Web Proxy Auto Discovery Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Know Before You Go
Know Before You Go NORWAY A Guide to Keep You Safe Abroad provided by: Pathways to Safety International Updated May 2019 KNOW BEFORE YOU GO: NORWAY 2 Let’s be perfectly clear, the number one way to prevent sexual assault is to not rape. While the responsibility of ending sexual gender based violence is on the perpetrators, this guide will offer general safety tips, country-specific information, and resources to help prevent and prepare travelers for the possibility of sexual assault abroad. GENERAL SAFETY TIPS: 1. Use the buddy system and travel with friends. 7 out of 10 2. Be aware of social and cultural norms. For example, looking at someone in rapes are the eyes when you speak to them is perfectly normal in the U.S., but in committed another country that could signify you’re interested in the person. by someone known to the 3. Recognize controlling behavior when entering a relationship. Most rape 1 survivors recall feeling “uncomfortable” about some of their partner’s behaviors victim such as degrading jokes/language or refusal to accept “no” as an answer, whether in a sexual context or otherwise.2 4. Avoid secluded places where you could be more vulnerable. Meet new people in public spaces and let a trusted friend know where you’ll be beforehand. Always have a backup plan in mind. 5. Trust your gut. Many victims have a “bad feeling” right before an assault takes place. It’s okay to leave a situation that is making you feel uncomfortable. Stay alert and aware in new social settings and places. -

Proxy Auto-Config Files
APPENDIX B Proxy Auto-Config Files Revised: July 15, 2010 Overview Proxy Auto-Configuration (PAC) is a method used by Web browsers to select a proxy for a given URL. The method for choosing a proxy is written as a JavaScript function contained in a PAC file. This file can be hosted locally or on a network. Browsers can be configured to use the file either manually or, in Microsoft Windows environments, automatically using Group Policy Objects. This appendix explains the basics of using PAC files. How PAC Files Work A PAC file is referenced each time a new URL is loaded. The host, for example cnn.com, the URL, for example cnn.com/images/logo.jpg, and other information such as the local machine IP address can be evaluated and rules based on this information used to determine whether to send the traffic via a proxy or direct to the Internet. The following example compares the URL requested by the user, with the URL ipcheckit.com/data/. If the URLs match, the PAC file will instruct the browser to send the request direct to the Internet. This can be used if you need to exception a section of a Web site from going via the Web Scanning Services; if the user had requested only ipcheckit.com, this rule would not apply: if (shExpMatch(url,"ipcheckit.com/data/*")) return "DIRECT"; In the next example the local IP address of the machine making a Web request is evaluated. If the IP address falls within the IP address range 10.10.1.* then the PAC file will send the request to proxy182.scansafe.net. -

The Potential Harms of the Tor Anonymity Network Cluster Disproportionately in Free Countries
The potential harms of the Tor anonymity network cluster disproportionately in free countries Eric Jardinea,1,2, Andrew M. Lindnerb,1, and Gareth Owensonc,1 aDepartment of Political Science, Virginia Tech, Blacksburg, VA 24061; bDepartment of Sociology, Skidmore College, Saratoga Springs, NY 12866; and cCyber Espion Ltd, Portsmouth PO2 0TP, United Kingdom Edited by Douglas S. Massey, Princeton University, Princeton, NJ, and approved October 23, 2020 (received for review June 10, 2020) The Tor anonymity network allows users to protect their privacy However, substantial evidence has shown that the preponder- and circumvent censorship restrictions but also shields those ance of Onion/Hidden Services traffic connects to illicit sites (7). distributing child abuse content, selling or buying illicit drugs, or With this important caveat in mind, our data also show that the sharing malware online. Using data collected from Tor entry distribution of potentially harmful and beneficial uses is uneven, nodes, we provide an estimation of the proportion of Tor network clustering predominantly in politically free regimes. In particular, users that likely employ the network in putatively good or bad the average rate of likely malicious use of Tor in our data for ways. Overall, on an average country/day, ∼6.7% of Tor network countries coded by Freedom House as “not free” is just 4.8%. In users connect to Onion/Hidden Services that are disproportion- countries coded as “free,” the percentage of users visiting Onion/ ately used for illicit purposes. We also show that the likely balance Hidden Services as a proportion of total daily Tor use is nearly of beneficial and malicious use of Tor is unevenly spread globally twice as much or ∼7.8%. -

