SUSE Linux: a Complete Guide to Novell's Community Distributionwill
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Withlinux Linux
LINUX JOURNAL MISTERHOUSE | F-SPOT | AJAX | KAFFEINE | ROBOTS | VIDEO CODING An Excerpt from Apress’ Beginning DIGITAL LIFESTYLE DIGITAL Ubuntu Linux: From Novice to Professional ™ Since 1994: The Original Magazine of the Linux Community OCTOBER 2006 | ISSUE 150 | www.linuxjournal.com MisterHouse | AL F-Spot DIGIT | Ajax | Kaffeine LIFESTYLE | ux Robots with LinuxLin | Video Coding Video >> F-Spot Tips >> Working with Digital Images >> H.264 Video Encoding for Low-Bitrate Video | Ubuntu >> Linux-Based Do-It-Yourself Robots >> Share Music with Kaffiene, Amarok, Last.fm and more >> Digital Convenience at Home with Open-Source Technology O >> Maddog’s Travel Gadgets C T O B E >> Using MisterHouse for Home Automation R 2006 AN I S S PUBLICATION U E USA $5.00 150 + Doc Searls Breaks the Marketing Matrix CAN $6.50 U|xaHBEIGy03102ozXv,:! Today, Carlo restored a failed router in Miami, rebooted a Linux server in Tokyo, and remembered someone’s very special day. With Avocent centralized management solutions, the world can finally revolve around you. Avocent puts secure access and control right at your fingertips – from multi-platform servers to network routers, your local data center to branch offices. Our “agentless” out-of-band solution manages your physical and virtual connections (KVM, serial, integrated power, embedded service processors, IPMI and SoL) from a single console. You have guaranteed access to your critical hardware even when in-band methods fail. Let others roll crash carts to troubleshoot – with Avocent, trouble becomes a thing of the past, so you can focus on the present. Visit www.avocent.com/special to download Data Center Control: Guidelines to Achieve Centralized Management white paper. -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

THE 2003 Editionlinux
SUBSCRIBE or renew your subscription to APC for your chance to WIN the new Alfa 156 JTS, valued at over $54,000 Only $65 for 12 issues THE 2003 edition linux POCKETBOOK Subscribe ... www.apcmag.com Online at magshop.com.au or Call 13 61 16 Authorised under NSW Permit No. L02/09075 VIC: 02/2531 SA: T02/3553 ACT: TP02/3650 NT: NT02/3286 For terms and conditions refer to www.xmas.magshop.au. Expiry date: 24/12/02 Contents CHAPTER 1 Customising Gnome 57 CHAPTER 6 Editorial INTRODUCTION 11 Exploring KDE 60 WORKING WITH WINDOWS 131 The origins of the Customising KDE 64 What about Windows? 132 Welcome back to The Linux Pocketbook 2003 edition! penguin 12 Windows connectivity 138 Many of you will probably remember the original print ver- CHAPTER 4 sions of The Linux Pocketbook on newsstands across the country. Why Linux? 18 Basic security 145 The original versions sold so well that we ran out of copies. We’ve The ways of the world 20 USING LINUX 67 had countless requests for reprints, so we’ve decided to bundle the Connecting to the Net 68 CHAPTER 7 entire book into this single resource. This version of the pocketbook relies heavily on Mandrake Linux 9.0 or Red Hat 8.0. Both were CHAPTER 2 Applications 71 PLAYING WITH LINUX 151 released late in 2002, and can be easily found for sale at www.everyth INSTALLING LINUX 21 Conjuring Linux 75 Linux multimedia 152 inglinux.com.au, or for download from either mandrakelinux.com or First published December 2000. -

