Computational Techniques for Analyzing Tumor DNA Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Prioritization of Metabolic Genes As Novel Therapeutic Targets in Estrogen-Receptor Negative Breast Tumors Using Multi-Omics Data and Text Mining
www.oncotarget.com Oncotarget, 2019, Vol. 10, (No. 39), pp: 3894-3909 Research Paper Prioritization of metabolic genes as novel therapeutic targets in estrogen-receptor negative breast tumors using multi-omics data and text mining Dinesh Kumar Barupal1,*, Bei Gao1,*, Jan Budczies2, Brett S. Phinney4, Bertrand Perroud4, Carsten Denkert2,3 and Oliver Fiehn1 1West Coast Metabolomics Center, University of California, Davis, CA, USA 2Institute of Pathology, Charité University Hospital, Berlin, Germany 3German Institute of Pathology, Philipps-University Marburg, Marburg, Germany 4UC Davis Genome Center, University of California, Davis, CA, USA *Co-first authors and contributed equally to this work Correspondence to: Oliver Fiehn, email: [email protected] Keywords: set-enrichment; ChemRICH; multi-omics; metabolic networks; candidate gene prioritization Received: March 12, 2019 Accepted: May 13, 2019 Published: June 11, 2019 Copyright: Barupal et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License 3.0 (CC BY 3.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. ABSTRACT Estrogen-receptor negative (ERneg) breast cancer is an aggressive breast cancer subtype in the need for new therapeutic options. We have analyzed metabolomics, proteomics and transcriptomics data for a cohort of 276 breast tumors (MetaCancer study) and nine public transcriptomics datasets using univariate statistics, meta- analysis, Reactome pathway analysis, biochemical network mapping and text mining of metabolic genes. In the MetaCancer cohort, a total of 29% metabolites, 21% proteins and 33% transcripts were significantly different (raw p <0.05) between ERneg and ERpos breast tumors. -

Clinical Characterization of Chromosome 5Q21.1–21.3 Microduplication: a Case Report
Open Medicine 2020; 15: 1123–1127 Case Report Shuang Chen, Yang Yu, Han Zhang, Leilei Li, Yuting Jiang, Ruizhi Liu, Hongguo Zhang* Clinical characterization of chromosome 5q21.1–21.3 microduplication: A case report https://doi.org/10.1515/med-2020-0199 Keywords: chromosome 5, prenatal diagnosis, microdu- received May 20, 2020; accepted September 28, 2020 plication, genetic counseling Abstract: Chromosomal microdeletions and microdupli- cations likely represent the main genetic etiologies for children with developmental delay or intellectual dis- ability. Through prenatal chromosomal microarray ana- 1 Introduction lysis, some microdeletions or microduplications can be detected before birth to avoid unnecessary abortions or Chromosomal microdeletions,microduplications,and birth defects. Although some microdeletions or microdu- unbalanced rearrangements represent the main genetic plications of chromosome 5 have been reported, nu- etiological factors for children with developmental delay [ ] - merous microduplications remain undescribed. We de- or intellectual disability 1 . Currently, chromosomal mi ( ) fi - - scribe herein a case of a 30-year-old woman carrying a croarray analysis CMA is considered a rst tier diag [ ] - fetus with a chromosome 5q21.1–q21.3 microduplication. nostic tool for these children 2 . Through prenatal diag Because noninvasive prenatal testing indicated a fetal nosis of CMA, some microdeletions or microduplications - chromosome 5 abnormality, the patient underwent am- can be detected before birth to avoid unnecessary abor [ ] niocentesis at 22 weeks 4 days of gestation. Karyotyping tions or birth defects 3 . The clinical features of some and chromosomal microarray analysis were performed on chromosome 5 microduplications have been described [ – ] [ ] amniotic fluid cells. Fetal behavioral and structural ab- previously 4 8 . -

