A Unified Theory of Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Archives First: Digital Preservation Further Investigations Into Digital
Archives First: digital preservation Further investigations into digital preservation for local authorities Viv Cothey * 2020 * Gloucestershire County Council ii Not caring about Archives because you have nothing to archive is no different from saying you don’t care about freedom of speech because you have nothing to say. Or that you don’t care about freedom of the press because you don’t like to read. (after Snowden, 2019, p 208) Disclaimer The views and opinions expressed in this report do not necessarily represent those of the institutions to which the author is affiliated. iii iv Executive summary This report is about an investigation into digital preservation by (English) local authorities which was commissioned by the Archives First consortium of eleven local authority record offices or similar memory organisations (Archives). The investigation is partly funded by The National Archives. Archival institutions are uniquely able to serve the public by providing current and future generations with access to authentic unique original records. In the case of local authority Archives these records will include documents related to significant decision making processes and events that bear on individuals and their communities. Archival practice, especially relating to provenance and purposeful preservation, is instrumental in supporting continuing public trust and essential to all of us being able to hold authority to account. The report explains how Archival practice differs from library practice where provenance and purposeful preservation are absent. The current investigation follows an earlier Archives First project in 2016-2017 that investigated local authority digital preservation preparedness. The 2016-2017 investigation revealed that local authority line of business systems in respect of children services, did not support the statutory requirement to retain digital records over the long- term (at least 100 years). -

Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library
ACRL Publications in Librarianship No. 72 Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library Editors Peter D. Fernandez and Kelly Tilton Association of College and Research Libraries A division of the American Library Association Chicago, Illinois 2018 The paper used in this publication meets the minimum requirements of Ameri- can National Standard for Information Sciences–Permanence of Paper for Print- ed Library Materials, ANSI Z39.48-1992. ∞ Cataloging-in-Publication data is on file with the Library of Congress. Copyright ©2018 by the Association of College and Research Libraries. All rights reserved except those which may be granted by Sections 107 and 108 of the Copyright Revision Act of 1976. Printed in the United States of America. 22 21 20 19 18 5 4 3 2 1 Contents Contents Introduction .......................................................................................................ix Peter Fernandez, Head, LRE Liaison Programs, University of Tennessee Libraries Kelly Tilton, Information Literacy Instruction Librarian, University of Tennessee Libraries Part I Contemplating Library Values Chapter 1. ..........................................................................................................1 The New Technocracy: Positioning Librarianship’s Core Values in Relationship to Technology Is a Much Taller Order Than We Think John Buschman, Dean of University Libraries, Seton Hall University Chapter 2. ........................................................................................................27 -

GVSU Libraries Digital Preservation Policy | 1
Version GVSU 1.0, November Libraries 15th, 2016 Digital Preservation Policy TABLE OF CONTENTS SECTION 1. PURPOSE ................................ .......................................................................................................... 2 SECTION 2. MANDATE ................................ ......................................................................................................... 2 SECTION 3. OBJECTIVES ................................ ..................................................................................................... 2 SECTION 4. SCOPE ................................ ................................................................................................................ 3 N COPE ATERIALS 4.1. I -‐S M ................................ ...................................................................................................................... 3 UT OF COPE ATERIALS 4.2. O -‐ -‐S M ................................ ............................................................................................................ 3 SECTION UPPORTED 5. DESIGNATED RESERVATION COMMUNITY EVELS ................................ ......................................................................... 4 4.3. S P L ................................ ............................................................................................. 3 ACULTY TAFF TUDENTS 5.1. GVSU F , S & S ................................ .......................................................................................... -