Dell™ Gigaos 6.5 Release Notes July 2015
Dell™ GigaOS 6.5 Release Notes July 2015 These release notes provide information about the Dell™ GigaOS release. • About Dell GigaOS 6.5 • System requirements • Product licensing • Third-party contributions • About Dell About Dell GigaOS 6.5 For complete product documentation, visit http://software.dell.com/support/. System requirements Not applicable. Product licensing Not applicable. Third-party contributions Source code is available for this component on http://opensource.dell.com/releases/Dell_Software. Dell will ship the source code to this component for a modest fee in response to a request emailed to [email protected]. This product contains the following third-party components. For third-party license information, go to http://software.dell.com/legal/license-agreements.aspx. Source code for components marked with an asterisk (*) is available at http://opensource.dell.com. Dell GigaOS 6.5 1 Release Notes Table 1. List of third-party contributions Component License or acknowledgment abyssinica-fonts 1.0 SIL Open Font License 1.1 ©2003-2013 SIL International, all rights reserved acl 2.2.49 GPL (GNU General Public License) 2.0 acpid 1.0.10 GPL (GNU General Public License) 2.0 alsa-lib 1.0.22 GNU Lesser General Public License 2.1 alsa-plugins 1.0.21 GNU Lesser General Public License 2.1 alsa-utils 1.0.22 GNU Lesser General Public License 2.1 at 3.1.10 GPL (GNU General Public License) 2.0 atk 1.30.0 LGPL (GNU Lesser General Public License) 2.1 attr 2.4.44 GPL (GNU General Public License) 2.0 audit 2.2 GPL (GNU General Public License) 2.0 authconfig 6.1.12 GPL (GNU General Public License) 2.0 avahi 0.6.25 GNU Lesser General Public License 2.1 b43-fwcutter 012 GNU General Public License 2.0 basesystem 10.0 GPL (GNU General Public License) 3 bash 4.1.2-15 GPL (GNU General Public License) 3 bc 1.06.95 GPL (GNU General Public License) 2.0 bind 9.8.2 ISC 1995-2011. -

MPLAYER-10 Mplayer-1.0Pre7-Copyright
MPLAYER-10 MPlayer-1.0pre7-Copyright MPlayer was originally written by Árpád Gereöffy and has been extended and worked on by many more since then, see the AUTHORS file for an (incomplete) list. You are free to use it under the terms of the GNU General Public License, as described in the LICENSE file. MPlayer as a whole is copyrighted by the MPlayer team. Individual copyright notices can be found in the file headers. Furthermore, MPlayer includes code from several external sources: Name: FFmpeg Version: CVS snapshot Homepage: http://www.ffmpeg.org Directory: libavcodec, libavformat License: GNU Lesser General Public License, some parts GNU General Public License, GNU General Public License when combined Name: FAAD2 Version: 2.1 beta (20040712 CVS snapshot) + portability patches Homepage: http://www.audiocoding.com Directory: libfaad2 License: GNU General Public License Name: GSM 06.10 library Version: patchlevel 10 Homepage: http://kbs.cs.tu-berlin.de/~jutta/toast.html