Military Guide to Terrorism in the Twenty-First Century
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
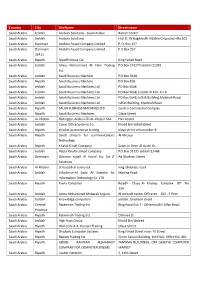
Country City Sitename Street Name Saudi Arabia Jeddah Arabian Solutions - Saudi Arabia Barom Center Saudi Arabia Jeddah Arabian Solutions Hial St
Country City SiteName Street name Saudi Arabia Jeddah Arabian Solutions - Saudi Arabia Barom Center Saudi Arabia Jeddah Arabian Solutions Hial St. W.Bogddadih AlZabin Cmpound villa 102 Saudi Arabia Damman Abdulla Fouad Company Limited P. O. Box 257 Saudi Arabia Dammam Abdulla Fouad Company Limited P O Box 257 31411 Saudi Arabia Riyadh Riyadh House Est. King Fahad Road Saudi Arabia Jeddah Idress Mohammed Ali Fatni Trading P.O.Box 132270 Jeddah 21382 Est. Saudi Arabia Jeddah Saudi Business Machine P.O.Box 5648 Saudi Arabia Riyadh Saudi Business Machine P.O Box 818 Saudi Arabia Jeddah Saudi Business Machines Ltd PO Box 5648 Saudi Arabia Jeddah Saudi Business Machines Ltd. PO Box 5648, Jeddah 21432, K S A Saudi Arabia Jeddah Saudi Business Machines Ltd. PO Box 5648, Juffali Building,Madinah Road Saudi Arabia Jeddah Saudi Business Machines Ltd. Juffali Building, Madinah Road Saudi Arabia Riyadh SAUDI BUSINESS MACHINES LTD. Centria Commercial Complex Saudi Arabia Riyadh Saudi Business Machines Olaya Street Saudi Arabia Al-Khobar Redington Arabia LTD AL-Khobar KSA Hail Center Saudi Arabia Jeddah Canar Office Systems Co Khalid Bin Walid Street Saudi Arabia Riyadh shrakat partnerships trading olaya street villa number 8 Saudi Arabia Riyadh Saudi Unicom for communications Al-Mrouje technology Saudi Arabia Riyadh Khalid Al Safi Company Salah Al-Deen Al-Ayubi St., Saudi Arabia Jeddah Azizia Panda United Company P.O.Box 33333 Jeddah 21448 Saudi Arabia Dammam Othman Yousif Al Yousif Est. for IT Ad Dhahran Street Solutions Saudi Arabia Al Khober al hasoob al asiavy est. king abdulaziz road Saudi Arabia Jeddah EchoServe-Al Sada Al Shamila for Madina Road Information Technology Co. -

Kingdom of Saudi Arabia
White Paper Makkah | Retail 2018 Kingdom of Saudi Arabia Evolving Dynamics Makkah Retail Overview Summary The holy city of Makkah is currently going through a major strategic development phase to improve connectivity, Ian Albert increase capacity, and enhance the experience of Umrah Regional Director and Hajj pilgrims throughout their stay. Middle East & North Africa This is reflected in the execution of several strategic infrastructure and transportation projects, which have a clear focus on increasing pilgrim capacity and improving connectivity with key projects, including the Holy Haram Expansion, Haramain High- Speed Railway, and King Abdulaziz International Airport. These projects, alongside Vision 2030, are shaping the city’s real estate landscape and stimulating the development of several large real estate projects in their surrounding areas, including King Abdulaziz Road (KAAR), Jabal Omar, Thakher City and Ru’a Al Haram. These projects are creating opportunities for the development of various retail Imad Damrah formats that target pilgrims. Managing Director | Saudi Arabia Makkah has the lowest retail density relative to other primary cities; Riyadh, Jeddah, Dammam Al Khobar and Madinah. With a retail density of c.140 sqm / 1,000 population this is 32% below Madinah which shares the same demographics profile. Upon completion of major transport infrastructure and real estate projects the number of pilgrims is projected to grow by almost 223% from 12.1 million in 2017 up to 39.1 million in 2030 in line with Vision 2030 targets. Importantly the majority of international Pilgrims originate from countries with low purchasing power. Approximately 59% of Hajj and Umrah pilgrims come from countries with GDP/capita below USD 5,000 (equivalent to SAR 18,750). -