Evaluation and Strategies of Digital Preservation & UNESCO's Role In
2nd Annual Conference of the ICA, Girona, October 2014 UNESCO-PERSIST Evaluation and Strategies of Digital Preservation & UNESCO’s Role in Facing the Technical Challenges Margriet van Gorsel, Michiel Leenaars, Natasa Milic-Frayling, Jonas Palm Introduction PERSIST (Platform to Enhance the Sustainability of the Information Society Trans globally) is a collaborative project of UNESCO, IFLA, ICA and other partners to address globally pressing questions on the preservation of digital information in the public domain related to strategies, technology, selection issues, and roles and responsibilities. It works under the assumption that on these issues a high-level global policy discussion is needed between heritage institutions, IT-industry and government, and that UNESCO’s Memory of the World Program is a unique platform to conduct that discussion. The idea for PERSIST was born at the Conference The Memory of the World in the Digital Age: Digitization and Preservation in Vancouver (September 2012). The Declaration adopted by its participants states that there is a pressing need to establish a roadmap proposing solutions, agreements and policies, that ensure long term access and trustworthy preservation. This roadmap should address issues like open government, open data, open access and electronic government. It should dovetail with national and international priorities and be in full agreement with human rights. PERSIST was launched as a project at the Conference A Digital Roadmap for Long‐Term Access to Digital Heritage in The Hague in December 2013. In its initial stage the project is coordinated by the Netherlands National Commission for UNESCO and financed by the Netherlands Ministry for Education, Culture and Science. -
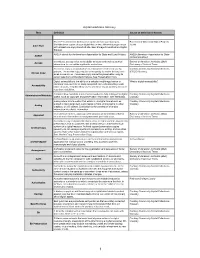
Digital Readiness Glossary
Digital Readiness Glossary Term Definition Source of definition (if known) The 3-2-1 rule informs digital preservation and storage strategies. Recollection Wisconsin Digital Projects Maintain three copies of your digital files on two different storage media Toolkit 3-2-1 Rule with at least one copy stored off site. See: Storage Diversification, Digital Storage AASLH stands for the American Association for State and Local History. AASLH (American Association for State AASLH and Local History) In archives, access refers to the ability to locate and retrieve archival Society of American Archivists (SAA) Access information for use within applicable restrictions. Dictionary of Archival Terms An access copy is a reproduction of a document created for use by Curating Community Digital Collections patrons. The access copy may be lower quality for easier delivery over (CCDC) Glossary Access Copy email or use online. The access copy allows the preservation copy to remain safe from unintended changes. See: Preservation Copy Digital accessibility is the ability of a website, mobile application or What is digital accessibility? electronic document to be easily navigated and understood by a wide Accessibility range of users, including those users who have visual, auditory, motor or cognitive disabilities. Administrative metadata is information needed to help manage the digital Curating Community Digital Collections Administrative Metadata object, such as copyright and preservation information. See: Metadata. Glossary Analog refers to information that exists in nondigital format such as Curating Community Digital Collections printed or manuscript text, audio tapes or films, photographs or other Glossary Analog graphics, or 3-D objects. Digitization is the conversion of analog information into digital information. -

Uncertainties of Digital Today's and Tomorrow's Igital Information And
Merit Research Journal of Education and Review Vol. 1(3) pp. 058-063, April, 2013 Available online http://www.meritresearchjournals.org/er/index.htm Copyright © 2013 Merit Research Journals Review Uncertainties of d igital information and preservation in today's and tomorrow’s generation: an idea Raghunadha T. Reddy 1, Dr. K. Kumar 1 and T. Sreenivasa Rao 2 1Librarian, SVCET, Chittoor-517127 2Assistant Librarian and Head, ANGRAU Regional Library. S.V. Agricultural College, Tirupati – 517 502 Accepted April 05, 2013 The digital information generated by organizations from domains such as government, cultural heritage, science and education, audio, video, films, health, insurance, banking, etc are part of our digital universe or each one is a digital universe in its own right . There is good understanding in the Library of preservation issues and of the constraints of preservation strategies, which are taken into a ccount in deciding what to take into the Library’s collections and how it should be managed. So this paper is brief discussion of an idea: uncertainties of digital information and preservation in today's and tomorrow's generation. Keywords: Digital Information, Preservation, Problems INTRODUCTION Preservation strategies in academic and research Requirements of India is conducted by Human Centered libraries are not new concepts. However, with an Design and Computing Group of C -DAC, Pune was increasing amoun t of digital content, organizations have entrusted with the responsibility to produce the national to cope with a new set of preservation issues. Digital study report on digital preservation requirements of India preservation is in its infancy worldwide and presents by Department of Information Technology, Government some difficult technological issues. -

