Informing the Fraud Triangle: Insights from Differential Association Theory
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UNIT 9 CRIMINOLOGY THEORIES Criminological Theories
UNIT 9 CRIMINOLOGY THEORIES Criminological Theories Structure 9.1 Introduction 9.2 Objectives 9.3 The Study of Criminology 9.4 What is Criminology? 9.5 Brief History of Criminology 9.6 Classical School of Criminology 9.6.1 Pre Classical School 9.6.2 Classical School of Criminology 9.6.3 Neo Classical School 9.7 Positive School of Criminology 9.8 Ecological School of Criminology 9.9 Theories Related to Physical Appearance 9.9.1 Phsiognomy and Phrenology 9.9.2 Criminal Anthropology: Lombroso to Goring 9.9.3 Body Type Theories: Sheldon to Cortes 9.10 Biological Factors and Criminal Behaviour 9.10.1 Chromosomes and Crime 9.10.2 Family Studies 9.10.3 Twin and Adoption Studies 9.10.4 Neurotransmitters 9.10.5 Hormones 9.10.6 The Autonomic Nervous System 9.11 Psychoanalytical Theories of Crime 9.11.1 Psychanalytic Explanations of Criminal Behaviour 9.12 Sociological Theories of Criminal Behaviour 9.12.1 Durkhiem, Anomie and Modernisation 9.12.2 Merton’s Strain Theory 9.12.3 Sutherland’s Differential Association Theory 9.13 Critical Criminology 9.13.1 Marxim and Marxist Criminology 9.14 Control Theories 9.14.1 Drift and Neutralisation 9.14.2 Hirschi’s Social Control 9.14.3 Containment Theory 9.14.4 Labeling Theory 9.15 Conflict Theories 9.15.1 Sellin’s Culture Conflict Theory 9.15.2 Vold’s Group Conflict Theory 9.15.3 Quinney’s Theory of the Social Reality of Crime 9.15.4 Turk’s Theory of Criminalisation 9.15.5 Chambliss and Seidman’s Analysis of the Criminal Justice System 5 Theories and Perspectives 9.16 Summary in Criminal Justice 9.17 Terminal Questions 9.18 Answers and Hints 9.19 References and Suggested Readings 9.1 INTRODUCTION Criminology is the scientific approach towards studying criminal behaviour. -

The Growth of Criminological Theories
THE GROWTH OF CRIMINOLOGICAL THEORIES Jonathon M. Heidt B.A., University of Montana, 2000 THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS In the School of Criminology OJonathon M. Heidt 2003 SIMON FRASER UNIVERSITY November 2003 All rights reserved. This work may not be reproduced in whole or in part, by photocopy or other means, without permission of the author. APPROVAL Name: Jonathon Heidt Degree: M.A. Title of Thesis: The Growth of Criminological Theories Examining Committee: Chair: ~ridnkurtch,P~JJ$ . D;. Robert ~ordoi,kh.~. Senior Supervisor Dr. Elizabeth Elliott, Ph.D. Member Sociology Department University at Albany - SUNY Date Approved: PARTIAL COPYRIGHT LICENCE I hereby grant to Simon Fraser University the right to lend my thesis, project or extended essay (the title of which is shown below) to users of the Simon Fraser University Library, and to make partial or single copies only for such users or in response to a request from the library of any other university, or other educational institution, on its own behalf or for one of its users. I further agree that permission for multiple copying of this work for scholarly purposes may be granted by me or the Dean of Graduate Studies. It is understood that copying or publication of this work for financial gain shall not be allowed without my written permission. Title of Thesis/Project/Extended Essay The Growth of Criminological Theories Author: Name ABSTRACT In the last 50 years, an extensive array of theories has appeared within the field of criminology, many generated by the discipline of sociology. -

