Analysis-Report “Study the Great Nation” 08.-09.2019 Cure53, Dr.-Ing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administra
Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administrative Law of the Committee on the Judiciary Questions for Mr. Kyle Andeer, Vice President, Corporate Law, Apple, Inc. 1. Does Apple permit iPhone users to uninstall Safari? If yes, please describe the steps a user would need to take in order to do so. If no, please explain why not. Users cannot uninstall Safari, which is an essential part of iPhone functionality; however, users have many alternative third-party browsers they can download from the App Store. Users expect that their Apple devices will provide a great experience out of the box, so our products include certain functionality like a browser, email, phone and a music player as a baseline. Most pre-installed apps can be deleted by the user. A small number, including Safari, are “operating system apps”—integrated into the core operating system—that are part of the combined experience of iOS and iPhone. Removing or replacing any of these operating system apps would destroy or severely degrade the functionality of the device. The App Store provides Apple’s users with access to third party apps, including web browsers. Browsers such as Chrome, Firefox, Microsoft Edge and others are available for users to download. 2. Does Apple permit iPhone users to set a browser other than Safari as the default browser? If yes, please describe the steps a user would need to take in order to do so. If no, please explain why not. iPhone users cannot set another browser as the default browser. -

List of Brands
Global Consumer 2019 List of Brands Table of Contents 1. Digital music 2 2. Video-on-Demand 4 3. Video game stores 7 4. Digital video games shops 11 5. Video game streaming services 13 6. Book stores 15 7. eBook shops 19 8. Daily newspapers 22 9. Online newspapers 26 10. Magazines & weekly newspapers 30 11. Online magazines 34 12. Smartphones 38 13. Mobile carriers 39 14. Internet providers 42 15. Cable & satellite TV provider 46 16. Refrigerators 49 17. Washing machines 51 18. TVs 53 19. Speakers 55 20. Headphones 57 21. Laptops 59 22. Tablets 61 23. Desktop PC 63 24. Smart home 65 25. Smart speaker 67 26. Wearables 68 27. Fitness and health apps 70 28. Messenger services 73 29. Social networks 75 30. eCommerce 77 31. Search Engines 81 32. Online hotels & accommodation 82 33. Online flight portals 85 34. Airlines 88 35. Online package holiday portals 91 36. Online car rental provider 94 37. Online car sharing 96 38. Online ride sharing 98 39. Grocery stores 100 40. Banks 104 41. Online payment 108 42. Mobile payment 111 43. Liability insurance 114 44. Online dating services 117 45. Online event ticket provider 119 46. Food & restaurant delivery 122 47. Grocery delivery 125 48. Car Makes 129 Statista GmbH Johannes-Brahms-Platz 1 20355 Hamburg Tel. +49 40 2848 41 0 Fax +49 40 2848 41 999 [email protected] www.statista.com Steuernummer: 48/760/00518 Amtsgericht Köln: HRB 87129 Geschäftsführung: Dr. Friedrich Schwandt, Tim Kröger Commerzbank AG IBAN: DE60 2004 0000 0631 5915 00 BIC: COBADEFFXXX Umsatzsteuer-ID: DE 258551386 1. -

