Opaak: Using Mobile Phones to Limit Anonymous Identities Online
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UC Santa Barbara UC Santa Barbara Electronic Theses and Dissertations
UC Santa Barbara UC Santa Barbara Electronic Theses and Dissertations Title A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz Permalink https://escholarship.org/uc/item/6w76f8x7 Author Swift, Kathy Publication Date 2017 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA Santa Barbara A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Education by Kathleen Anne Swift Committee in charge: Professor Richard Duran, Chair Professor Diana Arya Professor William Robinson September 2017 The dissertation of Kathleen Anne Swift is approved. ................................................................................................................................ Diana Arya ................................................................................................................................ William Robinson ................................................................................................................................ Richard Duran, Committee Chair June 2017 A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz Copyright © 2017 by Kathleen Anne Swift iii ACKNOWLEDGEMENTS I would like to thank the members of my committee for their advice and patience as I worked on gathering and analyzing the copious amounts of research necessary to -

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

People Are Either Too Fake Or Too Real'': Opportunities And
Behavior in Online Communities CHI 2017, May 6–11, 2017, Denver, CO, USA “People Are Either Too Fake or Too Real”: Opportunities and Challenges in Tie-Based Anonymity Xiao Ma Nazanin Andalibi Louise Barkhuus Jacobs Institute, Cornell Tech College of Computing and The IT University of New York, NY, USA Informatics, Drexel University Copenhagen [email protected] Philadelphia, PA, USA Copenhagen, Denmark [email protected] [email protected] Mor Naaman Jacobs Institute, Cornell Tech New York, NY, USA [email protected] ABSTRACT affected social interactions and dynamics in offline and on- In recent years, several mobile applications allowed individ- line environments [11, 27]. Anonymity allows people to feel uals to anonymously share information with friends and con- less constrained by the expectations of their everyday iden- tacts, without any persistent identity marker. The functions of tities [3, 25], which in turn allows more candid and honest these “tie-based” anonymity services may be notably differ- self-expressions [1, 43]. Anonymity also leads users to dis- ent than other social media services. We use semi-structured close more information [52], which may result in positive interviews to qualitatively examine motivations, practices and emotional outcomes for the person disclosing [45]. On the perceptions in two tie-based anonymity apps: Secret (now de- other hand, the lack of attribution and responsibility in anony- funct, in the US) and Mimi (in China). Among the findings, mous environments can encourage malicious behaviors such we show that: (1) while users are more comfortable in self- as trolling [33] and cyberbullying [5, 6, 34]. It is no wonder disclosure, they still have specific practices and strategies to that society in general, and HCI researchers in particular, have avoid or allow identification; (2) attempts for de-identification been fascinated with the topic of anonymity. -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -
Sample2.Js Malware Summary
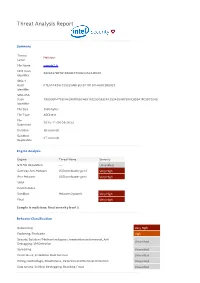
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Trolls Under the Bridge: Anonymous Online Comments and Gatekeeping in the Digital Realm
TROLLS UNDER THE BRIDGE: ANONYMOUS ONLINE COMMENTS AND GATEKEEPING IN THE DIGITAL REALM _______________________________________ A thesis presented to the faculty of the graduate school at the University of Missouri-Columbia ___________________________________________________________ in partial fulfillment of the requirements for the degree, master of arts ______________________________________________ by NOELLE M. STEELE Ryan J. Thomas, Thesis Supervisor DECEMBER 2013 The undersigned, appointed by the dean of the graduate school, have examined the thesis entitled TROLLS UNDER THE BRIDGE: ANONYMOUS ONLINE COMMENTS AND GATEKEEPING IN THE DIGITAL REALM presented by Noelle M. Steele, a candidate for the degree of master of arts, and hereby certify that, in their opinion, it is worthy of acceptance. __________________________________________ Dr. Ryan J. Thomas __________________________________________ Dr. Tim Vos ___________________________________________ Professor Joy Mayer ____________________________________________ Dr. Christina Wells ACKNOWLEDGEMENTS A special thank you to Sarah Smith-Frigerio for her unending encouragement, faithful guidance and witty responses that kept matters light when they might otherwise have been stressful. Many a graduate student would have lost their way without her prompt attention to every issue that cropped up and tireless dedication to resolving the problem. Endless thanks to my thesis chair, Dr. Ryan J. Thomas, for his attention to detail and refusal to allow me to settle for anything less than the most polished piece of work I could possibly produce. I owe the completion of this research to his persistence and enthusiasm for the project. And to the remainder of my thesis committee – Drs. Tim Vos and Christina Wells and Professor Joy Mayer – thank you for believing in my rough research idea and challenging me to refine it from the very beginning. -

