JMP Securities Elite 80 Report (Formerly Super 70)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Debate Over Measure Heats up Firefi Ghters, Offi Cials Square Off
www.PaloAltoOnline.com Palo 6°Ê888]Ê ÕLiÀÊÓÊUÊ"VÌLiÀÊ£x]ÊÓä£äÊN xäZ Alto Palo Alto dollars lean right in governor’s race Page 3 The debate over Measure heats up Firefi ghters, offi cials square off page 17 Inside this issue 'BMM3FBM&TUBUF A PUBLICATION OF THE ALMANAC AND PALO ALTO WEEKLY20 10 Pulse 12 Transitions 13 Spectrum 14 Movies 28 Eating Out 32 Puzzles 57 2010 G NArts UN fi lm festival takes on environment Page 24 NSports Stanford football has a lot of Luck Page 34 NHome Rethinking a mature garden Page 45 Perinatal Obstetric Diagnostic Anesthesia Center Packard Center for Stanford Children’s Fetal Health School of Hospital Medicine TOGETHER WHAT DREW US HERE AS DOCTORS, DRAWS US BACK AS PATIENTS. Obstetricians Karen Shin and Mary Parman spend their days caring for pregnant patients and delivering babies. Now that each doctor is pregnant with her fi rst child, the choice of where to deliver is clear: right here where they deliver their patients’ babies, at Lucile Packard Children’s Hospital. “At Packard, every specialist you could ever need is available within minutes, around the clock. When you’ve seen how successfully the physicians, staff and nurses work, especially in unpredictable situations, you instinctively www.lpch.org want that level of care for you and your baby.” To learn more about the services we provide to expectant mothers and babies, visit lpch.org Page 2ÊUÊ"VÌLiÀÊ£x]ÊÓä£äÊUÊ*>ÊÌÊ7iiÞ 1ST PLACE BEST LOCAL NEWS COVERAGE California Newspaper Publishers Association UpfrontLocal news, information and analysis Valley execs support Whitman’s ‘independent’ campaign Despite area’s political leanings, Atherton Republican In Menlo Park, another Silicon debate at the Dominican College in Brown countered that in addition enjoys local fundraising edge over Democrat Jerry Brown Valley city that normally favors San Rafael. -

Free, Hateful, and Posted: Rethinking First Amendment Protection of Hate Speech in a Social Media World
Boston College Law Review Volume 60 Issue 7 Article 6 10-30-2019 Free, Hateful, and Posted: Rethinking First Amendment Protection of Hate Speech in a Social Media World Lauren E. Beausoleil Boston College Law School, [email protected] Follow this and additional works at: https://lawdigitalcommons.bc.edu/bclr Part of the First Amendment Commons, and the Internet Law Commons Recommended Citation Lauren E. Beausoleil, Free, Hateful, and Posted: Rethinking First Amendment Protection of Hate Speech in a Social Media World, 60 B.C.L. Rev. 2100 (2019), https://lawdigitalcommons.bc.edu/bclr/vol60/iss7/6 This Notes is brought to you for free and open access by the Law Journals at Digital Commons @ Boston College Law School. It has been accepted for inclusion in Boston College Law Review by an authorized editor of Digital Commons @ Boston College Law School. For more information, please contact [email protected]. FREE, HATEFUL, AND POSTED: RETHINKING FIRST AMENDMENT PROTECTION OF HATE SPEECH IN A SOCIAL MEDIA WORLD Abstract: Speech is meant to be heard, and social media allows for exaggeration of that fact by providing a powerful means of dissemination of speech while also dis- torting one’s perception of the reach and acceptance of that speech. Engagement in online “hate speech” can interact with the unique characteristics of the Internet to influence users’ psychological processing in ways that promote violence and rein- force hateful sentiments. Because hate speech does not squarely fall within any of the categories excluded from First Amendment protection, the United States’ stance on hate speech is unique in that it protects it. -