Releasenote 2Q 2020 Final
Q61 (LM-Q630N), LM-G900N(Velvet) LM-Q510N (Q51), LM-V600N (V60 ThinQ), LM-Y120K (Folder 2), LM-Y120L (Folder 2), LM-Y120S (Folder 2) Galaxy A Quantum (SM-A716N, SM-A716S), SM-P610 (Galaxy Tab S6 Lite ( SAMSUNG (2) Wi-Fi)), SM-P615 (Galaxy Tab S6 Lite (LTE)) SM-A315F (Galaxy A31), SM-A315F_DS (Galaxy A31), SM-A315N (Galaxy A3 SAMSUNG (6) 1), SM-A516F (Galaxy A51), SM-A516F_DS (Galaxy A51), SM-A516N (Galaxy A51) SM-A260F (Galaxy A2 Core), SM-A260F_DS (Galaxy A2 Core), SMA260G (Ga laxy A2 Core), SM-A260G_DS (Galaxy A2 Core), SMA5070 (Galaxy A50s), S M-A507F (Galaxy A50s), SM-A507F_DS (Galaxy A50s), SM-A507FN (Galaxy A50s), SM-A507FN_DS (Galaxy A50s), SM-C9008 (Galaxy C9 Pro), SM-C900 SAMSUNG (25) F (Galaxy C9 Pro), SM-C900Y (Galaxy C9 Pro), SM-J400F (Galaxy J4), SM-J40 0F_DS (Galaxy J4), SM-J400G (Galaxy J4), SM-J400G_DS (Galaxy J4), SMJ40 0M (Galaxy J4), SM-J810F (Galaxy J8), SM-J810F_DS (Galaxy J8), SM-J810G (Galaxy J8), SM-J810G_DS (Galaxy On8), SMJ810GF (Galaxy J8), SM-J810M (Galaxy J8), SM-J810Y (Galaxy J8), SM-J810Y_DS (Galaxy On8) COR-AL00 (Honor Play), COR-AL10 (Honor Play), COR-L09 (Honor Play), CO HUAWEI (4) R-L29 (Honor Play) A4000 (One Plus 4), A5000 (One Plus 5), A5010 (One Plus 5T), A6010 (One Oneplus (5) Plus 6T), A6013 (One Plus 6T) BBB100-1 (Keyone), BBB100-2 (Keyone), BBB100-3 (Keyone), BBB100-4 (K BlackBerry (8) eyone), STV100-1 (Priv), STV100-2 (Priv), STV100-3 (Priv), STV100-4 (Priv) HTC (1) OPKV100 (One M8s) HRY-AL00a (Honor 10 Lite), HRY-LX1 (Honor 10 Lite), HRYLX1MEB (Honor 1 HUAWEI (8) 0 Lite), HRY-LX2 (Honor 10 -

How Companies Perpetuate and Resist Chinese Government Censorship ∗
How Companies Perpetuate and Resist Chinese Government Censorship ∗ Jennifer Pany Tongtong Zhangz February 11, 2020 Please click here for the most up-to-date version of this paper Abstract Given China’s growing market power, can firms operating in China resist govern- ment pressures to censor political dissent? Firms were once regarded as a potential catalyst for authoritarian breakdown, but recent research suggests they can bolster authoritarian rule. We theorize that the material incentives of firms can lead them to perpetuate government censorship but also to resist pressures to penalize dissent. We test this theory with two large-scale experiments that measure how diverse firms operating in China penalize job candidates for dissent. We find that despite the lure of the Chinese market, firms operating in China do not converge in their behavior. Although candidates who express dissent are less likely to receive a callback than those who express political loyalty, the largest proportion of employers do not penal- ize dissent, and some employers favor candidates who express dissent because they believe dissenters have valuable characteristics and knowledge. Keywords: censorship, dissent, firms, experiment, China Word Count: 9,078 ∗Our thanks to Haotian Bu, Luchi He, Shixian Li, Lin Liu, Yongbo Liu, Beibei Tan, Xuewei Tian, Tianyi Wang, Yue Wang, Qiushi Yin, Ni Zeng, Kan Zhang, and many others for superb research assistance; David Broockman, Daniel Butler, Alex Coppock, Charles Crabtree, Ana De La O, Donald Green, Jens Hainmeuller, Gregory Huber, Shanto Iyengar, Holger Kern, Gary King, Peter Lorentzen, Eddy Malesky, Neil Malhotra, Kristin Michelitch, Brendan Nyhan, Jean Oi, Elizabeth Perry, Jonathan Rodden, Weiyi Shi, David Szakonyi, Georg Vanberg, Andrew Walder, Chenggang Xu, Yiqing Xu, Boliang Zhu for many helpful comments and suggestions; and to the Freeman Spogli Institute China Fund and Asia-Pacific Scholars Fund for research support. -

