Three Algorithmic Journeys * * * DRAFT 0.3 *
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
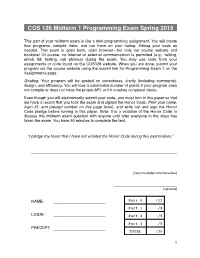
Programming Exam 1 on the Assignments Page
COS 126 Midterm 1 Programming Exam Spring 2015 This part of your midterm exam is like a mini-programming assignment. You will create four programs, compile them, and run them on your laptop. Debug your code as needed. This exam is open book, open browser—but only our course website and booksite! Of course, no internal or external communication is permitted (e.g., talking, email, IM, texting, cell phones) during the exam. You may use code from your assignments or code found on the COS126 website. When you are done, submit your program via the course website using the submit link for Programming Exam 1 on the Assignments page. Grading. Your program will be graded on correctness, clarity (including comments), design, and efficiency. You will lose a substantial number of points if your program does not compile or does not have the proper API, or if it crashes on typical inputs. Even though you will electronically submit your code, you must turn in this paper so that we have a record that you took the exam and signed the Honor Code. Print your name, login ID, and precept number on this page (now), and write out and sign the Honor Code pledge before turning in this paper. Note: It is a violation of the Honor Code to discuss this midterm exam question with anyone until after everyone in the class has taken the exam. You have 90 minutes to complete the test. “I pledge my honor that I have not violated the Honor Code during this examination.” ___________________________________________________________________ ___________________________________________________________________ [copy the pledge onto these lines] _____________________________ [signature] NAME: ______________________ Part 0 /12 Part 1 /8 LOGIN: ______________________ Part 2 /5 Part 3 /5 PRECEPT: ______________________ TOTAL /30 !1 The aliquot sum of a positive integer is the sum of its positive divisors other than itself (these divisors are called its proper divisors). -

POWERFUL AMICABLE NUMBERS 1. Introduction Let S(N) := ∑ D Be the Sum of the Proper Divisors of the Natural Number N. Two Disti
POWERFUL AMICABLE NUMBERS PAUL POLLACK P Abstract. Let s(n) := djn; d<n d denote the sum of the proper di- visors of the natural number n. Two distinct positive integers n and m are said to form an amicable pair if s(n) = m and s(m) = n; in this case, both n and m are called amicable numbers. The first example of an amicable pair, known already to the ancients, is f220; 284g. We do not know if there are infinitely many amicable pairs. In the opposite direction, Erd}osshowed in 1955 that the set of amicable numbers has asymptotic density zero. Let ` ≥ 1. A natural number n is said to be `-full (or `-powerful) if p` divides n whenever the prime p divides n. As shown by Erd}osand 1=` Szekeres in 1935, the number of `-full n ≤ x is asymptotically c`x , as x ! 1. Here c` is a positive constant depending on `. We show that for each fixed `, the set of amicable `-full numbers has relative density zero within the set of `-full numbers. 1. Introduction P Let s(n) := djn; d<n d be the sum of the proper divisors of the natural number n. Two distinct natural numbers n and m are said to form an ami- cable pair if s(n) = m and s(m) = n; in this case, both n and m are called amicable numbers. The first amicable pair, 220 and 284, was known already to the Pythagorean school. Despite their long history, we still know very little about such pairs. -

Mathematical Constants and Sequences
Mathematical Constants and Sequences a selection compiled by Stanislav Sýkora, Extra Byte, Castano Primo, Italy. Stan's Library, ISSN 2421-1230, Vol.II. First release March 31, 2008. Permalink via DOI: 10.3247/SL2Math08.001 This page is dedicated to my late math teacher Jaroslav Bayer who, back in 1955-8, kindled my passion for Mathematics. Math BOOKS | SI Units | SI Dimensions PHYSICS Constants (on a separate page) Mathematics LINKS | Stan's Library | Stan's HUB This is a constant-at-a-glance list. You can also download a PDF version for off-line use. But keep coming back, the list is growing! When a value is followed by #t, it should be a proven transcendental number (but I only did my best to find out, which need not suffice). Bold dots after a value are a link to the ••• OEIS ••• database. This website does not use any cookies, nor does it collect any information about its visitors (not even anonymous statistics). However, we decline any legal liability for typos, editing errors, and for the content of linked-to external web pages. Basic math constants Binary sequences Constants of number-theory functions More constants useful in Sciences Derived from the basic ones Combinatorial numbers, including Riemann zeta ζ(s) Planck's radiation law ... from 0 and 1 Binomial coefficients Dirichlet eta η(s) Functions sinc(z) and hsinc(z) ... from i Lah numbers Dedekind eta η(τ) Functions sinc(n,x) ... from 1 and i Stirling numbers Constants related to functions in C Ideal gas statistics ... from π Enumerations on sets Exponential exp Peak functions (spectral) .. -

