Cryptography in a Quantum World
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology?
Portland State University PDXScholar Young Historians Conference Young Historians Conference 2016 Apr 28th, 9:00 AM - 10:15 AM To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology? Hayley A. LeBlanc Sunset High School Follow this and additional works at: https://pdxscholar.library.pdx.edu/younghistorians Part of the European History Commons, and the History of Science, Technology, and Medicine Commons Let us know how access to this document benefits ou.y LeBlanc, Hayley A., "To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology?" (2016). Young Historians Conference. 1. https://pdxscholar.library.pdx.edu/younghistorians/2016/oralpres/1 This Event is brought to you for free and open access. It has been accepted for inclusion in Young Historians Conference by an authorized administrator of PDXScholar. Please contact us if we can make this document more accessible: [email protected]. To what extent did British advancements in cryptanalysis during World War 2 influence the development of computer technology? Hayley LeBlanc 1936 words 1 Table of Contents Section A: Plan of Investigation…………………………………………………………………..3 Section B: Summary of Evidence………………………………………………………………....4 Section C: Evaluation of Sources…………………………………………………………………6 Section D: Analysis………………………………………………………………………………..7 Section E: Conclusion……………………………………………………………………………10 Section F: List of Sources………………………………………………………………………..11 Appendix A: Explanation of the Enigma Machine……………………………………….……...13 Appendix B: Glossary of Cryptology Terms.…………………………………………………....16 2 Section A: Plan of Investigation This investigation will focus on the advancements made in the field of computing by British codebreakers working on German ciphers during World War 2 (19391945). -

How I Learned to Stop Worrying and Love the Bombe: Machine Research and Development and Bletchley Park
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by CURVE/open How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park Smith, C Author post-print (accepted) deposited by Coventry University’s Repository Original citation & hyperlink: Smith, C 2014, 'How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park' History of Science, vol 52, no. 2, pp. 200-222 https://dx.doi.org/10.1177/0073275314529861 DOI 10.1177/0073275314529861 ISSN 0073-2753 ESSN 1753-8564 Publisher: Sage Publications Copyright © and Moral Rights are retained by the author(s) and/ or other copyright owners. A copy can be downloaded for personal non-commercial research or study, without prior permission or charge. This item cannot be reproduced or quoted extensively from without first obtaining permission in writing from the copyright holder(s). The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the copyright holders. This document is the author’s post-print version, incorporating any revisions agreed during the peer-review process. Some differences between the published version and this version may remain and you are advised to consult the published version if you wish to cite from it. Mechanising the Information War – Machine Research and Development and Bletchley Park Christopher Smith Abstract The Bombe machine was a key device in the cryptanalysis of the ciphers created by the machine system widely employed by the Axis powers during the Second World War – Enigma. -

War Machines: Women's Computing Work and the Underpinnings of the Data-Driven State, 1930-1946
Programmed Inequality How Britain Discarded Women Technologists and Lost Its Edge in Computing Marie Hicks HD 6135 H53 2017 The Library Mt. St. Vincent Univ. Halifax, N.S. B3M 2J6 The MIT Press Cambridge, Massachusetts London, England 1 War Machines: Women's Computing Work and the Underpinnings of the Data-Driven State, 1930-1946 In recent years, the restoration of Bletchley Park has attracted worldwide attention. The country estate in Milton Keynes, United Kingdom, was the site of the most important codebreaking operations of World War II and home to the first digital, electronic, programmable computer: the Colossus. The British-designed and manufactured Colossus computers, of which there were ten in all by war's end, were critical to the conduct of Allied wartime operations. Unlike their better-known U.S. counter part, the ENIAC, the Colossus computers were actually deployed during the war, actively changing its outcome. Kept secret for decades, the full import of the developments at Bletchley has only recently become widely known.1 Yet while popular culture has begun to recognize the importance of Bletchley's wartime operations, misunderstandings persist about the nature of the information work performed there. The 2014 blockbuster The Imitation Game, for instance, cleaves the Colossus computers from the narrative entirely in favor of building a "great man" narrative for a single codebreaker.2 Hidden within the story of Bletchley is a less popular narrative that cannot leverage the appeal of a lone genius and his accomplishments. Thousands of women worked at Bletchley during the war-most in tech nical roles.3 Although it is generally accepted that the striking and wide ranging roles of the mostly women workers within Bletchley Park give lie to stereotypes about computing as a traditionally masculine field, the contributions of these women have not been analyzed as constitutive of larger trends in the history of computing. -

