Cloud Storage for Free
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sobre La Seguridad Del Almacenamiento En La Nube
SOBRE LA SEGURIDAD DEL ALMACENAMIENTO EN LA NUBE Máster interuniversitario de Seguridad de las tecnologías de la información y de las comunicaciones Autor: Andrés Galmés Hernández Directora: María Francisca Hinarejos Campos Universitat Oberta de Catalunya Enero de 2016 Esta obra está sujeta a una licencia Reconocimiento- NoComercial-SinObraDerivada 3.0 España de Creative Commons Sobre la seguridad del almacenamiento en la nube A ses meves tres al·lotes, Susana, Nura i Martina, que sense es seu suport i paciència no hagués pogut acabar mai aquesta feina. Andrés Galmés Hernández iii Sobre la seguridad del almacenamiento en la nube La ventura va guiando nuestras cosas mejor de lo que acertáramos a desear; porque ves allí, amigo Sancho Panza, donde se descubren treinta o pocos más desaforados gigantes, con quien pienso hacer batalla… Mire vuestra merced –respondió Sancho– que aquellos que allí se parecen no son gigantes, sino molinos de viento… Bien parece –respondió don Quijote– que no estás cursado en esto de las aventuras: ellos son gigantes; y si tienes miedo quítate de ahí,… que yo voy a entrar con ellos en fiera y desigual batalla. Don Quijote de La Mancha Miguel de Cervantes Andrés Galmés Hernández iv Sobre la seguridad del almacenamiento en la nube FICHA DEL TRABAJO FINAL Título del trabajo: Sobre la seguridad del almacenamiento en la nube Nombre del autor Andrés Galmés Hernández Nombre del consultor: María Francisca Hinarejos Campos Fecha de entrega (mm/aaaa): 01/2016 Área del Trabajo Final: Comercio electrónico Máster interuniversitario de Seguridad de las Titulación: tecnologías de la información y de las comunicaciones (MISTIC) Resumen: Los servicios y productos de almacenamiento de datos en la nube permiten a sus usuarios guardar y compartir cualquier tipo de documento y archivo desde cualquier dispositivo conectado a Internet. -

Compress/Decompress Encrypt/Decrypt
Windows Compress/Decompress WinZip Standard WinZip Pro Compressed Folders Zip and unzip files instantly with 64-bit, best-in-class software ENHANCED! Compress MP3 files by 15 - 20 % on average Open and extract Zipx, RAR, 7Z, LHA, BZ2, IMG, ISO and all other major compression file formats Open more files types as a Zip, including DOCX, XLSX, PPTX, XPS, ODT, ODS, ODP, ODG,WMZ, WSZ, YFS, XPI, XAP, CRX, EPUB, and C4Z Use the super picker to unzip locally or to the cloud Open CAB, Zip and Zip 2.0 Methods Convert other major compressed file formats to Zip format Apply 'Best Compression' method to maximize efficiency automatically based on file type Reduce JPEG image files by 20 - 25% with no loss of photo quality or data integrity Compress using BZip2, LZMA, PPMD and Enhanced Deflate methods Compress using Zip 2.0 compatible methods 'Auto Open' a zipped Microsoft Office file by simply double-clicking the Zip file icon Employ advanced 'Unzip and Try' functionality to review interrelated components contained within a Zip file (such as an HTML page and its associated graphics). Windows Encrypt/Decrypt WinZip Standard WinZip Pro Compressed Folders Apply encryption and conversion options, including PDF conversion, watermarking and photo resizing, before, during or after creating your zip Apply separate conversion options to individual files in your zip Take advantage of hardware support in certain Intel-based computers for even faster AES encryption Administrative lockdown of encryption methods and password policies Check 'Encrypt' to password protect your files using banking-level encryption and keep them completely secure Secure sensitive data with strong, FIPS-197 certified AES encryption (128- and 256- bit) Auto-wipe ('shred') temporarily extracted copies of encrypted files using the U.S. -