Introduction to Criminology
PART 1 © Nevarpp/iStockphoto/Getty Images Introduction to Criminology CHAPTER 1 Crime and Criminology. 3 CHAPTER 2 The Incidence of Crime . 35 1 © Tithi Luadthong/Shutterstock CHAPTER 1 Crime and Criminology Crime and the fear of crime have permeated the fabric of American life. —Warren E. Burger, Chief Justice, U.S. Supreme Court1 Collective fear stimulates herd instinct, and tends to produce ferocity toward those who are not regarded as members of the herd. —Bertrand Russell2 OBJECTIVES • Define criminology, and understand how this field of study relates to other social science disciplines. Pg. 4 • Understand the meaning of scientific theory and its relationship to research and policy. Pg. 8 • Recognize how the media shape public perceptions of crime. Pg. 19 • Know the criteria for establishing causation, and identify the attributes of good research. Pg. 13 • Understand the politics of criminology and the importance of social context. Pg. 18 • Define criminal law, and understand the conflict and consensus perspectives on the law. Pg. 5 • Describe the various schools of criminological theory and the explanations that they provide. Pg. 9 of the public’s concern about the safety of their com- Introduction munities, crime is a perennial political issue that can- Crime is a social phenomenon that commands the didates for political office are compelled to address. attention and energy of the American public. When Dealing with crime commands a substantial por- crime statistics are announced or a particular crime tion of the country’s tax dollars. Criminal justice sys- goes viral, the public demands that “something be tem operations (police, courts, prisons) cost American done.” American citizens are concerned about their taxpayers over $270 billion annually. -

Sociological Theories of Deviance: Definitions & Considerations
Sociological Theories of Deviance: Definitions & Considerations NCSS Strands: Individuals, Groups, and Institutions Time, Continuity, and Change Grade level: 9-12 Class periods needed: 1.5- 50 minute periods Purpose, Background, and Context Sociologists seek to understand how and why deviance occurs within a society. They do this by developing theories that explain factors impacting deviance on a wide scale such as social frustrations, socialization, social learning, and the impact of labeling. Four main theories have developed in the last 50 years. Anomie: Deviance is caused by anomie, or the feeling that society’s goals or the means to achieve them are closed to the person Control: Deviance exists because of improper socialization, which results in a lack of self-control for the person Differential association: People learn deviance from associating with others who act in deviant ways Labeling: Deviant behavior depends on who is defining it, and the people in our society who define deviance are usually those in positions of power Students will participate in a “jigsaw” where they will become knowledgeable in one theory and then share their knowledge with the rest of the class. After all theories have been presented, the class will use the theories to explain an historic example of socially deviant behavior: Zoot Suit Riots. Objectives & Student Outcomes Students will: Be able to define the concepts of social norms and deviance 1 Brainstorm behaviors that fit along a continuum from informal to formal deviance Learn four sociological theories of deviance by reading, listening, constructing hypotheticals, and questioning classmates Apply theories of deviance to Zoot Suit Riots that occurred in the 1943 Examine the role of social norms for individuals, groups, and institutions and how they are reinforced to maintain a order within a society; examine disorder/deviance within a society (NCSS Standards, p. -

