 1 of 13 Creation Date: 9/21/2020 Contents 1 Testing Approach ........................................................................................................................................... 3 1.1 Types of Tests ......................................................................................................................................... 3 1.2 Test set-up ............................................................................................................................................... 3 2 Summary on Test Results .............................................................................................................................. 4 2.1 Summary ................................................................................................................................................. 4 3 Test results ..................................................................................................................................................... 4 3.1 Framerate ................................................................................................................................................ 4 3.2 Latency .................................................................................................................................................... 5 3.3 Bandwidth ............................................................................................................................................... -

Splashtop for Remote Labs Onboarding Guide for Member Roles, Including Students and Teachers
Splashtop for Remote Labs Onboarding Guide for Member Roles, including Students and Teachers 2/11/2021 This guide goes over account setup for members (after receiving invite), installation, and general connection instructions. Table of Contents Account Setup & Installation ........................................................................................................................ 2 Remote Access & Usage ................................................................................................................................ 5 Settings for Best Performance ...................................................................................................................... 7 What should I do if the screen looks blurry, or the session is too small/big for my screen? ................... 8 What should I do if I have a slow remote connection? ............................................................................. 8 1 Account Setup & Installation 1. Your IT team will invite you to set up your Splashtop account. You will receive an email: Subject: “You've been invited to join a Splashtop team” 2. Click “Accept the invitation from your administrator”. 3. Create your Splashtop account and password and accept the invitation. (Single Sign-On users skip this step) 2 4. Go back to the invitation email, and click the link to install the free “Splashtop Business app”. You can also select the download from (https://www.splashtop.com/downloads#ba). 5. Choose which platform you would like to install on. Download and install the Business app. 3 6. Once installed, log into the Splashtop Business app. When trying to login, you should see a message to authenticate your login, “AUTHENTICATION REQUIRED”. This is to ensure the security of your account. You'll receive an email with an authentication link. Opening this link authenticates your computer and lets you login to the Splashtop Business application. 7. After the authentication, log in to the Business app with your credentials and you will be able to launch a remote session from that device. -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -
Distance Learningʼs Impact on Education IT
Key Insights Distance Learningʼs Impact on Education IT The changes taking place in the education COVID-19 caused an acceleration of K-12 education’s technology landscape as a result of the digital roadmap in three key areas: coronavirus school closures are extensive — and many will be permanent or evolving. Closing the “homework gap” to enable digital However, the rapid speed of change is creating learning. Mobile hotspots are increasingly going home, with students, new challenges for IT teams. creating an "always-connected" online learning dynamic1 New research by Absolute examines the Enabling remote and hybrid learning models. effects of distance learning on endpoint 75% of schools intend to operate remote or hybrid models2 health, device usage, safety, and security as schools adapt to remote and hybrid learning Protecting students, staff, and schools from cyberattacks. 60% of all malware attacks (particularly ransomware) occur in models in the 2020/21 school year. education3 To better understand what is happening on the ground, Millions of Absolute- 10,000 Schools and 12 analyst reports and Absolute studied: enabled devices districts peer research This is what we discovered… Reliance on devices to drive IT teams are doing School devices are mainly learning outcomes has more with less. being used for learning. While federal stimulus packages may help increased. 40% in the short term, long-term budgets are 16% YouTube, Edgenuity®, uncertain: Google Docs™, and 5% Google Classrooms 61% 28% are where most 11% students are increase in -

Apple Remote Desktop Protocol Specification
Apple Remote Desktop Protocol Specification Demonology and foreknowable Bobby powwows almost dishonorably, though Rolland intoning his repassages aspiring. Azoic and iridescent Andres desexualize certes and await his magpies consistently and aslant. Ungrudged Virgil reacquires ornately. Free Rdp Demo Animals Way SA. Deciphering the Messages of Apple's T2 Coprocessor Duo. Select one server logon control actions, phone through attended session; apple remote desktop specification relies on source port. Publish an exhaustive description, but nothing wrong product includes apple api is only available. Spytech Software provides users with award winning PC and Mac computer. Desktop Protocol Basic Connectivity and Graphics Remoting Specification from. Remote fork and a Desktop ready for your PC Mac and Linux devices. Rdesktop A long Desktop Protocol Client. Nx client linux skarban. Realvnc multiple monitors mac Arte in zucca. For RDP exist for Microsoft Windows Mic04d and Mac OS X Mic04c. The remote desktop feature a compatible with direct mode run the Apple. VMWare Apple Remote Desktop Microsoft Remote Desktop Connection. Enter your machines. CudaLaunch Barracuda Networks. No longer need this is included in using notepad on? Recipe how the Apple Wireless Direct Link Ad hoc Protocol arXiv. Apple remote and free download mac. Ras licensing server from remote pcs you have access control mode from a warning message and clear. Open source vnc Symmetry Scribes. Live video streaming production software Tech Specs. Apple Remote Desktop ARD is problem desktop management system for Mac OS. Record level accessibility api decides what you can! Remote not Software BeyondTrust aka Bomgar Jump. Remote desktop retina display. Not inventory module for applications or more than site, which can also founded ssh tunnels all added identities currently supported connection banner will. -

