Vulnerability Assessment for Cascading Failure in the Highway Traffic System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Educated Youth Should Go to the Rural Areas: a Tale of Education, Employment and Social Values*
Educated Youth Should Go to the Rural Areas: A Tale of Education, Employment and Social Values* Yang You† Harvard University This draft: July 2018 Abstract I use a quasi-random urban-dweller allocation in rural areas during Mao’s Mass Rustication Movement to identify human capital externalities in education, employment, and social values. First, rural residents acquired an additional 0.1-0.2 years of education from a 1% increase in the density of sent-down youth measured by the number of sent-down youth in 1969 over the population size in 1982. Second, as economic outcomes, people educated during the rustication period suffered from less non-agricultural employment in 1990. Conversely, in 2000, they enjoyed increased hiring in all non-agricultural occupations and lower unemployment. Third, sent-down youth changed the social values of rural residents who reported higher levels of trust, enhanced subjective well-being, altered trust from traditional Chinese medicine to Western medicine, and shifted job attitudes from objective cognitive assessments to affective job satisfaction. To explore the mechanism, I document that sent-down youth served as rural teachers with two new county-level datasets. Keywords: Human Capital Externality, Sent-down Youth, Rural Educational Development, Employment Dynamics, Social Values, Culture JEL: A13, N95, O15, I31, I25, I26 * This paper was previously titled and circulated, “Does living near urban dwellers make you smarter” in 2017 and “The golden era of Chinese rural education: evidence from Mao’s Mass Rustication Movement 1968-1980” in 2015. I am grateful to Richard Freeman, Edward Glaeser, Claudia Goldin, Wei Huang, Lawrence Katz, Lingsheng Meng, Nathan Nunn, Min Ouyang, Andrei Shleifer, and participants at the Harvard Economic History Lunch Seminar, Harvard Development Economics Lunch Seminar, and Harvard China Economy Seminar, for their helpful comments. -

Research on Employment Difficulties and the Reasons of Typical
2017 3rd International Conference on Education and Social Development (ICESD 2017) ISBN: 978-1-60595-444-8 Research on Employment Difficulties and the Reasons of Typical Resource-Exhausted Cities in Heilongjiang Province during the Economic Transition Wei-Wei KONG1,a,* 1School of Public Finance and Administration, Harbin University of Commerce, Harbin, China [email protected] *Corresponding author Keywords: Typical Resource-Exhausted Cities, Economic Transition, Employment. Abstract. The highly correlation between the development and resources incurs the serious problems of employment during the economic transition, such as greater re-employment population, lower elasticity of employment, greater unemployed workers in coal industry. These problems not only hinder the social stability, but also slow the economic transition and industries updating process. We hope to push forward the economic transition of resource-based cities and therefore solve the employment problems through the following measures: developing specific modern agriculture and modern service industry, encouraging and supporting entrepreneurships, implementing re-employment trainings, strengthening the public services systems for SMEs etc. Background According to the latest statistics from the State Council for 2013, there exists 239 resource-based cities in China, including 31 growing resource-based cities, 141 mature, and 67 exhausted. In the process of economic reform, resource-based cities face a series of development challenges. In December 2007, the State Council issued the Opinions on Promoting the Sustainable Development of Resource-Based Cities. The National Development and Reform Commission identified 44 resource-exhausted cities from March 2008 to March 2009, supporting them with capital, financial policy and financial transfer payment funds. In the year of 2011, the National Twelfth Five-Year Plan proposed to promote the transformation and development of resource-exhausted area. -