Technical and Legal Overview of the Tor Anonymity Network
Emin Çalışkan, Tomáš Minárik, Anna-Maria Osula Technical and Legal Overview of the Tor Anonymity Network Tallinn 2015 This publication is a product of the NATO Cooperative Cyber Defence Centre of Excellence (the Centre). It does not necessarily reflect the policy or the opinion of the Centre or NATO. The Centre may not be held responsible for any loss or harm arising from the use of information contained in this publication and is not responsible for the content of the external sources, including external websites referenced in this publication. Digital or hard copies of this publication may be produced for internal use within NATO and for personal or educational use when for non- profit and non-commercial purpose, provided that copies bear a full citation. www.ccdcoe.org [email protected] 1 Technical and Legal Overview of the Tor Anonymity Network 1. Introduction .................................................................................................................................... 3 2. Tor and Internet Filtering Circumvention ....................................................................................... 4 2.1. Technical Methods .................................................................................................................. 4 2.1.1. Proxy ................................................................................................................................ 4 2.1.2. Tunnelling/Virtual Private Networks ............................................................................... 5 -

How Speedy Is SPDY?
How Speedy is SPDY? Xiao Sophia Wang, Aruna Balasubramanian, Arvind Krishnamurthy, and David Wetherall, University of Washington https://www.usenix.org/conference/nsdi14/technical-sessions/wang This paper is included in the Proceedings of the 11th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’14). April 2–4, 2014 • Seattle, WA, USA ISBN 978-1-931971-09-6 Open access to the Proceedings of the 11th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’14) is sponsored by USENIX How speedy is SPDY? Xiao Sophia Wang, Aruna Balasubramanian, Arvind Krishnamurthy, and David Wetherall University of Washington Abstract provides only a modest improvement [13, 19]. In our SPDY is increasingly being used as an enhancement own study [25] of page load time (PLT) for the top 200 to HTTP/1.1. To understand its impact on performance, Web pages from Alexa [1], we found either SPDY or we conduct a systematic study of Web page load time HTTP could provide better performance by a significant (PLT) under SPDY and compare it to HTTP. To identify margin, with SPDY performing only slightly better than the factors that affect PLT, we proceed from simple, syn- HTTP in the median case. thetic pages to complete page loads based on the top 200 As we have looked more deeply into the performance Alexa sites. We find that SPDY provides a significant im- of SPDY, we have come to appreciate why it is chal- provement over HTTP when we ignore dependencies in lenging to understand. Both SPDY and HTTP perfor- the page load process and the effects of browser compu- mance depend on many factors external to the protocols tation. -

Defending Against Malicious Cyber Activity Originating From
TLP:WHITE Product ID: A20-183A July 1, 2020 Defending Against Malicious Cyber Activity Originating from Tor This advisory—written by the Cybersecurity Security and Infrastructure Security Agency (CISA) with contributions from the Federal Bureau of Investigation (FBI)—highlights risks associated with Tor, along with technical details and recommendations for mitigation. Cyber threat actors can use Tor software and network infrastructure for anonymity and obfuscation purposes to clandestinely conduct malicious cyber operations.1,2,3 Tor (aka The Onion Router) is software that allows users to browse the web anonymously by encrypting and routing requests through multiple relay layers or nodes. This software is maintained by the Tor Project, a nonprofit organization that provides internet anonymity and anti-censorship tools. While Tor can be used to promote democracy and free, anonymous use of the internet, it also provides an avenue for malicious actors to conceal their activity because identity and point of origin cannot be determined for a Tor software user. Using the Onion Routing Protocol, Tor software obfuscates a user’s identity from anyone seeking to monitor online activity (e.g., nation states, surveillance organizations, information security tools). This is possible because the online activity of someone using Tor software appears to originate from the Internet Protocol (IP) address of a Tor exit node, as opposed to the IP address of the user’s computer. CISA and the FBI recommend that organizations assess their individual risk of compromise via Tor and take appropriate mitigations to block or closely monitor inbound and outbound traffic from known Tor nodes. 1 CISA Alert published April 2020: Continued Threat Actor Exploitation Post Pulse Secure VPN Patching. -