Directory: libmpcodecs/native/ License: permissive, see libmpcodecs/native/xa_gsm.c Name: liba52 Version: 0.7.1b + patches Homepage: http://liba52.sourceforge.net/ Directory: liba52 License: GNU General Public License Name: libdvdcss Version: 1.2.8 + patches Homepage: http://developers.videolan.org/libdvdcss/ Directory: libmpdvdkit2 License: GNU General Public License Name: libdvdread Version: 0.9.3 + patches Homepage: http://www.dtek.chalmers.se/groups/dvd/development.shtml Directory: libmpdvdkit2 License: GNU General Public License Name: libmpeg2 Version: 0.4.0b + patches -

Linuxvilag-66.Pdf 8791KB 11 2012-05-28 10:27:18
Magazin Hírek Java telefon másképp Huszonegyedik századi autótolvajok Samsung okostelefon Linuxszal Magyarországon még nem jellemzõ, Kínában már kapható de tõlünk nyugatabbra már nem tol- a Samsung SCH-i819 mo- vajkulccsal vagy feszítõvassal, hanem biltelefonja, amely Prizm laptoppal járnak az autótolvajok. 2.5-ös Linuxot futtat. Ot- Mindezt azt teszi lehetõvé, hogy tani nyaralás esetén nyu- a gyújtás, a riasztó és az ajtózárak is godtan vásárolhatunk távirányíthatóak, így egy megfelelõen belõle, hiszen a CDMA felszerelt laptoppal is irányíthatóak 800 MHz-e mellett az ezek a rendszerek. európai 900/1800 MHz-et http://www.leftlanenews.com/2006/ is támogatja. A kommunikációt egy 05/03/gone-in-20-minutes-using- Qualcomm MSM6300-as áramkör bo- laptops-to-steal-cars/ nyolítja, míg az alkalmazások egy 416 MHz-es Intel PXA270-es processzoron A Lucent Technologies és a SUN Elephants Dream futnak. A készülék Class 10-es GPRS elkészítette a Jasper S20-at, ami adatátvitelre képes, illetve tartalmaz alapvetõen más koncepcióval GPS (globális helymeghatározó) vevõt © Kiskapu Kft. Minden jog fenntartva használja a Java-t, mint a mostani is. Az eszköz 64 megabájt SDRAM-ot és telefonok. Joggal kérdezheti a kedves 128 megabájt nem felejtõ flash memóri- Olvasó, hogy megéri-e, van-e hely át kapott, de micro-SD memóriakártyá- a jelenlegi Symbian, Windows Mobile val ezt tovább bõvíthetjük. A kijelzõje és Linux trió mellett. A jelenlegi 2.4 hüvelykes, felbontása pedig „csak” telefonoknál kétféleképpen futhat 240x320 képpont 65 ezer színnel. egy program: natív vagy Java mód- Május 19-én elérhetõvé tette az Orange Természetesen a trendeknek megfele- ban. A Java mód ott szükségessé Open Movie Project elsõ rövidfilmjét lõen nem maradt ki a 2 megapixeles tesz pár olyan szintet, amely Creative Commons jogállással. -

Fedora Core Works--Without the Fluff That Bogs Down Other Books and Help/How-To Web Sites
Fedora Linux By Chris Tyler ............................................... Publisher: O'Reilly Pub Date: October 01, 2006 ISBN-10: 0-596-52682-2 ISBN-13: 978-0-596-52682-5 Pages: 504 Table of Contents | Index "Neither a "Starting Linux" book nor a dry reference manual, this book has a lot to offer to those coming to Fedora from other operating systems or distros." -- Behdad Esfahbod, Fedora developer This book will get you up to speed quickly on Fedora Linux, a securely-designed Linux distribution that includes a massive selection of free software packages. Fedora is hardened out-of-the-box, it's easy to install, and