Social Structure, Culture, and Crime: Assessing Kornhauser’S Challenge to Criminology1
6 Social Structure, Culture, and Crime: Assessing Kornhauser’s Challenge to Criminology1 Ross L. Matsueda Ruth Kornhauser’s (1978) Social Sources of Delinquency has had a lasting infl uence on criminological theory and research. This infl uence consists of three contributions. First, Kornhauser (1978) developed a typology of criminological theories—using labels social disorganization, control, strain, and cultural devi- ance theories—that persists today. She distinguished perspectives by assump- tions about social order, motivation, determinism, and level of explanation, as well as by implications for causal models of delinquency. Second, Kornhauser addressed fundamental sociological concepts, including social structure, culture, and social situations, and provided a critical evaluation of their use within differ- ent theoretical perspectives. Third, she helped foster a resurgence of interest in social control and social disorganization theories of crime (e.g., Gottfredson and Hirschi 1990; Hirschi 1969; Sampson and Laub 1993; Bursik and Webb 1982; Kubrin and Weitzer 2003; Sampson and Groves 1989), both indirectly via the infl uence of an early version of the manuscript that would become Social Sources (see Chapter 3 in this volume) on Hirschi’s (1969) Causes of Delinquency , and directly via the infl uence of her book on the revitalization of social disorgani- zation theories of crime. Kornhauser’s infl uence on the writings of Hirschi, Bursik, and Sampson was particularly signifi cant and positive, as control and disorganization theo- ries came to dominate the discipline, stimulating a large body of research that increased our understanding of conventional institutional control of crime and delinquency through community organization, family life, and school effects. -
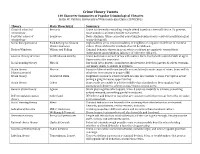
Crime Theory Tweets 140 Character Summaries of Popular Criminological Theories Justin W
Crime Theory Tweets 140 Character Summaries of Popular Criminological Theories Justin W. Patchin, University of Wisconsin-Eau Claire (CRMJ 301) Theory Main Theorist(s) Summary Classical school of Beccaria Crime is inherently rewarding. People offend based on a free will choice. To prevent, criminology must punish so potential benefit not worth it. Positivist school of Lombroso Born criminals. Crime caused by something beyond person’s control (usually biological criminology or psychological). Social disorganization Park & Burgess; Shaw & High mobility areas result in inability of neighbors to organize in defense of common McKay; Sampson values. Physical disorder symbols of social breakdown. Broken Windows Wilson and Kelling Criminal behavior thrives in areas where residents are apathetic toward their environment and neighbors (absence of collective efficacy). General theory of crime Gottfredson & Hirschi Crime & deviance a result of low self-control. One’s level of self-control stabile at age 8. Opportunity also important. Social bonding theory Hirschi Our bond (attachment, commitment, involvement, belief) to parents & others restrains our innate desire to engage in deviance. Strain theory Merton Pursuit of American Dream (wealth accumulation) is main cause of crime. Some will do (classic/anomie) whatever is necessary to acquire $$$. Strain theory Cloward & Ohlin Illegitimate means to achieve wealth are also inaccessible to some. Perception is that joining a gang increases opportunities. Strain theory Cohen Some youth are unable to achieve middle-class standards so they supplant legit pursuits with desire to achieve status/respect among peers. General strain theory Agnew Strain plus negative affect equals crime. 3 sources: inability to achieve; something valued removed; something painful introduced. -

Readings for Graduate Criminology Comprehensive Exam
READINGS FOR GRADUATE CRIMINOLOGY COMPREHENSIVE EXAM The following subdivisions are simply meant to be a heuristic device. They are not necessarily mutually exclusive or exhaustive. Note: Students are responsible for the last 5 years of articles in scholarly journals related to the area including Criminology, Criminology and Public Policy, and related papers published in the American Sociological Review, the American Journal of Sociology, and Social Forces and all other top journals. Social Disorganization and the Chicago School Bursik, R.J. 1988. "Social Disorganization theories of crime and delinquency: Problems and Prospects." Criminology 26:519-552. Morenoff, J., R. Sampson and S. Raudenbush. 2001. “Neighborhood inequality, collective efficacy, and the spatial dynamics of urban violence.” Criminology 39 (3): 517-559. Park, Robert E. 1915. “The City: Suggestions for the Investigation of Human Behavior in the City Environment. American Journal of Sociology 20: 577-612. Rose, D. and T. Clear. 1998. "Incarceration, social capital and crime: implications for social disorganization theory." Criminology 36:441-479. Sampson, R. 2012. The Great American City: Chicago and the Enduring Neighborhood Effect. University of Chicago Press. Sampson, R., S.W. Raudenbush and F. Earls. 1997."Neighborhoods and violent crime: A multilevel study of collective efficacy." Science 277: 918-924. Sampson, R., and Groves, W.B. (1989). “Community Structure and Crime: Testing Social- Disorganization Theory.” American Journal of Sociology 94 (4): 774-802. Shaw, Clifford R., and Henry D. McKay. 1942. Juvenile Delinquency in Urban Areas. Chicago: University of Chicago Press. Differential Association and Social Learning Theories Akers, R. L. 1998. Social Learning and Social Structure: A General Theory of Crime and Deviance. -