Biological Pathways, Candidate Genes, and Molecular Markers Associated with Quality-Of-Life Domains: an Update
Qual Life Res (2014) 23:1997–2013 DOI 10.1007/s11136-014-0656-1 REVIEW Biological pathways, candidate genes, and molecular markers associated with quality-of-life domains: an update Mirjam A. G. Sprangers • Melissa S. Y. Thong • Meike Bartels • Andrea Barsevick • Juan Ordon˜ana • Qiuling Shi • Xin Shelley Wang • Pa˚l Klepstad • Eddy A. Wierenga • Jasvinder A. Singh • Jeff A. Sloan Accepted: 19 February 2014 / Published online: 7 March 2014 Ó Springer International Publishing Switzerland 2014 Abstract (depressed mood) and positive (well-being/happiness) Background There is compelling evidence of a genetic emotional functioning, social functioning, and overall foundation of patient-reported quality of life (QOL). Given QOL. the rapid development of substantial scientific advances in Methods We followed a purposeful search algorithm of this area of research, the current paper updates and extends existing literature to capture empirical papers investigating reviews published in 2010. the relationship between biological pathways and molecu- Objectives The objective was to provide an updated lar markers and the identified QOL domains. overview of the biological pathways, candidate genes, and Results Multiple major pathways are involved in each molecular markers involved in fatigue, pain, negative QOL domain. The inflammatory pathway has the strongest evidence as a controlling mechanism underlying fatigue. Inflammation and neurotransmission are key processes On behalf of the GeneQol Consortium. involved in pain perception, and the catechol-O-methyl- transferase (COMT) gene is associated with multiple sorts Electronic supplementary material The online version of this article (doi:10.1007/s11136-014-0656-1) contains supplementary of pain. The neurotransmitter and neuroplasticity theories material, which is available to authorized users. -

Prioritization of Metabolic Genes As Novel Therapeutic Targets
bioRxiv preprint doi: https://doi.org/10.1101/515403; this version posted January 9, 2019. The copyright holder for this preprint (which was not certified by peer review) is the author/funder, who has granted bioRxiv a license to display the preprint in perpetuity. It is made available under aCC-BY-ND 4.0 International license. 1 Prioritization of metabolic genes as novel therapeutic targets 2 in estrogen-receptor negative breast tumors using multi-omics data and text mining 3 4 Dinesh Kumar Barupal#,1, Bei Gao#, 1, Jan Budczies2, Brett S. Phinney4, Bertrand Perroud4, 5 Carsten Denkert2,3 and Oliver Fiehn*,1 6 Affiliations 7 1West Coast Metabolomics Center, University of California, Davis, CA, 95616 8 2Institute of Pathology, Charité University Hospital, Berlin, 9 3German Institute of Pathology, Philipps-University Marburg, Germany 10 4UC Davis Genome Center, University of California, Davis, CA, 95616 11 #Co-first authors and contributed equally. 12 Email address for all authors 13 Dinesh Kumar Barupal: [email protected] 14 Bei Gao: [email protected] 15 Carsten Denkert: [email protected] 16 Brett S. Phinney: [email protected] 17 Bertrand Perroud: [email protected] 18 Jan Budczies: [email protected] 19 Oliver Fiehn: [email protected] 20 21 * Corresponding Author: 22 Oliver Fiehn 23 West Coast Metabolomics Center, 24 University of California, Davis, CA, 95616 25 Email: [email protected] 1 bioRxiv preprint doi: https://doi.org/10.1101/515403; this version posted January 9, 2019. The copyright holder for this preprint (which was not certified by peer review) is the author/funder, who has granted bioRxiv a license to display the preprint in perpetuity. -