Parlatore L a W G R O U P
PARLATORE L A W G R O U P 19 November 2019 Office of Inspector General United States Department of Defense, 4800 Mark Center Drive Alexandria, VA 22350-1500 Re: Complaint of Edward R. Gallagher We respectfully submit this complaint on behalf of Special Warfare Operator Chief Petty Officer (SOC) Edward R. Gallagher, United States Navy. For almost two years, SOC Gallagher has suffered irreparable damage at the hands of multiple individuals and entities within the Department of Defense. We are writing to you directly, because of the breadth of the issues, individuals, and commands involved. This complaint encompasses Naval Criminal Investigative Services (NCIS), Office of the Judge Advocate General (OJAG), both the Chief of Staff and the Southwest Region Legal Services Office (COS RLSO and RLSO SW), Chief of Navy Information (CHINFO) and Naval Special Warfare Command (WARCOM) and its subordinate units. As this complaint encompasses abuse by several different DON components, as well as Intelligence Oversight, restriction and retaliation, we believe that your office is the most appropriate to handle this matter. As you might be aware, SOC Gallagher was the defendant in a recent, highly-publicized court-martial related to his deployment to Mosul, Iraq as the Platoon Chief of Alpha Platoon, SEAL Team 7 (ST-7) from 6 February 2017 – 1 September 2017. Although he was charged with an array of offenses, including Murder and Attempted Murder, he was acquitted of those fabricated charges after a jury trial. The purpose of this complaint is not to re-litigate the case itself, but rather to seek accountability for the severe misconduct committed by the investigators, prosecutors, and the command before, during, and after the trial. -

Download Nettleton Indictment
Case 3:19-cr-00001-TJC-PDB Document 1 Filed 01/08/19 Page 1 of 36 PageID 1 UNITED STATES DISTRICT COURT MIDDLE DISTRICT OF FLORIDA 2D'" ,,I '. -J Ii .. .. JACKSONVILLE DIVISION 1/1:2) UNITED STATES OF AMERICA 1 ,,__[ :: V. Case No. 3:19-cr- 1-'7- 3;;2.. fD{> Ct. 1: 18 U.S.C. §§ 1512(b)(3) and 2 JOHN R. NETTLETON Ct. 2: 18 U.S.C. §§ 1512(c)(2) and 2 Ct. 3: 18 U.S.C. §§ IO0I(a)(l) and 2 Cts. 4-5: 18 U .S.C. §§ 1519 and 2 Cts. 6-1 0: 18 U.S.C. § I00I(a)(2) INDICTMENT The Grand Jury charges: Unless otherwise indicated, at all times material to this Indictment: BACKGROUND 1. The defendant, JOHN R. NETTLETON ("NETTLETON") is a Captain in the United States Navy ("Navy"), a department of the United States government. In or about June 2012, he was named the Commanding Officer ("Commander") of Naval Station Guantanamo Bay ("GTMO") at Guantanamo Bay, Cuba. 2. GTMO, located in the southeast comer of Cuba, is a U.S. military installation that serves the Navy. Several thousand U.S. military members, civilian personnel, and their families reside at GTMO. 3. GTMO is part of the Navy Region Southeast ("NRSE"), which is based at Naval Air Station Jacksonville, located in Jacksonville, Florida. As the Commander of GTMO, NETTLETON reported to the Commander of the Navy Case 3:19-cr-00001-TJC-PDB Document 1 Filed 01/08/19 Page 2 of 36 PageID 2 Region Southeast ("CNRSE") and the members of his or her command staff. -

Nothing Is As It Seems: Reading Deviance in Faulkner's Sanctuary
Nothing Is as It Seems: Reading Deviance in Faulkner’s Sanctuary and McCullers’ Reflections in a Golden Eye by Amanda R. Johnson A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Arts in English Middle Tennessee State University August 2014 Thesis Committee: Dr. William Brantley, Chair Dr. Laura Dubek This thesis is dedicated to my Grandmother, Helen Campbell Johnson, and my Mother, Debra Johnson, the women without whom my love of literature could have never blossomed; my father, without whom I could never have gotten through any of this; my Aunt Shirlea Pemberton, whose ears were always ready and open for deviant discussion; my friends, who most surely endured me at my most trying moments; and, finally, my professors, without whose passion and gentle guidance I never would have gotten over my hatred, caused by fear, of southern writers in general. ii ACKNOWLEDGEMENTS I would like to acknowledge the hard work and dedication of my director, Dr. Brantley, and my reader, Dr. Dubek. They have endured my wordiness armed only with the kindest of red pens. iii ABSTRACT Both William Faulkner and Carson McCullers question distinctions between deviance and normalcy through characters that challenge parameters of socially accepted behavior. In Sanctuary (1931) Faulkner presents the seedy underworld of a Memphis brothel; he entices readers into this social abyss while prompting them to investigate the crimes presented and to ponder the cloudy sources of deviant behavior. In Reflections in a Golden Eye (1941) McCullers portrays a commonplace world—that of an army base— in opposition to its commonplace depictions; in the process, she transforms readers from mere voyeurs into voyeur creators. -

