Openafs Client for Macos
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Getting Started on a Mac with Macgamut Download
Getting started on a Macintosh computer with MacGAMUT 6 (Download) These step-by-step instructions will get you started on any Macintosh OS X computer, when you make a Download purchase of MacGAMUT 6 from the MacGAMUT website. Getting started with MacGAMUT 6 is EASY, but it's still a good idea to follow these printed instructions as you proceed step by step, marking off each step as you complete it. Follow these steps to install MacGAMUT 6 as a download: 1. First, download and install the MacGAMUT 6 software. Yes, you can complete the download and installation even before you make your online purchase. You just won’t be able to use the installed program until you’ve paid for it! a. From the Home page at www.macgamut.com, follow the links from the Installers link on the left-hand side of the screen to go to the MacGAMUT Web Installers page. b. Read the “How-to” Videos paragraph before scrolling down to click the appropriate installer for your computer and system. c. You’ll find the downloaded Installer in your Macintosh’s Downloads folder. (If you are not working on your own computer, you can copy the Installer to a flash drive so you can install it later on your computer.) d. The Installer will start automatically when you open the Installer package. Just follow the instructions to complete your installation. e. If you are installing MacGAMUT 6 for the first time, you will need to restart your computer after the installation process is finished. f. The program installs in a folder labeled MacGAMUT 6 in your computer’s Applications folder. -

Examining the Viability of MINIX 3 As a Consumer Operating
Examining the Viability of MINIX 3 as a Consumer Operating System Joshua C. Loew March 17, 2016 Abstract The developers of the MINIX 3 operating system (OS) believe that a computer should work like a television set. You should be able to purchase one, turn it on, and have it work flawlessly for the next ten years [6]. MINIX 3 is a free and open-source microkernel-based operating system. MINIX 3 is still in development, but it is capable of running on x86 and ARM processor architectures. Such processors can be found in computers such as embedded systems, mobile phones, and laptop computers. As a light and simple operating system, MINIX 3 could take the place of the software that many people use every day. As of now, MINIX 3 is not particularly useful to a non-computer scientist. Most interactions with MINIX 3 are done through a command-line interface or an obsolete window manager. Moreover, its tools require some low-level experience with UNIX-like systems to use. This project will examine the viability of MINIX 3 from a performance standpoint to determine whether or not it is relevant to a non-computer scientist. Furthermore, this project attempts to measure how a microkernel-based operating system performs against a traditional monolithic kernel-based OS. 1 Contents 1 Introduction 5 2 Background and Related Work 6 3 Part I: The Frame Buffer Driver 7 3.1 Outline of Approach . 8 3.2 Hardware and Drivers . 8 3.3 Challenges and Strategy . 9 3.4 Evaluation . 10 4 Progress 10 4.1 Compilation and Installation . -

App Frameworks #WWDC16
App Frameworks #WWDC16 Improving Existing Apps Using modern best practices Session 213 Woody L., � to the Knowledge © 2016 Apple Inc. All rights reserved. Redistribution or public display not permitted without written permission from Apple. Agenda Reduce Technical Debt Asset Catalogs Dependency Injection Live Playgrounds Cycle of Development You down with ‘Dub-DC? Yeah, you know me. Lots of Requests Your boss More Requests Your customers Technical Debt //TODO: Write and clean up Customer’s Perspective Actuality Duarte requesting hi-res photo AppStore New API zsh AppKit CF AirPortUtility PreferencesApp iCal Foundation AVFoundation AirPortAssistant AirPortSettings AirPortAssistant OpenCL GameKit Dock Mail MapKit MobileMusicPlayer xnu AppKit AppStore MobileSafari zsh QuickTime udf WebKit BlueToothSettings cups Messages Dock ActivityMonitor MobileSafari bash Mail AccessibilitySettings GameKit GameKitServices MediaPlayerUI MediaPlayer MediaStream MobileMail Swift 3 Source code compatibility New and Updated Platforms A Dev’s Run Loop Bug Fixes Technical Debt New and Platforms ♽Updated APIs Customer Roadmap A Dev’s Run Loop Bug Fixes Technical Debt New and Platforms ♽Updated APIs Customer Roadmap A Dev’s Run Loop Bug Fixes Technical Debt New and Platforms ♽Updated APIs Customer Roadmap The Essentials A very good place to start Earlier iOS 8 5% 11% Minimum Deployment of iOS 8 • 95% of Devices iOS 9 84% As measured by the App Store on May 9, 2016 Pick a Deployment Target Latest update of previous release Deprecated API Deprecated API Treat Warnings -