Labeling Theory
Sociology Virtual Learning High School/Lesson 33 Symbolic Interactionism & Deviance May 5, 2020 Sociology Lesson: May 6, 2020 Objective/Learning Target: The student will understand the symbolic interactionism theory of deviance. Warm Up: Review: Think back to when we learned about culture. Is culture inherited or learned? What do sociologists say? Warm Up: Is culture inherited or learned? What do sociologists say? Culture is learned. If culture is learned, is deviance learned? Warm Up: Is culture inherited or learned? What do sociologists say? Culture is learned. If culture is learned, is deviance learned? Sociologists believe that deviance is a learned behavior that is culturally transmitted. Lesson/Activity Introduction: Think back to the very beginning of the semester when we learned about the three main perspectives in Sociology. If you need to review, click here. According to Symbolic Interactionism , deviance is transmitted through socialization in the same way that deviant behavior is learned. For example, an early study revealed that delinquent behavior can be transmitted through play groups & gangs. Today, you will learn about two theories that explain how deviant behavior is learned: Differential Association & Labeling Theory. Both are based on Symbolic Interactionism. Lesson/Activity: How is deviance learned? Differential association theory states that individuals learn deviance in proportion to the number of deviant acts they are exposed to. According to this theory, the more people are exposed to people who break the law, the more apt they are to become criminals. There are three characteristics that affect differential association: 1.The ratio of deviant to nondeviant individuals. A person who knows mostly deviants is more likely to learn deviant behavior. -

Why Do Criminals Obey the Law? the Nfluei Nce of Legitimacy and Social Networks on Active Gun Offenders Andrew V
Journal of Criminal Law and Criminology Volume 102 | Issue 2 Article 3 Spring 2012 Why Do Criminals Obey the Law? The nflueI nce of Legitimacy and Social Networks on Active Gun Offenders Andrew V. Papachristos Tracy L. Meares Jeffrey Fagan Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons Recommended Citation Andrew V. Papachristos, Tracy L. Meares, and Jeffrey Fagan, Why Do Criminals Obey the Law? The Influence of Legitimacy and Social Networks on Active Gun Offenders, 102 J. Crim. L. & Criminology 397 (2013). https://scholarlycommons.law.northwestern.edu/jclc/vol102/iss2/3 This Criminology is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. 0091-4169/12/10202-0397 THE JOURNAL OF CRIMINAL LAW & CRIMINOLOGY Vol. 102, No. 2 Copyright © 2012 by Northwestern University School of Law Printed in U.S.A. CRIMINOLOGY WHY DO CRIMINALS OBEY THE LAW? THE INFLUENCE OF LEGITIMACY AND SOCIAL NETWORKS ON ACTIVE GUN OFFENDERS* ANDREW V. PAPACHRISTOS,** TRACEY L. MEARES*** & JEFFREY FAGAN**** Research on procedural justice and legitimacy suggests that compliance with the law is best secured not by mere threat of force, but by fostering beliefs in the fairness of the legal systems and in the legitimacy of legal actors. To date, however, this research has been based on general population surveys and more banal types of law-violating behavior (such as unpaid parking tickets, excessive noise, etc.). -