Code Breaking at Bletchley Park
Middle School Scholars’ CONTENTS Newsletter A Short History of Bletchley Park by Alex Lent Term 2020 Mapplebeck… p2-3 Alan Turing: A Profile by Sam Ramsey… Code Breaking at p4-6 Bletchley Park’s Role in World War II by Bletchley Park Harry Martin… p6-8 Review: Bletchley Park Museum by Joseph Conway… p9-10 The Women of Bletchley Park by Sammy Jarvis… p10-12 Bill Tutte: The Unsung Codebreaker by Archie Leishman… p12-14 A Very Short Introduction to Bletchley Park by Sam Corbett… p15-16 The Impact of Bletchley Park on Today’s World by Toby Pinnington… p17-18 Introduction A Beginner’s Guide to the Bombe by Luca “A gifted and distinguished boy, whose future Zurek… p19-21 career we shall watch with much interest.” This was the parting remark of Alan Turing’s Headmaster in his last school report. Little The German Equivalent of Bletchley could he have known what Turing would go on Park by Rupert Matthews… 21-22 to achieve alongside the other talented codebreakers of World War II at Bletchley Park. Covering Up Bletchley Park: Operation Our trip with the third year academic scholars Boniface by Philip Kimber… p23-25 this term explored the central role this site near Milton Keynes played in winning a war. 1 intercept stations. During the war, Bletchley A Short History of Bletchley Park Park had many cover names, which included by Alex Mapplebeck “B.P.”, “Station X” and the “Government Communications Headquarters”. The first mention of Bletchley Park in records is in the Domesday Book, where it is part of the Manor of Eaton. -

Notes and References Documents Held at the Public Record Office, London, Are Crown Copyright and Are Reproduced by Permission of the Controller Ofhm Stationery Office
Notes and References Documents held at the Public Record Office, London, are crown copyright and are reproduced by permission of the Controller ofHM Stationery Office. I NTRODUCTION Christopher Andrew and David Dilks I. David Dilks (ed.), The Diaries rifSir Alexander Cadogan O.M. 1938-1945 (Lon don , (971) , p. 21. 2. Interview with Professor Hinsley in Part 3 of the BBC Radio 4 documentary series 'T he Profession of Intelligence', written and presented by Christopher Andrew (producer Peter Everett); first broadcast 16 Aug 1981. 3. F. H. Hinsleyet al., British Intelligencein the Second World War (London, 1979-). The first two chapters of volume I contain a useful retrospect on the pre-war development of the intelligence community. Curiously, despite the publication of Professor Hinsley's volumes, the government has decided not to release the official histories commissioned by it on wartime counter-espionage and deception. The forthcoming (non-official) collection of essays edited by Ernest R. May, Knowing One's Enemies: IntelligenceAssessment before the Two World Wars (Princeton) promises to add significantly to our knowledge of the role of intelligence on the eve of the world wars. 4. House of Commons Education, Science and Arts Committee (Session 1982-83) , Public Records: Minutes ofEvidence, pp . 76-7. 5. Chapman Pincher, Their Trade is Treachery (London, 1981). Nigel West, A Matter of Trust: MI51945-72 (London, 1982). Both volumes contain ample evidence of extensive 'inside information'. 6. Nigel West , MI5: British Security Operations /90/-/945 (London, 1981), pp . 41, 49, 58. One of the most interesting studies of British peacetime intelligence which depends on a substantial amount of inside information is Antony Verrier's history of post-war British foreign policy , Through the Looking Glass (London, 1983) . -