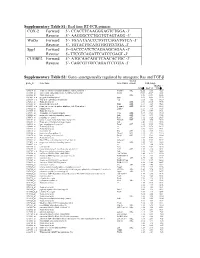
Supplementary Tables S1-S3
Supplementary Table S1: Real time RT-PCR primers COX-2 Forward 5’- CCACTTCAAGGGAGTCTGGA -3’ Reverse 5’- AAGGGCCCTGGTGTAGTAGG -3’ Wnt5a Forward 5’- TGAATAACCCTGTTCAGATGTCA -3’ Reverse 5’- TGTACTGCATGTGGTCCTGA -3’ Spp1 Forward 5'- GACCCATCTCAGAAGCAGAA -3' Reverse 5'- TTCGTCAGATTCATCCGAGT -3' CUGBP2 Forward 5’- ATGCAACAGCTCAACACTGC -3’ Reverse 5’- CAGCGTTGCCAGATTCTGTA -3’ Supplementary Table S2: Genes synergistically regulated by oncogenic Ras and TGF-β AU-rich probe_id Gene Name Gene Symbol element Fold change RasV12 + TGF-β RasV12 TGF-β 1368519_at serine (or cysteine) peptidase inhibitor, clade E, member 1 Serpine1 ARE 42.22 5.53 75.28 1373000_at sushi-repeat-containing protein, X-linked 2 (predicted) Srpx2 19.24 25.59 73.63 1383486_at Transcribed locus --- ARE 5.93 27.94 52.85 1367581_a_at secreted phosphoprotein 1 Spp1 2.46 19.28 49.76 1368359_a_at VGF nerve growth factor inducible Vgf 3.11 4.61 48.10 1392618_at Transcribed locus --- ARE 3.48 24.30 45.76 1398302_at prolactin-like protein F Prlpf ARE 1.39 3.29 45.23 1392264_s_at serine (or cysteine) peptidase inhibitor, clade E, member 1 Serpine1 ARE 24.92 3.67 40.09 1391022_at laminin, beta 3 Lamb3 2.13 3.31 38.15 1384605_at Transcribed locus --- 2.94 14.57 37.91 1367973_at chemokine (C-C motif) ligand 2 Ccl2 ARE 5.47 17.28 37.90 1369249_at progressive ankylosis homolog (mouse) Ank ARE 3.12 8.33 33.58 1398479_at ryanodine receptor 3 Ryr3 ARE 1.42 9.28 29.65 1371194_at tumor necrosis factor alpha induced protein 6 Tnfaip6 ARE 2.95 7.90 29.24 1386344_at Progressive ankylosis homolog (mouse) -

POGLUT1, the Putative Effector Gene Driven by Rs2293370 in Primary
www.nature.com/scientificreports OPEN POGLUT1, the putative efector gene driven by rs2293370 in primary biliary cholangitis susceptibility Received: 6 June 2018 Accepted: 13 November 2018 locus chromosome 3q13.33 Published: xx xx xxxx Yuki Hitomi 1, Kazuko Ueno2,3, Yosuke Kawai1, Nao Nishida4, Kaname Kojima2,3, Minae Kawashima5, Yoshihiro Aiba6, Hitomi Nakamura6, Hiroshi Kouno7, Hirotaka Kouno7, Hajime Ohta7, Kazuhiro Sugi7, Toshiki Nikami7, Tsutomu Yamashita7, Shinji Katsushima 7, Toshiki Komeda7, Keisuke Ario7, Atsushi Naganuma7, Masaaki Shimada7, Noboru Hirashima7, Kaname Yoshizawa7, Fujio Makita7, Kiyoshi Furuta7, Masahiro Kikuchi7, Noriaki Naeshiro7, Hironao Takahashi7, Yutaka Mano7, Haruhiro Yamashita7, Kouki Matsushita7, Seiji Tsunematsu7, Iwao Yabuuchi7, Hideo Nishimura7, Yusuke Shimada7, Kazuhiko Yamauchi7, Tatsuji Komatsu7, Rie Sugimoto7, Hironori Sakai7, Eiji Mita7, Masaharu Koda7, Yoko Nakamura7, Hiroshi Kamitsukasa7, Takeaki Sato7, Makoto Nakamuta7, Naohiko Masaki 7, Hajime Takikawa8, Atsushi Tanaka 8, Hiromasa Ohira9, Mikio Zeniya10, Masanori Abe11, Shuichi Kaneko12, Masao Honda12, Kuniaki Arai12, Teruko Arinaga-Hino13, Etsuko Hashimoto14, Makiko Taniai14, Takeji Umemura 15, Satoru Joshita 15, Kazuhiko Nakao16, Tatsuki Ichikawa16, Hidetaka Shibata16, Akinobu Takaki17, Satoshi Yamagiwa18, Masataka Seike19, Shotaro Sakisaka20, Yasuaki Takeyama 20, Masaru Harada21, Michio Senju21, Osamu Yokosuka22, Tatsuo Kanda 22, Yoshiyuki Ueno 23, Hirotoshi Ebinuma24, Takashi Himoto25, Kazumoto Murata4, Shinji Shimoda26, Shinya Nagaoka6, Seigo Abiru6, Atsumasa Komori6,27, Kiyoshi Migita6,27, Masahiro Ito6,27, Hiroshi Yatsuhashi6,27, Yoshihiko Maehara28, Shinji Uemoto29, Norihiro Kokudo30, Masao Nagasaki2,3,31, Katsushi Tokunaga1 & Minoru Nakamura6,7,27,32 Primary biliary cholangitis (PBC) is a chronic and cholestatic autoimmune liver disease caused by the destruction of intrahepatic small bile ducts. Our previous genome-wide association study (GWAS) identifed six susceptibility loci for PBC. -