The Community Industry: an Analysis of Reddit and /R/Socialism
THE COMMUNITY INDUSTRY: AN ANALYSIS OF REDDIT AND /R/SOCIALISM Richard Babb A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY May 2021 Committee: Radhika Gajjala, Advisor Samuel T McAbee, Graduate Faculty Representative Lara Lengel Yanqin Lu © 2021 Richard Babb All Rights Reserved iii ABSTRACT Radhika Gajjala, Advisor Social media is an increasingly important space for community formation and interactions. Coinciding with the rise of social media has been an increasing interest in leftist ideologies once outside the mainstream. This analysis seeks to understand the social media site Reddit.com’s enabling and constraining features on the community /r/socialism. Using the communicative theory of identity and Marxist media theory not only to look at Reddit and /r/socialism’s relationship, but five key functions of a media: capital-economic, media sales and media market function, commodity circulation, domination, and the audience. Employing a mixed-methods approach enabled various data to be analyzed and relationally understood. Qualitative content analysis was used to examine user’s salient topics and their uses for the community. Survey methods were deployed to the community to gather demographic data on the /r/socialism community and user opinions on the group’s relationship with Reddit. Finally, secondary documents were analyzed to provide greater context to the other findings. Findings from the content analysis of salient subjects showed a preference for contemporary capitalist critique, socialist quotations, and class issues. However, topics impacting women and other minority groups were light to nonexistent. -

Defamation Law in the Age of the Internet: Young People’S Perspectives
DEFAMATION LAW IN THE AGE OF THE INTERNET: YOUNG PEOPLE’S PERSPECTIVES Defamation Law in the Internet Age June 2017 Commissioned by the Law Commission of Ontario Prepared by Jane Bailey Valerie Steeves The LCO commissioned this paper to provide background research for its Defamation Law in the Internet Age project. The views expressed in this paper do not necessarily reflect the views of the LCO. DEFAMATION LAW IN THE AGE OF THE INTERNET: YOUNG PEOPLE’S PERSPECTIVES Prepared by: Jane Bailey1 and Valerie Steeves2 Prepared for: Law Commission of Ontario Final Report 15 June 2017 Table of Contents ACKNOWLEDGMENTS ........................................................................................................................................ 3 EXECUTIVE SUMMARY ....................................................................................................................................... 4 INTRODUCTION .................................................................................................................................................. 10 I. THE MEANING AND VALUE OF REPUTATION .............................................................................. 13 A. Understanding Online Reputation ..................................................................................................... 13 B. Creating an Online Reputation ............................................................................................................ 18 C. Avoiding Reputational Harm............................................................................................................... -

Automated Malware Analysis Report For
ID: 310931 Sample Name: 44S5D444F55G8222Y55UU44S4S.vbs Cookbook: default.jbs Time: 07:32:12 Date: 07/11/2020 Version: 31.0.0 Red Diamond Table of Contents Table of Contents 2 Analysis Report 44S5D444F55G8222Y55UU44S4S.vbs 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Startup 4 Malware Configuration 4 Yara Overview 4 Sigma Overview 4 Signature Overview 4 AV Detection: 5 Data Obfuscation: 5 Persistence and Installation Behavior: 5 Malware Analysis System Evasion: 5 HIPS / PFW / Operating System Protection Evasion: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 7 URLs 7 Domains and IPs 8 Contacted Domains 8 Contacted URLs 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 9 General Information 9 Simulations 10 Behavior and APIs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 11 General 11 File Icon 12 Network Behavior 12 TCP Packets 12 HTTP Request Dependency Graph 12 HTTP Packets 12 Code Manipulations 13 Statistics 13 Behavior 13 System Behavior 14 Analysis Process: wscript.exe PID: 6124 Parent PID: 3388 14 Copyright null 2020 Page 2 of 15 General 14 File Activities 14 File Created 14 File Written 14 Registry Activities 15 Analysis Process: wscript.exe PID: 5560 Parent PID: 6124 15 General 15 File Activities 15 Disassembly 15 Code Analysis 15 Copyright null 2020 Page 3 of -

LEAF:A Privacy-Conscious Social Network-Based Intervention Tool for IPV Survivors
LEAF:A Privacy-conscious Social Network-based Intervention Tool for IPV Survivors Balaji Palanisamy Sheldon Sensenig James Joshi Rose Constantinoy School of Information Sciences, University of Pittsburgh ySchool of Nursing, University of Pittsburgh fbpalan, sms233, jjoshi, [email protected] Abstract—Destructive relationship behavior directed from one acronym stands for lending encouragement, affirming futures. party to another in domestic relationships, both physical and These embody the vision for a system to provide support to emotional, is a common problem. When the behavior occurs those in difficult situations. in intimate relationships this is called intimate partner violence (IPV). There are many resources available to survivors of IPV LEAF is primarily focused on providing a secure privacy- in getting out of abusive situations, but the information is not conscious social-network based support system for survivors readily available and is not always easy to find. Furthermore, of intimate partner violence (IPV). We note that destructive once the survivor has escaped from the abusive situation, there relationship behavior directed from one party to another in are not many support type resources that are easily accessible, domestic relationships, both physical and emotional, is a especially to people lacking transportation and to those residing in rural or suburban areas. LEAF is being created to address the common problem. When the behavior occurs in intimate issues that arise from limits in physical community support. The relationships this is called intimate partner violence. LEAF acronym stands for lending encouragement, affirming futures. aims to provide an easily accessible support system to those These embody the vision for a system to provide support to those who have escaped from the abusive situation, especially to in difficult situations. -

The Loopix Anonymity System Ania M
The Loopix Anonymity System Ania M. Piotrowska and Jamie Hayes, University College London; Tariq Elahi, KU Leuven; Sebastian Meiser and George Danezis, University College London https://www.usenix.org/conference/usenixsecurity17/technical-sessions/presentation/piotrowska This paper is included in the Proceedings of the 26th USENIX Security Symposium August 16–18, 2017 • Vancouver, BC, Canada ISBN 978-1-931971-40-9 Open access to the Proceedings of the 26th USENIX Security Symposium is sponsored by USENIX The Loopix Anonymity System Ania M. Piotrowska Jamie Hayes Tariq Elahi University College London University College London KU Leuven Sebastian Meiser George Danezis University College London University College London Abstract cent leaks of extensive mass surveillance programs1, ex- posing such meta-data leads to significant privacy risks. We present Loopix, a low-latency anonymous commu- Since 2004, Tor [20], a practical manifestation of nication system that provides bi-directional ‘third-party’ circuit-based onion routing, has become the most popu- sender and receiver anonymity and unobservability. lar anonymous communication tool, with systems such Loopix leverages cover traffic and Poisson mixing—brief as Herd [33], Riposte [11], HORNET [10] and Vu- independent message delays—to provide anonymity and vuzela [46] extending and strengthening this paradigm. to achieve traffic analysis resistance against, including In contrast, message-based architectures, based on mix but not limited to, a global network adversary. Mixes and networks, have become unfashionable due to perceived clients self-monitor and protect against active attacks via higher latencies, that cannot accommodate real-time self-injected loops of traffic. The traffic loops also serve communications. However, unless cover traffic is em- as cover traffic to provide stronger anonymity and a mea- ployed, onion routing is susceptible to traffic analysis at- sure of sender and receiver unobservability.