Archives First: Digital Preservation Further Investigations Into Digital
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library
ACRL Publications in Librarianship No. 72 Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library Editors Peter D. Fernandez and Kelly Tilton Association of College and Research Libraries A division of the American Library Association Chicago, Illinois 2018 The paper used in this publication meets the minimum requirements of Ameri- can National Standard for Information Sciences–Permanence of Paper for Print- ed Library Materials, ANSI Z39.48-1992. ∞ Cataloging-in-Publication data is on file with the Library of Congress. Copyright ©2018 by the Association of College and Research Libraries. All rights reserved except those which may be granted by Sections 107 and 108 of the Copyright Revision Act of 1976. Printed in the United States of America. 22 21 20 19 18 5 4 3 2 1 Contents Contents Introduction .......................................................................................................ix Peter Fernandez, Head, LRE Liaison Programs, University of Tennessee Libraries Kelly Tilton, Information Literacy Instruction Librarian, University of Tennessee Libraries Part I Contemplating Library Values Chapter 1. ..........................................................................................................1 The New Technocracy: Positioning Librarianship’s Core Values in Relationship to Technology Is a Much Taller Order Than We Think John Buschman, Dean of University Libraries, Seton Hall University Chapter 2. ........................................................................................................27 -

Digital Preservation Handbook
Digital Preservation Handbook Digital Preservation Briefing Illustrations by Jørgen Stamp digitalbevaring.dk CC BY 2.5 Denmark Who is it for? Senior administrators (DigCurV Executive Lens), operational managers (DigCurV Manager Lens) and staff (DigCurV Practitioner Lens) within repositories, funding agencies, creators and publishers, anyone requiring an introduction to the subject. Assumed level of knowledge Novice. Purpose To provide a strategic overview and senior management briefing, outlining the broad issues and the rationale for funding to be allocated to the tasks involved in preserving digital resources. To provide a synthesis of current thinking on digital preservation issues. To distinguish between the major categories of issues. To help clarify how various issues will impact on decisions at various stages of the life-cycle of digital materials. To provide a focus for further debate and discussion within organisations and with external audiences. Gold sponsor Silver sponsors Bronze sponsors Reusing this information You may re-use this material in English (not including logos) with required acknowledgements free of charge in any format or medium. See How to use the Handbook for full details of licences and acknowledgements for re-use. For permission for translation into other languages email: [email protected] Please use this form of citation for the Handbook: Digital Preservation Handbook, 2nd Edition, http://handbook.dpconline.org/, Digital Preservation Coalition © 2015. 2 Contents Why Digital Preservation Matters -

GVSU Libraries Digital Preservation Policy | 1
Version GVSU 1.0, November Libraries 15th, 2016 Digital Preservation Policy TABLE OF CONTENTS SECTION 1. PURPOSE ................................ .......................................................................................................... 2 SECTION 2. MANDATE ................................ ......................................................................................................... 2 SECTION 3. OBJECTIVES ................................ ..................................................................................................... 2 SECTION 4. SCOPE ................................ ................................................................................................................ 3 N COPE ATERIALS 4.1. I -‐S M ................................ ...................................................................................................................... 3 UT OF COPE ATERIALS 4.2. O -‐ -‐S M ................................ ............................................................................................................ 3 SECTION UPPORTED 5. DESIGNATED RESERVATION COMMUNITY EVELS ................................ ......................................................................... 4 4.3. S P L ................................ ............................................................................................. 3 ACULTY TAFF TUDENTS 5.1. GVSU F , S & S ................................ .......................................................................................... -

A New Digital Dark Age? Collaborative Web Tools, Social Media and Long-Term Preservation Stuart Jeffrey Version of Record First Published: 05 Dec 2012
This article was downloaded by: [University of York] On: 10 December 2012, At: 04:01 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK World Archaeology Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/rwar20 A new Digital Dark Age? Collaborative web tools, social media and long-term preservation Stuart Jeffrey Version of record first published: 05 Dec 2012. To cite this article: Stuart Jeffrey (2012): A new Digital Dark Age? Collaborative web tools, social media and long-term preservation, World Archaeology, 44:4, 553-570 To link to this article: http://dx.doi.org/10.1080/00438243.2012.737579 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and-conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. A new Digital Dark Age? Collaborative web tools, social media and long-term preservation Stuart Jeffrey Abstract This paper examines the impact of exciting new approaches to open data sharing, collaborative web tools and social media on the sustainability of archaeological data. -