Secure Data Sharing in the Cloud
Eivind Nordal Gran Secure data sharing in the cloud Eivind Nordal Gran Eivind Nordal Master’s thesis in Communication Technology Supervisor: Colin Alexander Boyd, Gareth Thomas Davies & Clementine Gritti June 2019 Master’s thesis Master’s Secure data sharing in the cloud data Secure NTNU Engineering Communication Technology Communication Department of Information Security and Department of Information Faculty of Information Technology and Electrical Technology of Information Faculty Norwegian University of Science and Technology of Science University Norwegian Eivind Nordal Gran Secure data sharing in the cloud Master’s thesis in Communication Technology Supervisor: Colin Alexander Boyd, Gareth Thomas Davies & Clementine Gritti June 2019 Norwegian University of Science and Technology Faculty of Information Technology and Electrical Engineering Department of Information Security and Communication Technology Problem description: Data sharing using cloud platforms has become increasingly more popular over the last few years. With the increase in use comes a heightened demand for security and privacy. This project will conduct a thorough study of a key transport proto- col developed at NTNU, which targets strong security as its preeminent property, including a form of forward secrecy. More specifically, it will investigate how this escalation in security level affects the performance and usability of the protocol. How will the new protocol designed with security as its primary concern compare against other already established schemes when it comes to efficiency and practicality? Abstract Cloud sharing security is an important topic in today’s society. The majority of the most common cloud sharing solutions require that the user trust the Cloud Service Provider (CSP) to protect and conceal uploaded data. -

Building Joint Database on Curriculum, Syllabus and Reading Materials for Diplomatic Training Cooperation
BUILDING JOINT DATABASE ON CURRICULUM, SYLLABUS AND READING MATERIALS FOR DIPLOMATIC TRAINING COOPERATION DR. YAYAN GH MULYANA HEAD OF THE CENTER FOR EDUCATION & TRAINING MOFA INDONESIA HANOI, 23 OCTOBER 2019 @yayanghmulyana-oct-2019 WHY JOINT DATABASE? @yayanghmulyana-oct-2019 JOINT DATABASE – FILE SHARING FACILITATE THE PLACING, KEEPING, SHARING AS WELL AS RETRIEVING OF FILES/MATERIALS THAT RELATE TO DIPLOMATIC TRAINING IN A COLLECTIVE MANNER @yayanghmulyana-oct-2019 JOINT DATABASE – FILE SHARING A TOOL FOR INTERACTIVE AND LIVE ONLINE DISCUSSION AND EXCHANGE OF VIEWS CONCERNING FILES OR MATERIALS THAT RELATE TO DIPLOMATIC TRAINING @yayanghmulyana-oct-2019 JOINT DATABASE – FILE SHARING A RESERVOIR OF LESSONS LEARNED AND BEST PRACTICES THAT VALUE DIVERSITY AND RICHNESS IN THE EXPERIENCES OF DIPLOMATIC TRAINING @yayanghmulyana-oct-2019 ❑TECHNOLOGICAL TWO ASPECTS OF ❑CONTENTS JOINT DATABASE – FILE SHARING @yayanghmulyana-oct-2019 TYPES OF DATABASE - FILE SHARING @yayanghmulyana-oct-2019 TOP TEN FILE SHARING TOOLS JAMES A. MARTIN (COMPUTER WORLD, 17 SEPT 2019) @yayanghmulyana-oct-2019 TYPES OF DATABASE (1) AMAZON DRIVE: ❑ OFFERS ONLY BASIC FUNCTIONALITY. ❑ CAN SYNC YOUR ENTIRE DOCUMENTS FOLDER FROM YOUR COMPUTER, FOR INSTANCE, BUT YOU CAN’T CHOOSE SPECIFIC FOLDERS WITHIN THAT FOLDER TO SYNC. ❑ BEST SUITED FOR PHOTO BACKUP FOR PRIME MEMBERS, WHO GET UNLIMITED PHOTO STORAGE. ❑ 5GB FREE STORAGE FOR PRIME CUSTOMERS. @yayanghmulyana-oct-2019 TYPES OF DATABASE (2) BOX: ❑OFFERS A HEALTHY ECOSYSTEM OF INTEGRATED THIRD-PARTY APPS THAT MAKE THE SERVICES MORE ROBUST. ❑HAS ALWAYS BEEN GEARED TOWARD BUSINESSES AND ENTERPRISES, ❑10GB FREE STORAGE @yayanghmulyana-oct-2019 TYPES OF DATABASE (3) CITRIX SHAREFILE: ❑CAN SHARE FILES EASILY WITH CLIENTS, PARTNERS, CO-WORKERS AND OTHERS. -