Microkernels in a Bit More Depth Early Operating Systems Had Very Little Structure a Strictly Layered Approach Was Promoted by Dijkstra
Motivation Microkernels In a Bit More Depth Early operating systems had very little structure A strictly layered approach was promoted by Dijkstra THE Operating System [Dij68] COMP9242 2007/S2 Week 4 Later OS (more or less) followed that approach (e.g., Unix). UNSW Such systems are known as monolithic kernels COMP9242 07S2 W04 1 Microkernels COMP9242 07S2 W04 2 Microkernels Issues of Monolithic Kernels Evolution of the Linux Kernel E Advantages: Kernel has access to everything: all optimisations possible all techniques/mechanisms/concepts implementable Kernel can be extended by adding more code, e.g. for: new services support for new harwdare Problems: Widening range of services and applications OS bigger, more complex, slower, more error prone. Need to support same OS on different hardware. Like to support various OS environments. Distribution impossible to provide all services from same (local) kernel. COMP9242 07S2 W04 3 Microkernels COMP9242 07S2 W04 4 Microkernels Approaches to Tackling Complexity Evolution of the Linux Kernel Part 2 A Classical software-engineering approach: modularity Software-engineering study of Linux kernel [SJW+02]: (relatively) small, mostly self-contained components well-defined interfaces between them Looked at size and interdependencies of kernel "modules" enforcement of interfaces "common coupling": interdependency via global variables containment of faults to few modules Analysed development over time (linearised version number) Doesn't work with monolithic kernels: Result 1: -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -
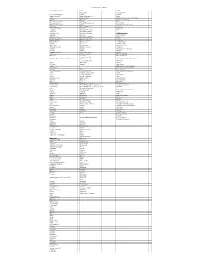
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Introduction to Xgrid: Cluster Computing for Everyone
Introduction to Xgrid: Cluster Computing for Everyone Barbara J. Breen1, John F. Lindner2 1Department of Physics, University of Portland, Portland, Oregon 97203 2Department of Physics, The College of Wooster, Wooster, Ohio 44691 (First posted 4 January 2007; last revised 24 July 2007) Xgrid is the first distributed computing architecture built into a desktop operating system. It allows you to run a single job across multiple computers at once. All you need is at least one Macintosh computer running Mac OS X v10.4 or later. (Mac OS X Server is not required.) We provide explicit instructions and example code to get you started, including examples of how to distribute your computing jobs, even if your initial cluster consists of just two old laptops in your basement. 1. INTRODUCTION Apple’s Xgrid technology enables you to readily convert any ad hoc collection of Macintosh computers into a low-cost supercomputing cluster. Xgrid functionality is integrated into every copy of Mac OS X v10.4. For more information, visit http://www.apple.com/macosx/features/xgrid/. In this article, we show how to unlock this functionality. In Section 2, we guide you through setting up the cluster. In Section 3, we illustrate two simple ways to distribute jobs across the cluster: shell scripts and batch files. We don’t assume you know what shell scripts, batch files, or C/C++ programs are (although you will need to learn). Instead, we supply explicit, practical examples. 2. SETTING UP THE CLUSTER In a typical cluster of three or more computers (or processors), a client computer requests a job from the controller computer, which assigns an agent computer to perform it. -

Troubleshooting Rosetta Stone Log-In Issues on Mobile
Portal > Knowledgebase > Teaching Learning and Research > Rosetta Stone > Troubleshooting Rosetta Stone Log-in Issues on Mobile Troubleshooting Rosetta Stone Log-in Issues on Mobile Kyle A. Oliveira - 2019-05-31 - 0 Comments - in Rosetta Stone A recent update to the Rosetta Stone apps on both iOS and Android may cause authentication issues. Please refer to the information below for resolving these issues. iOS To prevent any further issues regarding logging into the app on iOS, you must avoid opening the app unless you've authenticated through Brown's log in portal. Opening the app outside of logging in through Brown, will most likely result in the inability to log in and use the app. If you are having issues logging into it: Solution 1 1. Open your device's web browser, visit rosettastone.brown.edu, and log in 2. Click the “Launch Rosetta Stone Language Lessons” link to launch the app 3. You will experience the same problem as in the past - you will just see a "splash" screen instead of being logged in. On this screen, click Enterprise And Education Learners. 4. On the login screen that appears, type three random values (just a single letter will work) into the Username, Password, and Namespace fields. 5. You will see an error message. Click Try again and proceed with the next step. 6. Return to your web browser and again, visit rosettastone.brown.edu. 7. Click the “Launch Rosetta Stone Language Lessons” link to launch the app again. 8. Wait for the login to proceed - it should work. If you still see the error message, click the Try Again option. -