Parallel Computing Prehistory
Parallel Computing Prehistory John Burkardt Information Technology Department Virginia Tech .......... FDI Summer Track V: Using Virginia Tech High Performance Computing http://people.sc.fsu.edu/∼jburkardt/presentations/... history 2009 vt.pdf 26-28 May 2009 1 / 43 How Did We Get Here? [date uncertain] I don't know where I am, but I'm making record time! Last transmission from a Navy pilot, somewhere in the Pacific... 2 / 43 What Happens if You Don't Know Where You Are In 1707, Admiral Sir Cloudesly Shovell sank his fleet by sailing directly into the Scilly Islands, which weren't where he thought they were...because he didn't know where he was. 3 / 43 Fine Clockwork Can Tell You Where You Are The British Admiralty put out an RFP, seeking a reliable means of determining longitude. John Harrison's "superclock" solved the problem...though of course he had much trouble getting reimbursed! 4 / 43 Babbage Shows Calculation is Like Clockwork The Navy still had plenty of navigational problems in the 19th century, and (partially) funded Charles Babbage's Difference Engine and his Analytical Engine. 5 / 43 Hollerith Automates Data Processing Hermann Hollerith, inspired by an automatic weaving device, developed a machine to tabulate the 1890 census - later a big seller for the International Business Machine Corporation, aka IBM. 6 / 43 Numerical Calculations Were Done by "Computers" Computing was done by computers, that is, people. This is the computer lab for the Harvard Astronomical Observatory in 1890. 7 / 43 Richardson Forecasts the Weather Lewis Richardson attempted the first weather forecast in 1917. -

How to Decrypt a Lorenz SZ42 Message Using Virtual Colossus 3D
How to decrypt a Lorenz SZ42 message using Virtual Colossus 3D A tutorial on decrypting a German Lorenz SZ42 message using Virtual Colossus 3D https://virtualcolossus.co.uk This document will take you through an example process used on Colossus to get the start positions of a received message. There wasn't a set program which would run to work out the settings, it was a matter of following a "menu" of different algorithms and sometimes required knowledge of what worked on a particular radio link. Colossus was not able to run a sequence of algorithms or use the results of previous calculations (like we would expect from a computer today), each run required a decision by the operator or code breaker assigned to that machine on which operation would be the next best to run. Once the start positions of each of the twelve rotors are calculated, we can use a Lorenz machine to try to decipher the final message. Wheel breaking We will assume that we have already broken the wheel patterns for this message. Wheel breaking meant working out the pin settings of all 501 pins on each of the twelve Lorenz cipher wheels. This was generally done using a few methods including from messages in depth (where several messages were received enciphered with the same key) in a process devised by Alan Turing called Turingery. Later, a new process called rectangling allowed wheel breaking potentially using a single long message. Colossus could help with rectangling to assist with wheel breaking, and Colossus 6 was used almost exclusively for this, but in general, wheel breaking was done by hand methods. -

Secure Volunteer Computing for Distributed Cryptanalysis
ysis SecureVolunteer Computing for Distributed Cryptanal Nils Kopal Secure Volunteer Computing for Distributed Cryptanalysis ISBN 978-3-7376-0426-0 kassel university 9 783737 604260 Nils Kopal press kassel university press ! "# $ %& & &'& #( )&&*+ , #()&- ( ./0 12.3 - 4 # 5 (!!&& & 6&( 7"#&7&12./ 5 -839,:,3:3/,2;1/,2% ' 5 -839,:,3:3/,2;13,3% ,' 05( (!!<& &!.2&.81..!")839:3:3/2;133 "=( (!!, #& !(( (2221,;2;13/ '12.97 # ?@7 & &, & ) ? “With magic, you can turn a frog into a prince. With science, you can turn a frog into a Ph.D. and you still have the frog you started with.” Terry Pratchett Abstract Volunteer computing offers researchers and developers the possibility to distribute their huge computational jobs to the computers of volunteers. So, most of the overall cost for computational power and maintenance is spread across the volunteers. This makes it possible to gain computing resources that otherwise only expensive grids, clusters, or supercomputers offer. Most volunteer computing solutions are based on a client-server model. The server manages the distribution of subjobs to the computers of volunteers, the clients, which in turn compute the subjobs and return the results to the server. The Berkeley Open Infrastructure for Network Computing (BOINC) is the most used middleware for volunteer computing. A drawback of any client-server architecture is the server being the single point of control and failure. To get rid of the single point of failure, we developed different distribution algorithms (epoch distribution algorithm, sliding-window distribution algorithm, and extended epoch distribution algorithm) based on unstructured peer-to-peer networks. These algorithms enable the researchers and developers to create volunteer computing networks without any central server. -
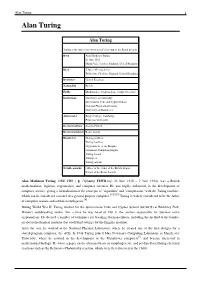
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Cryptology's Role in the Early Development of Computer
Cryptology’s Role in the Early Development of Computer Capabilities in the United States This publication is a product of the National Security Agency history program. It presents a historical perspective for informational and educational purposes, is the result of independent research, and does not necessarily reflect a position of NSA/CSS or any other U.S. government entity. This publication is distributed free by the National Security Agency. If you would like additional copies, please email your request to [email protected] or write to: Center for Cryptologic History National Security Agency 9800 Savage Road, Suite 6886 Fort George G. Meade, MD 20755-6886 Cover: A World War II COLOSSUS computer system. Cryptology’s Role in the Early Development of Computer Capabilities in the United States James V. Boone and James J. Hearn Center for Cryptologic History National Security Agency 2015 Preface ryptology is an extraordinary national endeavor where only first place counts. This attitude was prevalent among the partici- pantsC in the U.K.’s Government Code and Cypher School (GC&CS) activities at Bletchley Park1 during World War II. One of GC&CS’s many achievements during this time was the development and exten- sive use of the world’s first large-scale electronic digital computer called COLOSSUS. The highly skilled military personnel assigned to Bletchley Park returned to the U.S. with this experience and, aug- mented by the experience from other government-supported devel- opment activities in the U.S., their ideas for using electronic digital computer technology were quickly accepted by the U.S. -

