Trend Micro Apex One™ (Mac) 2019 Administrator's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Getting Started on a Mac with Macgamut Download
Getting started on a Macintosh computer with MacGAMUT 6 (Download) These step-by-step instructions will get you started on any Macintosh OS X computer, when you make a Download purchase of MacGAMUT 6 from the MacGAMUT website. Getting started with MacGAMUT 6 is EASY, but it's still a good idea to follow these printed instructions as you proceed step by step, marking off each step as you complete it. Follow these steps to install MacGAMUT 6 as a download: 1. First, download and install the MacGAMUT 6 software. Yes, you can complete the download and installation even before you make your online purchase. You just won’t be able to use the installed program until you’ve paid for it! a. From the Home page at www.macgamut.com, follow the links from the Installers link on the left-hand side of the screen to go to the MacGAMUT Web Installers page. b. Read the “How-to” Videos paragraph before scrolling down to click the appropriate installer for your computer and system. c. You’ll find the downloaded Installer in your Macintosh’s Downloads folder. (If you are not working on your own computer, you can copy the Installer to a flash drive so you can install it later on your computer.) d. The Installer will start automatically when you open the Installer package. Just follow the instructions to complete your installation. e. If you are installing MacGAMUT 6 for the first time, you will need to restart your computer after the installation process is finished. f. The program installs in a folder labeled MacGAMUT 6 in your computer’s Applications folder. -

DECIPHER: Harnessing Local Sequence Context to Improve Protein Multiple Sequence Alignment Erik S
Wright BMC Bioinformatics (2015) 16:322 DOI 10.1186/s12859-015-0749-z RESEARCH ARTICLE Open Access DECIPHER: harnessing local sequence context to improve protein multiple sequence alignment Erik S. Wright1,2 Abstract Background: Alignment of large and diverse sequence sets is a common task in biological investigations, yet there remains considerable room for improvement in alignment quality. Multiple sequence alignment programs tend to reach maximal accuracy when aligning only a few sequences, and then diminish steadily as more sequences are added. This drop in accuracy can be partly attributed to a build-up of error and ambiguity as more sequences are aligned. Most high-throughput sequence alignment algorithms do not use contextual information under the assumption that sites are independent. This study examines the extent to which local sequence context can be exploited to improve the quality of large multiple sequence alignments. Results: Two predictors based on local sequence context were assessed: (i) single sequence secondary structure predictions, and (ii) modulation of gap costs according to the surrounding residues. The results indicate that context-based predictors have appreciable information content that can be utilized to create more accurate alignments. Furthermore, local context becomes more informative as the number of sequences increases, enabling more accurate protein alignments of large empirical benchmarks. These discoveries became the basis for DECIPHER, a new context-aware program for sequence alignment, which outperformed other programs on largesequencesets. Conclusions: Predicting secondary structure based on local sequence context is an efficient means of breaking the independence assumption in alignment. Since secondary structure is more conserved than primary sequence, it can be leveraged to improve the alignment of distantly related proteins. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -
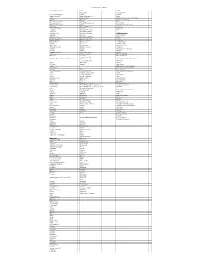
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Introduction to Xgrid: Cluster Computing for Everyone
Introduction to Xgrid: Cluster Computing for Everyone Barbara J. Breen1, John F. Lindner2 1Department of Physics, University of Portland, Portland, Oregon 97203 2Department of Physics, The College of Wooster, Wooster, Ohio 44691 (First posted 4 January 2007; last revised 24 July 2007) Xgrid is the first distributed computing architecture built into a desktop operating system. It allows you to run a single job across multiple computers at once. All you need is at least one Macintosh computer running Mac OS X v10.4 or later. (Mac OS X Server is not required.) We provide explicit instructions and example code to get you started, including examples of how to distribute your computing jobs, even if your initial cluster consists of just two old laptops in your basement. 1. INTRODUCTION Apple’s Xgrid technology enables you to readily convert any ad hoc collection of Macintosh computers into a low-cost supercomputing cluster. Xgrid functionality is integrated into every copy of Mac OS X v10.4. For more information, visit http://www.apple.com/macosx/features/xgrid/. In this article, we show how to unlock this functionality. In Section 2, we guide you through setting up the cluster. In Section 3, we illustrate two simple ways to distribute jobs across the cluster: shell scripts and batch files. We don’t assume you know what shell scripts, batch files, or C/C++ programs are (although you will need to learn). Instead, we supply explicit, practical examples. 2. SETTING UP THE CLUSTER In a typical cluster of three or more computers (or processors), a client computer requests a job from the controller computer, which assigns an agent computer to perform it. -