Introduction to Digital Preservation: Why Preserve? How to Preserve?
Introduction to Digital Preservation: Why Preserve? How to Preserve? Dr. Ross King Austrian Institute of Technology Outline • Introduction: Digital Universe • Digital Preservation Challenges – Information Retrieval past and present – Bit-stream Preservation – Logical Preservation • Digital Preservation Incentives – Markets – Incentives – Risks • Conclusions Introduction The Digital Universe The Digital Universe • Estimated volume of • Estimated growth rate: ca. 60% digital information • → 700 Exabytes in 2009! worldwide in 2007: 281 Exabytes Digital Information Created, Captured, and Replicated Worldwide 2000 1000 k kilo 1800 1000 2 M mega 1600 1000 3 G giga 1400 1200 1000 4 T tera 1000 5 1000 P peta 800 Exabytes 1000 6 E exa 600 1000 7 Z zetta 400 200 1000 8 Y yotta 0 2005 2006 2007 2008 2009 2010 2011 2012 source: Year “The Diverse and Exploding Digital Universe” IDC White Paper, March 2008 http://www.emc.com/collateral/analyst-reports/diverse-exploding-digital-universe.pdf The Digital Universe • Information creation is beginning to exceed storage capacity • Much of this information is – transient – redundant The Digital Universe Issues: • What is worth preserving? • How to preserve? • How to preserve so much? • How to ensure quality? • How to create incentives to preserve? The Digital Universe Issues: • What is worth preserving? • How to preserve? • How to preserve so much? • How to ensure quality? • How to create incentives to preserve? Part 1 Digital Preservation Challenges Digital Preservation • standards, best-practices, and technologies -

Sandra Deljanin, [email protected] University of Belgrade, Faculty of Philology October 2011
UDK 004.65 DIGITAL OBSOLESCENCE Sandra Deljanin, [email protected] University of Belgrade, Faculty of Philology October 2011 Summary Problems of digital obsolescence due to obsolescence of computers, software and data mediums are presented in this article. Librarians and archivists are mostly concerned because of the “digital dark age” phenomenon, and they are looking for more efficient solutions to preserve cultural and intellectual heritage in digital form in order to de- crease expenses and prevent time wasting. Further in the article, disadvantages of some computer platforms and methods of temporary data revival are shown, but for now no efficient standardized and long-term strategy, which could be applied to all types of dig- ital resources, has been established. Many examples of computer, format, program and medium obsolescence that are listed, should awake everyone’s consciousness no matter what their professional occupation is, because contemporary business and social life can’t be imagined without computer technology which makes communication easier and faster, but it can also disable and interrupt all connections with future generations. Key words digital obsolescence, Domesday project, emulators, format specifications, digital dark age, digital preservation, digital preservation strategies. INFOtheca No 1, Volume XIII, May 2012 43 DIGITAL OBSOLESCENCE 1. Introduction which computer platform can read them and in Situation in which digital resource cannot be which format they are. It makes the data retrieval read anymore, either because physical medium process, with which librarians and archivists are that contains it is no longer in use, or hardware faced with always growing data collections, even or software which executes it is not available, is harder. -

"Through a Glass, Darkly" Technical, Policy, and Financial Actions to Avert the Coming Digital Dark Ages Richard S
Santa Clara High Technology Law Journal Volume 33 | Issue 2 Article 1 1-1-2017 "Through A Glass, Darkly" Technical, Policy, and Financial Actions to Avert the Coming Digital Dark Ages Richard S. Whitt Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Intellectual Property Law Commons, and the Science and Technology Law Commons Recommended Citation Richard S. Whitt, "Through A Glass, Darkly" Technical, Policy, and Financial Actions to Avert the Coming Digital Dark Ages, 33 Santa Clara High Tech. L.J. 117 (2017). Available at: http://digitalcommons.law.scu.edu/chtlj/vol33/iss2/1 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized editor of Santa Clara Law Digital Commons. For more information, please contact [email protected]. “THROUGH A GLASS, DARKLY” TECHNICAL, POLICY, AND FINANCIAL ACTIONS TO AVERT THE COMING DIGITAL DARK AGES Richard S. Whitt† This paper explains the digital preservation challenge, examines various technical, legal, commercial, and governance elements, and recommends concrete proposals in each area. The research is based on a wide-ranging review of pertinent books, reports, studies, and articles familiar to experts in the digital preservation community. Much of our global cultural heritage, and our own individual and social imprint, is at serious risk of disappearing. More and more of our lives is bound to the ones and zeroes of bits residing on a cloud server or a mobile device. -