VOLUME 20 • ISSUE 11 • JUNE 24, 2020 the CCP
VOLUME 20 • ISSUE 11 • JUNE 24, 2020 IN THIS ISSUE: The CCP Politburo Holds Its First Collective Study Session for 2020 By John Dotson………………………………………………………pp. 1-5 Fighting the Battle for the Pandemic Narrative: The PRC White Paper on Its COVID-19 Response By April Herlevi………………………………………………………..pp. 6-11 The COVID-19 Pandemic Boosts Sino-Russian Cooperation By Richard Weitz……………………………………………………….pp. 12-17 Chinese Views of the United States Amid Rising Sino-American Clashes By Nikita Savkov…………………………………………………….....pp. 18-22 The India-U.S. Defense Relationship Grows Amid Rising Tensions with China By Rup Narayan Das……..…………………………………………...pp. 23-27 The CCP Politburo Holds Its First Collective Study Session for 2020 By John Dotson Introduction On May 29, the Chinese Communist Party (CCP) Politburo held its first “collective study” (集体学习, jiti xuexi) session for the year 2020. It is unusual that the first of these events took place only near the mid-point of the year: in recent years, these Politburo political study sessions have been convened either monthly or on alternate months, with an average occurrence of 8 times per year. [1] Throughout the early months of 2020, the political leadership of the People’s Republic of China (PRC) has been focused upon the COVID-19 crisis and its attendant problems—which have included a worsening of the country’s economic problems, and the delay of the “Two Sessions” (the annual convening of the National People’s Congress and the Chinese People’s Political Consultative Conference) from the usual timeframe of early March to late May (China Brief, 1 ChinaBrief • Volume 20 • Issue 11 • June 24, 2020 May 26; China Brief, May 29). -

Distance Learning Solutions Recommended by UNESCO
Distance Learning Solutions recommended by UNESCO Distance Learning Solutions recommended by UNESCO Distance Learning Solutions recommended by UNESCO https://en.unesco.org/themes/education-emergencies/coronavirus-school-closures/solutions Digital learning management systems Blackboard …………………………………………………………………………..….3 CenturyTech ………………...……………………………………………..………..….4 ClassDojo ……………………………………...………………………….………...…. 5 Edmodo ……………………………………………………………………..……….….6 Edraak ………………………………………………………………………….…….….7 EkStep …………………………………………………………………………..……….8 Google Classroom ………………………………………………………..…………….9 Moodle ………………………………………………………………………….……….11 Nafham ………………………………………………………………………….……….12 Schoology …………………………………………………………………….………….13 Seesaw ……………………………………………………………………………..…….14 Skooler ………………………………………………………………………..………….15 Study Sapuri …………………………………………………………………………….16 Systems purpose-built for mobile phones Cell-Ed …………………………………………………...…………………………….17 Eneza Education …………………………………………...………………………….19 Funzi ……………………………………………………………..…………………….20 KaiOS ………………………………………………………………….……………….21 Ubongo ……………………………………………………………………..………….22 Ustad Mobile …………………………………………………………………………..2 3 Systems with strong offline functionality Can’t wait to Learn ……………………...…………………………………………….24 Kolibri ………………………………………………………………………………….25 Rumie ……………………………………….………………………………………….26 Ustad Mobile ………………………………….……………………………………….26 Massive Open Online Course (MOOC) Platforms Alison ……………………………………………………………………….………….27 Coursera ……………………………………………………………………………….28 EdX ……………………………………………………………………………………..3 -
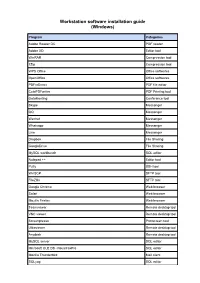
Workstation Software Installation Guide (Windows)
Workstation software installation guide (Windows) Program Categories Adobe Reader DC PDF reader Adobe XD Editor tool WinRAR Compression tool 7Zip Compression tool WPS Office Office softwares OpenOffice Office softwares PDFreDirect PDF file editor CutePDFwriter PDF Printing tool GotoMeeting Conference tool Skype Messenger QQ Messenger Wechat Messenger Whatsapp Messenger Line Messenger Dropbox File Sharing GoogleDrive File Sharing MySQL workbench SQL editor Notepad ++ Editor tool Putty SSH tool WinSCP SFTP tool FileZilla SFTP tool Google Chrome Web browser Safari Web browser Mozilla Firefox Web browser Teamviewer Remote desktop tool VNC viewer Remote desktop tool Screenpresso Printscreen tool Ultraviewer Remote desktop tool Anydesk Remote desktop tool MySQL server SQL editor Microsoft OLE DB -VisualFoxPro SQL editor Mozilla Thunderbird Mail client SQLyog SQL editor Visual Studio Express 201x (Community edition) Editor tool Genymotion Android Emulator (Personal edition) Android emulator Sonarqube (Free & Open Source; Community edition) Coding tool Appium (Free & Open Source) Automation tool Jenkins (Free & Open Source - Rupyn-tester installed in own office notebook) Automation tool Android Studio (Free & Open Source) Application tool Ingress In House tools Timetec Web Installer In House tools Biztrak In House tools Netbeans Coding tool Visual Studio Code Coding tool Sublime Coding tool Eclipse Coding tool PDFSam PDF file editor DingTalk Messenger Microsoft Team Conference tool Zoom Meeting Conference tool Workstation software installation -