Pioneers in Criminology: Cesare Lombroso (1825-1909) Marvin E
Journal of Criminal Law and Criminology Volume 52 Article 1 Issue 4 November-December Winter 1961 Pioneers in Criminology: Cesare Lombroso (1825-1909) Marvin E. Wolfgang Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation Marvin E. Wolfgang, Pioneers in Criminology: Cesare Lombroso (1825-1909), 52 J. Crim. L. Criminology & Police Sci. 361 (1961) This Article is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. The Journal of CRIMINAL LAW, CRIMINOLOGY, AND POLICE SCIENCE Vol. 52 NOVEMBER-DECEMBER 1961 No. 4 PIONEERS IN CRIMINOLOGY: CESARE LOMBROSO (1835-1909) MARVIN E. WOLFGANG The author is Associate Professor of Sociology in the University of Pennsylvania, Philadelphia. He is the author of Patterns in Criminal Homicide, for which he received the August Vollmer Research Award last year, and is president of the Pennsylvania Prison Society. As a former Guggenheim Fellow in Italy, Dr. Wolfgang collected material for an historical analysis of crime and punishment in the Renaissance. Presently he is engaged in a basic research project entitled, "The Measurement of De- linquency." Some fifty years have passed since the death of Cesare Lombroso, and there are several important reasons why a reexamination and evaluation of Lombroso's life and contributions to criminology are now propitious. Lombroso's influence upon continental criminology, which still lays significant em- phasis upon biological influences, is marked. -

Predictability of Delinquency Through Psychosocial and Environmental Variables Across Three Generational Status Groups Margaret Frances Sabia Walden University
Walden University ScholarWorks Walden Dissertations and Doctoral Studies Walden Dissertations and Doctoral Studies Collection 2016 Predictability of Delinquency through Psychosocial and Environmental Variables across Three Generational Status Groups Margaret Frances Sabia Walden University Follow this and additional works at: https://scholarworks.waldenu.edu/dissertations Part of the Criminology Commons, Criminology and Criminal Justice Commons, and the Social and Cultural Anthropology Commons This Dissertation is brought to you for free and open access by the Walden Dissertations and Doctoral Studies Collection at ScholarWorks. It has been accepted for inclusion in Walden Dissertations and Doctoral Studies by an authorized administrator of ScholarWorks. For more information, please contact [email protected]. Walden University College of Social and Behavioral Sciences This is to certify that the doctoral dissertation by Margaret Sabia has been found to be complete and satisfactory in all respects, and that any and all revisions required by the review committee have been made. Review Committee Dr. Gregory Hickman, Committee Chairperson, Human Services Faculty Dr. William Barkley, Committee Member, Human Services Faculty Dr. Eric Youn, University Reviewer, Human Services Faculty Chief Academic Officer Eric Riedel, Ph.D. Walden University 2016 Abstract Predictability of Delinquency through Psychosocial and Environmental Variables across Three Generational Status Groups by Margaret Frances Sabia MSCJ, Everest University, 2012 BS, University of Connecticut, 2008 Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy Human Services Walden University May 2016 Abstract Issues such as the rapid growth of the immigrant youth population and delinquency among adolescents generate public safety concerns among the U.S. -

Differential Social Organization, Collective Action, and Crime
Crime Law Soc Change DOI 10.1007/s10611-006-9045-1 Differential social organization, collective action, and crime Ross L. Matsueda # Springer Science + Business Media B.V. 2006 Abstract This article elaborates and extends Sutherland’s[Principles of criminology (4th ed.), Lippincott, Philadelphia, Sutherland (1947)] concept of differential social organiza- tion, the sociological counterpart to his social psychological theory of differential association. Differential social organization contains a static structural component, which explains crime rates across groups, as well as a dynamic collective action component, which explains changes in crime rates over time. I argue that by drawing on George Herbert Mead’s[Mind, self, and society. University of Chicago Press, Chicago, Mead (1934)] theories of symbolic interaction and social control, we can conceptualize organization in favor of, and against, crime as collective behavior. We can then integrate theoretical mechanisms of models of collective behavior, including social network ties, collective action frames, and threshold models of collective action. I illustrate the integrated theory using examples of social movements against crime, neighborhood collective efficacy, and the code of the street. Differential social organization, collective action, and crime The theory of differential association, along with the concept of white collar crime, was probably Edwin Sutherland’s greatest legacy. It is well known that the theory explains individual criminality with a social psychological process of learning crime within interaction with social groups. Criminal behavior, according to Sutherland [71], is the result of learning an excess of definitions favorable to crime. This is the differential association process. Less well known is Sutherland’s attempt to explain aggregate crime rates across groups and societies.