Tiktok Y La Creación De Marca Personal
Tiktok y la creación de marca personal Tiktok y la creación de marca personal 1. ÍNDICE - ¿Qué es TikTok? - Historia de TikTok - Evolución de TikTok y expansión imparable (boom durante la pandemia) - Target principal de TikTok (más que la Generación Z) - Las claves del éxito de TikTok - Cómo publicar en TikTok - Consejos para publicar en TikTok - TikTok y su gran engagement - Inversión publicitaria y formatos de anuncios de TikTok - Pasos para hacer una campaña de publicidad serfserve en TikTok - La alianza de TikTok con Shopify: e-commerce - ¿Qué son y para qué sirven el Video Template, Automated Creative Optimisation y Smart Video Soundtrack? - Ventajas de activar una cuenta PRO en TikTok - Otras opciones de privacidad y seguridad en TikTok - Desintoxicación digital: ‘Gestión de Tiempo en Pantalla’, ‘Sincronización familiar’, ‘Modo Restringido’ - Estrategia de influencers, fondo de creadores y compra de monedas virtuales (programa Diamante) - Influencers que más ganan en TikTok - Verificación de cuentas en TikTok - Rumores de espionaje y censura - Cómo crear tu imagen de marca personal en TikTok - Conclusión 2. ¿QUÉ ES TIKTOK? TikTok es una red social china que nace en 2016 y que se basa en la publicación de vídeos cortos y verticales (de entre 3 y 60 segundos) en los que la música y el baile juegan un papel destacado. En China mantiene el nombre original de DouYin, pero en 2018 se extendió por todo el planeta con el nombre de TikTok tras su fusión con la app Musical.ly. Actualmente, se ha convertido en una de las apps más descargadas del mundo por su afinidad y popularidad entre los jóvenes de la Generación Z (nacidos entre 1994 y 2010) y un público de edad cada vez más amplio a raíz del aumento de su popularidad durante la pandemia del Covid- 19. -

Super! Drama TV April 2021
Super! drama TV April 2021 Note: #=serial number [J]=in Japanese 2021.03.29 2021.03.30 2021.03.31 2021.04.01 2021.04.02 2021.04.03 2021.04.04 Mon Tue Wed Thu Fri Sat Sun 06:00 06:00 TWILIGHT ZONE Season 5 06:00 TWILIGHT ZONE Season 5 06:00 06:00 TWILIGHT ZONE Season 5 06:00 TWILIGHT ZONE Season 5 06:00 #15 #17 #19 #21 「The Long Morrow」 「Number 12 Looks Just Like You」 「Night Call」 「Spur of the Moment」 06:30 06:30 TWILIGHT ZONE Season 5 #16 06:30 TWILIGHT ZONE Season 5 06:30 06:30 TWILIGHT ZONE Season 5 06:30 TWILIGHT ZONE Season 5 06:30 「The Self-Improvement of Salvadore #18 #20 #22 Ross」 「Black Leather Jackets」 「From Agnes - With Love」 「Queen of the Nile」 07:00 07:00 CRIMINAL MINDS Season 10 07:00 CRIMINAL MINDS Season 10 07:00 07:00 STAR TREK Season 1 07:00 THUNDERBIRDS 07:00 #1 #2 #20 #19 「X」 「Burn」 「Court Martial」 「DANGER AT OCEAN DEEP」 07:30 07:30 07:30 08:00 08:00 THE BIG BANG THEORY Season 08:00 THE BIG BANG THEORY Season 08:00 08:00 ULTRAMAN towards the future 08:00 THUNDERBIRDS 08:00 10 10 #1 #20 #13「The Romance Recalibration」 #15「The Locomotion Reverberation」 「bitter harvest」 「MOVE- AND YOU'RE DEAD」 08:30 08:30 THE BIG BANG THEORY Season 08:30 THE BIG BANG THEORY Season 08:30 08:30 THE BIG BANG THEORY Season 08:30 10 #14「The Emotion Detection 10 12 Automation」 #16「The Allowance Evaporation」 #6「The Imitation Perturbation」 09:00 09:00 information[J] 09:00 information[J] 09:00 09:00 information[J] 09:00 information[J] 09:00 09:30 09:30 THE GREAT 09:30 SUPERNATURAL Season 14 09:30 09:30 BETTER CALL SAUL Season 3 09:30 ZOEY’S EXTRAORDINARY -