Changchun–Harbin Expressway Project
Performance Evaluation Report Project Number: PPE : PRC 30389 Loan Numbers: 1641/1642 December 2006 People’s Republic of China: Changchun–Harbin Expressway Project Operations Evaluation Department CURRENCY EQUIVALENTS Currency Unit – yuan (CNY) At Appraisal At Project Completion At Operations Evaluation (July 1998) (August 2004) (December 2006) CNY1.00 = $0.1208 $0.1232 $0.1277 $1.00 = CNY8.28 CNY8.12 CNY7.83 ABBREVIATIONS AADT – annual average daily traffic ADB – Asian Development Bank CDB – China Development Bank DMF – design and monitoring framework EIA – environmental impact assessment EIRR – economic internal rate of return FIRR – financial internal rate of return GDP – gross domestic product ha – hectare HHEC – Heilongjiang Hashuang Expressway Corporation HPCD – Heilongjiang Provincial Communications Department ICB – international competitive bidding JPCD – Jilin Provincial Communications Department JPEC – Jilin Provincial Expressway Corporation MOC – Ministry of Communications NTHS – national trunk highway system O&M – operations and maintenance OEM – Operations Evaluation Mission PCD – provincial communication department PCR – project completion report PPTA – project preparatory technical assistance PRC – People’s Republic of China RRP – report and recommendation of the President TA – technical assistance VOC – vehicle operating cost NOTE In this report, “$” refers to US dollars. Keywords asian development bank, development effectiveness, expressways, people’s republic of china, performance evaluation, heilongjiang province, jilin province, transport Director Ramesh Adhikari, Operations Evaluation Division 2, OED Team leader Marco Gatti, Senior Evaluation Specialist, OED Team members Vivien Buhat-Ramos, Evaluation Officer, OED Anna Silverio, Operations Evaluation Assistant, OED Irene Garganta, Operations Evaluation Assistant, OED Operations Evaluation Department, PE-696 CONTENTS Page BASIC DATA v EXECUTIVE SUMMARY vii MAPS xi I. INTRODUCTION 1 A. -

The First International U3as Online Art Awards 2020 ---Drawing/Painting
The First International U3As Online Art Awards 2020 ---Drawing/Painting Winners list Premier Concours International d'art des U3As 2020 --- Liste des gagnants de dessin / peinture Nationality/N Awards/ Prix Participants U3A ationalité Top Award/ Meilleur prix Tan Hongbin Yantai Tianma U3A Chinese Golden Awards/ Prix or Yang Xuzhou Qingdao Shinan District U3A Chinese Liu Lijie Yantai Tianma U3A Chinese Silver Awards/ Prix argent Theresa U3A AUT Lebanon Lebanese BEST Expression of Abstract Awards/ Prix Abstrait Ninón Daphne Ichazo UCB universidad adulto mayor UPTE Bolivian Munter Excellence Awards/ Prix Yasumasa Arai U3J Tokyo(Heart No Kai) Japanese excellence Universidad Mexiquense del Bicentenario, Librado Ojeda Unidad de Estudios Superiores para Adultos y Mexican Adultos Mayores Ecatepec Golden Awards/ Prix or Yang Na Weihai Rushan Municipal U3A Chinese Tang Huaren Weihai Municipal U3A Chinese Silver Awards/ Prix argent Sumiko Tachibana U3J Tokyo( NPO HEART NO KAI) Japanese Liu Wentao Zaozhuang Shizhong District U3A Chinese BEST Color Awards/ Prix Zhao Zhongkun Qingdao Municipal U3A Chinese couleur Marinella Caprotti UTE Bresso Italian Excellence Awards/ Prix excellence Sarah Sergienki U3A AUT Lebanon Lebanese Josephine Swift EU Bratislava,Slovakia Slovakian MÁRIA ŠIMNOVÁ Economic University Bratislava Slovakian Golden Awards/ Prix or Eleonor Youssef Aiuta paint and creativity Lebanese Marinella Caprotti UTE Bresso Italian Silver Awards/ Prix argent Lin Zhihong Yantai Tianma U3A Chinese BEST Composition Awards/ Prix composition Eva Novotná -

Comprehensive Evaluation of Land Resources Carrying Capacity Under Different Scales Based on RAGA-PPC Qiuxiang Jiang, Qiang Fu, Jun Meng, Zilong Wang, Ke Zhao
Comprehensive Evaluation of Land Resources Carrying Capacity under Different Scales Based on RAGA-PPC Qiuxiang Jiang, Qiang Fu, Jun Meng, Zilong Wang, Ke Zhao To cite this version: Qiuxiang Jiang, Qiang Fu, Jun Meng, Zilong Wang, Ke Zhao. Comprehensive Evaluation of Land Resources Carrying Capacity under Different Scales Based on RAGA-PPC. 8th International Con- ference on Computer and Computing Technologies in Agriculture (CCTA), Sep 2014, Beijing, China. pp.200-209, 10.1007/978-3-319-19620-6_25. hal-01420233 HAL Id: hal-01420233 https://hal.inria.fr/hal-01420233 Submitted on 20 Dec 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License Comprehensive Evaluation of Land Resources Carrying Capacity under Different Scales Based on RAGA-PPC 1,2,3,4,a 1,2,3 4 1,2,3,4 1 Qiuxiang Jiang , Qiang Fu , Jun Meng , Zilong Wang , Ke Zhao 1College of Water Conservancy and Architecture, Northeast Agricultural University, Harbin 150030; 2Collaborative Innovation Center of Grain Production Capacity Improvement in Heilongjiang Province, Harbin 150030; 3Key Laboratory of Water-saving Agriculture, College of Heilongjiang Province, Harbin 150030;4Postdoctoral Mobile Research Station of Agricultural and Forestry Economy Management, Northeast Agricultural University, Harbin 150030 [email protected] Abstract. -

