East German SIGINT Operations by Ben Fischer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
11701-19-A0558 RVH Landmarke 4 Engl
Landmark 4 Brocken ® On the 17th of November, 2015, during the 38th UNESCO General Assembly, the 195 member states of the United Nations resolved to introduce a new title. As a result, Geoparks can be distinguished as UNESCO Global Geoparks. As early as 2004, 25 European and Chinese Geoparks had founded the Global Geoparks Network (GGN). In autumn of that year Geopark Harz · Braunschweiger Land · Ostfalen became part of the network. In addition, there are various regional networks, among them the European Geoparks Network (EGN). These coordinate international cooperation. 22 Königslutter 28 ® 1 cm = 26 km 20 Oschersleben 27 18 14 Goslar Halberstadt 3 2 1 8 Quedlinburg 4 OsterodeOsterodee a.H.a.Ha H.. 9 11 5 13 15 161 6 10 17 19 7 Sangerhausen Nordhausen 12 21 In the above overview map you can see the locations of all UNESCO Global Geoparks in Europe, including UNESCO Global Geopark Harz · Braunschweiger Land · Ostfalen and the borders of its parts. UNESCO-Geoparks are clearly defi ned, unique areas, in which geosites and landscapes of international geological importance are found. The purpose of every UNESCO-Geopark is to protect the geological heritage and to promote environmental education and sustainable regional development. Actions which can infl ict considerable damage on geosites are forbidden by law. A Highlight of a Harz Visit 1 The Brocken A walk up the Brocken can begin at many of the Landmark’s Geopoints, or one can take the Brockenbahn from Wernigerode or Drei Annen-Hohne via Schierke up to the highest mountain of the Geopark (1,141 meters a.s.l.). -

Guides to German Records Microfilmed at Alexandria, Va
GUIDES TO GERMAN RECORDS MICROFILMED AT ALEXANDRIA, VA. No. 32. Records of the Reich Leader of the SS and Chief of the German Police (Part I) The National Archives National Archives and Records Service General Services Administration Washington: 1961 This finding aid has been prepared by the National Archives as part of its program of facilitating the use of records in its custody. The microfilm described in this guide may be consulted at the National Archives, where it is identified as RG 242, Microfilm Publication T175. To order microfilm, write to the Publications Sales Branch (NEPS), National Archives and Records Service (GSA), Washington, DC 20408. Some of the papers reproduced on the microfilm referred to in this and other guides of the same series may have been of private origin. The fact of their seizure is not believed to divest their original owners of any literary property rights in them. Anyone, therefore, who publishes them in whole or in part without permission of their authors may be held liable for infringement of such literary property rights. Library of Congress Catalog Card No. 58-9982 AMERICA! HISTORICAL ASSOCIATION COMMITTEE fOR THE STUDY OP WAR DOCUMENTS GUIDES TO GERMAN RECOBDS MICROFILMED AT ALEXAM)RIA, VA. No* 32» Records of the Reich Leader of the SS aad Chief of the German Police (HeiehsMhrer SS und Chef der Deutschen Polizei) 1) THE AMERICAN HISTORICAL ASSOCIATION (AHA) COMMITTEE FOR THE STUDY OF WAE DOCUMENTS GUIDES TO GERMAN RECORDS MICROFILMED AT ALEXANDRIA, VA* This is part of a series of Guides prepared -

Formerly, but on the Other Hand the Weather-Observing Airplane Is
formerly, but on the other hand the for safety in high-altitude cities like weather-observing airplane is rapidly Denver. At the meeting of the Amer- becoming one of the routine adjuncts ican Chemical Society here today, J. of meteorology. H. Eisemann, Dr. F. A. Smith and There is only one place in the world C. J. Merritt of the U. S. Bureau where similar records are obtained by of Standards reported on their ex- means of instruments attached to the periments on the changes needed in car of a mountain railroad.1 The gas appliances for safe operation at mountain in question is the Zugspitze, high altitudes. the highest peak in Germany, and the In general, they found that the car, suspended from an overhead maximum safe rate for the supply cable, travels a vertical distance of of gas at sea level, measured in heat nearly a mile in 16 minutes; several units consumed per hour, is reduced trips being made between the summit by approximately three to four per and the base of the mountain every cent for each thousand feet of alti- day. A set of instruments that make tude; but the number of cubic feet continuous records of barometric per hour of gas of given composition pressure, air temperature and humid- which can be burned completely is ity is fastened above the roof of the practically independent of altitude. car.—C. F. Talman in Why the The area of flue opening which will Weather? (SS). permit the flow of enough air to in- Gas stoves in mountain cities have sure complete combustion increases special air requirements. -

Verbände Und Truppen Der Deutschen Wehrmacht Und Waffen SS Im Zweiten Weltkrieg 1939-1945
GEORG TESSIN Verbände und Truppen der deutschen Wehrmacht und Waffen SS im Zweiten Weltkrieg 1939-1945 ZWEITER BAND: Die Landstreitkräfte 1—5 Bearbeitet auf Grund der Unterlagen des Bundesarchiv-Militärarchivs Herausgegeben mit Unterstützung des Bundesarchivs und des Arbeitskreises für Wehrforschung VERLAG E. S. MITTLER & SOHN GMBH. • FRANKFURT/MAIN 1" ( 1 Einleitung und Quellen Einleitung und Quellen Das vorliegende Werk hat es sich zum Ziel gesetzt, in einer zusammenfassenden Arbeit die Verbände und Einheiten des Kriegsheeres 1939—1945 von der Spitze bis hinab zu den Einheiten in Bataillons- und Abteilungsstärke darzustellen. Es setzt eine vom gleichen Verfasser in der Schriftenreihe des Bundesarchivs erschienene „Formations geschichte der Wehrmacht 1933-1939" J) fort. Die Arbeit soll gleichzeitig als ein Hilfsmittel für die wissenschaftliche Erfor schung des Krieges, wie auch als schnelles und für den Laien gut zu überschauendes Nachschlagewerk für den Gebrauch von Behörden, besonders in Versorgungs fragen, dienen. Bei der Überfülle von Material mußten die Angaben, besonders die über den Einsatz, äußerst knapp gehalten und viele bekannten Daten weggelassen werden. Trotz der Beschränkung wird da. Werk etwa 12 Bände umfassen. Es bietet eine Gesamt schau, Einzelangaben hingegen nur in strengster Auswahl. Die meisten von uns, die den Krieg mitgemacht haben, werden über ihre Einheit umfassender orientiert sein. Ober die Entwicklung aller Wehrmachtteile in ihrer Gesamtheit (Heer, Luftwaffe, Marine, Waffen SS) 2) dürfte auch der Organisationsbearbeiter an verantwortlicher Stelle wäh rend des Krieges kaum unterrichtet gewesen sein. So spiegelt die Arbeit den Aufbau der Wehrmacht wider. a) Literatur An Literatur erschien bereits 1953 eine Arbeit von Siegler über die höheren Dienst stellen der deutschen Wehrmacht.3) Sie erschien zu einem Zeitpunkt, in dem echte Unterlagen kaum zur Verfügung standen und ist auch heute noch als Nachschlagewerk ein gutes Hilfsmittel. -

Witterungsverlauf in Deutschland Im Jahr 2007 Temperatur- Und Niederschlagsverteilung
©Ges. zur Förderung d. Erforschung von Insektenwanderungen e.V. München, download unter www.zobodat.at Atalanta 39 (1-4): 4-12, Würzburg (2008), ISSN 0171-0079 Witterungsverlauf in Deutschland im Jahr 2007 Temperatur- und Niederschlagsverteilung Zusammengestellt von Stefanie Biermann Januar:Die höchsten Mitteltemperaturen gab es in diesem Monat im Nordwesten, insbesondere an der Nordsee und am Rhein. Dort lagen die Monatswerte teilweise über 6°C (Frankfurt a. M. 6,1°C, Freiburg i. Br. 6,2°C, Aachen, Karlsruhe und Mannheim 6,3°C, Köln 6,5°C, Düsseldorf 6,7°C, Norderney 7,0°C, Helgoland 7,2°C). Sonst bewegten sich die Monatsmittel in den Niederungen meist um 5°C. Im Osten und Süden Deutschlands lagen die Monatsmittelwerte in den Niederungen teilweise noch etwas tiefer. Örtlich lagen sie unter 3°C (Hof/ Nordbayern 2,6°C, Zwiesel/ Bayrischer Wald 2,0°C, Sonneberg/ Thüringen 1,6°C). Erst oberhalb 1500 m blieben die Mitteltemperaturen mehrheitlich unter 0°C. Nur auf den höchsten deutschen Alpengipfeln lagen sie unter -5°C (Zugspitze -8,5°C). In ganz Deutschland war es viel zu mild für die Jahreszeit. Für zahlreiche Stationen war es der wärmste Januar seit Beginn der Meßreihen. Besonders große Abweichungen von den Normalwerten ergaben sich in Ostdeutschland und in den Niederungen Südbayerns. D ort lagen die Differenzen zu den Bezugswerten teilweise über 6°C (Berlin-Schönefeld, Ingoldstadt und Regensburg 6,1°C, Cottbus 6,3°C, Passau 6,4°C, München-Flughafen und Straubing 6,5°C). Im Westen und Südwesten waren die Abweichungen etwas geringer. Dort lagen die Differenzen meist unter 5°C. -

Professional TV Broadcast Antennas UHF Band IV/V 470 - 862 Mhz (Analogue TV) As It Stands Per January 2020
References Professional TV Broadcast Antennas UHF Band IV/V 470 - 862 MHz (Analogue TV) KATHREIN Broadcast GmbH Ing.-Anton-Kathrein-Str. 1-7, 83101 Rohrdorf, Germany Telephone +49 8031 6193 100, E-mail: [email protected] www.kathrein-bca.com References Professional TV Broadcast Antennas UHF Band IV/V 470 - 862 MHz (Analogue TV) as it stands per January 2020 Country Station Country Station Country Station Albania Tirana Brazil Anhanguera Canada Vaughan 1, ON Araraquara Vaughan 2, ON Algeria Akfadou Belo Horizonte Victoria Algier Cabo Branco Wawa Morro di Pena Wharncliffe Angola Luanda 1 Sao Paulo Windsor Luanda 2 Luanda 3 Bulgaria Petrohan Chile Santiago de Chile Argentina Antina Cambodia Bantea Meanchey China Beijing Buenos Aires Kampong Thom Beijing Buenos Aires Koh Kong Canton Mondulkiri Dongguan Australia Gosford Phnom Penh 1 Guangsong Phnom Penh 2 Guangzhou Austria Dobratsch Henan TV Tower 1 Dünserberg Cameroon Ekondo Titi Henan TV Tower 2 Freinberg Huiyang Gaisberg Canada Abbotsford, BC Jedong Galgenberg Alanwater Jiangmen Goldeck Barrie Maoming Hauser-Kaibling Barry's Bay Ningxia Hirschenstein Baton Windsor Shantou Hohe Salve Brethour Shenyang Jauerling Calgary Shenzhen 1 Katrin Charlottetown Shenzhen 2 Kitzbühler Horn Chilliwack, BC Shijiazhuang Koralpe Duck Lake Swatow Linz Edmonton Tianjin Mattersburg-Heub. Evansville Yin Chuan Mugl Evanturel Zhuhai Neumarkt-Kulmera. Fort Erie Patscherkofel Grand Fonds Cyprus Selvilitepe Pfänder Gravelbourg Saalfelden Harris Township Czech Republic Brno-Hady Schöckl 1 Hawk Junction Brno-Kojal Schöckl 2 Kenogami Lake Bukova Hora Sonnwendstein 1 Lac Ste Therese Hradec Kralove Sonnwendstein 2 Longlac Klatovy Steyr Manotick Olomouc-Radikov Wachberg Mount Royal Pilsen Zugspitze Orilllia Prag-Cukrak Osnaburgh Pribram Barbados Sturges Ottawa Radikov Parry Sound Rychnov Belgium Brüssel 1 Pays Plat Susice Brüssel 2 Penetanguis Svitavy Brüssel-Everberg Peterborough 1 Tabor Brüssel-Financiet. -

BERGVERLAG ROTHER Rother Wanderführer Harz Von Bernhard Pollmann ISBN 978-3-7633-4257-0