Tommy Flowers - Wikipedia
7/2/2019 Tommy Flowers - Wikipedia Tommy Flowers Thomas Harold Flowers, BSc, DSc,[1] MBE (22 December 1905 – 28 October 1998) Thomas Harold Flowers was an English engineer with the British Post Office. During World War II, Flowers MBE designed and built Colossus, the world's first programmable electronic computer, to help solve encrypted German messages. Contents Early life World War II Post-war work and retirement See also References Bibliography External links Tommy Flowers – possibly taken Early life around the time he was at Bletchley Flowers was born at 160 Abbott Road, Poplar in London's East End on 22 December Park 1905, the son of a bricklayer.[2] Whilst undertaking an apprenticeship in mechanical Born 22 December 1905 engineering at the Royal Arsenal, Woolwich, he took evening classes at the University of Poplar, London, London to earn a degree in electrical engineering.[2] In 1926, he joined the England telecommunications branch of the General Post Office (GPO), moving to work at the Died 28 October 1998 research station at Dollis Hill in north-west London in 1930. In 1935, he married Eileen (aged 92) Margaret Green and the couple later had two children, John and Kenneth.[2] Mill Hill, London, From 1935 onward, he explored the use of electronics for telephone exchanges and by England 1939, he was convinced that an all-electronic system was possible. A background in Nationality English switching electronics would prove crucial for his computer designs. Occupation Engineer Title Mr World War II Spouse(s) Eileen Margaret Flowers' first contact with wartime codebreaking came in February 1941 when his Green director, W. -

Jewel Theatre Audience Guide Addendum: Alan Turing Biography
Jewel Theatre Audience Guide Addendum: Alan Turing Biography directed by Kirsten Brandt by Susan Myer Silton, Dramaturg © 2019 ALAN TURING The outline of the following overview of Turing’s life is largely based on his biography on Alchetron.com (https://alchetron.com/Alan-Turing), a “social encyclopedia” developed by Alchetron Technologies. It has been embellished with additional information from sources such as Andrew Hodges’ books, Alan Turing: The Enigma (1983) and Turing (1997) as well as his website, https://www.turing.org.uk. The following books have also provided additional information: Prof: Alan Turing Decoded (2015) by Dermot Turing, who is Alan’s nephew by way of his only sibling, John; The Turing Guide by B. Jack Copeland, Jonathan Bowen, Mark Sprevak, and Robin Wilson (2017); and Alan M. Turing, written by his mother, Sara, shortly after he died. The latter was republished in 2012 as Alan M. Turing – Centenary Edition with an Afterword entitled “My Brother Alan” by John Turing. The essay was added when it was discovered among John’s writings following his death. The republication also includes a new Foreword by Martin Davis, an American mathematician known for his model of post-Turing machines. Extended biographies of Christopher Morcom, Dillwyn Knox, Joan Clarke (the character of Pat Green in the play) and Sara Turing, which are provided as Addendums to this Guide, provide additional information about Alan. Beginnings Alan Mathison Turing was an English computer scientist, mathematician, logician, cryptanalyst, philosopher and theoretical biologist. He was born in a nursing home in Maida Vale, a tony residential district of London, England on June 23, 1912.