The Destruction of Religious and Cultural Sites I. Introduction The
Mapping the Saudi State, Chapter 7: The Destruction of Religious and Cultural Sites I. Introduction The Ministry for Islamic Affairs, Endowments, Da’wah, and Guidance, commonly abbreviated to the Ministry of Islamic Affairs (MOIA), supervises and regulates religious activity in Saudi Arabia. Whereas the Commission for the Promotion of Virtue and the Prevention of Vice (CPVPV) directly enforces religious law, as seen in Mapping the Saudi State, Chapter 1,1 the MOIA is responsible for the administration of broader religious services. According to the MOIA, its primary duties include overseeing the coordination of Islamic societies and organizations, the appointment of clergy, and the maintenance and construction of mosques.2 Yet, despite its official mission to “preserve Islamic values” and protect mosques “in a manner that fits their sacred status,”3 the MOIA is complicit in a longstanding government campaign against the peninsula’s traditional heritage – Islamic or otherwise. Since 1925, the Al Saud family has overseen the destruction of tombs, mosques, and historical artifacts in Jeddah, Medina, Mecca, al-Khobar, Awamiyah, and Jabal al-Uhud. According to the Islamic Heritage Research Foundation, between just 1985 and 2014 – through the MOIA’s founding in 1993 –the government demolished 98% of the religious and historical sites located in Saudi Arabia.4 The MOIA’s seemingly contradictory role in the destruction of Islamic holy places, commentators suggest, is actually the byproduct of an equally incongruous alliance between the forces of Wahhabism and commercialism.5 Compelled to acknowledge larger demographic and economic trends in Saudi Arabia – rapid population growth, increased urbanization, and declining oil revenues chief among them6 – the government has increasingly worked to satisfy both the Wahhabi religious establishment and the kingdom’s financial elite. -

In Defense of Cyberterrorism: an Argument for Anticipating Cyber-Attacks
IN DEFENSE OF CYBERTERRORISM: AN ARGUMENT FOR ANTICIPATING CYBER-ATTACKS Susan W. Brenner Marc D. Goodman The September 11, 2001, terrorist attacks on the United States brought the notion of terrorism as a clear and present danger into the consciousness of the American people. In order to predict what might follow these shocking attacks, it is necessary to examine the ideologies and motives of their perpetrators, and the methodologies that terrorists utilize. The focus of this article is on how Al-Qa'ida and other Islamic fundamentalist groups can use cyberspace and technology to continue to wage war againstthe United States, its allies and its foreign interests. Contending that cyberspace will become an increasingly essential terrorist tool, the author examines four key issues surrounding cyberterrorism. The first is a survey of conventional methods of "physical" terrorism, and their inherent shortcomings. Next, a discussion of cyberspace reveals its potential advantages as a secure, borderless, anonymous, and structured delivery method for terrorism. Third, the author offers several cyberterrorism scenarios. Relating several examples of both actual and potential syntactic and semantic attacks, instigated individually or in combination, the author conveys their damagingpolitical and economic impact. Finally, the author addresses the inevitable inquiry into why cyberspace has not been used to its full potential by would-be terrorists. Separately considering foreign and domestic terrorists, it becomes evident that the aims of terrorists must shift from the gross infliction of panic, death and destruction to the crippling of key information systems before cyberattacks will take precedence over physical attacks. However, given that terrorist groups such as Al Qa'ida are highly intelligent, well-funded, and globally coordinated, the possibility of attacks via cyberspace should make America increasingly vigilant. -