Event Transcript
THOMSON REUTERS EDITED TRANSCRIPT Q3 2020 Salesforce.Com Inc Earnings Call EVENT DATE/TIME: DECEMBER 03, 2019 / 10:00PM GMT THOMSON REUTERS | Contact Us 1 ©2019 Thomson Reuters. All rights reserved. Republication or redistribution of Thomson Reuters content, including by framing or similar means, is prohibited without the prior written consent of Thomson Reuters. 'Thomson Reuters' and the Thomson Reuters logo are registered trademarks of Thomson Reuters and its affiliated companies. DECEMBER 03, 2019 / 10:00PM GMT, Q3 2020 Salesforce.Com Inc Earnings Call CORPORATE PARTICIPANTS Amy E. Weaver salesforce.com, inc. - President of Legal & Corporate Affairs, General Counsel and Secretary Bret Steven Taylor salesforce.com, inc. - President & Chief Product Officer John Cummings salesforce.com, inc. - SVP of IR Keith G. Block salesforce.com, inc. - Co-CEO & Director Marc R. Benioff salesforce.com, inc. - Co-Founder, Chairman & Co-CEO Mark J. Hawkins salesforce.com, inc. - President & CFO CONFERENCE CALL PARTICIPANTS Brent Alan Bracelin Piper Jaffray Companies, Research Division - MD & Senior Research Analyst Brent John Thill Jefferies LLC, Research Division - Equity Analyst Karl Emil Keirstead Deutsche Bank AG, Research Division - Director and Senior Equity Research Analyst Kasthuri Gopalan Rangan BofA Merrill Lynch, Research Division - MD and Head of Software Keith Weiss Morgan Stanley, Research Division - Equity Analyst Sarah Emily Hindlian Macquarie Research - Senior Analyst PRESENTATION Operator Ladies and gentlemen, thank you for standing by, and welcome to the fiscal third quarter earnings conference call. (Operator Instructions) Please be advised that today's conference is being recorded. (Operator Instructions) And without further delay, I would like to hand over the conference to Mr. -
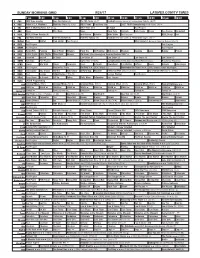
Sunday Morning Grid 9/24/17 Latimes.Com/Tv Times
SUNDAY MORNING GRID 9/24/17 LATIMES.COM/TV TIMES 7 am 7:30 8 am 8:30 9 am 9:30 10 am 10:30 11 am 11:30 12 pm 12:30 2 CBS CBS News Sunday Face the Nation (N) The NFL Today (N) Å Football Houston Texans at New England Patriots. (N) Å 4 NBC Today in L.A. Weekend Meet the Press (N) (TVG) NBC4 News Presidents Cup 2017 TOUR Championship Final Round. (N) Å 5 CW KTLA 5 Morning News at 7 (N) Å KTLA News at 9 In Touch Paid Program 7 ABC News This Week News Rock-Park Outback Jack Hanna Ocean Sea Rescue Basketball 9 KCAL KCAL 9 News Sunday (N) Joel Osteen Schuller Mike Webb Paid Program REAL-Diego Paid 11 FOX Fox News Sunday FOX NFL Kickoff (N) FOX NFL Sunday (N) Football New York Giants at Philadelphia Eagles. (N) Å 13 MyNet Paid Matter Fred Jordan Paid Program MLS Soccer LA Galaxy at Sporting Kansas City. (N) 18 KSCI Paid Program Paid Program 22 KWHY Paid Program Paid Program 24 KVCR Paint With Painting Joy of Paint Wyland’s Paint This Oil Painting Milk Street Mexican Cooking Jazzy Baking Project 28 KCET 1001 Nights 1001 Nights Mixed Nutz Edisons DW News: Live Coverage of German Election 2017 Å 30 ION Jeremiah Youseff In Touch Law Order: CI Law Order: CI Law Order: CI Law Order: CI 34 KMEX Conexión Paid Program Como Dice el Dicho La Comadrita (1978, Comedia) María Elena Velasco. República Deportiva 40 KTBN James Win Walk Prince Carpenter Jesse In Touch PowerPoint It Is Written Jeffress Super Kelinda John Hagee 46 KFTR Paid Program Recuerda y Gana The Reef ›› (2006, Niños) (G) Remember the Titans ››› (2000, Drama) Denzel Washington. -