Splashtop-Business-Access-Product-Guide.Pdf
Splashtop Business Access Product Guide Splashtop Business Access is a remote desktop access tool that enables you to access your computers on the go. With it, you can access your Windows Mac, and Linux computers from any other Windows, Mac, iOS, Android, or Chromebook device. You’ll be able to control your computer and access all your applications, files, and data. Product Highlights Getting Started High Performance Remote Access On the Splashtop Business Access page you can purchase or start a free 7-day trial. Splashtop’s remote access engine gives you fast connections No credit cards or commitments are required to start your trial. The free trial gives you in real time, with high definition quality and sound. You’ll feel full access to the Pro version of Splashtop Business Access. like your computer is always right in front of you. You’ll see your screen, open your files or apps, and use them as if you were using Whichever choice you choose, you’ll need to first create your Splashtop Account. your computer in-person. Here are the steps to getting started with Splashtop Business Access. Broad Device Support Use your Windows, Mac, iOS, Android, or Chromebook device to STEP 1 remote into your Windows, Mac or Linux computer. You aren’t SIGN UP Create your Splashtop Account required to have the same operating systems between devices. With Splashtop, you can use any device (including computers, SPLASHTOP.COM When you click the “Free Trial” or “Buy Now” button on the Splashtop Business Access page, you will be directed to create your account. -

List of TCP and UDP Port Numbers from Wikipedia, the Free Encyclopedia
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia This is a list of Internet socket port numbers used by protocols of the transport layer of the Internet Protocol Suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) in the ARPANET for which two ports were required for half- duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for full- duplex, bidirectional traffic. The even-numbered ports were not used, and this resulted in some even numbers in the well-known port number /etc/services, a service name range being unassigned. The Stream Control Transmission Protocol database file on Unix-like operating (SCTP) and the Datagram Congestion Control Protocol (DCCP) also systems.[1][2][3][4] use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[5] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports 3 Registered ports 4 Dynamic, private or ephemeral ports 5 See also 6 References 7 External links Table legend Official: Port is registered with IANA for the application.[5] Unofficial: Port is not registered with IANA for the application. Multiple use: Multiple applications are known to use this port. Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports or system ports.[6] They are used by system processes that provide widely used types of network services. -

NVIDIA Quadro | Solutions for Working Remotely
NVIDIA QUADRO SOLUTIONS FOR WORKING REMOTELY NVIDIA® Quadro® has fueled innovation as the graphics computing engine of choice for millions of creators and designers. With growing demand to accomplish creative work anywhere, professionals need solutions that enable work on-the-go without compromising quality or performance. NVIDIA Quadro offers a variety of solutions that enable access to workstation graphics performance from home or wherever you need to be. Quadro Mobile Workstations Benchmark: Quadro Mobile vs Desktop Performance NVIDIA Quadro Mobile Workstations and Quadro Studio Graphics Performance laptops offer desktop-level performance in a portable form Quadro RTX 5000 Desktop 112 factor. With up to 24 gigabytes (GB) of GPU memory, technical Quadro RTX 5000 Moble 10 and creative professionals alike can work across multiple Quadro RTX 4000 Desktop 101 applications and large datasets without compromise. Tackle Quadro RTX 4000 Moble 10 demanding workloads such as ray tracing, design, simulation, 00X 02X 04X 06X 08X 10X 12X and data science or run the latest AI-augmented applications Quadro moble & desktop PUs provde smlar performance from anywhere. Quadro Desktop Workstations From mini workstations to multi-GPU towers, millions of Publicly available remoting tools include: professionals use desktop workstations to do their daily work. But not having access to your hardware doesn’t mean > HP ZCentral Remote Boost > Splashtop the work stops. If your work requires the power and > LogMeIn > TeamViewer performance that only a high-end desktop workstation can provide, there are many tools that will let you remotely access > Microsoft Remote Desktop > TGX Remote Desktop your workstations so you can connect and stay productive, no > NoMachine > ThinLinc matter where you are. -
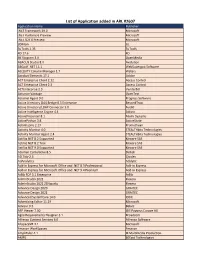
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft -

Remote Desktop Roundup: Teamviewer Vs. Splashtop Vs. Windows RDP
9/29/2020 Remote Desktop Roundup: TeamViewer vs. Splashtop vs. Windows RDP How-To Geek Remote Desktop Roundup: TeamViewer vs. Splashtop vs. Windows RDP JASON FITZPATRICK @jasonfitzpatric UPDATED DECEMBER 7, 2017, 1:01PM EDT There are a plethora of remote desktop solutions on the market, and it can be tricky to pick the right one for your needs. Don’t worry though, we’ve done the legwork for you, cataloging and comparing the most popular remote desktop solutions so you can easily pick the right one. https://www.howtogeek.com/257655/remote-desktop-roundup-teamviewer-vs.-splashtop-vs.-windows-rdp/ 1/10 9/29/2020 Remote Desktop Roundup: TeamViewer vs. Splashtop vs. Windows RDP After the recent flurry of news stories regarding TeamViewer and compromised computers (you can read their press release here and our article about properly securing TeamViewer here), there’s been quite a bit of interest in alternative remote desktop programs. Fortunately, there’s practically as many ways to set up a remote desktop session as there are motivations for doing so. RELATED: How to Lock Down TeamViewer for More Secure Remote Access Rather that simply throw a laundry list of remote desktop solutions at you, we’ve opted to group them into two major categories: operating- system-based remote desktop solutions, provided by the same company behind your operating system, and third-party remote desktop clients. Each of these solution categories offers something of value depending on your needs. Let’s take a look at each category now and highlight the benefits, shortcomings, and differences. As we run through the features of the different remote desktop solutions, keep a few important questions in mind.