Pooch Manual In
What’s New As of August 21, 2011, Pooch is updated to version 1.8.3 for use with OS X 10.7 “Lion”: Pooch users can renew their subscriptions today! Please see http://daugerresearch.com/pooch for more! On November 17, 2009, Pooch was updated to version 1.8: • Linux: Pooch can now cluster nodes running 64-bit Linux, combined with Mac • 64-bit: Major internal revisions for 64-bit, particularly updated data types and structures, for Mac OS X 10.6 "Snow Leopard" and 64-bit Linux • Sockets: Major revisions to internal networking to adapt to BSD Sockets, as recommended by Apple moving forward and required for Linux • POSIX Paths: Major revisions to internal file specification format in favor of POSIX paths, recommended by Apple moving forward and required for Linux • mDNS: Adapted usage of Bonjour service discovery to use Apple's Open Source mDNS library • Pooch Binary directory: Added Pooch binary directory support, making possible launching jobs using a remotely-compiled executable • Minor updates and fixes needed for Mac OS X 10.6 "Snow Leopard" Current Pooch users can renew their subscriptions today! Please see http://daugerresearch.com/pooch for more! On April 16, 2008, Pooch was updated to version 1.7.6: • Mac OS X 10.5 “Leopard” spurs updates in a variety of Pooch technologies: • Network Scan window • Preferences window • Keychain access • Launching via, detection of, and commands to the Terminal • Behind the Login window behavior • Other user interface and infrastructure adjustments • Open MPI support: • Complete MPI support using libraries -

Rosetta Stone Software Use Opportunity User Expectations and Guidelines
Rosetta Stone Software Use Opportunity User Expectations and Guidelines Introduction CYFD-BHS and the Southwest Regional Training Center at NMSU are providing the opportunity to current approved CYFD staff to access Spanish language lessons. We have selected Rosetta Stone for this online language learning opportunity. Rosetta Stone’s interactive and award-winning software creates an intuitive and engaging environment for thinking and communicating in a new language. Through Rosetta Stone’s software, users will have access to: Language Training: Reading, writing, speaking and listening skills are introduced in core lessons, then key skills, such as grammar and vocabulary, are refined in focused activities. Speech recognition technology evaluates the pronunciation of each word and sentence, providing immediate feedback. Games & Activities: Interactive games sharpen language skills and stories provide students opportunities to read long passages aloud. Games & Activities reinforces language learned in Language Training and builds students' confidence. Rosetta Stone Language Training for Apple and Android: Students will be able to continue their language training via our mobile app. Progress made in this application syncs with progress in the program, and vice versa. Note: The Rosetta Stone Language Training mobile app is available for select languages. Additional information can be found at www.rosettastone.com. User Guidelines 1. Rosetta Stone software licenses are available to current Children, Youth and Family Department Community Behavioral Health Clinicians (CBHCs) and others approved by a CYFD-Behavioral Health Services Deputy Director. 2. Rosetta Stone software is not intended to train clinicians to provide services in a second language. 3. Individuals who are interested in utilizing the Rosetta Stone software must complete the User Access Request Form at https://bhs.nmsu.edu/rosetta-stone . -

SSMUG Feb Newsletter UPCOMING MEETINGS Page 2 Ƒƒ
February 2008 UPCOMING MEETINGS Apple reports best MARCH Search Engine quarterly revenue and Optimization of Web Sites. earnings in its history Special Meeting Notice Announcing financial results for its A shortened version of a seminar. fiscal 2008 first quarter, which The full seminar on Search ended December 29, 2007, Apple Engine Optimazation costs today posted revenue of $9.6 billion $39.00 but we get a free preview at and net quarterly profit of $1.58 the March meeting! billion, or $1.76 per diluted share. These results compare to revenue Meetings will be held from June of $7.1 billion and net quarterly through December at the Grande profit of $1 billion, or $1.14 per Prairie Public Library. diluted share, in the year-ago quarter. In attaining its highest revenue and earnings in company APPLE NEWS history, Apple shipped 2,319,000 Andrea Jung Joins Apple’s Macs, a 44% unit growth and 47% revenue growth over the year ago Board of Directors quarter; sold 22,121,000 iPods, representing five percent unit CUPERTINO, California—January growth and 17 percent revenue 7—Apple® today announced that growth over the year-ago quarter; Andrea Jung, chairman and chief and sold 2,315,000 iPhones in the executive officer of Avon Products, quarter. [Jan 22, 2008] was elected to Apple’s board of directors. Andrea also serves on the board of directors of the General Electric Company and is a member Tickled pink over new of the New York Presbyterian iPod nano Hospital board of trustees and the Catalyst board of directors.