Answer Key for Grade 5 – Quarter #4
Answer Key for Grade 5 – Quarter #4 (for both individual work and for group work) Notes for Parents: • This document is intended for parents and teachers – not for students. • This answer key doesn’t include all answers. Week 25 Individual Work: Triangular numbers: 1, 3, 6, 10, 15, 21,15, 21, 28, 36, 45, 55, 66, 78, 91, 105, 120, 136, 153, 171, etc. Sequences: 1) Add 6 to previous number: 9, 15, 21, 27, 33, 39, 45, 51, etc. 2) Multiply by 3: 7, 21, 63, 189, 567, 1701, etc. 3) Add previous two numbers: 4, 7, 11, 18, 29, 47, 76, 123, 199, 322, etc. 4) Powers of Two. 2, 4, 8, 16, 32, 64, 128, 256, 512, 1024, 2,048, 4,096, 8,192, etc. Group Assignment: for Tuesday. 1) no 2) yes 3) yes 4) no 5) yes 6) no 7) yes 8) yes 9) 13 is a factor of 403. 403 is in the 13’s table. If you divide 403 by 13, there is no remainder. 10) 43 and 68 11) 4 and 45 for Thursday. Goldbach’s Conjecture: 36: 5+31; 7+29; 13+23; 17+19 54: 7+47; 11+43; 13+41; 17+37; 23+31 90: 7+83; 11+79; 17+73; 19+71; 23+67; 29+61; 31+59; 37+53; 43+47 120: 7+113; 11+109; 13+107; 17+103; 19+101; 23+97; 31+89; 37+83; 41+79; 47+73; 53+67; 59+61. Week 26 Individual Work: Powers of 11: 11, 121, 1331, 14,641, 161,051, 1,771,561, 19,487,171, 214,358,881, 2,357,947,691, etc. -

GENERATING a PRIME NUMBER FUNCTION Ppppp Pf 1
GENERATING A PRIME NUMBER FUNCTION We have shown in several earlier notes that any positive integer has associated with it a number fraction- {sum of the divisors of N (N 1)} ( (N ) (N 1) f (N ) N N , where (N) is the sigma function of number theory. The function f(N) , which is a rational fraction, has the important property that it vanishes if and only if N is a prime number. Proceeding to higher powers of the primes p, we have- 1 1 p 1 p p2 ) f ( p 2 ) , f ( p3 ) , and f ( p4 ) p p 2 p3 From these results one can conclude that- n2 pk 1 1 1 f ( p n ) k1 ..... p n1 p n1 p n2 p Thus f(121)=1/11, f(625)=f(54)=31/125, and f(343)=f(73)=8/49 etc. It is also noted that one can manipulate the above results to obtain- 1 ( 1) p f ( p 2 ) 1 1 p(1 p) pf ( p3 ) p 2 , provided that p remains a prime number. So for p=7, we find {7(8/49)-(1/7)}=1. If we now introduce a new function- f (N 2 ) 1 [ (N 2 ) 1] g(N 2 ) F(N ) Nf (N 3 ) [ (N 3 ) 1] N 3 g(N 3 ) N 3 , it is clear that F(N) will always be equal to one if N=p. However, when N is not a prime then F(N) will typically be less than one such as F[6]=(f(36)+1)/(6f(216))= 90/283 and F(8)=21/85. -

Numbers 1 to 100
Numbers 1 to 100 PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Tue, 30 Nov 2010 02:36:24 UTC Contents Articles −1 (number) 1 0 (number) 3 1 (number) 12 2 (number) 17 3 (number) 23 4 (number) 32 5 (number) 42 6 (number) 50 7 (number) 58 8 (number) 73 9 (number) 77 10 (number) 82 11 (number) 88 12 (number) 94 13 (number) 102 14 (number) 107 15 (number) 111 16 (number) 114 17 (number) 118 18 (number) 124 19 (number) 127 20 (number) 132 21 (number) 136 22 (number) 140 23 (number) 144 24 (number) 148 25 (number) 152 26 (number) 155 27 (number) 158 28 (number) 162 29 (number) 165 30 (number) 168 31 (number) 172 32 (number) 175 33 (number) 179 34 (number) 182 35 (number) 185 36 (number) 188 37 (number) 191 38 (number) 193 39 (number) 196 40 (number) 199 41 (number) 204 42 (number) 207 43 (number) 214 44 (number) 217 45 (number) 220 46 (number) 222 47 (number) 225 48 (number) 229 49 (number) 232 50 (number) 235 51 (number) 238 52 (number) 241 53 (number) 243 54 (number) 246 55 (number) 248 56 (number) 251 57 (number) 255 58 (number) 258 59 (number) 260 60 (number) 263 61 (number) 267 62 (number) 270 63 (number) 272 64 (number) 274 66 (number) 277 67 (number) 280 68 (number) 282 69 (number) 284 70 (number) 286 71 (number) 289 72 (number) 292 73 (number) 296 74 (number) 298 75 (number) 301 77 (number) 302 78 (number) 305 79 (number) 307 80 (number) 309 81 (number) 311 82 (number) 313 83 (number) 315 84 (number) 318 85 (number) 320 86 (number) 323 87 (number) 326 88 (number) -