entnommen aus dem BERGVERLAG ROTHER Rother Wanderführer Harz von Bernhard Pollmann ISBN 978-3-7633-4257-0 6.30 Std. 16 Schierke – Brocken – Wurmberg 8C Über die beiden höchsten Berge im Harz Mit Brocken und Wurmberg verbindet diese aussichtsreiche Rundwanderung die beiden höchsten erwanderbaren Harzberge. Ausgangspunkt: Schierke (640 m), sie- auf dem Wurmbergsteig ist sehr steil, vor he Tour 15. allem bei Nässe ist Vorsicht geboten. Höhenunterschied: 700 m. Einkehr: Brocken, Wurmberg. Anforderungen: Der Aufstieg ist steil Variante: Vom Dreieckigen Pfahl kann und erfolgt zum Teil über grobblockige man auch direkt zurück nach Schierke Fels- und Wurzelwege. Auch der Abstieg gehen, ca. 60 Min. kürzer. Blick vom Wurmberg zum Brocken. Vom Wintersportplatz Schierke erfolgt der Aufstieg zum Brocken auf dem Eckerlochstieg wie in Tour 15. Vom Brocken geht es auf der für den öffentli- chen Verkehr gesperrten Brockenstraße zurück, bis an der Abzweigung des Neuen Goethewegs die Trasse der Brockenbahn kreuzt. Aussichtsreich führt der Goetheweg im Gleichlauf mit dem Harzer Grenzweg parallel zur Trasse der Brockenbahn abwärts Richtung Torfhaus, zuletzt auf einem Be- tonplattenweg aus der Zeit des Warschauer Pakts. Beim Eckersprung ver- lässt der Grenz- den Goetheweg und führt am Bodesprung, der Quelle der Kalten Bode, vorbei zur Verzweigung beim Rastplatz Dreieckiger Pfahl. Wer abkürzen will, kann hier direkt nach Schierke zurückwandern, während der Grenzweg der ehemaligen innerdeutschen Demarkationslinie in einem teils verheideten, teils vermoorten Gebiet weiterfolgt. Nach sachtem Abstieg beginnt der Weg an einer Brockenblick-Verzwei- gung wieder anzusteigen, bis der kurze, steile Aufstieg zum Wurmberg ausgeschildert ist. Vom Gipfel mit der Sprungschanze geht es auf demsel- ben Weg zurück zum Grenzweg, der wenig später die Raststelle im Sattel zwischen Wurm- und Winterberg Brocken erreicht. -

U/Pb Dating and Geochemical Characterization of the Brocken and the Ramberg Plutons, Harz Mountain, Germany J
Geophysical Research Abstracts, Vol. 9, 03255, 2007 SRef-ID: 1607-7962/gra/EGU2007-A-03255 © European Geosciences Union 2007 U/Pb dating and geochemical characterization of the Brocken and the Ramberg Plutons, Harz Mountain, Germany J. Ilgner (1), T. Jeffries (2), D. Faust (1), B.Ullrich (3) and U. Linnemann (4) (1) Institut für Geographie, TU Dresden, Germany, (2) Natural History Museum, London, UK, (3) Institut für Geotechnik, TU Dresden, (4) Staatliche Naturhistorische Sammlungen Dresden, Germany, ([email protected] / Fax: +41 31 631 8511 / Phone: +41 31 631 8019) The Harz Mountains (Germany) form a part of the Variscan basement in the south- ern part of the Rheno-Hercynian Zone of the Central European Variscides. The area is situated close to the suture between Laurussia and Gondwana represented by the Mid-German Crystalline Zone. The Harz Mountains became intruded by a number of granitoids that are believed to be related to the Variscan orogeny culminating in Devono-Carboniferous time. The two major granitoids in the Harz Mountains are rep- resented by the Brocken and the Ramberg plutons. We dated zircons of two samples from the marginal facies of the Brocken and the Ramberg granites in the Harz Mountains using U/Pb single zircon dating by a Laser- ICP-MS. The measurements of the youngest population of needle-shaped magmatic zircons show a concordia age of 283 ± 2.1 Ma for the Brocken granite and a concordia age of 283 ± 2.8 Ma for the Ramberg granite. Both overlapping results are interpreted to reflect the age of intrusion of these two granitoids. -

Wunderbar Wanderbar – Unser NRW!