Transcriptomic Analysis of the Oleaginous Microalga Neochloris Oleoabundans Reveals Metabolic Insights Into Triacylglyceride Accumulation
Transcriptomic analysis of the oleaginous microalga Neochloris oleoabundans reveals metabolic insights into triacylglyceride accumulation The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation Rismani-Yazdi, Hamid et al. “Transcriptomic Analysis of the Oleaginous Microalga Neochloris Oleoabundans Reveals Metabolic Insights into Triacylglyceride Accumulation.” Biotechnology for Biofuels 5.1 (2012): 74. Web. As Published http://dx.doi.org/10.1186/1754-6834-5-74 Publisher BioMed Central Ltd. Version Final published version Citable link http://hdl.handle.net/1721.1/76618 Terms of Use Creative Commons Attribution Detailed Terms http://creativecommons.org/licenses/by/2.0 Rismani-Yazdi et al. Biotechnology for Biofuels 2012, 5:74 http://www.biotechnologyforbiofuels.com/content/5/1/74 RESEARCH Open Access Transcriptomic analysis of the oleaginous microalga Neochloris oleoabundans reveals metabolic insights into triacylglyceride accumulation Hamid Rismani-Yazdi1,2, Berat Z Haznedaroglu1, Carol Hsin1 and Jordan Peccia1* Abstract Background: The lack of sequenced genomes for oleaginous microalgae limits our understanding of the mechanisms these organisms utilize to become enriched in triglycerides. Here we report the de novo transcriptome assembly and quantitative gene expression analysis of the oleaginous microalga Neochloris oleoabundans, with a focus on the complex interaction of pathways associated with the production of the triacylglycerol (TAG) biofuel precursor. Results: After growth under nitrogen replete and nitrogen limiting conditions, we quantified the cellular content of major biomolecules including total lipids, triacylglycerides, starch, protein, and chlorophyll. Transcribed genes were sequenced, the transcriptome was assembled de novo, and the expression of major functional categories, relevant pathways, and important genes was quantified through the mapping of reads to the transcriptome. -

New-Born DNA-Methylation, Childhood Lung Function, and The
1 http://hdl.handle.net/1765/118758 Chapter 3.1 New-born DNA-methylation, New-born DNA-methylation, childhood childhood lung function, and the lung function, and the risks of asthma risks of asthmaand COPD and across COPD the acrosslife course the life course Herman T. den Dekker*, Kimberley Burrows*, Janine F. Felix*, Lucas A. Salas, Ivana Nedeljković, Jin Yao, Sheryl L. Rifas-Shiman, Carlos Ruiz-Arenas, N. Amin, Mariona Bustamante, Dawn L. DeMeo, A. John Henderson, Caitlin G. Howe, Marie-France Hivert, M. Arfan Ikram, Johan C. de Jongste, Lies Lahousse, Pooja R. Mandaviya, Joyce B. van Meurs, Mariona Pinart, Gemma C. Sharp, Lisette Stolk, André G. Uitterlinden, Josep M. Anto, Augusto A. Litonjua, Carrie V. Breton, Guy G. Brusselle, Jordi Sunyer, George # Davey Smith, CarolineHerman L. T. Relton den Dekker*, , Kimberley Burrows*, Janine F. Felix*, # # Vincent W.V. LucasJaddoe A. ,Salas Liesbeth, Duijts , Jin Yao, Sheryl L. Rifas-Shiman, *fi rst authors contributedCarlos Ruiz-Arenas equally , N. Amin, Mariona Bustamante, Dawn L. DeMeo, Ivana Nedeljković #last authorsA. John contributed Henderson equally, Caitlin G. Howe, Marie-France Hivert, M. Arfan Ikram, Johan C. de Jongste, Lies Lahousse, Pooja R. Mandaviya, Joyce B. van Meurs, This chapter is published in European Respiratory Journal, February 2019. Mariona Pinart, Gemma C. Sharp, Lisette Stolk, André G. Uitterlinden, The supplemental material for this paper is available at: https://doi.org/10.1183/13993003.01795-2018Josep M. Anto, Augusto A. Litonjua, Carrie V. Breton, Guy G. Brusselle, Jordi Sunyer, George Davey Smith, Caroline L. Relton#, Vincent W.V. Jaddoe#, Liesbeth Duijts# *�irst authors contributed equally #last authors contributed equally This chapter is published in European Respiratory Journal, February 2019. -