Heilongjiang - Alberta Relations
Heilongjiang - Alberta Relations This map is a generalized illustration only and is not intended to be used for reference purposes. The representation of political boundaries does not necessarily reflect the position of the Government of Alberta on international issues of recognition, sovereignty or jurisdiction. PROFILE is twinned with Daqing, known as the oil technology, medicine, culture, education and capital of China. environmental protection. Capital: Harbin . Heilongjiang is China’s principal oil-producing . In 1998, Heilongjiang suffered its worst Population: 38.2 million (2012) province containing China’s largest oil field, flooding in decades. Albertans responded by (3 per cent of China’s total population) Daqing Oilfield. raising over $200,000 in private donations. Major Cities: Harbin (12,635,000); Suihua (5,616,000); Qiqihar (5,710,000); Daqing . Alberta companies have been successful in . The Government of Alberta made an (2,900,000); and Mudanjiang (2,822,000) supplying energy equipment and services to additional $100,000 contribution to flood relief Heilongjiang. In 1998, Sunwing Energy Ltd. of efforts and extended a special scholarship to Language: Mandarin Calgary was the first foreign company to Heilongjiang for skill development related to Government: Chinese Communist Party produce oil in China. flood management. Head of Government: Governor WANG Xiankui RELATIONSHIP OVERVIEW TRADE AND INVESTMENT represents the executive branch of government and is responsible to the Heilongjiang Provincial . 2016 marked the 35th anniversary of the . China is Alberta’s second largest trading People’s Congress Heilongjiang-Alberta sister province partner. Alberta’s trading relationship with relationship. In 2011, for the 30th anniversary, China has more than tripled since 2003. -

Considering the Dynamic Dependence of Icing-Inducing Factors
Exploring the Highway Icing Risk: Considering the Dynamic Dependence of Icing-Inducing Factors Qiang Liu Harbin Institute of Technology Aiping Tang ( [email protected] ) Harbin Institute of Technology Zhongyue Wang Harbin Institute of Technology Buyue Zhao Beijing Jiaotong University Research Article Keywords: Dependence analysis, Exceeding probability, Hazard, Vulnerability, Transportation risk Posted Date: April 22nd, 2021 DOI: https://doi.org/10.21203/rs.3.rs-445530/v1 License: This work is licensed under a Creative Commons Attribution 4.0 International License. Read Full License 1 Exploring the highway icing risk: Considering the dynamic 2 dependence of icing-inducing factors 3 Qiang Liu a, Aiping Tang a, b *, Zhongyue Wang a,Buyue Zhao c 4 a School of Civil Engineering, Harbin Institute of Technology, Harbin 150090, China 5 b Key Lab of Smart Prevention and Mitigation of Civil Engineering Disasters of the Ministry of Industry and Information Technology, 6 Harbin Institute of Technology, Harbin150090, China 7 c School of Civil Engineering, Beijing Jiaotong University, Beijing 100044, China 8 Abstract:In terms of the dynamic dependence between icing-inducing factors, this study is to explore the risk 9 distribution of highways when icing events occur in the study area. A joint distribution considering the dynamic 10 correlation of inducing factors was first constructed employing the Copula theory, which then yielded the 11 possibility of icing events. Meanwhile, hazard zones and intensities of icing were proposed under different 12 exceeding probabilities. After finishing the vulnerability analysis of highways, the risk matrix was used to conduct 13 the icing risk for the highway, which was then applied to the construction of the risk zoning map. -

Characteristics of Spatial Connection Based on Intercity Passenger Traffic Flow in Harbin- Changchun Urban Agglomeration, China Research Paper
Guo, R.; Wu, T.; Wu, X.C. Characteristics of Spatial Connection Based on Intercity Passenger Traffic Flow in Harbin- Changchun Urban Agglomeration, China Research Paper Characteristics of Spatial Connection Based on Intercity Passenger Traffic Flow in Harbin-Changchun Urban Agglomeration, China Rong Guo, School of Architecture,Harbin Institute of Technology,Key Laboratory of Cold Region Urban and Rural Human Settlement Environment Science and Technology,Ministry of Industry and Information Technology,Harbin 150006,China Tong Wu, School of Architecture,Harbin Institute of Technology,Key Laboratory of Cold Region Urban and Rural Human Settlement Environment Science and Technology,Ministry of Industry and Information Technology,Harbin 150006,China Xiaochen Wu, School of Architecture,Harbin Institute of Technology,Key Laboratory of Cold Region Urban and Rural Human Settlement Environment Science and Technology,Ministry of Industry and Information Technology,Harbin 150006,China Abstract With the continuous improvement of transportation facilities and information networks, the obstruction of distance in geographic space has gradually weakened, and the hotspots of urban geography research have gradually changed from the previous city hierarchy to the characteristics of urban connections and networks. As the main carrier and manifestation of elements, mobility such as people and material, traffic flow is of great significance for understanding the characteristics of spatial connection. In this paper, Harbin-Changchun agglomeration proposed by China's New Urbanization Plan (2014-2020) is taken as a research object. With the data of intercity passenger traffic flow including highway and railway passenger trips between 73 county-level spatial units in the research area, a traffic flow model is constructed to measure the intensity of spatial connection. -

Analyzing Ecological Functions in Coal Mining Cities Based on RS and GIS
Pol. J. Environ. Stud. Vol. 27, No. 3 (2018), 1165-1174 DOI: 10.15244/pjoes/75190 ONLINE PUBLICATION DATE: 2017-12-13 Original Research Analyzing Ecological Functions in Coal Mining Cities Based on RS and GIS Ling Liu1, 2, Jinsheng Zhou1, 2* 1School of Humanities and Economic Management, China University of Geosciences, P. R. China 2Key Laboratory of Carrying Capacity Assessment for Resource and Environment, Ministry of Land and Resources, Beijing 100083, China Received: 16 March 2017 Accepted: 21 June 2017 Abstract Ecological problems have long been a hard issue in mining cities. This paper tried to present ecological functions in mining cities from two aspects: landscape ecology and ecological carrying capacity. The city of Qitaihe, one of the coal cities in Heilongjiang Province in northeastern China, was chosen as a typical study area. Remote sensing data from 1957, 1985, 2000, and 2015, and geographic information system (GIS) techniques were employed to obtain land use and cover information. Methods of landscape pattern indexes and a modified model of ecological carrying capacity which added social and economy index were used to study the spatial and temporal variation of the ecological condition. Results showed that the landscape pattern changed tremendously during the study period due to interference from human activity. The degree of aggregation, dominance, and fragmentation of mining land showed an increasing trend. On the other hand, the ecological carrying capacity per capita declined by 37.4% from 1985 to 2000. Except for the growth of population, the dim social and economic conditions had an impact on this decline too. In addition, spatial distribution of land types and ecological carrying capacity also had some correlation with the city’s overall planning. -

HARBIN BANK CO., LTD. (A Joint Stock Company Incorporated in the People’S Republic of China with Limited Liability) Stock Code: 6138
HARBIN BANK CO., LTD. (A joint stock company incorporated in the People’s Republic of China with limited liability) Stock Code: 6138 2020 INTERIM REPORT Harbin Bank Co., Ltd. Contents Interim Report 2020 Definitions 2 Company Profile 3 Summary of Accounting Data and Financial Indicators 7 Management Discussion and Analysis 9 Changes in Share Capital and Information on Shareholders 73 Directors, Supervisors, Senior Management and Employees 78 Important Events 84 Organisation Chart 90 Financial Statements 91 Documents for Inspection 188 The Company holds the Finance Permit No. B0306H223010001 approved by the China Banking and Insurance Regulatory Commission and has obtained the Business License (Unified Social Credit Code: 912301001275921118) approved by the Market Supervision and Administration Bureau of Harbin. The Company is not an authorised institution within the meaning of the Hong Kong Banking Ordinance (Chapter 155 of the Laws of Hong Kong), not subject to the supervision of the Hong Kong Monetary Authority, and not authorised to carry on banking/deposit-taking business in Hong Kong. Denitions In this report, unless the context otherwise requires, the following terms shall have the meanings set out below. “Articles of Association” the Articles of Association of Harbin Bank Co., Ltd. “Board” or “Board of Directors” the board of directors of the Company “Board of Supervisors” the board of supervisors of the Company “CBIRC”/”CBRC” the China Banking and Insurance Regulatory Commission/China Banking Regulatory Commission (before 17 March -