Digital Preservation Handbook Content Specific Preservation
Digital Preservation Handbook Content Specific Preservation Illustrations by Jørgen Stamp digitalbevaring.dk CC BY 2.5 Denmark Who is it for? Operational managers (DigCurV Manager Lens) and staff (DigCurV Practitioner Lens) in repositories, publishers and other data creators, third party service providers. Assumed level of knowledge Novice to Intermediate Purpose To provide a bridge to and achieve synergies with, reports in the DPC Tech Watch Series. The reports provide advanced level "deep dives" in specific areas of content preservation (e.g. email) that can be cited or to source case studies in the Handbook. To be developed for ease of maintenance, cost-efficiency, and sustainability in the long-term by the DPC via updates and additions to the Tech Watch series. To provide a brief overview and case studies, suitable for novice or intermediate level users, of digital preservation issues for specific content types covered by DPC Technology Watch Reports. Currently three content types are available: e-journals, moving picture and sound, and web-archiving. We hope to add more at a later date. Gold sponsor Silver sponsors Bronze sponsors Reusing this information You may re-use this material in English (not including logos) with required acknowledgements free of charge in any format or medium. See How to use the Handbook for full details of licences and acknowledgements for re-use. For permission for translation into other languages email: [email protected] Please use this form of citation for the Handbook: Digital Preservation Handbook, 2nd Edition, http://handbook.dpconline.org/, Digital Preservation Coalition © 2015. 2 Contents e-Journals .................................................................................................................................................. 4 Case study 1: the e-journal or its past issues are no longer available from the publisher .................. -

Digital Preservation Policy
Procedures for Selecting Digital Formats Digital Preservation Policy Procedures relating to: Digital Preservation Policy Approving authority: Collections Committee Consultation via: Digital Preservation Group, AV Group Approval date: 23 October 2015 Effective date: 23 October 2015 Review period: Three Years Responsible Executive Secretary of the University Responsible Office: Heritage and Information Governance HERIOT-WATT UNIVERSITY POLICY TITLE CONTENT Section Page 1 Introduction 3 2 Standards for Selecting Digital Formats 3 3 Related policies, procedures and further reference 7 4 Further help and advice 8 5 Definitions 8 6 Policy version and history 9 Appendix 1 Archival Records summary 10 Heriot-Watt University’s Procedures: Digital Preservation Policy 1. INTRODUCTION Standards for the selection of formats for digital records in connection with the Digital reservation Policy 2. STANDARDS FOR SELECTING DIGITAL FORMATS There are a wide range of digital formats. However some are suitable for facilitating long term preservation and others are not. The use of proprietary formats runs the risk of digital obsolescence. In many cases the University controls the formats available for use e.g. Microsoft Office although this is not always the case. When a data creator is making the decision regarding which format to use the overriding factor will be their business needs. However the data creator should also take the long term preservation of the data for both future business use and archival preservation into consideration. Failure to do so will make it difficult and costly to manage the data in a preservation system or make it unusable for future business purposes. In addition, some Research Council Specialist Subject Repositories have quite strict criteria over which formats they can or cannot accept to facilitate data sharing, and may ask for details of the formats to be used and how the researcher plans to ensure long term preservationas part of the data management plan. -

Cop PROGRESS REPORT YEAR 2
Project Acronym: Presto4U Grant Agreement no: 600845 Project Title: European Technology for Digital Audiovisual Media Preservation D2.5: CoP PROGRESS REPORT YEAR 2 Project funded by the European Community in the 7th Framework Programme Project Deliverable 2.5 Table of contents 1 Scope and Executive summary ............................................................................. 4 2 Learning and Teaching Repositories ................................................................. 5 2.1 Introduction to the work done, general challenges and progress .................... 5 2.2 The Community’s long term digital preservation needs ................................. 13 2.3 Barriers to the Community’s adoption of new technology .............................. 17 2.4 Connection between the Community and suppliers and vendors .................. 19 2.5 Recommendations for the future of the Community ...................................... 22 3 Video Production and Post-Production ........................................................... 25 3.1 Introduction to the work done, general challenges and progress .................. 25 3.2 The Community’s long term digital preservation needs ................................. 30 3.3 Barriers to the Community’s adoption of new technology .............................. 35 3.4 Connection between the Community and suppliers and vendors .................. 38 3.5 Recommendations for the future of the Community ...................................... 40 4 Sound and Music Community of Practice ......................................................