Analysis the Structure of SAM and Cracking Password Base on Windows Operating System
International Journal of Future Computer and Communication, Vol. 5, No. 2, April 2016 Analysis the Structure of SAM and Cracking Password Base on Windows Operating System Jiang Du and Jiwei Li latest Windows 10, the registry contains information that Abstract—Cracking Windows account password is critical to Windows continually references during operation, such as the forensic analyst. The general methods of decipher password profiles for each user, the applications installed on the include clean the password, guess by social engineering, computer and the types of documents, property sheet settings mathematical analyzing, exhaustive attacking, dictionary attacking and rainbow tables algorithm. This paper provides the of folders and application icons, what hardware exists on the details about the Security Account Manager(SAM) database system, and the ports that are being used [3]. On disk, the and describes how to get the user information from SAM and Windows registry is not only a large file but a set of discrete cracks account password of Windows 10 that the latest files called hives. Each hive is a hierarchical tree which operating system of Microsoft. identified by a root key to provide access to all sub-keys in the tree up to 512 levels deep. Index Terms—SAM, decipher password, crack password, Windows 10. III. SECURITY ACCOUNT MANAGER (SAM) I. INTRODUCTION Security Account Manager (SAM) is a database used to In the process of computer forensic the analyst need to store user account information, including password, account enter the Windows operating system by cracking windows groups, access rights, and special privileges in Windows account password to collect evidence at times. -

Decipher Prostate Cancer Classifier
Lab Management Guidelines v2.0.2019 Decipher Prostate Cancer Classifier MOL.TS.294.A v2.0.2019 Procedures addressed The inclusion of any procedure code in this table does not imply that the code is under management or requires prior authorization. Refer to the specific Health Plan's procedure code list for management requirements. Procedures addressed by this Procedure codes guideline Decipher Prostate Cancer Classifier 81479 What are gene expression profiling tests for prostate cancer Definition Prostate cancer (PC) is the most common cancer and a leading cause of cancer- related deaths worldwide. It is considered a heterogeneous disease with highly variable prognosis.1 High-risk prostate cancer (PC) patients treated with radical prostatectomy (RP) undergo risk assessment to assess future disease prognosis and determine optimal treatment strategies. Post-RP pathology findings, such as disease stage, baseline Gleason score, time of biochemical recurrence (BCR) after RP, and PSA doubling- time, are considered strong predictors of disease-associated metastasis and mortality. Following RP, up to 50% of patients have pathology or clinical features that are considered at high risk of recurrence and these patients usually undergo post-RP treatments, including adjuvant or salvage therapy or radiation therapy, which can have serious risks and complications. According to clinical practice guideline recommendations, high risk patients should undergo 6 to 8 weeks of radiation therapy (RT) following RP. However, approximately 90% of high-risk patients -

Comparing Tools for Non-Coding RNA Multiple Sequence Alignment Based On
Downloaded from rnajournal.cshlp.org on September 26, 2021 - Published by Cold Spring Harbor Laboratory Press ES Wright 1 1 TITLE 2 RNAconTest: Comparing tools for non-coding RNA multiple sequence alignment based on 3 structural consistency 4 Running title: RNAconTest: benchmarking comparative RNA programs 5 Author: Erik S. Wright1,* 6 1 Department of Biomedical Informatics, University of Pittsburgh (Pittsburgh, PA) 7 * Corresponding author: Erik S. Wright ([email protected]) 8 Keywords: Multiple sequence alignment, Secondary structure prediction, Benchmark, non- 9 coding RNA, Consensus secondary structure 10 Downloaded from rnajournal.cshlp.org on September 26, 2021 - Published by Cold Spring Harbor Laboratory Press ES Wright 2 11 ABSTRACT 12 The importance of non-coding RNA sequences has become increasingly clear over the past 13 decade. New RNA families are often detected and analyzed using comparative methods based on 14 multiple sequence alignments. Accordingly, a number of programs have been developed for 15 aligning and deriving secondary structures from sets of RNA sequences. Yet, the best tools for 16 these tasks remain unclear because existing benchmarks contain too few sequences belonging to 17 only a small number of RNA families. RNAconTest (RNA consistency test) is a new 18 benchmarking approach relying on the observation that secondary structure is often conserved 19 across highly divergent RNA sequences from the same family. RNAconTest scores multiple 20 sequence alignments based on the level of consistency among known secondary structures 21 belonging to reference sequences in their output alignment. Similarly, consensus secondary 22 structure predictions are scored according to their agreement with one or more known structures 23 in a family. -

Download the Os X Mavericks Application from the Mac App Store
Download the os x mavericks application from the mac app store CLICK HERE TO DOWNLOAD Nov 01, · Open the App Store and search for “OS X Mavericks” or just click the direct App Store link (free, downloading one times or is always free) Click the “Download” button and confirm that you want to download the OS X Installer again by choosing “Continue”. Nov 07, · Connecting to the Mac App Store. The "Install OS X Mavericks" should be on the order of 5 or 6GB in size (I do not have the exact size at the moment, but GB is way too small). More Less. Question: Q: where can I download OS X Mavericks Update More Less. Apple Footer. May 28, · About Mac OS Mavericks Apple OS X Mavericks was first announced in June and was then released in October of It was the tenth big release of the Apple OS X line. At the same time, Mavericks was promoted and marketed as a major release just as was the case with the Lion and Mountain Lion OS X updates which came before the Mavericks. Oct 22, · Apple released OS X Mavericks today, Download Free from mac app store. plus new features compatible for macbook, mac mini, imac and macbook air models. OS X Mavericks -- the latest update to Apple's desktop OS -- noticeably improves the overall experience on for both new and older renuzap.podarokideal.ru:Free: Mac OS. Oct 23, · OS X Server requires Mavericks and is available from the Mac App Store for $ (US). Apple designs Macs, the best personal computers in the world, along with OS X, iLife, iWork and professional software. -