Partial Sum of the Sequence of Aliquot Sums
Parabola Volume 56, Issue 2 (2020) Partial sum of the sequence of aliquot sums Timothy Hume1 1 Introduction The aliquot sum s(n), for a positive integer n, is the sum of all divisors of n, excluding n itself. For example, the aliquot sum of 12 is 1+2+3+4+6 = 16. The sequence of aliquot sums, s(n) for n = 1; 2; 3;:::, has been studied by mathematicians since antiquity. The On-Line Encyclopedia of Integer Sequences (OEIS) [1] presents an elegant for- mula - without proof - for the sum of the first n terms of the sequence of aliquot sums2: n n X n(n − 1) X s(n) = − (n mod i) : (1) 2 i=1 i=1 In this article a proof of the above formula is presented. However, first a brief introduction to the aliquot sum is presented for readers who may be unfamiliar with this sequence. 2 The aliquot sum The first few terms in the sequence of aliquot sums are shown in Table1. n: 1 2 3 4 5 6 7 8 9 10 11 12 s(n): 0 1 1 3 1 6 1 7 4 8 1 16 Table 1: The first twelve terms in the sequence of aliquot sums. The sequence can also be visually represented as a scatter plot, as shown in Figure1. Representing sequences as scatter plots can be helpful, because the eye is adept at finding patterns which might otherwise be missed in long lists of numbers. A number of patterns are evident in the scatter plot. Not surprisingly, as n increases, s(n) tends to increase, because larger numbers often have more or larger factors. -

Programming Lab
Programming Lab MCA- 107 SELF LEARNING MATERIAL DIRECTORATE OF DISTANCE EDUCATION SWAMI VIVEKANAND SUBHARTI UNIVERSITY MEERUT – 250 005, UTTAR PRADESH (INDIA) SLM Module Developed By : Author: Reviewed by : Assessed by: Study Material Assessment Committee, as per the SVSU ordinance No. VI (2) Copyright © Gayatri Sales DISCLAIMER No part of this publication which is material protected by this copyright notice may be reproduced or transmitted or utilized or stored in any form or by any means now known or hereinafter invented, electronic, digital or mechanical, including photocopying, scanning, recording or by any information storage or retrieval system, without prior permission from the publisher. Information contained in this book has been published by Directorate of Distance Education and has been obtained by its authors from sources be lived to be reliable and are correct to the best of their knowledge. However, the publisher and its author shall in no event be liable for any errors, omissions or damages arising out of use of this information and specially disclaim and implied warranties or merchantability or fitness for any particular use. Published by: Gayatri Sales Typeset at: Micron Computers Printed at: Gayatri Sales, Meerut. 2 PROGRAMMING LAB • Write C program to find largest of three integers. • Write C program to check whether the given string is palindrome or not. • Write C program to find whether the given integer is (i) a prime number (ii) an Armstrong number. • Write C program for Pascal triangle. • Write C program to find sum and average of n integer using linear array. • Write C program to perform addition, multiplication, transpose on matrices. -

A Note on Perfect Numbers
IJRDO - Journal of Mathematics ISSN: 2455-9210 Note on Same Amazing properties of Perfect Numbers Kayla Jones, Mulatu Lemma Department of Mathematics Savannah State University Savannah, Georgia 31404 USA Abstract. Number theory has been a fascinating topic for many mathematicians because of the relationships they can find between numbers and their divisors. One of which are, perfect numbers. They date back to ancient Greek mathematics when they studied the relationships between numbers and their divisors. As of 2018, there are currently 50 perfect numbers that have been found. The first four are 6, 28, 496, and 8128.The largest containing more than 23 million digits. Perfect numbers are still being found to this day and no one has found an odd perfect number yet. Euclid proved a formula for finding perfect numbers: If is prime, then is perfect. In other words, n is a number whose positive divisors sums to n. Key Words: Prime Numbers and Perfect numbers. 1. Introduction and Background Throughout history, there have been studies on perfect numbers. It is not known when perfect numbers were first studied and indeed the first studies may go back to the earliest times when numbers first aroused curiosity [6]. It is rather likely, although not completely certain, that the Egyptians would have come across such numbers naturally given the way their methods of calculation worked, where detailed justification for this idea is given [6]. Perfect numbers were studied by Pythagoras and his followers, more for their mystical properties than for their number theoretic properties [6]. Although, the four perfect numbers 6, 28, 496 and 8128 seem to have been known from ancient times and there is no record of these discoveries [6]. -