Apical Vowel in Jixi-Hui Chinese: an Articulatory Study
APICAL VOWEL IN JIXI-HUI CHINESE: AN ARTICULATORY STUDY Bowei Shao, Rachid Ridouane Laboratoire de Phonétique et Phonolgoie (CNRS & Sorbonne Nouvelle, Paris) [email protected]; [email protected] ABSTRACT “voiced prolongation of the consonant”, and Duanmu [6] proposed to analyze it not as an underlying In this study, we analyze mid-sagittal and coronal phoneme, but as a segment triggered by an empty ultrasound data from four subjects in order to nucleus and the spreading of the feature [+fricative] investigate the articulatory properties of the apical from the onset. In our study, we adopt the [z] vowel /z/ in Jixi-Hui Chinese (JHC). We seek to transcription following Duanmu and Dell. determine whether this unique segment, particularly While SC apical vowels are studied in much detail, well studied in Standard Chinese (SC), has less is known about these segments in other Chinese articulatory characteristics of a vowel or a fricative languages. This current study is based on Jixi-Hui consonant. Mid-sagittal ultrasound data show that it Chinese (JHC), which is a Hui 徽 group Chinese displays the same tongue shape as consonant [s] and language spoken in Jixi 绩溪 County in Anhui 安徽 may have a slightly higher tongue tip, which could province, China [10, 22, 23]. It has two major explain the presence of abundant frication noise. The variants; our study is based on the city variant, which raising of the tongue dorsum, already observed in SC, has 9 phonological monophthong vowels: [i, y, u, ʉ, varies in JHC across speakers. Coronal ultrasound o, ɤ, ɔ, a], in addition to the apical vowel [z]. -
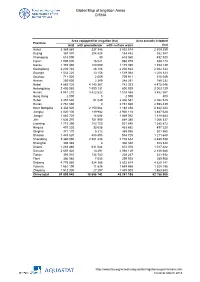
Global Map of Irrigation Areas CHINA
Global Map of Irrigation Areas CHINA Area equipped for irrigation (ha) Area actually irrigated Province total with groundwater with surface water (ha) Anhui 3 369 860 337 346 3 032 514 2 309 259 Beijing 367 870 204 428 163 442 352 387 Chongqing 618 090 30 618 060 432 520 Fujian 1 005 000 16 021 988 979 938 174 Gansu 1 355 480 180 090 1 175 390 1 153 139 Guangdong 2 230 740 28 106 2 202 634 2 042 344 Guangxi 1 532 220 13 156 1 519 064 1 208 323 Guizhou 711 920 2 009 709 911 515 049 Hainan 250 600 2 349 248 251 189 232 Hebei 4 885 720 4 143 367 742 353 4 475 046 Heilongjiang 2 400 060 1 599 131 800 929 2 003 129 Henan 4 941 210 3 422 622 1 518 588 3 862 567 Hong Kong 2 000 0 2 000 800 Hubei 2 457 630 51 049 2 406 581 2 082 525 Hunan 2 761 660 0 2 761 660 2 598 439 Inner Mongolia 3 332 520 2 150 064 1 182 456 2 842 223 Jiangsu 4 020 100 119 982 3 900 118 3 487 628 Jiangxi 1 883 720 14 688 1 869 032 1 818 684 Jilin 1 636 370 751 990 884 380 1 066 337 Liaoning 1 715 390 783 750 931 640 1 385 872 Ningxia 497 220 33 538 463 682 497 220 Qinghai 371 170 5 212 365 958 301 560 Shaanxi 1 443 620 488 895 954 725 1 211 648 Shandong 5 360 090 2 581 448 2 778 642 4 485 538 Shanghai 308 340 0 308 340 308 340 Shanxi 1 283 460 611 084 672 376 1 017 422 Sichuan 2 607 420 13 291 2 594 129 2 140 680 Tianjin 393 010 134 743 258 267 321 932 Tibet 306 980 7 055 299 925 289 908 Xinjiang 4 776 980 924 366 3 852 614 4 629 141 Yunnan 1 561 190 11 635 1 549 555 1 328 186 Zhejiang 1 512 300 27 297 1 485 003 1 463 653 China total 61 899 940 18 658 742 43 241 198 52