extensively customizable - and this book shows you how to make Fedora work for you. Fedora Linux: A Complete Guide to Red Hat's Community Distribution will take you deep into essential Fedora tasks and activities by presenting them in easy-to-learn modules. From installation and configuration through advanced topics such as administration, security, and virtualization, this book captures the important details of how Fedora Core works--without the fluff that bogs down other books and help/how-to web sites. Instead, you can learn from a concise task-based approach to using Fedora as both a desktop and server operating system. In this book, you'll learn how to: Install Fedora and perform basic administrative tasks Configure the KDE and GNOME desktops Get power management working on your notebook computer and hop on a wired or wireless network Find, install, and update any of the thousands of packages available for Fedora Perform backups, increase reliability with RAID, and manage your disks with logical volumes Set up a server with file sharing, DNS, DHCP, email, a Web server, and more Work with Fedora's security features including SELinux, PAM, and Access Control Lists (ACLs) Whether you are running the stable version of Fedora Core or bleeding-edge Rawhide releases, this book has something for every level of user. -

Linux: Come E Perchх
ÄÒÙÜ Ô ©2007 mcz 12 luglio 2008 ½º I 1. Indice II ½º Á ¾º ¿º ÈÖÞÓÒ ½ º È ÄÒÙÜ ¿ º ÔÔÖÓÓÒÑÒØÓ º ÖÒÞ ×Ó×ØÒÞÐ ÏÒÓÛ× ¾½ º ÄÒÙÜ ÕÙÐ ×ØÖÙÞÓÒ ¾ º ÄÒÙÜ ÀÖÛÖ ×ÙÔÔ ÓÖØØÓ ¾ º È Ð ÖÒÞ ØÖ ÖÓ ÓØ Ù×Ö ¿½ ½¼º ÄÒÙÜ × Ò×ØÐÐ ¿¿ ½½º ÓÑ × Ò×ØÐÐÒÓ ÔÖÓÖÑÑ ¿ ½¾º ÒÓÒ ØÖÓÚÓ ÒÐ ×ØÓ ÐÐ ×ØÖÙÞÓÒ ¿ ½¿º Ó׳ ÙÒÓ ¿ ½º ÓÑ × Ð ××ØÑ ½º ÓÑ Ð ½º Ð× Ñ ½º Ð Ñ ØÐ ¿ ½º ÐÓ ½º ÓÑ × Ò×ØÐÐ Ð ×ØÑÔÒØ ¾¼º ÓÑ ÐØØÖ¸ Ø×Ø ÐÖ III Indice ¾½º ÓÑ ÚÖ Ð ØÐÚ×ÓÒ ¿ 21.1. Televisioneanalogica . 63 21.2. Televisione digitale (terrestre o satellitare) . ....... 64 ¾¾º ÐÑØ ¾¿º Ä 23.1. Fotoritocco ............................. 67 23.2. Grafica3D.............................. 67 23.3. Disegnovettoriale-CAD . 69 23.4.Filtricoloreecalibrazionecolori . .. 69 ¾º ×ÖÚ Ð ½ 24.1.Vari.................................. 72 24.2. Navigazionedirectoriesefiles . 73 24.3. CopiaCD .............................. 74 24.4. Editaretesto............................. 74 24.5.RPM ................................. 75 ¾º ×ÑÔ Ô ´ËÐе 25.1.Montareundiscoounapenna . 77 25.2. Trovareunfilenelsistema . 79 25.3.Vedereilcontenutodiunfile . 79 25.4.Alias ................................. 80 ¾º × ÚÓÐ×× ÔÖÓÖÑÑÖ ½ ¾º ÖÓÛ×Ö¸ ÑÐ ººº ¿ ¾º ÖÛÐРгÒØÚÖÙ× Ð ÑØØÑÓ ¾º ÄÒÙÜ ½ ¿¼º ÓÑ ØÖÓÚÖ ÙØÓ ÖÖÑÒØ ¿ ¿½º Ð Ø×ØÙÐ Ô Ö Ð ×ØÓÔ ÄÒÙÜ ¿¾º ´ÃµÍÙÒØÙ¸ ÙÒ ×ØÖÙÞÓÒ ÑÓÐØÓ ÑØ ¿¿º ËÙÜ ÙÒ³ÓØØÑ ×ØÖÙÞÓÒ ÄÒÙÜ ½¼½ ¿º Á Ó Ò ÄÒÙÜ ½¼ ¿º ÃÓÒÕÙÖÓÖ¸ ÕÙ×ØÓ ½¼ ¿º ÃÓÒÕÙÖÓÖ¸ Ñ ØÒØÓ Ô Ö ½½¿ 36.1.Unaprimaocchiata . .114 36.2.ImenudiKonqueror . .115 36.3.Configurazione . .116 IV Indice 36.4.Alcuniesempidiviste . 116 36.5.Iservizidimenu(ServiceMenu) . 119 ¿º ÃÓÒÕÙÖÓÖ Ø ½¾¿ ¿º à ÙÒ ÖÖÒØ ½¾ ¿º à ÙÒ ÐÙ×ÓÒ ½¿½ ¼º ÓÒÖÓÒØÓ Ò×ØÐÐÞÓÒ ÏÒÓÛ×È ÃÍÙÒØÙ º½¼ ½¿¿ 40.1. -
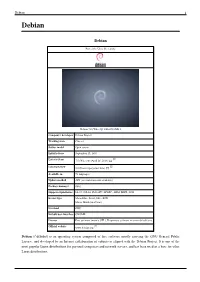
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

Tuning SUSE LINUX Enterprise Server on IBM Eserver Xseries Servers