Super! Drama TV December 2020 ▶Programs Are Suspended for Equipment Maintenance from 1:00-7:00 on the 15Th
Super! drama TV December 2020 ▶Programs are suspended for equipment maintenance from 1:00-7:00 on the 15th. Note: #=serial number [J]=in Japanese [D]=in Danish 2020.11.30 2020.12.01 2020.12.02 2020.12.03 2020.12.04 2020.12.05 2020.12.06 Mon Tue Wed Thu Fri Sat Sun 06:00 06:00 MACGYVER Season 2 06:00 MACGYVER Season 2 06:00 MACGYVER Season 2 06:00 MACGYVER Season 2 06:00 06:00 MACGYVER Season 3 06:00 BELOW THE SURFACE 06:00 #20 #21 #22 #23 #1 #8 [D] 「Skyscraper - Power」 「Wind + Water」 「UFO + Area 51」 「MacGyver + MacGyver」 「Improvise」 06:30 06:30 06:30 07:00 07:00 THE BIG BANG THEORY 07:00 THE BIG BANG THEORY 07:00 THE BIG BANG THEORY 07:00 THE BIG BANG THEORY 07:00 07:00 STAR TREK Season 1 07:00 STAR TREK: THE NEXT 07:00 Season 12 Season 12 Season 12 Season 12 #4 GENERATION Season 7 #7「The Grant Allocation Derivation」 #9 「The Citation Negation」 #11「The Paintball Scattering」 #13「The Confirmation Polarization」 「The Naked Time」 #15 07:30 07:30 THE BIG BANG THEORY 07:30 THE BIG BANG THEORY 07:30 THE BIG BANG THEORY 07:30 information [J] 07:30 「LOWER DECKS」 07:30 Season 12 Season 12 Season 12 #8「The Consummation Deviation」 #10「The VCR Illumination」 #12「The Propagation Proposition」 08:00 08:00 SUPERNATURAL Season 11 08:00 SUPERNATURAL Season 11 08:00 SUPERNATURAL Season 11 08:00 SUPERNATURAL Season 11 08:00 08:00 THUNDERBIRDS ARE GO 08:00 STAR TREK: THE NEXT 08:00 #5 #6 #7 #8 Season 3 GENERATION Season 7 「Thin Lizzie」 「Our Little World」 「Plush」 「Just My Imagination」 #18「AVALANCHE」 #16 08:30 08:30 08:30 THUNDERBIRDS ARE GO 「THINE OWN SELF」 08:30 -

Designing the Internet of Things
Designing the Internet of Things Adrian McEwen, Hakim Cassimally This edition first published 2014 © 2014 John Wiley and Sons, Ltd. Registered office John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex, PO19 8SQ, United Kingdom For details of our global editorial offices, for customer services and for information about how to apply for permission to reuse the copyright material in this book please see our website at www.wiley.com. The right of the author to be identified as the author of this work has been asserted in accordance with the Copyright, Designs and Patents Act 1988. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, except as permitted by the UK Copyright, Designs and Patents Act 1988, without the prior permission of the publisher. Wiley also publishes its books in a variety of electronic formats. Some content that appears in print may not be available in electronic books. Designations used by companies to distinguish their products are often claimed as trademarks. All brand names and product names used in this book are trade names, service marks, trademarks or registered trademarks of their respective owners. The publisher is not associated with any product or vendor mentioned in this book. This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold on the under- standing that the publisher is not engaged in rendering professional services. If professional advice or other expert assistance is required, the services of a competent professional should be sought. -

We Envision a Digital World Powered by Intelligent Identity
WE ENVISION A DIGITAL WORLD POWERED BY INTELLIGENT IDENTITY pingidentity.com | @pingidentity IDENTITY SECURES AND CONNECTS YOUR AGILE ENTERPRISE Enterprises compete in a new digital era where user experience is paramount and security can’t be sacrificed. With data breaches on the rise and new threats emerging, organizations need strong security. At the same time, users expect to easily access all of their applications from any device. Finding the right mix of security and convenience is challenging, especially across the complex IT environments and application portfolios found in the world’s largest enterprises. At Ping Identity, we help you use identity to generate more value from your digital business initiatives by providing users with secure, seamless access to all their applications and resources from anywhere. We help you meet your security requirements while allowing you to achieve greater agility with our flexible deployment options that support all stages of cloud adoption. Our modern IAM platform spans hybrid IT and multi-cloud infrastructures to connect all users to all applications and APIs at scale. WE’RE AN IAM INDUSTRY LEADER RECOGNIZED LEADER in Access Management and Identity as a Service (IDaaS) AWARD WINNER in Identity and Access Security, Cybersecurity, Information Security and API Security OVER 50% OF THE FORTUNE 500 USE PING SOLUTIONS 12 of the 12 8 of the 10 largest U.S. banks largest bio-pharmacueticals 4 of the 5 2 of the 3 largest healtchare plans largest hospitals ENTERPRISE-GRADE FROM THE BEGINNING We’re proud to be born and raised in the enterprise. Since 2002, our standards- based platform has evolved to allow all users and devices to securely access all cloud, mobile, SaaS and on-premises applications and APIs.