Standards in Weapons Training (Special Operations Forces)
Department of the Army Pamphlet 350–39 Training Standards in Weapons Training (Special Operations Forces) Headquarters Department of the Army Washington, DC 3 July 1997 UNCLASSIFIED SUMMARY of CHANGE DA PAM 350–39 Standards in Weapons Training (Special Operations Forces) This revision-- o Deletes requirements for M72A2 light antitank weapon (LAW) (Chap 2). o Deletes requirements for ranger antiarmor-antipersonnel weapon system (RAAWS) (Chap 2). o Deletes requirements for Stinger crews (Chap 2). o Deletes requirements for mine warfare (Chap 2). o Deletes requirements for MGXX warfare (Chap 2). o Deletes requirements for CAR15 warfare (Chap 2). o Deletes requirements for Combat Training Center (CTC) (Chap 2). o Adds requirements for rocket propelled grenades (RPG) (Chap 3). o Adds requirements for close-quarters combat (CQC) (Chap 3). o Adds requirements for recoilless rifles (RCRL) 84-mm and 90-mm (Chap 3). o Adds requirements for Stinger crews (Chap 3). o Adds requirements for mortars 107-mm (Chap 3). Headquarters *Department of the Army Department of the Army Pamphlet 350–39 Washington, DC 3 July 1997 Training Standards in Weapons Training (Special Operations Forces) procedures for planning, resourcing, and exe- of Staff for Operations and Plans may dele- cuting training. It includes weapons qualifica- gate this authority, in writing, to a division tion standards, suggested training programs, chief within the proponent agency or a field and ammunition requirements for the attain- operating agency in the grade of colonel or ment and sustainment of weapons proficien- the civilian equivalent. c y . T h e p r o g r a m s i n c o r p o r a t e t r a i n i n g devices and simulators. -

1. Apply LSA-T, LSA, Or GMD Lubricant Generously (Enough to 1
1. Apply LSA-T, LSA, or GMD lubricant generously (enough to 1. Use the original plastic bag (barrier bag) used to pack the GTA 43-01-030 spread with your finger) to the MK19 receiver rails and the weapon to keep the sand out of the AT4’s exterior moving mating bolt surfaces (LSA and GMD are alternate lubricants). parts that are listed in TM 9-1315-886-12. SMALL CALIBER (5.56MM TO Cal .50) WEAPONS Using improper lubricants can result in functioning problems. HOT WEATHER/DESERT OPERATION 2. If operating in sand without the original plastic bag, stand up This abbreviated checklist is not to be used as a replacement for 2. Be sure to pay close attention to temperature ranges for exposed AT4 on the aft end instead of laying flat on the ground. the –10 series Tech Manuals or any other PMCS guide lubricants in any climate condition. At temperatures of +33 OF to +145 OF and in sand and dust conditions generously 3. Ensure rubber dust seal at muzzle end is not broken. A broken MACHINE GUNS (5.56MM TO CAL .50) lubricate dust seal will allow contaminant inside the tube, adversely affecting performance. 1. Inspect twice as often as normal. Keep weapon covered when M130 FLARE DISPENSER possible. 1. Inspect and clean, with a soft brush, the 30 contact pins and 2. Generously lube internal working parts. Wipe lubricants from exposed surfaces (Only for 5.56mm to 7.62mm). grounding springs of the M130 dispenser breech. 3. If weapon stops firing, apply Immediate Action Procedures (IAP). -

Remington Defense 2012 Catalog
REMINGTON ARMS CO., LLC Defense Products 870 Remington Drive P.O. Box 700 Madison, NC 27025-0700 Phone: 336-548-8899 Fax: 336-548-7800 www.remingtondefense.com ©2011 Remington Arms Company, LLC Ammunition represented in this catalog is produced by Remington Arms Co., Inc., at an ISO9001:2000 Registered Facility located in Lonoke, RM2125 Arkansas. Remington longarms are manufactured to the highest quality and performance standards, providing reliability, safety, performance, durability, and long service life. SNIPER RIFLES XM2010 SNIPER WEAPON SYSTEM Systematically eliminating all variables. The M24 is based on the legendary Model 700™ and 40-X™ rifles. Its unmatched accuracy and reliability have made it the standard in long-range tactical situations, with over 15,000 sold since 1988, and our Sniper Weapon Systems make outfitting your operation as efficient and as simple as possible. From the basic M24 Sniper System – the standard for the U.S. Army since 1988 – to the advanced XM2010 configuration, we include the world-famous rifle and all the premium, service-proven components you need. Remington® was awarded the U.S. XM2010 Army Enhanced Sniper Rifle (ESR) contract in September 2010 to reconfigure up to 3,600 M24 Sniper Weapon Systems after a full and open competition. FOLDING STOCK » Folded Remington® Arms XM2010 Sniper Weapon System Chassis System captures the bolt handle Order # 86442 securely for airborne operations. M24 SNIPER WEAPON SYSTEM » 24” 7.62 cold-hammer-forged 5R Rifling 416 stainless steel barrel • 1:11.25 twist • Composite aramid fiber-reinforced stock with aluminum bedding block • 5 round internal magazine • Leupold® Mark 4 M3 10x day optic • Steel rings and 2-piece base • Target-style iron sights • Deployment kit and hard case M24 Sniper Weapon System XM2010 sniper WEAPON SYSTEMS (Order #25679) Designed as an upgrade to the venerable M24 SWS, the XM2010 comes configured with the Remington® Arms Chassis System (RACS). -