Evaluation and Strategies of Digital Preservation & UNESCO's Role In
2nd Annual Conference of the ICA, Girona, October 2014 UNESCO-PERSIST Evaluation and Strategies of Digital Preservation & UNESCO’s Role in Facing the Technical Challenges Margriet van Gorsel, Michiel Leenaars, Natasa Milic-Frayling, Jonas Palm Introduction PERSIST (Platform to Enhance the Sustainability of the Information Society Trans globally) is a collaborative project of UNESCO, IFLA, ICA and other partners to address globally pressing questions on the preservation of digital information in the public domain related to strategies, technology, selection issues, and roles and responsibilities. It works under the assumption that on these issues a high-level global policy discussion is needed between heritage institutions, IT-industry and government, and that UNESCO’s Memory of the World Program is a unique platform to conduct that discussion. The idea for PERSIST was born at the Conference The Memory of the World in the Digital Age: Digitization and Preservation in Vancouver (September 2012). The Declaration adopted by its participants states that there is a pressing need to establish a roadmap proposing solutions, agreements and policies, that ensure long term access and trustworthy preservation. This roadmap should address issues like open government, open data, open access and electronic government. It should dovetail with national and international priorities and be in full agreement with human rights. PERSIST was launched as a project at the Conference A Digital Roadmap for Long‐Term Access to Digital Heritage in The Hague in December 2013. In its initial stage the project is coordinated by the Netherlands National Commission for UNESCO and financed by the Netherlands Ministry for Education, Culture and Science. -
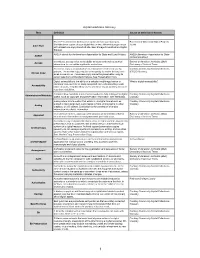
Digital Readiness Glossary
Digital Readiness Glossary Term Definition Source of definition (if known) The 3-2-1 rule informs digital preservation and storage strategies. Recollection Wisconsin Digital Projects Maintain three copies of your digital files on two different storage media Toolkit 3-2-1 Rule with at least one copy stored off site. See: Storage Diversification, Digital Storage AASLH stands for the American Association for State and Local History. AASLH (American Association for State AASLH and Local History) In archives, access refers to the ability to locate and retrieve archival Society of American Archivists (SAA) Access information for use within applicable restrictions. Dictionary of Archival Terms An access copy is a reproduction of a document created for use by Curating Community Digital Collections patrons. The access copy may be lower quality for easier delivery over (CCDC) Glossary Access Copy email or use online. The access copy allows the preservation copy to remain safe from unintended changes. See: Preservation Copy Digital accessibility is the ability of a website, mobile application or What is digital accessibility? electronic document to be easily navigated and understood by a wide Accessibility range of users, including those users who have visual, auditory, motor or cognitive disabilities. Administrative metadata is information needed to help manage the digital Curating Community Digital Collections Administrative Metadata object, such as copyright and preservation information. See: Metadata. Glossary Analog refers to information that exists in nondigital format such as Curating Community Digital Collections printed or manuscript text, audio tapes or films, photographs or other Glossary Analog graphics, or 3-D objects. Digitization is the conversion of analog information into digital information. -

Digital Preservation.Pdf
Digital Preservation By Jean-Yves Le Meur project leader of CERN Digital Memory 100 AD End of cuneiform on tablets 350-50 BC Jupiter orbit Tablets -> British Museum 1800- 1300-1400 Jupiter orbit 2014 (again) The missing 29 Jan 2016 ‘rosetta’ tablet Digital preservation in a nutshell ● World wide Landscape ○ Rationale ○ Interesting initiatives ○ Good practices: OAIS ● The different Approaches The Digital “Dark Age” "We are nonchalantly throwing all of our data into what could become an information black hole without realizing it" Vint Cerf (vice-president of Google in Feb 2015) The Digital “Dark Age” ● Very large community worrying about the preservation of digital content ● Digital Preservation Coalition ● Open Preservation Foundation ● UNESCO PERSIST project, EU e-ARK project, National Libraries and Archives ● Many related conferences: iPRES series, etc. “This is not about preserving bits, It is about preserving meaning, much like the Rosetta Stone.” More than 70 major libraries destroyed over time: accidents, disasters, ethnocides How digital data evaporates (I) 1. Physical Obsolescence: Bit rot Ten 2. Redundancy failure Major 3. Technological Obsolescence of readers, formats, OS, HWs New 4. Lost in migrations ! Risks 5. Missing context: no codec ! How digital data evaporates (II) 6. Redundancy failure Ten 7. Economical Failures Major 8. Lost in transitions: people ! New 9. Corruption, mistake or attack 10. Dissipation: out of reach Risks Some examples at CERN ● The very first WWW pages ○ Reconstructed in 2013 - found again in 2018! -