Work Package 5 - a Genetically-Based Strategy to Identify New Targets in Ldl- C Metabolism
WORK PACKAGE 5 - A GENETICALLY-BASED STRATEGY TO IDENTIFY NEW TARGETS IN LDL- C METABOLISM Task 3 : Functional characterization of new FHBL/ADH genes Méryl Roudaut Amandine Caillaud Karim SI-TAYEB Unité Inserm UMR 1087-CNRS UMR 6291 Transatlantic Network of Excellence 2014-2019 WORK PACKAGE 5 - A GENETICALLY-BASED STRATEGY TO IDENTIFY NEW TARGETS IN LDL- C METABOLISM Task 3 : Functional characterization of new FHBL/ADH genes Nouvelle cible FHBL UCell hypochol propositus’ sister (44386) Microscopie optique Native Ucell in culture UCell en cours de reprogrammation hiPS hypochol propositus (43899) Characterisation : Immunofluorescence OCT4 Tra1-60 Dapi Merge Clone 5 Clone Clone 7 Clone hiPS hypochol propositus (43899) Characterisation : flow cytometry Tra1-60 SSEA3 SSEA4 Clone 5 Clone Clone 7 Clone Work in progress… Propositus’ sister: - Clone picking - early characterization Propositus : - further characterization - hepatocyte differentiation (ongoing) What we need now? Hints from the genetic team to focus our functionnal exploration Developing a 3D model of Human iPS Cell-derived Hepatocytes Méryl Roudaut Jun, 29th 2017 Summary First part : generality Summary First part : generality Second part : first differentiation step Summary First part : generality Second part : first differentiation step Third part : second differentiation step Summary First part : generality Second part : first differentiation step Third part : second differentiation step Conclusion 3D gels and microenvironnement 3D compared to 2D culture : hepatic differentiation -

Multi-Omics Study of Chronic Obstructive Pulmonary Disease and Related Disorders
S E R IV T E C D U R R O T S I S D B O D E C I T A N L O E R R H C D N F A O E Y S D A U E T S S I D S C I Y R M A O N - I O T M L L U U M P MULTI-OMICS STUDY OF CHRONIC OBSTRUCTIVE PULMONARY DISEASE AND RELATED DISORDERS I va n a P r o k I ć I va n a P r o k I ć Multi-omics Study of Chronic Obstructive Pulmonary Disease and Related Disorders Ivana Prokić Acknowledgements The work described in this thesis was conducted at the Genetic Epidemiology Unit, Department of Epidemiology, Erasmus Medical Center, Rotterdam, The Netherlands. The work presented in this thesis was supported by grant number 4.1.13.007 of Lung Foundation Netherlands (Longfonds), Biobanking and Biomolecular Resources arship. Research Infrastracture (BBMRI)-NL (184.021.007), Corbell, and by ERAWEB schol- The Erasmus Rucphen Family study as a part of EUROSPAN (European Special Populations Research Network) was supported by European Commission FP6 STRP grant number 018947 (LSHG-CT-2006-01947) and also received funding from the European Community’s Seventh Framework Programme (FP7/2007-2013)/ grant agreement HEALTH-F4-2007-201413 by the European Commission under the programme “Quality of Life and Management of the Living Resources” of 5th by Erasmus Medical Center and Erasmus University, Rotterdam, Netherlands Orga Framework Programme (no. QLG2-CT-2002-01254). The Rotterdam Study is funded - nization for the Health Research and Development (ZonMw), the Research Institute for Diseases in the Elderly (RIDE), the Ministry of Education, Culture and Science, the Ministry for Health, Welfare and Sports, the European Commission (DG XII), and ists, researchers, institutions and funders of all other studies from this thesis are the Municipality of Rotterdam. -