Seite 06 Seite 16 Seite 18 Sagenumwobener Rheinsteig Märchenhaftes Weserbergland Aussichtsreiches Siegerland Wunderbar wanderbar – unser NRW! Unterwegs mit Bus und Bahn Ausgabe 2012 NRW lädt zum Wandern ein Hinweise: Alle Touren sind bequem mit Bus und Bahn zu erreichen. Für die An- und Abreise empfi ehlt sich das SchönerTagTicket NRW – erhältlich für Gruppen und Alleinreisende. Auf unserer Internetseite finden Sie Fahrplan- auskünfte und weitere Informationen zum NRW-Tarif. Vorwort von Manuel Andrack 4 Dort halten wir darüber hinaus zur besseren Auf dem Rheinsteig von Niederdollendorf Orientierung unterwegs, detaillierte Wanderkarten nach Rhöndorf 6 für Sie bereit: www.nahverkehr.nrw.de Auf dem Rothaarsteig rund um Brilon 8 Am Lago Maggiore des Ruhrgebiets 10 Auf dem Klompenweg von Wesel nach Hünxe 12 Auf den Klippen der Weser nach Höxter 16 Auf dem Kindelsbergpfad im Siegerland 18 HALLE HOHE MARK In der Rureifel von Heimbach HÖXTER nach Blens 20 WESEL ROTHAARSTEIG Auf dem Grat des Teutoburger Walds ESSEN zwischen Borgholzhausen und Halle 22 In der Hohen Mark von Maria Veen KROMBACH nach Reken 24 Gewinnspiel: RHEINSTEIG NRW-Wanderbahnhof 2012 26 Impressum 28 HEIMBACH 2 Wunderbar wanderbar! 3 Das Ticket für Wanderfans: Welche Wandertour soll es sein? Lieber die Vorwort Mit dem SchönerTagTicket NRW mit einer großen sportlichen Herausforde- derer in ganz NRW mobil und können sind alle Wan- rung oder die mit besonderem historischem Nahverkehrsmittel nutzen. Das Schöner- Flair? Jeder Wandertyp ist anders, und was TagTicket NRW für 37,50 Euro eignet sich dem einen gefällt, muss der andere noch lange für Gruppen von bis zu fünf Personen bzw. nicht mögen. Bei der Auswahl einer passen- Eltern/Großeltern mit beliebig vielen Kin- den Tour helfen die Andrack-Sterne in jeder dern/Enkeln bis einschließlich 14 Jahre. -
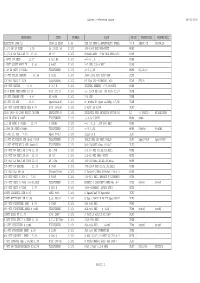
Subject Reference Dbase 09-05-2006
Subject reference dbase 09-05-2006 ONDERWERP TYPE NUMMER BIJZ GROEP TREFWOORD1 TREFWOORD2 ELECTRON 1958.12 1958.12 ELEC Z 46 TEK CX GEVR L,KWANTONETC KUBEL TS-N KERST CX LW,KW,LO 0,5/1 KW LW SEND 2.39 As 33/A1 34 Z 101 100-1000 KHZ MOB+FEST MOBS 0,7/1,4 KW SEND AS 60 10.40 AS 60 Z 101 FRUEHE AUSF 3-24 MHZ MOB+FEST MOBS 1 KWTT KW SEND 11.37 S 521 Bs Z 101 =+/-G 1,5.... MOBS 1 KWTT SHORT WAVE TR 5.36 S 486F Z 101 3-7 UND 2,5-6 MHZ MOBS 1 kW KW SEND S 521Bs TELEFUNKEN Z 172 +/-G 1,2K MOBS G1,2K+/- 10 WTT TELEF SENDER 10.34 S 318H Z 101 1500-3333 KHZ GUSS GEH SCHS 100 WTT SEND S 317H TELEFUNKEN Z 172 RS 31g 100-800METER alt SCHS S317H 100 WTT SENDER 4.33 S 317 H Z 101 UNIVERS SENDER 377-3000KHZ MOBS 15 W EINK SEND EMPF 10.35 Stat 272 B Z 101 +/- 15 W SE 469 SE 5285 F1/37 TRSE 15 WTT KARREN STN 4.40 SE 469A Z 101 3-5 MHZ TRSE 15 WTT KW STN 10.35 Spez804/445 Z 101 S= 804Bs E= Spez 445dBg 3-7,5M TRSE 150 WTT LANGW SENDE ANL 8.39 Stat 1006aF Z 101 S 427F SA 429F FLFU 1898-1938 40 JAAR RADIO IN NED SWIERSTRA R. Z 143 INLEGVEL VAN SWIERSTA PRIVE'38 LI 40 RADIO!! WILHELMINA 1kW KW SEND S 486F TELEFUNKEN Z 172 +/-2,5-7,5MHZ MOBS S486 1,5 LW SEND S 366Bs 11.37 S 366Bs Z 101 =+/- G1,5...100-600 KHZ MOBS 1,5kW LW SEND S366Bs TELEFUNKEN Z 172 +/-G 1,5L MOBS S366Bs S366BS 20 WTT FL STN 3.35 Spez 378mF Z 101 TELEF D B FLFU 20 WTT FLUGZEUG STN Spez 378nF TELEFUNKEN Z 172 URALT ANL LW FEST FREQU FLFU Spez378nF Spez378NF 20 WTT MITTELWELL GER Stat901 TELEFUNKEN Z 172 500-1500KHZ Stat 901A/F FLFU 200 WTT KW SEND AS 1008 11.39 AS 1008 Z 101 2,5-10 MHZ A1,A2,A3,HELL -