Front cover Tuning SUSE LINUX Enterprise Server on IBMM Eserver xSeries Servers Describes ways to tune the operating system Introduces performance tuning tools Covers key server applications David Watts Martha Centeno Raymond Phillips Luciano Magalhães Tomé ibm.com/redbooks Redpaper International Technical Support Organization Tuning SUSE LINUX Enterprise Server on IBM Eserver xSeries Servers July 2004 Note: Before using this information and the product it supports, read the information in “Notices” on page vii. First Edition (July 2004) This edition applies to SUSE LINUX Enterprise Server 8 and 9 running on IBM Eserver xSeries servers. © Copyright International Business Machines Corporation 2004. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . vii Trademarks . viii Preface . ix The team that wrote this Redpaper . ix Become a published author . .x Comments welcome. xi Chapter 1. Tuning the operating system. 1 1.1 Disabling daemons . 2 1.2 Shutting down the GUI . 4 1.3 Compiling the kernel . 6 1.4 Changing kernel parameters. 7 1.5 V2.4 kernel parameters. 9 1.6 V2.6 kernel parameters. 12 1.7 Tuning the processor subsystem . 14 1.8 Tuning the memory subsystem . 15 1.9 Tuning the file system . 16 1.9.1 Hardware considerations before installing Linux. 16 1.9.2 ReiserFS, the default SUSE LINUX file system . 19 1.9.3 Other journaling file systems. 20 1.9.4 File system tuning in the Linux kernel. 20 1.9.5 The swap partition. 26 1.10 Tuning the network subsystem . -
Win32codecs Mandriva
Win32codecs mandriva click here to download Hi i am am having trouble playing wmv files through KMPlayer. i downloaded the codec pack from Mplayer site and unpacked it to /usr/lib/win32 why to www.doorway.ru "www.doorway.ru" file in every new. Win32 codec binaries /mirror/www.doorway.ru Mandriva , www.doorway.ru Mandriva When I installed Mandriva free the install CD's referred to something calle Among other things I need to install win32codecs, libdvdcss, and. (I am using Mandriva Linux ) Moved to Mandriva section. If you want to learn I installed VLC, wincodecs, libdvdcss sucessfully. Now Mandriva Free Linux, though is extremely user friendly it wincodecs package containes a number of diffeent dll files which. Posts about mandriva sources written by tanclo. faad2 libfaad2_2 xine-faad libquicktime-faad mencoder ffmpeg helixplayer k9copy ogmrip wincodecs. For instance, typing wincodecs (which contains most codecs) will turn out no results within Mandriva's Software Management. Some packages like the Win32 codecs are not available in the standard Mandriva repositories. The easiest way to make such packages available to your system. Problem installing mplayer codecs Mandriva Linux. preplf, wincodecsplf. In Mandriva , it only includes , and I would like to upgrade to . Use MCC to install the mplayer, win32 codecs and mplayer plugins for mozilla. KMPlayer Sound and Video Problems Mandriva Linux. Did you install all the wincodecs from plf? Yes. I just did and that fixed the WMV. In reply to: Another round of changes at Mandriva by danielpf there are plf sites from where you can easily download the win32 codecs, etc. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae