Application Identification and Control
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DFA Canada Global 50EQ-50FI Portfolio - Class F (USD) As of July 31, 2021 (Updated Monthly) Source: RBC Holdings Are Subject to Change
DFA Canada Global 50EQ-50FI Portfolio - Class F (USD) As of July 31, 2021 (Updated Monthly) Source: RBC Holdings are subject to change. The information below represents the portfolio's holdings (excluding cash and cash equivalents) as of the date indicated, and may not be representative of the current or future investments of the portfolio. The information below should not be relied upon by the reader as research or investment advice regarding any security. This listing of portfolio holdings is for informational purposes only and should not be deemed a recommendation to buy the securities. The holdings information below does not constitute an offer to sell or a solicitation of an offer to buy any security. The holdings information has not been audited. By viewing this listing of portfolio holdings, you are agreeing to not redistribute the information and to not misuse this information to the detriment of portfolio shareholders. Misuse of this information includes, but is not limited to, (i) purchasing or selling any securities listed in the portfolio holdings solely in reliance upon this information; (ii) trading against any of the portfolios or (iii) knowingly engaging in any trading practices that are damaging to Dimensional or one of the portfolios. Investors should consider the portfolio's investment objectives, risks, and charges and expenses, which are contained in the Prospectus. Investors should read it carefully before investing. This fund operates as a fund-of-funds and generally allocates its assets among other mutual funds, but has the ability to invest in securities and derivatives directly. The holdings listed below contain both the investment holdings of the corresponding underlying funds as well as any direct investments of the fund. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Download Audio Content for Re-Listening
European Proceedings of Social and Behavioural Sciences EpSBS www.europeanproceedings.com e-ISSN: 2357-1330 DOI: 10.15405/epsbs.2020.11.03.23 DCCD 2020 Dialogue of Cultures - Culture of Dialogue: from Conflicting to Understanding INFORMATION TECHNOLOGY IN TEACHING CHINESE: ANALYSIS AND CLASSIFICATION OF DIGITAL EDUCATIONAL RESOURCES Tatiana L. Guruleva (a)* *Corresponding author (a) Moscow City University, 5B Malyj Kazennyj pereulok, Moscow, Russia; Institute of Far Eastern Studies of Russian Academy of Sciences, 32 Nakhimovskii prospect, 117997, Moscow, Russia, [email protected] Abstract The intercultural approach to teaching Chinese as a foreign language in Russia was first implemented by us in a model for co-learning languages and cultures. This model was developed in 2009-2011, it took into account the specifics of teaching the Chinese language, which is studied simultaneously with the English language. The model was tested in the international multicultural educational region of Siberia and the Far East of Russia and northeastern part of China. However, the intercultural approach has wide potential for implementation not only in conditions of direct contact with representatives of another culture. In the modern world, information technologies for teaching foreign languages are increasingly in demand. For a number of objective reasons, large technology companies until the beginning of the 21st century could not begin to develop information technologies that support the Chinese language. Therefore, the history of the creation and use of information technologies for teaching the Chinese language is happening right now before our eyes. In this regard, the analysis and classification of information resources for teaching the Chinese language is relevant and in demand. -

Master Thesis
Master's Programme in Computer Network Engineering, 60 credits MASTER Connect street light control devices in a secure network THESIS Andreas Kostoulas, Efstathios Lykouropoulos, Zainab Jumaa Network security, 15 credits Halmstad 2015-02-16 “Connect street light control devices in a secure network” Master’s Thesis in Computer Network engineering 2014 Authors: Andreas Kostoulas, Efstathios Lykouropoulos, Zainab Jumaa Supervisor: Alexey Vinel Examiner: Tony Larsson Preface This thesis is submitted in partial fulfilment of the requirements for a Master’s Degree in Computer Network Engineering at the Department of Information Science - Computer and Electrical Engineering, at University of Halmstad, Sweden. The research - implementation described herein was conducted under the supervision of Professor Alexey Vinel and in cooperation with Greinon engineering. This was a challenging trip with both ups and downs but accompanied by an extend team of experts, always willing to coach, sponsor, help and motivate us. For this we would like to thank them. We would like to thank our parents and family for their financial and motivational support, although distance between us was more than 1500 kilometres. Last but not least we would like to thank our fellow researchers and friends on our department for useful discussions, comments, suggestions, thoughts and also creative and fun moments we spend together. i Abstract Wireless communications is a constantly progressing technology in network engineering society, creating an environment full of opportunities that are targeting in financial growth, quality of life and humans prosperity. Wireless security is the science that has as a goal to provide safe data communication between authorized users and prevent unauthorized users from gaining access, deny access, damage or counterfeit data in a wireless environment. -

Fraud and the Darknets
OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division Fraud And The Darknets Thomas Harper Assistant Special Agent in Charge Technology Crimes Division OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division What is an OIG? • Established by Congress • Independent agency that reports to Congress • Agency head appointed by the President and confirmed by Congress • Mission: protect the taxpayer’s interests by ensuring the integrity and efficiency of the associated agency OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division Technology Crimes Division • Investigate criminal cyber threats against the Department’s IT infrastructure, or • Criminal activity in cyber space that threatens the Department’s administration of Federal education assistance funds • Investigative jurisdiction encompasses any IT system used in the administration of Federal money originating from the Department of Education. OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division Work Examples • Grade hacking • Computer Intrusions • Criminal Forums online selling malware • ID/Credential theft to hijack Student Aid applications • Misuse of Department systems to obtain personal information • Falsifying student aid applications by U.S. government employees • Child Exploitation material trafficking OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division Fraud and the Darknets Special Thanks to Financial Crimes Enforcement Network (FINCEN) OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division Fraud and the Darknets OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division OFFICE OF THE INSPECTOR GENERAL U.S. Department of Education Technology Crimes Division OFFICE OF THE INSPECTOR GENERAL U.S. -

August 10, 2011 Broadcasting Board of Governors International
August 10, 2011 Broadcasting Board of Governors International Broadcasting Bureau Office of Engineering Cohen Building, Room 4300 330 Independence Avenue, SW Washington, DC 20237 Attn: Malita Dyson Dear Ms. Dyson, Below is our thirty-ninth invoice for contract number BBGCON1808C6700, Accounting Appropri ation Data 9568-08-0206-E009701048A. There are no travel costs. Services rendered include blocking resistance architecture and testing, scalability and promotion and advocacy for the Tor network, and other detailed tasks under 0001 of our contract as confirmed in our status reports to BBG. Please do not hesitate to email me at [email protected] or call me at (b) (6) if there are any questions. Invoice 39: Period Months Rate Cost 06/17/2011 - 07/17/2011 1 $15,000 $15,000 Thank you. Sincerely, Andrew Lewman Executive Director TorProject Invoice BBG08102011 The Tor Project, Inc. 969 Main Street, Suite 206, Walpole, MA 02081-2972 USA https://www.torproject.org/ From: Andrew Lewman. Executive Director To: Kelly DeYoe, program officer, BBG RE: contract BBGCON1807S6441 Date: August 10, 2011 This report documents progress in July 2011 on contract BBGCON1807S6441 between BBG and The Tor Project. New releases, new hires, new funding New Releases 1. On July 7, we released Torbutton 1.4.0. The addon has been disabled on addons.mozilla.org. Our URL is now canonical. This release features support for Firefox 5.0, and has been tested against the vanilla release for basic functionality. However, it has not been audited for Network Isolation, State Separation, Tor Undiscoverability or Interoperability issues[l] due to toggling under Firefox 5. -

Piratez Are Just Disgruntled Consumers Reach Global Theaters That They Overlap the Domestic USA Blu-Ray Release
Moviegoers - or perhaps more accurately, lovers of cinema - are frustrated. Their frustrations begin with the discrepancies in film release strategies and timing. For example, audiences that saw Quentin Tarantino’s1 2 Django Unchained in the United States enjoyed its opening on Christmas day 2012; however, in Europe and other markets, viewers could not pay to see the movie until after the 17th of January 2013. Three weeks may not seem like a lot, but some movies can take months to reach an international audience. Some take so long to Piratez Are Just Disgruntled Consumers reach global theaters that they overlap the domestic USA Blu-Ray release. This delay can seem like an eternity for ultiscreen is at the top of the entertainment a desperate fan. This frustrated enthusiasm, combined industry’s agenda for delivering digital video. This with a lack of timely availability, leads to the feeling of M is discussed in the context of four main screens: being treated as a second class citizen - and may lead TVs, PCs, tablets and mobile phones. The premise being the over-anxious fan to engage in piracy. that multiscreen enables portability, usability and flexibility for consumers. But, there is a fifth screen which There has been some evolution in this practice, with is often overlooked – the cornerstone of the certain films being released simultaneously to a domestic and global audience. For example, Avatar3 was released entertainment industry - cinema. This digital video th th ecosystem is not complete without including cinema, and in theaters on the 10 and 17 of December in most it certainly should be part of the multiscreen discussion. -

Tor and Circumvention: Lessons Learned
Tor and circumvention: Lessons learned Nick Mathewson The Tor Project https://torproject.org/ 1 What is Tor? Online anonymity 1) open source software, 2) network, 3) protocol Community of researchers, developers, users, and relay operators Funding from US DoD, Electronic Frontier Foundation, Voice of America, Google, NLnet, Human Rights Watch, NSF, US State Dept, SIDA, ... 2 The Tor Project, Inc. 501(c)(3) non-profit organization dedicated to the research and development of tools for online anonymity and privacy Not secretly evil. 3 Estimated ~250,000? daily Tor users 4 Anonymity in what sense? “Attacker can’t learn who is talking to whom.” Bob Alice Alice Anonymity network Bob Alice Bob 5 Threat model: what can the attacker do? Alice Anonymity network Bob watch Alice! watch (or be!) Bob! Control part of the network! 6 Anonymity isn't cryptography: Cryptography just protects contents. “Hi, Bob!” “Hi, Bob!” Alice <gibberish> attacker Bob 7 Anonymity isn't just wishful thinking... “You can't prove it was me!” “Promise you won't look!” “Promise you won't remember!” “Promise you won't tell!” “I didn't write my name on it!” “Isn't the Internet already anonymous?” 8 Anonymity serves different interests for different user groups. Anonymity “It's privacy!” Private citizens 9 Anonymity serves different interests for different user groups. Anonymity Businesses “It's network security!” “It's privacy!” Private citizens 10 Anonymity serves different interests for different user groups. “It's traffic-analysis resistance!” Governments Anonymity Businesses “It's network security!” “It's privacy!” Private citizens 11 Anonymity serves different interests for different user groups. -

AWS Site-To-Site VPN User Guide AWS Site-To-Site VPN User Guide
AWS Site-to-Site VPN User Guide AWS Site-to-Site VPN User Guide AWS Site-to-Site VPN: User Guide Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. AWS Site-to-Site VPN User Guide Table of Contents What is Site-to-Site VPN ..................................................................................................................... 1 Concepts ................................................................................................................................... 1 Working with Site-to-Site VPN ..................................................................................................... 1 Site-to-Site VPN limitations ......................................................................................................... 2 Pricing ...................................................................................................................................... 2 How AWS Site-to-Site VPN works ........................................................................................................ 3 Site-to-Site VPN Components ..................................................................................................... -

Building Ipv6 Based Tunneling Mechanisms for Voip Security
WK,QWHUQDWLRQDO0XOWL&RQIHUHQFHRQ6\VWHPV6LJQDOV 'HYLFHV Building IPv6 Based Tunneling Mechanisms for VoIP Security Amzari J. Ghazali, Waleed Al-Nuaimy, Ali Al-Ataby, Majid A. Al-Taee Department of Electrical Engineering and Electronics University of Liverpool, UK e-mail: {amzari.ghazali, wax, ali.ataby, altaeem}@liv.ac.uk Abstract—Internet protocol version 6 (IPv6) was such as Toredo, 6to4 and manual configuration [4]. developed to resolve the IPv4 address exhaustion Despite the benefits of using IPv6, there are still problem and support new features. However, IPv6 still challenges and obstacles in implementing and comprises some defectiveness of IPv4 protocol such as practically using IPv6 VoIP [5]. The issues of the multimedia security. This paper presents IPv6-based transition from the current IPv4 network to IPv6 as tunneling mechanisms for securing Voice over Internet Protocol (VoIP) network traffic using OpenSwan IPSec well as VoIP performance for both IP versions need (site-to-site). IPSec with Triple Data Encryption to be assessed and compared. Algorithm (3DES) is used to create a Virtual Private Evaluation of VoIP performance with IPSec in Network (VPN) on top of existing physical networks. IPv4, IPv6 and 6to4 networks using Teredo for NAT Secure communication mechanisms can therefore be provided for data and control information transmitted traversal in a test LAN was previously reported in between networks. Secure VoIP-oriented mechanisms [6]. The testbed used softphones to setup calls, and on VPN IPv6 have been designed, implemented and background traffic was generated to create congestion tested successfully using open source approaches. The on the links and routers. The results demonstrated the performance of the IPv6 VoIP network is assessed feasibility of using a single Linux box to handle experimentally in terms of several performance metrics IPSec, 6to4 and NAT processing, and it was found including jitter, throughput and packet loss rate. -
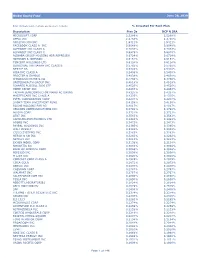
Global Equity Fund Description Plan 3S DCP & JRA MICROSOFT CORP
Global Equity Fund June 30, 2020 Note: Numbers may not always add up due to rounding. % Invested For Each Plan Description Plan 3s DCP & JRA MICROSOFT CORP 2.5289% 2.5289% APPLE INC 2.4756% 2.4756% AMAZON COM INC 1.9411% 1.9411% FACEBOOK CLASS A INC 0.9048% 0.9048% ALPHABET INC CLASS A 0.7033% 0.7033% ALPHABET INC CLASS C 0.6978% 0.6978% ALIBABA GROUP HOLDING ADR REPRESEN 0.6724% 0.6724% JOHNSON & JOHNSON 0.6151% 0.6151% TENCENT HOLDINGS LTD 0.6124% 0.6124% BERKSHIRE HATHAWAY INC CLASS B 0.5765% 0.5765% NESTLE SA 0.5428% 0.5428% VISA INC CLASS A 0.5408% 0.5408% PROCTER & GAMBLE 0.4838% 0.4838% JPMORGAN CHASE & CO 0.4730% 0.4730% UNITEDHEALTH GROUP INC 0.4619% 0.4619% ISHARES RUSSELL 3000 ETF 0.4525% 0.4525% HOME DEPOT INC 0.4463% 0.4463% TAIWAN SEMICONDUCTOR MANUFACTURING 0.4337% 0.4337% MASTERCARD INC CLASS A 0.4325% 0.4325% INTEL CORPORATION CORP 0.4207% 0.4207% SHORT-TERM INVESTMENT FUND 0.4158% 0.4158% ROCHE HOLDING PAR AG 0.4017% 0.4017% VERIZON COMMUNICATIONS INC 0.3792% 0.3792% NVIDIA CORP 0.3721% 0.3721% AT&T INC 0.3583% 0.3583% SAMSUNG ELECTRONICS LTD 0.3483% 0.3483% ADOBE INC 0.3473% 0.3473% PAYPAL HOLDINGS INC 0.3395% 0.3395% WALT DISNEY 0.3342% 0.3342% CISCO SYSTEMS INC 0.3283% 0.3283% MERCK & CO INC 0.3242% 0.3242% NETFLIX INC 0.3213% 0.3213% EXXON MOBIL CORP 0.3138% 0.3138% NOVARTIS AG 0.3084% 0.3084% BANK OF AMERICA CORP 0.3046% 0.3046% PEPSICO INC 0.3036% 0.3036% PFIZER INC 0.3020% 0.3020% COMCAST CORP CLASS A 0.2929% 0.2929% COCA-COLA 0.2872% 0.2872% ABBVIE INC 0.2870% 0.2870% CHEVRON CORP 0.2767% 0.2767% WALMART INC 0.2767% -

Chapter Iv Strategy Analysis
CHAPTER IV STRATEGY ANALYSIS 4.1 Marketing Mix 4.1.1 Products Through the multiple Internet platforms in China, Tencent offers diversified services which include QQ, Weixin or Wechat for communications; Qzone for social networking; QQ Game platform for online games; QQ.com for information; Soso for search engine; Paipai and Tenpay for ecommerce transaction. The company’s business scope mainly covers four ereas: Internet value-add service (IVAS), mobile and telecommunication value-add services (MVAS), online advertising and e-Commerce transactions, to meet the various needs of Internet users including communication, information, entertainment, ecommerce and others. 4.1.2 Price Table 4. 1 Tencent major products and services’ usage fees Usage fee Communications QQ Free Weixin/Wechat Free Value-Added Services (VAS) a) Social Networks QQ Membership RMB 10 per month Super QQ Membership RMB 20 per month 26 Qzone Free; monthly subscription fee for VIP privileges (RMB10); and items sales from apps on open platform Tencent Microblog Free; monthly subscription fee for VIP privileges (RMB10); QQ Show (Avatars) Free; Monthly subscription fee for VIP privileges (RMB10); or item sales QQ Music Free; Monthly subscription fee for VIP privileges (RMB10); or item sale QQ mail Free Mobile VAS Monthly subscription fee for VIP privileges (RMB5-15); or item sales (RMB1- 2 per item) b) Online Games QQ Game Platform Monthly subscription fee for VIP privileges (RMB10-15) or item sales ACGs Monthly subscription fee for VIP privileges (RMB10-30) or item sales MMOGs Monthly subscription fee for VIP privileges (RMB20) or item sales; Time-based Mobile Games Monthly subscription fee for VIP privileges (RMB10) or item sales c) eCommerce Paipai.com Free Tenpay Free Online Advertising Brand display Inventories on QQ.com and verticals; online video platform; QQ IM, Mobile Browser etc; Pricing mainly by cost per time (CPT) or cost per day(CPD).