Bodenübersichtskarte Von Deutschland 1:3.000.000
Bodenübersichtskarte von Deutschland 1 : 3 000 000 LEGENDE Bodenübersichtskarte von Deutschland 1 : 3 000 000 N L E S N I Böden der Küstenregion und Moore Tschernosem-ParabraunerdeParabraunerde-Tschernosem E N H E O T S E C R S D S Podsol-RegosolRegosol I F O R S I E E ParabraunerdeFahlerdePseudogley-ParabraunerdePseudo- I S L R E A F N gley D Wattboden D R E O N S r nal e a d K D E i V O MarschbodenKleimarsch ParabraunerdeFahlerdeBraunerde R R Kalkmarsch O - P e N e O s t M s M O E R - N Niedermoorboden PseudogleyParabraunerde-PseudogleyParabraunerde d r w o o Peene N n Moorgley Gley I N S E L N r Rega C H E a I S I E S W F R T O S Hochmoorboden M E C K L OSTFRIESLAND E N HAMBURG B Böden der Berg- und Hügelländer sowie der Mittelgebirge l U Kana R - Jade- G ms Müritz E I S C RendzinaBraunerde-RendzinaPararendzina H K E R S E E A Böden der breiten Flusstäler einschließlich Terrassenflächen ! N P E L A T T E M L B R Wilseder Berg E Bundö Ndiedeernun gdener breiten Flusstäler # E al K kan BREMEN P R I G N I T Z C üsten - L Ü N E B U R G E R U K AuenbodenGley BraunerdeTerra fusca e H h t u c r n ts a t E Gley-Tschernosem Parabraunerde D e H E I D E n a lb e v r e fd D N O o - D Rendzina o S E H R ! A e i t e L rt n a a W - S K E AuenbodenGley Pelosol-BraunerdePelosol-Pseudogley -

How the Germans Brought Their Communism to Yemen
Miriam M. Müller A Spectre is Haunting Arabia Political Science | Volume 26 This book is dedicated to my parents and grandparents. I wouldn’t be who I am without you. Miriam M. Müller (Joint PhD) received her doctorate jointly from the Free Uni- versity of Berlin, Germany, and the University of Victoria, Canada, in Political Science and International Relations. Specialized in the politics of the Middle East, she focuses on religious and political ideologies, international security, international development and foreign policy. Her current research is occupied with the role of religion, violence and identity in the manifestations of the »Isla- mic State«. Miriam M. Müller A Spectre is Haunting Arabia How the Germans Brought Their Communism to Yemen My thanks go to my supervisors Prof. Dr. Klaus Schroeder, Prof. Dr. Oliver Schmidtke, Prof. Dr. Uwe Puschner, and Prof. Dr. Peter Massing, as well as to my colleagues and friends at the Forschungsverbund SED-Staat, the Center for Global Studies at the University of Victoria, and the Political Science Depart- ment there. This dissertation project has been generously supported by the German Natio- nal Academic Foundation and the Center for Global Studies, Victoria, Canada. A Dissertation Submitted in (Partial) Fulfillment of the Requirements for the- Joint Doctoral Degree (Cotutelle) in the Faculty of Political and Social Sciences ofthe Free University of Berlin, Germany and the Department of Political Scien- ceof the University of Victoria, Canada in October 2014. This work is licensed under the Creative Commons Attribution-NonCommer- cial-NoDerivs 4.0 (BY-NC-ND) which means that the text may be used for non- commercial purposes, provided credit is given to the author.