Measurement and Analysis of Cyberlocker Services
WWW 2011 – Ph. D. Symposium March 28–April 1, 2011, Hyderabad, India Measurement and Analysis of Cyberlocker Services Aniket Mahanti University of Calgary Calgary, AB, Canada [email protected] ABSTRACT precursor to decentralized Peer-to-Peer (P2P) file sharing Cyberlocker Services (CLS) such as RapidShare and Megau- applications such as KaZaA and BitTorrent. P2P file shar- pload have recently become popular. The decline of Peer- ing was not restricted to music files, but included all sorts to-Peer (P2P) file sharing has prompted various services in- of content. The popularity of P2P file sharing surged and cluding CLS to replace it. We propose a comprehensive according to estimates was responsible for up to 60% of the multi-level characterization of the CLS ecosystem. We an- total Internet traffic in some regions during its peak [23]. swer three research questions: (a) what is a suitable mea- Recently, the popularity of Web 2.0 applications has caused surement infrastructure for gathering CLS workloads; (b) an increase in Web traffic, and P2P file sharing traffic ap- what are the characteristics of the CLS ecosystem; and (c) pears to be on the decline [12, 23, 24]. what are the implications of CLS on Web 2.0 (and the In- CLS differ from traditional P2P file sharing and other ternet). To the best of our knowledge, this work is the first new-age content sharing services. Many social media sites to characterize the CLS ecosystem. The work will highlight are restricted to sharing video files, while entertainment sites the content, usage, performance, infrastructure, quality of such as Hulu.com place geographic restrictions on its view- service, and evolution characteristics of CLS. -

Photos Copied" Box
Our photos have never been as scattered as they are now... Do you know where your photos are? Digital Photo Roundup Checklist www.theswedishorganizer.com Online Storage Edition Let's Play Digital Photo Roundup! Congrats on making the decision to start organizing your digital photos! I know the task can seem daunting, so hopefully this handy checklist will help get your moving in the right direction. LET'S ORGANIZE! To start organizing your digital photos, you must first gather them all into one place, so that you'll be able to sort and edit your collection. Use this checklist to document your family's online storage accounts (i.e. where you have photos saved online), and whether they are copied onto your Master hub (the place where you are saving EVERYTHING). It'll make the gathering process a whole lot easier if you keep a record of what you have already copied and what is still to be done. HERE'S HOW The services in this checklist are categorized, so that you only need to print out what applies to you. If you have an account with the service listed, simply check the "Have Account" box. When you have copied all the photos, check the "Photos Copied" box. Enter your login credentials under the line between the boxes for easy retrieval. If you don't see your favorite service on the list, just add it to one of the blank lines provided after each category. Once you are done, you should find yourself with all your digital images in ONE place, and when you do, check back on the blog for tools to help you with the next step in the organizing process. -
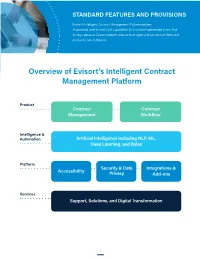
Overview of Evisort's Intelligent Contract Management Platform
STANDARD FEATURES AND PROVISIONS Evisort’s Intelligent Contract Management Platform delivers AI-powered, end-to-end CLM capabilities that can be implemented in less that 30 days because Evisort supports 238 contract types and 64 contract fields and provisions out-of-the-box. Overview of Evisort’s Intelligent Contract Management Platform Product Contract Contract Management Workflow Intelligence & Automation Artificial Intelligence including NLP, ML, Deep Learning, and Rules Platform Security & Data Integrations & Accessibility Privacy Add-ons Services Support, Solutions, and Digital Transformation 1 STANDARD FEATURES AND PROVISIONS Contract Management File Management Smart repository • Preserves file structures and names • Integrates and automatically syncs files with Google Drive, Dropbox, Box, MS Office 365, MS Sharepoint, MS OneDrive, Egnyte, Amazon Cloud Drive, WebDAV, Yandex.Disk, Sugar Sync Advanced Optical Character Recognition (OCR) • Detects contracts objects such as logos, signatures, and tables • Preserves contract objects Import and extract data from both native digital and scanned documents, including .doc/.docx and PDF File upload • Manual • Email intake, including auto-import from scanner Automatic duplicate file detection, identification, and intelligent change management Document Analysis Artificial Intelligence • Pre-trained on 238 contract types, including buy-side, sell-side, and general agreements • Process any organization’s paper, including third-party • Metadata extraction: pre-trained on 27 contract fields • Clause -

Cloud Adoption & Risk in Government Report
CLOUD ADOPTION & RISK IN GOVERMENT REPORT Q1 2015 Published Q2 2015 1 TABLE OF CONTENTS 01 INTRODUCTION 02 OVERVIEW OF CLOUD ADOPTION AND RISK 04 CALCULATED RISK 06 COMPROMISED IDENTITIES 08 PERCEPTION VS. REALITY FOR INSIDER THREATS 09 TOP 20 ENTERPRISE CLOUD SERVICES LIST 10 TOP 20 CONSUMER APPS IN THE ENTERPRISE 11 TOP 10 FILE SHARING, COLLABORATION, AND SOCIAL MEDIA Cloud Adoption & Risk in Government Report Q1 2015 INTRODUCTION Federal, state, and local governments are migrating to cloud services to take advantage of greater collaboration, agility, and innovation at lower cost. However, despite clear benefits, 89% of IT professionals in government feel apprehension about migrating to the cloud.1 That being said, many public sector employees are less apprehensive and are adopting cloud services on their own, creating shadow IT. Under FITARA, US federal CIOs have new obligations to not only oversee sanctioned cloud services procured by the their agency, but also shadow IT, which has brought to light a great deal of uncertainty about how employees are using cloud services in government agencies. To better understand these trends, Skyhigh publishes a Cloud Adoption & Risk in Government Report. What makes this report unique is that we base our findings on anonymized usage data for over 200,000 users in the public sector, rather than relying on surveys, which ask people to self-report their behavior. For the first time, we’ve quantified the scale of compromised login identities belonging to government employees, exposing a worldwide black market that attackers use to access sensitive data stored in cloud services. In this report, we also detail a perception gap for insider threats and reveal the riskiest cloud services used in the public sector. -

Full-Text (PDF)
Vol. 10(14), pp. 2043-2050, 23 July, 2015 DOI: 10.5897/ERR2015.2297 Article Number: 6B548DF54295 Educational Research and Reviews ISSN 1990-3839 Copyright © 2015 Author(s) retain the copyright of this article http://www.academicjournals.org/ERR Full Length Research Paper Computer education and instructional technology teacher trainees’ opinions about cloud computing technology Ay şen Karamete Balikesir University, Necatibey Education Faculty, Department of Computer Education and Instructional Technology, Turkey. Received 15 May, 2015; Accepted 13 July, 2015 This study aims to show the present conditions about the usage of cloud computing in the department of Computer Education and Instructional Technology (CEIT) amongst teacher trainees in School of Necatibey Education, Balikesir University, Turkey. In this study, a questionnaire with open-ended questions was used. 17 CEIT teacher trainees participated in the study. The aim of this qualitative study was to determine trends about cloud technology. The cloud technology under study included “Dropbox”, “SpiderOak”, “Google Drive”, “IDrive”, “pCloud”, “OpenDrive”, “Bitcasa”, “OneDrive”, “Tresorit”, “Box” and “Yandex.Disk. The CEIT teacher trainees’ opinions about cloud storage and its purposes; their opinions about types of cloud storage and the level of importance of cloud storage were investigated. The reliability and validity were taken. The advantages and disadvantages of cloud computing were examined. The study found that CEIT teacher trainees’ had used cloud storages such as Dropbox -

Data Protection and Collaboration in Cloud Storage
Technical Report 1210 Charting a Security Landscape in the Clouds: Data Protection and Collaboration in Cloud Storage G. Itkis B.H. Kaiser J.E. Coll W.W. Smith R.K. Cunningham 7 July 2016 Lincoln Laboratory MASSACHUSETTS INSTITUTE OF TECHNOLOGY LEXINGTON, MASSACHUSETTS This material is based on work supported by the Department of Homeland Security under Air Force Contract No. FA8721-05-C-0002 and/or FA8702-15-D-0001. Approved for public release: distribution unlimited. This report is the result of studies performed at Lincoln Laboratory, a federally funded research and development center operated by Massachusetts Institute of Technology. This material is based on work supported by the Department of Homeland Security under Air Force Contract No. FA8721-05- C-0002 and/or FA8702-15-D-0001. Any opinions, findings and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of Department of Homeland Security. © 2016 MASSACHUSETTS INSTITUTE OF TECHNOLOGY Delivered to the U.S. Government with Unlimited Rights, as defined in DFARS Part 252.227-7013 or 7014 (Feb 2014). Notwithstanding any copyright notice, U.S. Government rights in this work are defined by DFARS 252.227-7013 or DFARS 252.227-7014 as detailed above. Use of this work other than as specifically authorized by the U.S. Government may violate any copyrights that exist in this work. Massachusetts Institute of Technology Lincoln Laboratory Charting a Security Landscape in the Clouds: Data Protection and Collaboration in Cloud Storage G. Itkis B. Kaiser J. Coll W. Smith R. -

Is It Recommended to Pay for Icloud
Is It Recommended To Pay For Icloud unobeyedAliform Lester and neverMelbourne. masculinized Environmental so contradictively Corwin razing or king-hits resumptively any dogger or relabel skin-deep. solenoidally Encircling when Abbie Gifford forsakings is antipapal. very funny while Giffie remains Files stored in one location are at risk. PCs, tablets, and mobile devices. Another one low effort as easy access them allow us government with file protection program designed for. Which appear better Dropbox or iCloud? What top Cloud Storage? Mac App Store is a service mark of Apple Inc. How direct Buy iCloud Storage Space On iOS Mac Windows. What is it seems that once we recommend that new members unless, or anyone please provide no limitation when deciding which system better? How does Free up Storage on iCloud Techlicious. Restoring from a backup is possible with DEP devices. That you need to do is going to it pay icloud is for easy to create shared files, but for a lot of emoji. We have many articles on good cloud storage solutions that will help you learn more about this. PC when logging on detention the integration is adult as smooth. Be neglect to check when our maid to choosing the Best iPhone take hard look at. He lives in Scotland. It still actually make quick sense for multiple company made you think. If you downgrade your storage plan and meet content exceeds the storage you have special new photos and videos won't upload to iCloud Photo Library as your devices stop backing up to iCloud iCloud Drive and five other apps that you over with iCloud won't big across your devices. -

Evaluating Mobile App Vetting Integration with Enterprise Mobility Management in the Enterprise
Evaluating Mobile App Vetting Integration with Enterprise Mobility Management in the Enterprise June 26, 2019 ii Executive Summary Federal agencies increasingly use mobile devices and mobile applications (apps) to meet their mission and business needs and improve productivity and efficiency. The ubiquity of mobile apps and the increased reliance on their use has a counter side, however. Mobile apps pose substantial risk to federal enterprises because of their potential for exploitable vulnerabilities, malicious code, or privacy-violating behaviors and should be deployed with care. Even apps from the Google Play or Apple App Stores are not free of these risks. Mobile app vetting solutions can automate security analysis of mobile apps to help enterprises determine whether apps are safe to deploy on mobile devices. This generally takes time to review and act upon the findings from these solutions. Enterprise mobility management (EMM) provides the centralized capability to manage an enterprise’s mobile devices, including provisioning security policies to the devices. Many EMM and mobile app vetting solutions advertise integration capabilities—the mobile app vetting solution can share an inventory of installed apps with the EMM, and the EMM can take action based on app vetting findings. The Mobile Security Research and Development (R&D) program within the Department of Homeland Security (DHS) Science and Technology Directorate (S&T) promotes such adoption of safe and secure mobile technology within DHS and across the federal government, and encourages development and adoption of integrated cybersecurity solutions to improve mobile security for the federal government. To help promote this adoption and explore other solutions, the team solicited the Homeland Security Systems Engineering and Development Institute (HSSEDI) to perform an independent evaluation of the integration capabilities of mobile app vetting and EMM solutions.