Bridging the Domain Gap: Improve Informal Language Translation Via Counterfactual Domain Adaptation
The Thirty-Fifth AAAI Conference on Artificial Intelligence (AAAI-21) Bridging the Domain Gap: Improve Informal Language Translation via Counterfactual Domain Adaptation Ke Wang,1,2 Guandan Chen,3 Zhongqiang Huang,3 Xiaojun Wan,1,2 Fei Huang3 1Wangxuan Institute of Computer Technology, Peking University 2The MOE Key Laboratory of Computational Linguistics, Peking University 3DAMO Academy, Alibaba Group fwangke17, [email protected] fguandan.cgd, z.huang, [email protected] Abstract A natural solution to this problem is domain adaptation, Despite the near-human performances already achieved on which aims to adapt NMT models trained on one or more formal texts such as news articles, neural machine transla- source domains (formal texts in our case) to the target do- tion still has difficulty in dealing with ”user-generated” texts main (informal texts in our case). Domain adaptation meth- that have diverse linguistic phenomena but lack large-scale ods can be roughly categorized into model-based and data- high-quality parallel corpora. To address this problem, we based ones (Chu and Wang 2018). The model-based meth- propose a counterfactual domain adaptation method to better ods make explicit changes to NMT model such as designing leverage both large-scale source-domain data (formal texts) new training objectives (Luong, Pham, and Manning 2015; and small-scale target-domain data (informal texts). Specifi- Chu, Dabre, and Kurohashi 2017), modifying the model ar- cally, by considering effective counterfactual conditions (the chitecture (Kobus, Crego, and Senellart 2017; Johnson et al. concatenations of source-domain texts and the target-domain 2017; Dou et al. -

1. Information Systems
International Journal of Information Systems Management Research and Development (IJISMRD) ISSN(P): 2250-236X; ISSN(E): 2319-4480 Vol. 5, Issue 1, Jun 2015, 1-10 © TJPRC Pvt. Ltd. ALIBABA GROUP: FROM ONLINE TO O2O SUNGYOUNG HUH 1, SAEBOM LEE 2, SAERIM HONG 3, YURIM LEE 4, BOKYUNG KIM 5, DAYOUNGKO 6, HAEYOON KIM 7, BORAM HAN 8 & SEUGHO CHOI 9 1,2,3,4,5,6,7 Undergraduate Students, Department of Management, Ewha School of Business, EwhaWomans University, Seoul, South Korea 8Graduate Students, Department of Management, Ewha School of Business, EwhaWomans University, Seoul, South Korea 9Assistant Professor, Department of Management, Ewha School of Business, EwhaWomans University, Seoul, South Korea ABSTRACT "One day I was in San Francisco in a coffee shop, and I was thinking Alibaba is a good name. And then a waitress came, and I said do you know about Alibaba? And she said yes. I said what do you know about Alibaba, and she said ‘Alibaba and 40 thieves'. And I said yes, this is the name! Then I went onto the street and found 30 people and asked them, ‘Do you know Alibaba?’ People from India, people from Germany, people from Tokyo and China… They all knew about Alibaba. Alibaba — open sesame. Alibaba is a kind, smart businessperson, and he helped the village. So…easy to spell, and globally known. Alibaba opens sesame for small-to medium-sized companies. We also registered the name Alimama, in case someone wants to marry us” Jack Ma has built Alibaba over a decade from a simple B2B Web site for manufacturers to a global online empire. -