Svitlana Mazur Nina Solovey Tetiana Andriichuk ENGLISH FOR
Svitlana Mazur Nina Solovey Tetiana Andriichuk ENGLISH FOR STUDENTS OF MATHEMATICS Видавничий Дім Дмитра Бураго 2020 УДК 811 ББК 81.2 Англ-9 П 61 Рекомендовано до друку Вченою радою Інституту філології КНУ імені Тараса Шевченка від 29 жовтня 2019 р. Рецензенти: канд.філол.наук, доцент кафедри японської філології Київського національного лінгвістичного університету В.Л. Пирогов. канд. фіз.-матем. наук, доцент кафедри алгебри та математичної логіки КНУ імені Тараса Шевченка Є.А. Кочубінська. Мазур С. М., Соловей Н. В., Андрійчук Т. В. English for students of mathematics. – К.: Видавничий дім Дмитра Бураго, 2020. – 208 с. ISBN 978-966-489-487-3 This textbook is English course for students of mathematics. It consists of 12 units based on topics of great interest to everyone studying mathematics. We hope this course will develop the communication skills one needs to succeed in a professional environment and will broaden the knowledge of the history of mathematics and will help to find out connections between mathematics and human progress. Students are offered a variety of discussion questions as an introduction to each unit. Students will extend their vocabulary by learning useful new words and phrases. Glossary at the end of the course will also help to increase math vocabulary. Students will read texts from the book 50 mathematical ideas you really need to know by Tony Crilly. Students will develop their reading skills. They will also be able to discuss the issues raised in the extracts from the books mentioned above. As a result they will become more accurate in their use of English at level B2. -
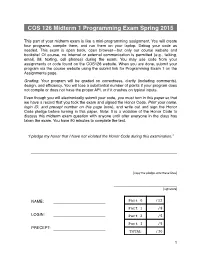
COS 126 Midterm 1 Programming Exam Spring 2015
COS 126 Midterm 1 Programming Exam Spring 2015 This part of your midterm exam is like a mini-programming assignment. You will create four programs, compile them, and run them on your laptop. Debug your code as needed. This exam is open book, open browser—but only our course website and booksite! Of course, no internal or external communication is permitted (e.g., talking, email, IM, texting, cell phones) during the exam. You may use code from your assignments or code found on the COS126 website. When you are done, submit your program via the course website using the submit link for Programming Exam 1 on the Assignments page. Grading. Your program will be graded on correctness, clarity (including comments), design, and efficiency. You will lose a substantial number of points if your program does not compile or does not have the proper API, or if it crashes on typical inputs. Even though you will electronically submit your code, you must turn in this paper so that we have a record that you took the exam and signed the Honor Code. Print your name, login ID, and precept number on this page (now), and write out and sign the Honor Code pledge before turning in this paper. Note: It is a violation of the Honor Code to discuss this midterm exam question with anyone until after everyone in the class has taken the exam. You have 90 minutes to complete the test. “I pledge my honor that I have not violated the Honor Code during this examination.” ___________________________________________________________________ ___________________________________________________________________ [copy the pledge onto these lines] _____________________________ [signature] NAME: ______________________ Part 0 /12 Part 1 /8 LOGIN: ______________________ Part 2 /5 Part 3 /5 PRECEPT: ______________________ TOTAL /30 !1 The aliquot sum of a positive integer is the sum of its positive divisors other than itself (these divisors are called its proper divisors). -
Functional Thinking
Functional Thinking Neal Ford Functional Thinking by Neal Ford Copyright © 2014 Neal Ford. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/ institutional sales department: 800-998-9938 or [email protected]. Editors: Mike Loukides and Meghan Blanchette Indexer: Judith McConville Production Editor: Kristen Brown Cover Designer: Karen Montgomery Copyeditor: Eileen Cohen Interior Designer: David Futato Proofreader: Jasmine Kwityn Illustrator: Rebecca Demarest July 2014: First Edition Revision History for the First Edition: 2014-06-26: First release See http://oreilly.com/catalog/errata.csp?isbn=9781449365516 for release details. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Functional Thinking, the image of a thick-tailed greater galago, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. ISBN: 978-1-449-36551-6 [LSI] Table of Contents Preface.