Daesh/IS Armored Vehicle Borne Improvised Explosive Devices (Avbieds): Insurgent Use and Terrorism Potentials
Claremont Colleges Scholarship @ Claremont CGU Faculty Publications and Research CGU Faculty Scholarship 2-2-2016 Daesh/IS Armored Vehicle Borne Improvised Explosive Devices (AVBIEDs): Insurgent Use and Terrorism Potentials. Robert J. Bunker Claremont Graduate University Recommended Citation Bunker, R. J. (2016, February 02). Daesh/IS Armored Vehicle Borne Improvised Explosive Devices (AVBIEDs): Insurgent Use and Terrorism Potentials. Retrieved February 02, 2016, from TRENDS Research & Advisory, http://trendsinstitution.org/daeshis- armored-vehicle-borne-improvised-explosive-devices-avbieds-insurgent-use-and-terrorism-potentials/ This Blog is brought to you for free and open access by the CGU Faculty Scholarship at Scholarship @ Claremont. It has been accepted for inclusion in CGU Faculty Publications and Research by an authorized administrator of Scholarship @ Claremont. For more information, please contact [email protected]. Robert J. Bunker Non-Resident Fellow, Counter-Terrorism © January 2016 http://trendsinstitution.org/daeshis-armored-vehicle-borne-improvised-explosive-devices-avbieds-insurgent- use-and-terrorism-potentials/ Daesh/IS Armored Vehicle Borne Improvised Explosive Devices (AVBIEDs): Insurgent Use and Terrorism Potentials This essay in the TRENDS terrorism futures series focuses on advanced threats related to vehicle borne improvised explosive devices (VBIEDs). It provides a threat typology of these devices with their evolution into the armored (AVBIED) variant that has now been fielded by Daesh/IS in both Iraq and Syria. A short overview of such insurgent use will be provided as well as a brief discussion of the terrorism potentials of such use if directed against the UAE, Europe, or the United States. VBIED Threat Typology Vehicle borne improvised explosive devices (VBIEDs), or simply vehicle bombs, have existed since the September 1920 deployment of ‘Buda’s Wagon’—an actual horse drawn wagon filled with explosives and scrap metal—at Wall and Broad streets in downtown Manhattan by the anarchist Mario Buda. -

Illicit Trafficking in Firearms, Their Parts, Components and Ammunition To, from and Across the European Union
Illicit Trafficking in Firearms, their Parts, Components and Ammunition to, from and across the European Union REGIONAL ANALYSIS REPORT 1 UNITED NATIONS OFFICE ON DRUGS AND CRIME Vienna Illicit Trafficking in Firearms, their Parts, Components and Ammunition to, from and across the European Union UNITED NATIONS Vienna, 2020 UNITED NATIONS OFFICE ON DRUGS AND CRIME Vienna Illicit Trafficking in Firearms, their Parts, Components and Ammunition to, from and across the European Union REGIONAL ANALYSIS REPORT UNITED NATIONS Vienna, 2020 © United Nations, 2020. All rights reserved, worldwide. This publication may be reproduced in whole or in part and in any form for educational or non-profit purposes without special permission from the copy- right holder, provided acknowledgment of the source is made. UNODC would appreciate receiving a copy of any written output that uses this publication as a source at [email protected]. DISCLAIMERS This report was not formally edited. The contents of this publication do not necessarily reflect the views or policies of UNODC, nor do they imply any endorsement. Information on uniform resource locators and links to Internet sites contained in the present publication are provided for the convenience of the reader and are correct at the time of issuance. The United Nations takes no responsibility for the continued accuracy of that information or for the content of any external website. This document was produced with the financial support of the European Union. The views expressed herein can in no way be taken to reflect -