An Overview of Hypertext Transfer Protocol Service Security on Business Domain
2012 International Conference on Management and Education Innovation IPEDR vol.37 (2012) © (2012) IACSIT Press, Singapore An Overview of Hypertext Transfer Protocol service Security on Business Domain + Burra Venkata Durga Kumar Taylor’s Business School, Taylor’s University-Malaysia Abstract. Network protocols define the way data is transported between computers in a networked environment. Network protocols completely hide business functionality from higher level services and protocols, which can simply assume that, by providing the assigned name of another computer and company can transit a message or open a continuous communication stream without dealing with the intricacies of data transport. Populates Internet began to grow rapidly like expands with new tools, that is the new standard Hypertext Transfer Protocol and Hypertext Markup Language were introduced to the public. Hypertext Transfer Protocol to make accessing information through the Transfer Control Protocol or Internet Protocol is easier than ever. Hypertext Markup Language allows people to present information that is visually more interesting. Appearance of Hypertext Transfer Protocol and Hypertext Markup Language made people knows so popular, that is often considered synonymous with the Internet itself to the World Wide Web. The purpose of this paper is that knowing what kinds of security methods are appropriate for this Hypertext Transfer Protocol service and then explanations on World Wide Web and Hypertext Transfer Protocol works mechanisms. Proving the security methods of the answers obtained from what are assumed from the issues and included all models. Keywords: Network Protocols, Hypertext Transfer Protocol, Hypertext Markup Language, Transfer Control Protocol, Security, Business. 1. Introduction Nowadays, Internet service become very widely in business purpose and functionality, and for two popular internet services that common used by people, such as FTP (File Transfer Protocol) and HTTP (Hypertext Transfer Protocol). -

The Fundamentals of Http/2 the Fundamentals of Http/2
Ali Jawad THE FUNDAMENTALS OF HTTP/2 THE FUNDAMENTALS OF HTTP/2 Ali Jawad Bachelor’s Thesis June 2016 Information Technology Oulu University of Applied Sciences ABSTRACT Oulu University of Applied Sciences Degree Programme, Option of Internet Services Author: Ali Jawad Title of the bachelor’s thesis: Fundamentals Of HTTP/2 Supervisor: Teemu Korpela Term and year of completion: June 2016 Number of pages: 31 The purpose of this Bachelor’s thesis was to research and study the new ver- sion of HTTP ”HTTP2.0”, which is considered to be the future of the web. Http/2 is drawing a great attention from the web industry. Most of the Http/2 features are inherited from SPDY. This thesis shows how HTTP/2 enables a more efficient use of network re- sources and a reduced perception of latency by introducing a header field com- pression and allowing multiple concurrent exchanges on the same connection ”multiplexing” and more other features. Also, it discusses the security of Http/2 and the new risks and dangerous at- tacks that resurfaces with the arrival of this new protocol version. The simulation results show how HTTP/2 influences the page load time compar- ing to the other previous versions of HTTP. Keywords: HTTP1, HTTP/2, SPDY, SNI, DOS, CRIME, Downgrade-attack. 3 PREFACE This thesis was written for Oulu University of Applied Sciences and done during 1 February – 23 May 2016. The role of the instructor was guiding the thesis from the requirements and bases of writing a thesis document through meet- ings. The role of the supervisor was instructing the thesis plan and its require- ments which were done by the author. -

PDF Link Forces Download Instead of Open Document PDF Link Forces
PDF link forces download instead of open document • mozillaZine Forums http://forums.mozillazine.org/viewtopic.php?f=3&t=3010157&p=14636... Logout [ Andy Boze ] PDF link forces download instead of open document 0 new messages Post a reply User Control Panel View your posts First unread post • 13 posts • Page 1 of 1 Reply with quote ( ./posting.php?mode=quote&f=3&p=14631197 ) FAQ / Rules Report this post ( ./report.php?f=3&p=14631197 ) Members / Staff Posted Wed Jun 15, 2016 8:07 am A website I'm forced to use offers letters as pdf document. They might not want to pay for stamps and/or postage handling. When I click the link I do not get an open pdf document dialogue, but am forced to save the document Search locally. I then have to go to that location before I can open the document. When I complained about this procedure I got the answer that "this function differs per browser" and was invited to use a different browser... Boards (Advanced): I am not quite clear what has to happen behind the scenes to offer a pdf document from a database to the user, but forcing the user to another browser is a bit stiff in my opinion. Knowledge Base: Anyone care to comment? Mozilla/5.0 (Windows NT 10.0; WOW64; rv:43.0) Gecko/20100101 Firefox/43.0 SeaMonkey/2.40 Reply with quote ( ./posting.php?mode=quote&f=3&p=14631263 ) Report this post ( ./report.php?f=3&p=14631263 ) Posted Wed Jun 15, 2016 9:07 am Do other PDFs open in the browser for you? knowledge base If not, I like to install pdf.js ( https://github.com/mozilla/pdf.js/ ) in SeaMonkey to open PDFs (it's built into Firefox) - the XPI is here. -
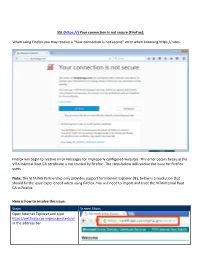
SSL ( Your Connection Is Not Secure (Firefox): When Using Firefox You May Receive a “Your Connection
SSL (https://) Your connection is not secure (FireFox): When using Firefox you may receive a “Your connection is not secure” error when browsing https:// sites. Firefox will begin to receive error messages for improperly configured websites. This error occurs because the VITA Internal Root CA certificate is not trusted by Firefox. The steps below will resolve the issue for FireFox users. Note: The VITA/NG Partnership only provides support for Internet Explorer (IE), below is a resolution that should fix the issue experienced when using Firefox. You will need to import and trust the VITAInternal Root CA in Firefox. Here is how to resolve this issue: Steps Screen Shots Open Internet Explorer and type https://certificate.cov.virginia.gov/certsrv/ in the address bar. Type in your COV credentials (username and password) if prompted. i.e. cov\abc12345 Select “Download a CA certificate, certificate or CRL” by using your mouse and left click on the link Select the “YES” button at the “Web Access Confirmation” dialog box by using your mouse and left click on the link, if prompted Select the link “Download CA certificate” Select the “Save” button when prompted In Firefox, select the “Menu” button in the upper right corner Using the mouse button left click on the “Options” icon Select the “Advanced” option in the left menu bar Using your mouse, left click the “Certificates” tab Select “View Certificates” 1. Click the Authorities Tab. 2. Click Import 1. Select the Downloads Folder if needed. 2. Click certnew.cer 3. Click Open 1. Select Trust this CA to identify websites 2. -