A De Novo Complex Chromosome Rearrangement Associated with Multisystematic Abnormalities, a Case Report
Tian et al. Molecular Cytogenetics (2017) 10:32 DOI 10.1186/s13039-017-0332-6 CASE REPORT Open Access A de novo complex chromosome rearrangement associated with multisystematic abnormalities, a case report Chan Tian1,2†, Dan Li1†, Ping Liu1,2, Liping Jiao1, Xuefeng Gao1 and Jie Qiao1,2* Abstract Background: Complex chromosomal rearrangements (CCRs) are constitutional structural rearrangements that involve three or more chromosomes or that have more than two breakpoints. Case presentation: Here, we describe a four-way CCR involving chromosomes 4, 5, 6 and 8. The patient had mild multisystematic abnormalities during his development, including defects in his eyes and teeth, exomphalos and asthenozoospermia. His wife had two spontaneous abortions during the first trimester. The translocations in 4q27, 5q22, 6q22.3, and 8p11.2 were diagnosed by conventional cytogenetic analysis and confirmed by fluorescence in situ hybridization(FISH). After analysis using a SNP array, we defined three microdeletions, including 0. 89 Mb on chromosome 4, 5.39 Mb on chromosome 5 and 0.43 Mb on chromosome 8. His mother had a chimera karyotype of 47, XXX[5]/45, X[4]/46, XX[91]; the other chromosomes were normal. After one cycle of in vitro fertility (IVF) treatment followed by preimplantation genetic diagnosis (PGD), they obtained two embryos, but neither was balanced. Conclusions: The patient’s phenotype resulted from the CCR and microdeletion of chromosomes 4, 5 and 8. The couple decided to use artificial insemination by donor (AID) technology. Keywords: CCR, SNP-array, FISH, Microdeletion, Rearrangement, AID Background Occasionally, cases have been detected because of psy- Complex chromosome rearrangements (CCRs) are chiatric trouble [3, 4]. -

Biological Pathways, Candidate Genes, and Molecular Markers Associated with Quality-Of-Life Domains: an Update
Qual Life Res DOI 10.1007/s11136-014-0656-1 REVIEW Biological pathways, candidate genes, and molecular markers associated with quality-of-life domains: an update Mirjam A. G. Sprangers • Melissa S. Y. Thong • Meike Bartels • Andrea Barsevick • Juan Ordon˜ana • Qiuling Shi • Xin Shelley Wang • Pa˚l Klepstad • Eddy A. Wierenga • Jasvinder A. Singh • Jeff A. Sloan Accepted: 19 February 2014 Ó Springer International Publishing Switzerland 2014 Abstract (depressed mood) and positive (well-being/happiness) Background There is compelling evidence of a genetic emotional functioning, social functioning, and overall foundation of patient-reported quality of life (QOL). Given QOL. the rapid development of substantial scientific advances in Methods We followed a purposeful search algorithm of this area of research, the current paper updates and extends existing literature to capture empirical papers investigating reviews published in 2010. the relationship between biological pathways and molecu- Objectives The objective was to provide an updated lar markers and the identified QOL domains. overview of the biological pathways, candidate genes, and Results Multiple major pathways are involved in each molecular markers involved in fatigue, pain, negative QOL domain. The inflammatory pathway has the strongest evidence as a controlling mechanism underlying fatigue. Inflammation and neurotransmission are key processes On behalf of the GeneQol Consortium. involved in pain perception, and the catechol-O-methyl- transferase (COMT) gene is associated with multiple sorts Electronic supplementary material The online version of this article (doi:10.1007/s11136-014-0656-1) contains supplementary of pain. The neurotransmitter and neuroplasticity theories material, which is available to authorized users. M. A.