Getting Started Deciphering
Getting Started DECIPHERing Erik S. Wright May 19, 2021 Contents 1 About DECIPHER 1 2 Design Philosophy 2 2.1 Curators Protect the Originals . 2 2.2 Don't Reinvent the Wheel . 2 2.3 That Which is the Most Difficult, Make Fastest . 2 2.4 Stay Organized . 2 3 Functionality 3 4 Installation 5 4.1 Typical Installation (recommended) . 5 4.2 Manual Installation . 5 4.2.1 All platforms . 5 4.2.2 MacOSX........................................... 6 4.2.3 Linux ............................................. 6 4.2.4 Windows ........................................... 6 5 Example Workflow 6 6 Session Information 11 1 About DECIPHER DECIPHER is a software toolset that can be used for deciphering and managing biological sequences efficiently using the R statistical programming language. The program features tools falling into five categories: Sequence databases: import, maintain, view, and export a massive number of sequences. Sequence alignment: accurately align thousands of DNA, RNA, or amino acid sequences. Quickly find and align the syntenic regions of multiple genomes. Oligo design: test oligos in silico, or create new primer and probe sequences optimized for a variety of objectives. Manipulate sequences: trim low quality regions, correct frameshifts, reorient nucleotides, determine consensus, or digest with restriction enzymes. Analyze sequences: find chimeras, classify into a taxonomy of organisms or functions, detect repeats, predict secondary structure, create phylogenetic trees, and reconstruct ancestral states. 1 Gene finding: predict coding and non-coding genes in a genome, extract them from the genome, and export them to a file. DECIPHER is available under the terms of the GNU Public License version 3. 2 Design Philosophy 2.1 Curators Protect the Originals One of the core principles of DECIPHER is the idea of the non-destructive workflow. -

Simplified Macos Upgrade Workflow This Guide Walks You Through the Workflow Process for Deciding How to Upgrade Your Mac Fleet to Macos High Sierra Using Jamf Pro
Simplified macOS Upgrade Workflow This guide walks you through the workflow process for deciding how to upgrade your Mac fleet to macOS High Sierra using Jamf Pro. With the release of a new Apple operating system, it’s recommended to first check compatibility with existing software, test the stability of the OS, and make sure it meets the organization’s needs prior to upgrading. That’s why the first question you need to ask is—Do you want to upgrade now? NO Jamf Pro has the ability to block the install file for any macOS upgrade. If you want to wait on upgrading, simply create a policy that will block the macOS High Sierra installer app from running. YES Once you have decided to move forward with an upgrade you need to determine what to do with the existing data on your Macs. Are these shared Macs in a lab? Are they assigned to a specific user? The bottom line is— Do you want to keep the data intact? There are 4 methods to deploy the new macOS for your users with the data intact. In all KEEP DATA these options, using the Caching Service within macOS will help reduce network traffic. Consider using this service on your network. Macs enrolled via the Device Enrollment Program (DEP) and running 10.11.4 or later can be upgraded by sending a mobile device management (MDM) command to download and install macOS High Sierra. No user interaction or admin rights required for this option. Download the “Install macOS High Sierra” app from the Mac App Store. -

Mac Os High Sierra App Store Background Download Question: Q: How to Download Full Installer of High Sierra
mac os high sierra app store background download Question: Q: How to Download full installer of High sierra. i have Purchased macbook pro mid 2014 13" today. it currently have Mac Os X Yosemite .I want to download Mac Os High Sierra . When ever i tried to download it from app store, it just download a 19.9MB file instead of 4.80GB. i have 4 MacBooks. i want to download full installer and then make a bootable USB from it to update my all 4 MacBooks. what should i do? how can i download full installer . MacBook Pro with Retina display, OS X Yosemite (10.10.5), Macbook Pro Mid 2014 13" Download the New macOS High Sierra 10.13 Wallpaper for your Mac. Apart from the amazing hardware announcements at WWDC 2017, Apple unveiled a new operating system for Mac called macOS High Sierra. The new operating system comes with many performance improvements under-the-hood and new features, such as the Apple File System, support for HVEC format, better user privacy in Safari, and much more. As is the case with every new iteration of macOS, a new wallpaper was also added to macOS 10.13 that looks beautiful. Below is a preview of the macOS High Sierra wallpaper. To download it, click on the link below it and save to your desktop. The first beta version of macOS can be downloaded by developers via the software update mechanism in the Mac App Store or through the Apple Developer Center. The public beta will be released by the end of June, while the official release will be made later this year as a free software update from the MacApp Store.