2. Avaya System Products with Seamonkey Installed: None 3
seamonkey security update (RHSA-2006-0676) Original Release Date: September 18, 2006 Last Revised: September 18, 2006 Number: ASA-2006-196 Risk Level: None Advisory Version: 1.0 Advisory Status: Final 1. Overview: The SeaMonkey open-source software suite from the Mozilla Foundation provides a user with a Web browser, Mail and Usenet client, an Internet Relay Chat (IRC) client and an HTML editing utility. A number of security issues were recently found in the SeaMonkey software suite. These vulnerabilities relate to how vulnerable versions of SeaMonkey handle regular expressions, Javascript, select types of RSA keys, and HTML frames. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CVE-2006- 4565, CVE-2006-4566, CVE-2006-4253), CVE-2006-4340, CVE-2006-4568, CVE- 2006-4570, and CVE-2006-4571 to these issues. No Avaya system products are vulnerable, as seamonkey is not installed by default. More information about these vulnerabilities can be found in the security advisory issued by RedHat Linux: · https://rhn.redhat.com/errata/RHSA-2006-0676.html 2. Avaya System Products with seamonkey installed: none 3. Avaya Software-Only Products Avaya software-only products operate on general-purpose operating systems. Occasionally vulnerabilities may be discovered in the underlying operating system or applications that come with the operating system. These vulnerabilities often do not impact the software-only product directly but may threaten the integrity of the underlying platform. In the case of this advisory Avaya software-only products are not affected by the vulnerability directly but the underlying Linux platform may be. -

An Analysis of the SPDY Protocol and the SPDY Proxy
April 2014 An Analysis of the SPDY Protocol and the SPDY Proxy Executive Summary Web-based commerce and content continues to grow, with mobile devices accounting for an increasing portion of network traffic. In a bid to enhance the speed of the web, browser and application developers are implementing new protocols to improve performance. At the same time, end-to-end encryption is increasing being used to improve user privacy and security. Google’s SPDY, described as “an experimental protocol for a faster web”, is one of the new protocols being introduced to reduce web page load times. Deployment is increasing, but as of today many web servers still do not support SPDY. To accelerate adoption of the protocol, SPDY proxy services have been deployed to offer some of the benefits of SPDY even when downloading content from web servers that have not yet implemented the SPDY protocol. However, by bundling multiple requests and encrypting all web traffic for a user inside a single connection, the SPDY proxy creates an opaque tunnel, hiding the true source of the content and breaking network management, content distribution, and many services offered by the network operators. This would be equally true for any proxy service that bundled all traffic from a given user inside an opaque tunnel, irrespective of the protocol used. The Problem Web content is becoming more complex both in size and in the number of separate connections/requests. Web pages are dominated by images and scripts, both of which are easily compressible, but are not compressed by current implementations. Mobile devices over wireless networks are constrained in terms of bandwidth and latency.