CLASSIC HANDGUNS: the Soviet Pistole
February 10 Blue Press Section 2 12/14/09 11:10 AM Page 40 40 LASSIC ANDGUNS By John Marshall C .380H ACP, it utilized a bullet diameter: T of haboute SWoviet Pistolet Makarova The Makarov pistol was the standard sidearm of .364” (9mm Luger and .380 ACP bullets measure a most of the Soviet bloc for many years. It was .355” in diameter). In power level, it is about q widely distributed and manufactured in three other midway between the .380 ACP and the 9mm h countries besides its native Russia. It was the most Luger. Makarov’s design was accepted as stan- t ubiquitous sidearm of the Communist empire dur- dard military issue in 1951. It proved to be an d ing the Cold War era. Often regarded as the effective combination of German and Russian b “Russian PP,” it is in fact quite a different pistol. It’s ideas. It was reliable, effective, and easy to man- a a classic and effective design, made in huge numbers and distributed through- out the world. As World War II ended, the Russians were still using the Model 1895 gas-seal Nagant revolver and the very crude TT- 33 Tokarev 7.62mm semiauto pistol. The Tokarev cartridge was a spin-off of and virtually inter- changeable with the 7.63mm Mauser, a bottlenecked high-veloc- ity number. The Tokarev pistol was an interesting design that looked a lot like our 1911 pistol, but had an en-bloc remov- able sear and hammer system, and no manual safety. It was an adequate but flawed design, and although many newer designs were considered before and during WWII, none were picked to replace it. -

Naval Shipbuilding Expansion: the World War II Surface Combatant Experience
Naval Shipbuilding Expansion: The World War II Surface Combatant Experience Dr. Norbert Doerry1 (FL), Dr. Philip Koenig1, P.E. (FL) 1. Naval Sea Systems Command, Washington, D.C. From the demise of the Soviet Union in 1991 to the present day, the U.S. Navy has exercised uncontested control of the high seas. In the absence of peer naval competition, the surface combatant force was re-oriented towards land attack and near-shore operations in support of power projection. This historically unprecedented strategic situation appears to be nearing its end with the rapid growth and reach of the new 21st century Chinese navy and the reinvigoration of the Russian fleet. In response, U.S. Navy strategic planning has been re-balanced towards naval warfare against growing peer competitors, and the naval shipbuilding program is being ramped up. The last time this took place was in the run-up to World War II. What can we learn from that experience, so that the currently planned buildup can be as effective as possible? This paper offers an introductory examination of how the U.S. planned, designed, and built the surface combatant fleet during the interwar period (1920-1941), with a focus on destroyers. After accounting for differences in warship complexity and the industrial and shipbuilding capabilities of the United States of the 1930’s and 1940’s as compared to today, lessons for today’s surface combatant designers and program managers are identified and discussed. Recommendations are made for further work. KEY WORDS nuclear, industrial-scale war can no longer be dismissed. -

Transnational Neo-Nazism in the Usa, United Kingdom and Australia
TRANSNATIONAL NEO-NAZISM IN THE USA, UNITED KINGDOM AND AUSTRALIA PAUL JACKSON February 2020 JACKSON | PROGRAM ON EXTREMISM About the Program on About the Author Extremism Dr Paul Jackson is a historian of twentieth century and contemporary history, and his main teaching The Program on Extremism at George and research interests focus on understanding the Washington University provides impact of radical and extreme ideologies on wider analysis on issues related to violent and societies. Dr. Jackson’s research currently focuses non-violent extremism. The Program on the dynamics of neo-Nazi, and other, extreme spearheads innovative and thoughtful right ideologies, in Britain and Europe in the post- academic inquiry, producing empirical war period. He is also interested in researching the work that strengthens extremism longer history of radical ideologies and cultures in research as a distinct field of study. The Britain too, especially those linked in some way to Program aims to develop pragmatic the extreme right. policy solutions that resonate with Dr. Jackson’s teaching engages with wider themes policymakers, civic leaders, and the related to the history of fascism, genocide, general public. totalitarian politics and revolutionary ideologies. Dr. Jackson teaches modules on the Holocaust, as well as the history of Communism and fascism. Dr. Jackson regularly writes for the magazine Searchlight on issues related to contemporary extreme right politics. He is a co-editor of the Wiley- Blackwell journal Religion Compass: Modern Ideologies and Faith. Dr. Jackson is also the Editor of the Bloomsbury book series A Modern History of Politics and Violence. The views expressed in this paper are solely those of the author, and not necessarily those of the Program on Extremism or the George Washington University.