Ryan Green Sr
Commerce Obsessed: How to Map a B2C Customer Journey #MLEU Ryan Green Sr. Manager, Commerce Product Marketing @Greener250 #MLEU #CommerceObsessed [email protected] #MLEU You’ve got to start with the customer CUSTOMER TECHNOLOGY experience and work back toward Flash the technology – not the other way around. Steve Jobs Boxed Software #MLEU My Commerce Experiences & Trends #MLEU Sometimes We Make it Too Easy… #MLEU B2C to B2B…pop up? #MLEU Uber Humanizes My Experience John 4.93 Red Nissan | AET112 Change color Your driver is deaf or hard of hearing. To help you spot your ride, you can change the icon glowing in your driver’s windshield #MLEU Dating Push Notification HINGE HINGE 5m ago 5m ago 19 people from Binghamton joined Hinge in NYC. BINGHAMTON You’re19 75% people more likely from to connect Binghamton with joined Hinge in NYC. hometowners!You’re 75% more likely to connect with HOME Slide for more hometowners! Slide for more NEW YORK CITY LIVE #MLEU Banking & Shopping #MLEU Marketplaces… #MLEU Competition from all angles [Patent Pending] Fulfillment Tmall / Taobao / AliExpress / Online Multi-level for UAVs Rail-borne Lazada / Alibaba.com / Amazon.com Marketplace 1688.com / Juhuasuan / Daraz Physical Whole Foods / Amazon Go / Intime / Suning* / Hema Retail Amazonbooks Ant Financial* / Paytm* Payments Amazon Payments Airborne Underground Youku / UCWeb / Alisports Amazon Video / Amazon Music Digital /Alibaba Music / Damai / Alibaba / Twitch / Amazon Game Studio Entertainment Pictures* / Audible Ele.Me (Local) / Koubei (Local) / Alimama -

A Blueprint for Remote Working: Lessons from China
McKinsey Digital A blueprint for remote working: Lessons from China As home to some of the world’s largest firms, China offers lessons for those that are just now starting to embrace the shift to remote working. by Raphael Bick, Michael Chang, Kevin Wei Wang, Tianwen Yu March 2020 From Alibaba to Ping An and Google to Ford, 1. Designing an effective structure companies around the globe are telling staff to work Teams or whole business units working remotely from home1 in a bid to stem the spread of COVID-19. can quickly result in confusion and a lack of clarity. Being isolated leads to uncertainty about who to Such remote working at scale is unprecedented and talk to on specific issues and how and when to will leave a lasting impression on the way people approach them, leading to hold-ups and delays. live and work for many years to come. China, which felt the first impact of the pandemic2, was an early That’s why establishing a structure and architecture mover in this space. As home to some of the world’s for decision making and effective communication largest firms, it offers lessons for those that are just is key. Here, smaller cross-functional teams can be now starting to embrace the shift. helpful, each with a clear mission and reporting line, where directions and tasks are easy to implement. Working from home sky-rocketed in China3 in This also simplifies onboarding new hires, who can the wake of the COVID-19 crisis as companies integrate faster in a tight-knit group, at a time when told their employees to stay home. -

December Quarter 2016 Results
December Quarter 2016 Results January 24, 2017 Disclaimer This presentation contains forward-looking statements. These statements are made under the “safe harbor” provisions of the U.S. Private Securities Litigation Reform Act of 1995. These forward-looking statements can be identified by terminology such as “will,” “expects,” “anticipates,” “future,” “intends,” “plans,” “believes,” “estimates,” “potential,” “continue,” “ongoing,” “targets,” “guidance” and similar statements. Among other things, statements that are not historical facts, including statements about Alibaba’s strategies and business plans, Alibaba’s beliefs and expectations regarding the growth of its businesses and its revenue for the full fiscal year, the business outlook and quotations from management in this presentation, as well as Alibaba’s strategic and operational plans, are or contain forward-looking statements. Alibaba may also make forward-looking statements in its periodic reports to the U.S. Securities and Exchange Commission (the “SEC”), in press releases and other written materials and in oral statements made by its officers, directors or employees to third parties. Forward-looking statements involve inherent risks and uncertainties. A number of factors could cause actual results to differ materially from those contained in any forward-looking statement, including but not limited to the following: Alibaba’s goals and strategies; Alibaba’s future business development; Alibaba’s ability to maintain the trusted status of its ecosystem, reputation and brand; risks