Follow-Up Questions
Follow-Up Questions ASERL Webinar: “Intro to Digital Preservation #2 -- Forbearing the Digital Dark Age: Capturing Metadata for Digital Objects” Speaker = Chris Dietrich, National Park Service Session Recording: https://vimeo.com/63669010 Speaker’s PPT: http://bit.ly/10PKvu8 UPDATED – May 23, 2013 Tools 1. Is photo watermarking available using Windows Explorer? Microsoft Paint, which comes installed with Microsoft Windows, provides basic (albeit inelegant) watermarking capabilities. 2. Do Microsoft tools capture basic metadata automatically, without user intervention? Microsoft Office products capture very basic metadata automatically. The Author, Initials, and Company are captured automatically from a user’s Windows User Account settings. File system properties like File Size, Date, etc. are also automatically captured. The following Microsoft Knowledge Base articles provide details for each Microsoft Office product: http://office.microsoft.com/en-us/access-help/view-or-change-the-properties-for-an-office-file- HA010354245.aspx, http://office.microsoft.com/en-us/help/about-file-properties-HP003071721.aspx. Microsoft SharePoint can be configured to automatically capture metadata for items uploaded to libraries: http://office.microsoft.com/en-us/sharepoint-help/introduction-to-managed-metadata-HA102832521.aspx. 3. Can you recommend tools/services that leverage geospatial data that do not provide latitude & longitude information? For example, I want to plot a photo of “Mt Doom” on a map but have no coordinates…. Embedding geospatial coordinates in digital objects (often called “geotagging”) can be done with a number of software tools. GPS Photo Link (http://www.geospatialexperts.com/gps-photo%20link.php) allows users to add coordinates to embedded metadata manually, or by selecting a photo(s) and then clicking a point on a Bing Maps satellite image. -

Uncertainties of Digital Today's and Tomorrow's Igital Information And
Merit Research Journal of Education and Review Vol. 1(3) pp. 058-063, April, 2013 Available online http://www.meritresearchjournals.org/er/index.htm Copyright © 2013 Merit Research Journals Review Uncertainties of d igital information and preservation in today's and tomorrow’s generation: an idea Raghunadha T. Reddy 1, Dr. K. Kumar 1 and T. Sreenivasa Rao 2 1Librarian, SVCET, Chittoor-517127 2Assistant Librarian and Head, ANGRAU Regional Library. S.V. Agricultural College, Tirupati – 517 502 Accepted April 05, 2013 The digital information generated by organizations from domains such as government, cultural heritage, science and education, audio, video, films, health, insurance, banking, etc are part of our digital universe or each one is a digital universe in its own right . There is good understanding in the Library of preservation issues and of the constraints of preservation strategies, which are taken into a ccount in deciding what to take into the Library’s collections and how it should be managed. So this paper is brief discussion of an idea: uncertainties of digital information and preservation in today's and tomorrow's generation. Keywords: Digital Information, Preservation, Problems INTRODUCTION Preservation strategies in academic and research Requirements of India is conducted by Human Centered libraries are not new concepts. However, with an Design and Computing Group of C -DAC, Pune was increasing amoun t of digital content, organizations have entrusted with the responsibility to produce the national to cope with a new set of preservation issues. Digital study report on digital preservation requirements of India preservation is in its infancy worldwide and presents by Department of Information Technology, Government some difficult technological issues. -

Problems of Digital Sustainability
Acta Polytechnica Hungarica Vol. 7, No. 3, 2010 Problems of Digital Sustainability Tamás Szádeczky Department of Measurement and Automation, Kandó Kálmán Faculty of Electrical Engineering, Óbuda University Tavaszmező u. 17, H-1084 Budapest, Hungary [email protected] Abstract: The article introduces digital communication by drawing comparisons between the histories of digital and conventional written communication. It also shows the technical and legal bases and the currently reached achievements. In relation to the technical elements, it acquaints the reader with the development and current effects of computer technology, especially cryptography. In connection with the legal basis, the work presents the regulations which have emerged and made possible the legal acceptance of the digital signature and electronic documents in the United States of America, in the European Union and among certain of its member countries, including Hungary. The article reviews the regulations and the developed practices in the fields of e-commerce, electronic invoices, electronic records management and certain e-government functions in Hungary which are necessary for digital communication. The work draws attention to the importance of secure keeping and processing of electronic documents, which is also enforced by the legal environment. The author points to the technical requirements and practical troubles of digital communication, called digital sustainability. Keywords: electronic archive; digital sustainability; preservation; electronic signature; data security 1 Introduction We may distinguish three revolutions in the development of written communication [1]. The first revolution was the invention of alphabetical writing carrying phonetic value around 1300 BC., which segregated the text from the content. The second revolution in the 15th Century was the book printing invented by Gutenberg, Johannes Gensfleisch, which made written material widely available. -

Introduction to Digital Preservation: Why Preserve? How to Preserve?
Introduction to Digital Preservation: Why Preserve? How to Preserve? Dr. Ross King Austrian Institute of Technology Outline • Introduction: Digital Universe • Digital Preservation Challenges – Information Retrieval past and present – Bit-stream Preservation – Logical Preservation • Digital Preservation Incentives – Markets – Incentives – Risks • Conclusions Introduction The Digital Universe The Digital Universe • Estimated volume of • Estimated growth rate: ca. 60% digital information • → 700 Exabytes in 2009! worldwide in 2007: 281 Exabytes Digital Information Created, Captured, and Replicated Worldwide 2000 1000 k kilo 1800 1000 2 M mega 1600 1000 3 G giga 1400 1200 1000 4 T tera 1000 5 1000 P peta 800 Exabytes 1000 6 E exa 600 1000 7 Z zetta 400 200 1000 8 Y yotta 0 2005 2006 2007 2008 2009 2010 2011 2012 source: Year “The Diverse and Exploding Digital Universe” IDC White Paper, March 2008 http://www.emc.com/collateral/analyst-reports/diverse-exploding-digital-universe.pdf The Digital Universe • Information creation is beginning to exceed storage capacity • Much of this information is – transient – redundant The Digital Universe Issues: • What is worth preserving? • How to preserve? • How to preserve so much? • How to ensure quality? • How to create incentives to preserve? The Digital Universe Issues: • What is worth preserving? • How to preserve? • How to preserve so much? • How to ensure quality? • How to create incentives to preserve? Part 1 Digital Preservation Challenges Digital Preservation • standards, best-practices, and technologies -

A DIY Approach to Digital Preservation
Practical Digital Solutions: A DIY Approach to Digital Preservation by Tyler McNally A Thesis Submitted to the Faculty of Graduate Studies of the University of Manitoba In Partial Fulfillment of the Requirements of the Degree of MASTER OF ARTS Department of History (Archival Studies) Joint Masters Program University of Manitoba/University of Winnipeg Winnipeg, Manitoba Copyright © 2018 by Tyler McNally Table of Contents Abstract…………………………………………………………...i AcknoWledgments…………………………………………….ii Acronym IndeX…………………………………………………iii Introduction……………………………………………………..1 Chapter 1………………………………………………………….12 Chapter 2………………………………………………………….54 Chapter 3………………………………………………………….81 Conclusion ……………………………………………………….116 Bibliography……………………………………………………..125 iii Abstract Since the introduction of computers, archivists have had to find ways to deal with digital records. As more records are born digital (created through digital means) and digital technologies become more entrenched in hoW data is created and processed, it is imperative that archivists properly preserve these records. This thesis seeks to propose one possible solution to this issue. Rather than advocate for paid solutions or electronic record management systems, it advocates for more practical in-house DIY solutions. The first chapter lays out background information and the historiography of digital archiving in Canada at the federal level. The second chapter moves step-by-step through a Workflow developed at the University of Manitoba’s Faculty of Medicine Archives that lays out one possible DIY style solution. The third chapter is an audit of the WorkfloW from the second chapter against three important international standards for preserving digital information. iv Acknowledgments I would like to acknoWledge and thank Professors Thomas Nesmith and Greg Bak. Their role as professors of the Archival Studies program has been a great source of support and inspiration as well as their knowledge and passion for both archives and their students.